Archive
-
 National Cybersecurity Awareness Month: shining a spotlight on secure access
National Cybersecurity Awareness Month: shining a spotlight on secure accessOctober is National Cybersecurity Awareness Month (NCSAM), and here at Yubico, we’re doing our part to raise awareness on the importance of cybersecurity and staying safe online. Billions of login credentials and user records are routinely leaked — sometimes in the course of a single year — and can cause significant damage to those who […]
Read more -
 YubiHSM 2 Now Qualified for AWS IoT Greengrass Hardware Security Integration
YubiHSM 2 Now Qualified for AWS IoT Greengrass Hardware Security IntegrationWe are excited to announce that Amazon Web Service (AWS) Internet of Things (IoT) Greengrass users can now use Yubico’s hardware security module, the YubiHSM 2, Yubico’s ultra-portable hardware security module, for secure key storage. AWS IoT Greengrass software provides local compute, messaging, and data caching for the IoT devices, enabling users to run IoT […]
Read more -
 Taking strong, hardware-backed MFA where mobile phones can’t go with PingID
Taking strong, hardware-backed MFA where mobile phones can’t go with PingIDThe need for identity and access management With security breaches becoming a growing and expensive problem, organizations are embracing identity and access management (IAM) platforms like Ping Identity with multi factor authentication (MFA). This technology enables organizations to address expanding security concerns and regulatory requirements within and beyond their employee base, while also reducing complexity […]
Read more -
 Accountants protecting data and Yubico Developer Program update
Accountants protecting data and Yubico Developer Program updateWe just received some stats from our friends over at QuickBooks—the number of apps used by the Small Business Market is projected to grow threefold in the next few years. The QuickBooks Online Community is comprised of more than 3.2 million small businesses, 200 thousand accountants/bookkeepers, and thousands of 3rd party app developers. That’s a […]
Read more -
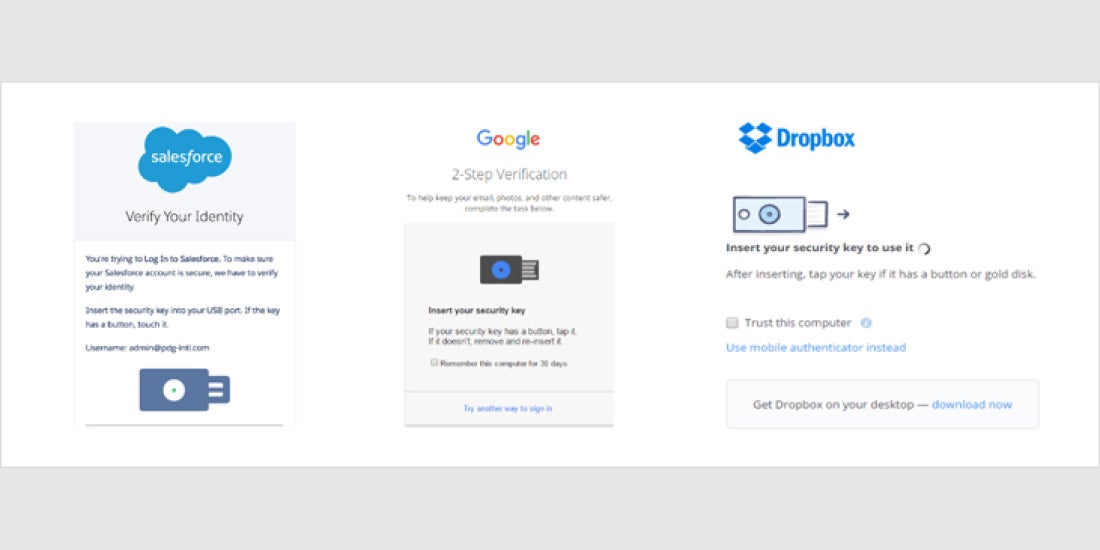 3 Top Things to Consider When Implementing FIDO U2F With Your Service
3 Top Things to Consider When Implementing FIDO U2F With Your ServiceNow more than ever, security must be built into everything. By leveraging open standards, instead of building security protocols from the ground up, organizations can provide strong authentication faster than ever before. We created the Universal 2nd Factor (U2F) protocol together with Google several years ago and offered it the world for free along with […]
Read more
