Protect against cyber security threats in retail and hospitality
Stop account takeovers while enhancing customer experience

The high availability of sensitive data including payment card information (PCI) and employee and customer personal identifiable information (PII), makes retail and hospitality organizations a lucrative target for cyberattacks including phishing, ransomware, and data theft.
A core part of a strong Zero Trust cybersecurity approach is multi-factor authentication (MFA), but not all forms are created equal in terms of security or user experience. Retail and hospitality industries are consumer and customer-facing and the MFA solution should enable a frictionless experience.
Legacy authentication such as usernames and passwords can be easily hacked and increase IT help desk costs related to password resets. Mobile-based authentication are highly susceptible to attacks and attribute to MFA fatigue while also unable to be used in certain environments.
Yubico offers the YubiKey for highest-assurance phishing-resistant two-factor, multi-factor, and passwordless authentication, helping retail and hospitality organizations stop phishing attacks, ransomware, and account takeovers, all while protecting sensitive customer and financial data, and driving regulatory compliance.
Customer Spotlight:
Hyatt Hotels is going passwordless
Modern phishing-resistant MFA eliminates authentication fatigue for colleagues, while also creating improved guest experiences. YubiKeys work seamlessly with Hyatt’s existing Microsoft environment creating elevated security for employees and guest data.
WHITE PAPER
Protecting against modern cyber threats in retail and hospitality
Learn how modernizing authentication can secure shared devices, protect sensitive data, and prevent account takeovers while enhancing customer experience.
The cyber security benefits for retail and hospitality are within your reach with the YubiKey.

Secure access to systems, apps and data while modernizing device security
YubiKeys ensure that only authorized users have access to PII data and critical systems, while also securing access to POS terminals, shared workstations/devices, and RFID readers. Even provide strong security for customer accounts and loyalty programs by leveraging YubiKeys. They protect anyone, anywhere. YubiKeys are also easily re-programmed, making them suitable for seasonal and temporary workers, and they ensure self-service password resets, drastically reducing IT help desk costs.

Protect call center agents and any mobile-restricted environments
Mobile-restricted environments historically have been an issue for mobile-based MFA methods using SMS, push or apps. The YubiKey offers easy and secure authentication when there is no cellular connection or where mobile devices are restricted. YubiKeys are highly suitable for users that can’t, won’t, or don’t use mobile authentication, helping you achieve 100% MFA coverage and satisfy your cyber insurance MFA requirements.

Drive compliance to industry regulations and authentication standards
YubiKeys enable strong verification of users keeping organizations compliant with existing and emerging regulations such as Payment Card Industry Data Security Standard (PCI DSS) v4.0.1 and v4.0, EU Payment Services Directive 2 (PSD2), GDPR, and more. YubiKeys are also FIDO2/WebAuthn compliant streamlining workflows and increasing productivity, protecting against the most common types of phishing attacks and allow for a simple “plug and Play” set of instructions for non technical users”
Protect your entire supply chain and eliminate vulnerability gaps
YubiKeys offers secure, convenient, and scalable security making it easy for you and your supply chain vendors to deploy strong authentication. Yubico solutions, and flexible YubiKey procurement and deployment options through YubiEnterprise Subscription, you can experience an estimated 203% ROI over three years and a reduction of password-related help desk support tickets by 75% by year 3.
With YubiEnterprise Delivery from Yubico, it’s easy for your supply chain to get security keys directly into the hands of their users. Authentication of users is vital along the supply chain, but so is authentication between systems and machines, which is provided by the world’s smallest hardware security module (HSM), the YubiHSM2.
WATCH THE WEBINAR
How to bolster your authentication strategy for PCI DSS 4.0
Learn about what this new standard means for you and how not all forms of multi-factor authentication (MFA) are created equal in terms of compliance and mitigating cyber risk.

RCS provides PCI compliance and easy multi-factor authentication with YubiKey
“Instead of YubiKey being a highly recommended solution for our clients,we’re moving towards making them a required solution. We are building it into our hosting suite, and into our user fees.”
STUDY
Risk reduction, business growth, and efficiency enabled by YubiKeys
Enter your own company data to create a custom Dynamic TEI study and instantly see how Yubico’s solutions can help your organization!
YubiKeys integrate seamlessly with existing IAM solutions and provide secure authentication for hundreds of applications and services eliminating any rip or replace of existing solutions.

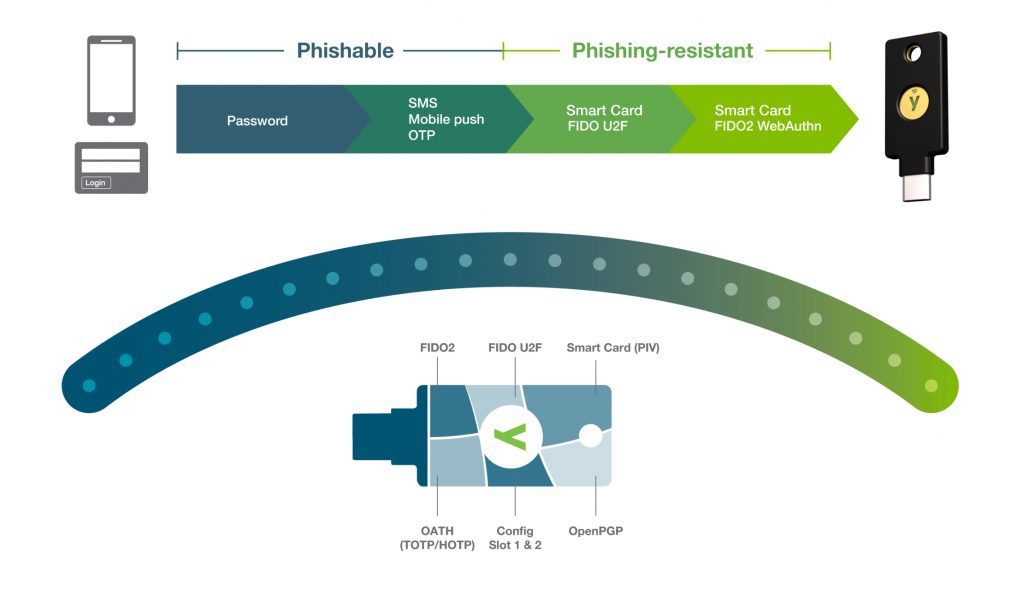
Secure today, future proof for tomorrow
Moving to a passwordless and a phishing-resistant future is a journey due to managing older infrastructure. You need a solution to meet you where you are while bolstering your cybersecurity posture for the better. With the YubiKey’s multi-protocol support, it is possible to move towards a more secure future in meaningful steps, eventually moving to passwordless authentication—authentication that does not require the user to provide a password at login at all.
Ready to take the next step?

Find the right YubiKey
Contact our sales team for a personalized assessment of your company’s needs.

Learn how to get started
Check out the deployment best practices that can help to accelerate adoption of modern, phishing-resistant MFA at scale using the YubiKey.
