Passkeys
Secure login without passwords
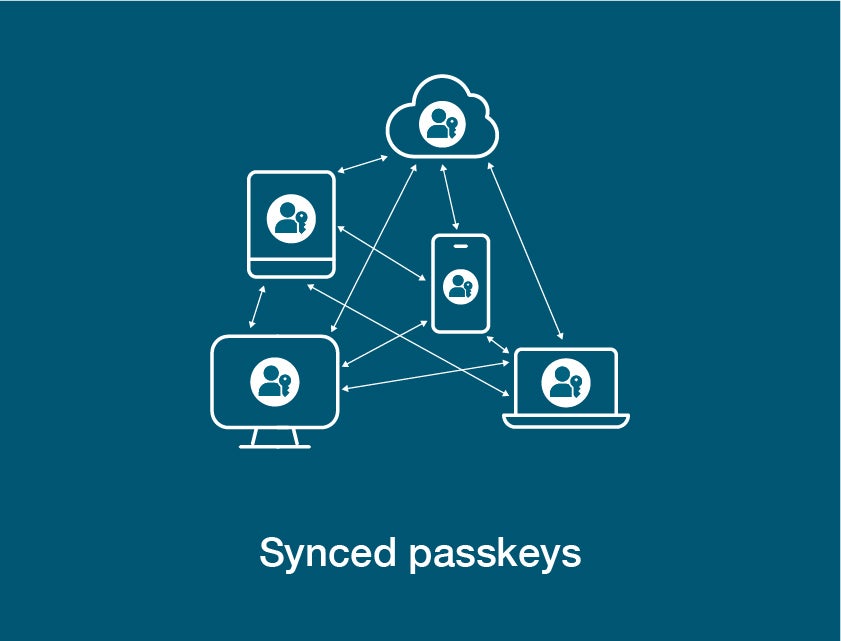
Passkeys are a kind of account credential. They can be stored on a device such as a computer, smartphone or, for better protection, a security key—or copied between devices.
Passkeys are meant to replace passwords and can be used by individuals and enterprises to enhance security for their online accounts, all with passwordless access.
Passkeys are available on all major operating systems, identity providers, and an ever-growing number of apps and websites.

Don’t know where to start?

Not all passkeys are created equal
Synced passkeys can be shared between devices offering lower assurance consumer-grade security.
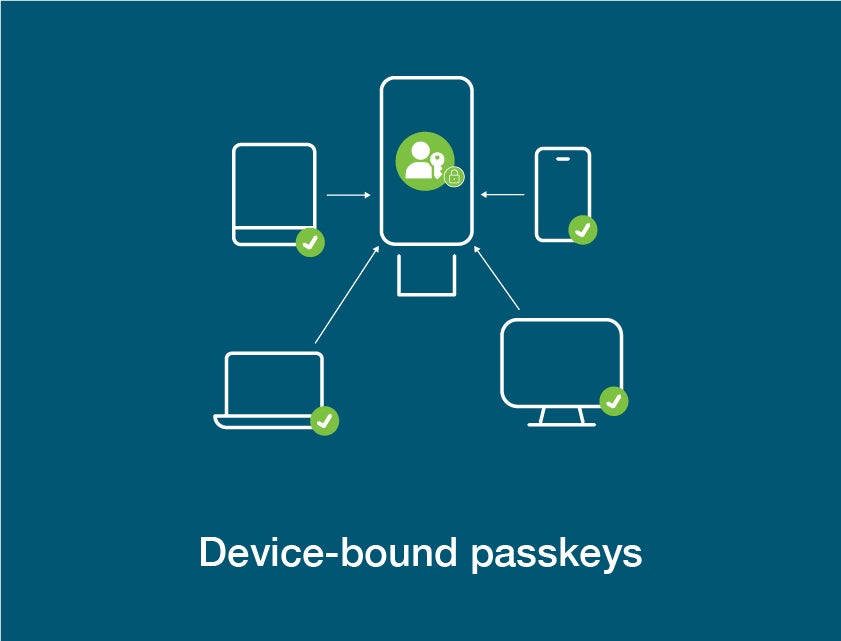
Device-bound passkeys are restricted to one device, offering higher assurance enterprise-grade security and stronger management capabilities.

