Securing SMBs with phishing-resistant MFA
Protecting small and medium businesses against cyber attacks and keeping the innovation engine for the economy safe.
Get started with phishing-resistant YubiKey
MFA for your favorite services and applications
Small and medium-sized businesses underestimate
the risk of a cybersecurity breach

1 in 3 breaches involved an SMB.
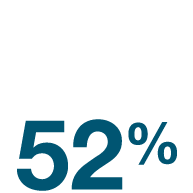
52% of SMBs experienced at least one cyberattack in the last year. Of them, 10% experienced more than 10 cyberattacks.

40% do not have a comprehensive and up-to-date cybersecurity incident response plan.
State of Global Enterprise Authentication Survey
Yubico’s exclusive research asks employees around the world how they authenticate. Discover the common mistakes that leave organizations vulnerable to attacks, hear from decision makers about the cybersecurity issues that keep them up at night, and learn how and why modern enterprises are embracing phishing-resistant MFA.

Evolving cyber threat and regulatory landscape
requires stronger security

Growth in cybercrime
During the Covid-19 health crisis, cybercrimes have gone up by as much as 300%. And public incidents of cybersecurity breaches have been in the news regularly, with affected organizations experiencing massive reputational and financial losses. According to a recent survey, 72% of SMBs today are more concerned about cybersecurity than a year ago, with the top 3 cyber threats being ransomware, phishing, and malware.

Stringent compliance mandates
With the recent number of attacks that have had significant impact on critical systems, a new Executive Order on improving the nation’s cybersecurity was released on May 12, 2021, covering key areas needed to protect critical digital infrastructures. The EO affects many organizations, both in the public and private sector, that work with the government. While the order covers a number of topics, implementing phishing-resistant multi-factor authentication (MFA) as part of deploying a Zero Trust Architecture and securing the software supply chain are of the highest importance.
SMBs are the lifeblood of the economy and a critical part of the overall supply chain and partner ecosystem of larger organizations. Now is the time for these businesses to move towards stronger forms of user authentication, beyond passwords and mobile apps, in order to stay secure and be viewed as a trusted organization and partner.
The critical need for phishing-resistant MFA

The trouble with passwords
Passwords are easy to create and use, offering access to enterprise systems and applications. However, they are increasingly the cause of costly security breaches. In fact, weak passwords or the use of lost or stolen credentials are responsible for more than 80% of breaches in 2020. Stolen credentials not only allow malicious actors to impersonate a compromised user, but can also be used to gain additional credentials and information.

Modern MFA addresses modern threats
Authentication using only a username and password is single-factor authentication. By adding an additional, physical layer of MFA with security keys, SMBs can significantly reduce cyber risks.
MFA raises the bar for security by requiring a user to offer 2 out of 3 factors to verify their identity:
- Something you know
(e.g. username and password) - Something you have
(e.g. YubiKey security key or token) - Something you are
(e.g. biometric – fingerprint, facial recognition, iris scan)
The bar is simply too low with passwords. Even legacy MFA methods, such as SMS or mobile authentication, have all been proven to be highly vulnerable to phishing. Phishing-resistant MFA is the modern and effective approach to keeping your hard work, brand image, and business protected.
Jumpstart authentication security best practices
Watch the webinar
Best Practices to Secure SMBs in an Evolving Cyberthreat Landscape

Think legacy MFA like mobile authentication is good enough? Think again.

Read the white paper
Avoid the pitfalls of legacy MFA that’s quickly falling behind.
Limited IT staff or cybersecurity training?
The YubiKey delivers peace of mind out-of-the-box with an intuitive experience

Stop account takeovers
Get strong security in minutes with the YubiKey, a hardware security key that provides phishing-resistant two-factor, multi-factor, and passwordless authentication. Move beyond passwords with a solution that’s been proven to stop account takeovers in their tracks and mitigate risks tied to growing ransomware threats. With the YubiKey, you can secure your business, become a trusted part of the supply chain, and experience peace of mind.

Experience fast and easy account login
Using a YubiKey is very simple. To get started the user simply needs to register their YubiKey with the applications or services they wish to secure. Just enter a PIN or password and touch or tap your YubiKey, and you’re in. Reduce downtime due to password-related account lockouts and deliver an intuitive experience to your users for wider security adoption and greater user satisfaction.

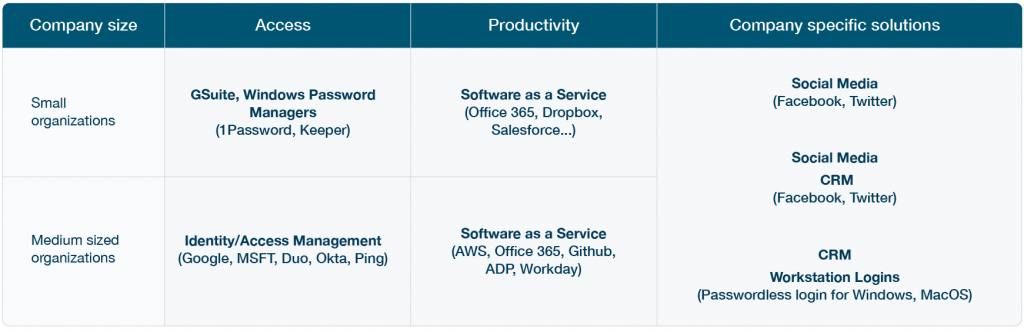
Secure all the systems you use to stay productive
YubiKeys work seamlessly across on-premises or cloud environments and offer secure access to:
- Email/webmail
- Corporate virtual private networks (VPNs)
- Internet-facing systems
- Cloud solutions
- Network devices
- and much more
One key can work across hundreds of applications and systems and YubiKeys share secrets between registered services, store no data and require no cellular connectivity. Work offline anytime, anywhere and experience always-on security keeping user identities and the business safe.
Looking to secure O365, GSuite, Salesforce and other cloud services? YubiKeys have you covered.
How the YubiKey works
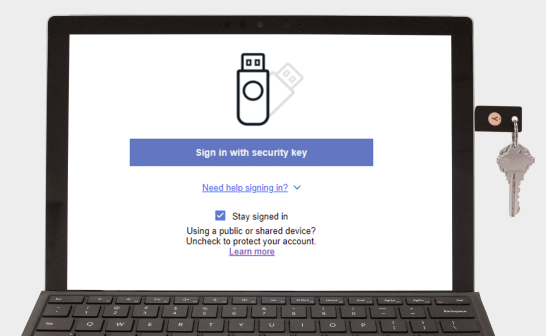
Register your YubiKey
To use the YubiKey, go to the Security Settings of a supported service and select “Add Security Key”.

Insert YubiKey & touch
On a computer, insert the YubiKey into a USB-port and touch the YubiKey to verify you are human and not a remote hacker.

Tap YubiKey to device
Tap the YubiKey on NFC enabled devices. Once registered, many services will not require the key after first login – it just works!
Get started

Find the right YubiKey
Contact our sales team for a personalized assessment of your company’s needs.













