Passwordless for enterprises
Implement secure, simple, scalable authentication today.
Passwords leave enterprises vulnerable to damaging cyber attacks, while employees are frustrated by increasingly complex password requirements, resulting in time and resources being wasted on password resets.
The true cost of passwords



That’s why enterprises are increasingly moving to creating phishing-resistant users and accelerating them to passwordless.
66% of enterprises are piloting, have deployed or are planning to deploy passwordless authentication within the next year4. Gartner predicts 50% of the workforce will be passwordless by 20255.
Why go passwordless?
Passwordless authentication offers improved security, a better user experience and lower long-term costs. Users aren’t required to create or enter a password at any time. Say goodbye to passwords, SMS codes and OTP apps.

No more password resets
No more time wasted logging in

No more account takeovers
WHITE PAPER
Going passwordless in a passkey age
Read the Yubico white paper to get real guidance on how enterprises can evaluate passwordless authentication options in the age of passkeys.
WATCH THE WEBINAR
Create phishing-resistant users and accelerate your enterprise to passwordless
Watch this webinar to learn how phishing-resistant users create phishing-resistant enterprises that can accelerate to enhanced security and operational efficiency, all within a modern passwordless environment.
YubiKeys make passwordless possible
Passwordless can be achieved using legacy Smart Card protocols, or modern FIDO2 / Passkey authentication secured by PIN or biometric identification.
The multi-protocol YubiKey offers total flexibility, and can store up to 100 passkey credentials.
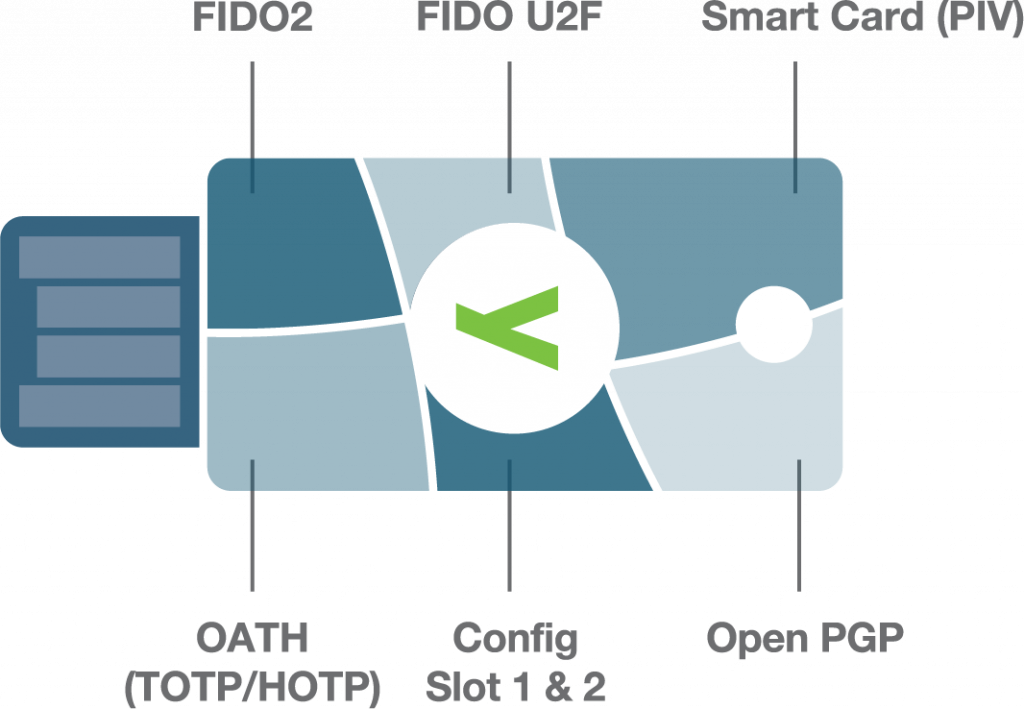
Choose the passwordless login flow that suits your needs.
Unlike passwords, which are shared across networks and highly vulnerable to phishing, PINs are locally stored and only used to unlock a specific device.



“The biggest benefit that Hyatt is going to receive from deploying YubiKeys is to be able to get rid of passwords in our environment.”
Curious about the YubiKey?
Implementing passwordless at scale just got easier. Introducing Yubico FIDO Pre-reg
Moving an entire enterprise to passwordless is always worthwhile, but can place a burden on IT teams, who may have to manually register and then deliver authenticators to a distributed workforce. End users can be frustrated by complicated self-service registration processes.
To maximize adoption and make life easier for IT teams and end users, organizations should be able to enable new and existing users to go passwordless in just minutes. Strong registration and account recovery process limit attack vectors for social engineering.
What is Yubico FIDO Pre-reg?
A first in the industry, our turnkey activation service eliminates manual activation. YubiKeys
are delivered to end users and activated in a simple two-step online process.
- Saves time and cost for IT department
- Accelerates security and productivity for end users
- Strengthens registration and account recovery processes
Knowing the right YubiKeys are in the right hands helps ensure you create an enterprise of phishing-resistant users.
Yubico FIDO Pre-reg is available exclusively with the YubiKey as a Service program and currently limited to Okta customers only.
YubiKey as a Service: peace of mind and flexibility for less than a cup of coffee per user/month
Simplify purchase and support while also providing financial benefits. Estimate your potential savings with a subscription as compared to a one-time purchasing model.
Let us help you create a custom plan for your business!
Want to fast-track your enterprise to passwordless?
- Identity Week, (accessed May 10, 2024)
https://identityweek.net/mastercard-80-of-data-breaches-linked-to-passwords/,
- IBM, 2023 Cost of Data Breach Report, (July 24, 2023), https://www.ibm.com/reports/data-breach
- Including staffing and infrastructure. Forrester Research, Inc, Optimize User Experience With Passwordless Authentication, (March 2, 2020), https://www.forrester.com/report/optimize-user-experience-with-passwordless-authentication/RES158717.
- S&P Global Market Intelligence, With Security Breaches Mounting, Now Is the Time To Move From Legacy MFA to Modern, Phishing-Resistant MFA, 2023
- David Jones, Microsoft, Apple and Google double down on FIDO passwordless standard, (May 5, 2022), https://www.cybersecuritydive.com/news/microsoft-apple-google-fido-passwordless/623273/