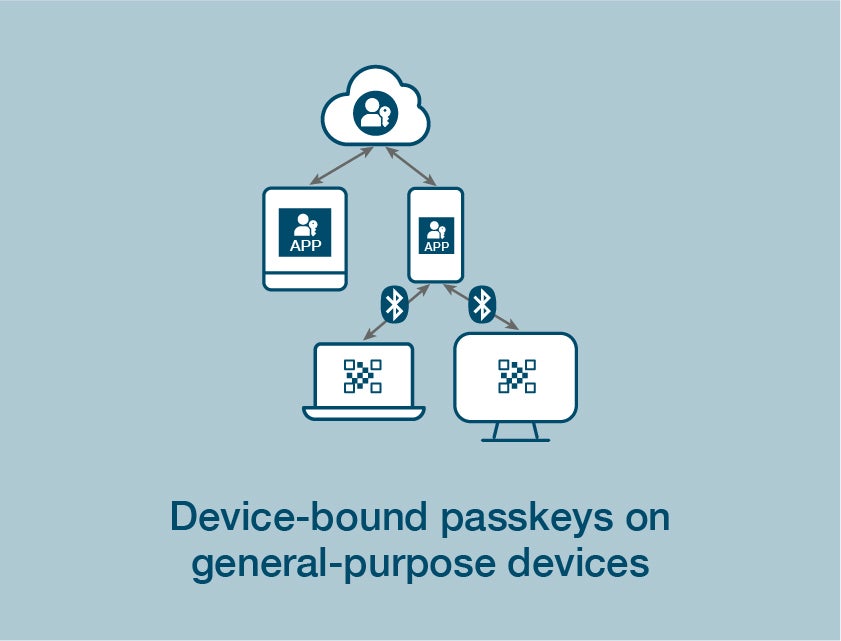
Considering synced passkeys?
Enterprises have options.
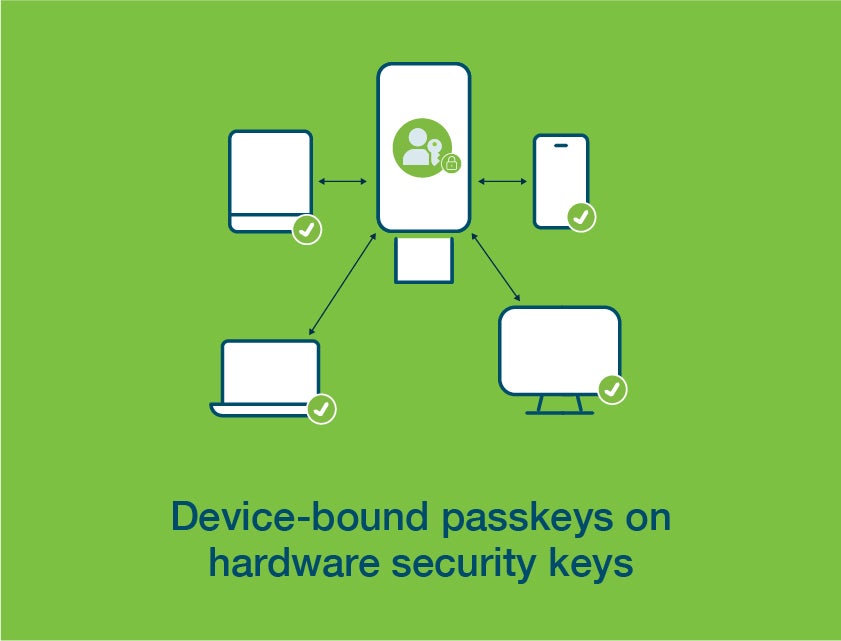
Device-bound passkeys are more secure, especially those that reside in hardware security keys, purpose built for strong security.
Passkeys for enterprises


Learn from an expert.
Deploying YubiKeys
YubiKeys allow enterprises to create phishing-resistant users, and offer high assurance authentication that moves with the user as they work across platforms and devices.

On-boarding registration

Credential recovery

Compliance audit
Ready to deploy? Download our guide to best practices.

Want to learn more from our experts?
What the Authn?
How passkeys offer a fresh take to authentication dilemmas

Passkeys for your enterprise?
Key considerations for success

Many roads to passwordless
How passkeys fit in the modern landscape

Enterprise passkey implementation
Key considerations and tradeoffs
Want to know more? Read our FAQs
Passwords are the root cause of 90% of cyber attacks according to the U.S. Cybersecurity and Infrastructure Security Agency. Simple passwords are easily guessed, while policies requiring complex passwords frustrate users and require IT support to help with frequent password resets. Users may be tempted to repeat passwords across multiple accounts. As a consequence, just one cracked or stolen password can threaten the entire online life of a user—and their organization.
That’s why Yubico, and our fellow members of the FIDO Alliance, created passkeys.
Passkeys are the new name for WebAuthn/FIDO2 credentials developed by the FIDO (Fast Identity Online) Alliance. The FIDO Alliance is an open industry association with a focused mission: reduce the world’s reliance on passwords. To accomplish this, the FIDO Alliance promotes the development of, use of, and compliance with standards for authentication and device attestation.
Passkeys use public key cryptography (also known as asymmetric cryptography): each passkey is a combination of a public key and a private key, both very large numbers that are linked together by complex mathematical formulas. The public key is stored by the site or application, while the private key is stored on the user’s device. When logging in, successful authentication relies on a validation and ‘handshake’ between the two keys, which solves many of the problems inherent with passwords.

Passkeys pair a public key with an unguessable private key which is never shared.

Every credential is tied to a real URL, which can be verified as legitimate or not.

Every credential is registered to a real human, blocking bots or other remote attacks.

A passkey is the credential itself, a digital file. An authenticator is where the passkey lives. For example, on a phone, laptop, hardware key or other device.
Yes! Passkeys are a form of multi-factor authentication; those factors include something you know, something you have, and something you are.
- Something you know: a PIN used to unlock the device.
- Something you have: the authenticator, whether that’s a security key or something embedded in a personal device/phone.
- Something you are: could include a fingerprint, scan of your face.
Hardware security keys enable enterprises to build trusted credential lifecycle management processes. Security keys enable enterprise users to register new devices, authenticate to their enterprise passkey providers and register other device-bound credentials (like Windows Hello or Okta Fastpass) because each user has a portable, phishing-resistant credential for simply and securely authenticating themselves during these processes. This removes risk from the help desk and enables enterprises to comply with stringent requirements across any industry.
The recently released YubiKey 5.7 firmware allows each YubiKey to store a total of 100 passkeys, offering more than enough storage not just for enterprise needs but for users’ personal accounts, while maintaining robust security standards.
Yes! It doesn’t have to be one or the other: A hybrid approach might suit an enterprise best in key scenarios, like using 3rd party passkey providers for low-risk apps/users or for temporary use during recovery scenarios. Also consider that using a pre-enrolled YubiKey provisioned and delivered to the end user creates the strong binding needed to bootstrap the setup of another type of device-bound passkey within a 3rd party passkey provider. This significantly raises the bar for security and usability creating a robust credential lifecycle strategy that an organization can build upon.
Need help deploying passkeys in your enterprise?

