Modern security for your supply chain
Secure users, products, and 3rd parties at scale against phishing attacks and account takeovers
Protect your supply chain with Zero Trust security
Today’s supply chain includes all the products and services acquired to support an organization, including product parts, hardware, software, and code, as well as the physical and digital interactions between people, applications, and processes. A supply chain that is vulnerable to cyberattacks opens up enterprises to significant operational disruptions, financial loss, damage to brand, product integrity, safety issues, and the loss of intellectual property (IP).
With multiple moving parts along the supply chain, it’s essential to consider deploying a Zero Trust framework—where no one and no thing is trusted, and an explicit trust decision is made for each user, product, service, and interaction before access is granted. Modern, strong authentication based on phishing-resistant public key cryptography is a core foundation of Zero Trust, and can be leveraged by organizations to secure users, products and third parties against modern cyber threats.
Protecting the supply chain with highest-assurance security
Learn authentication best practices in securing supply chain integrity.
Ensure integrity of your software supply chain
Whether you use code that’s been developed by internal teams or from external sources, it is important to always deploy phishing-resistant multi-factor authentication (MFA) for code access and implement trusted code-signing.
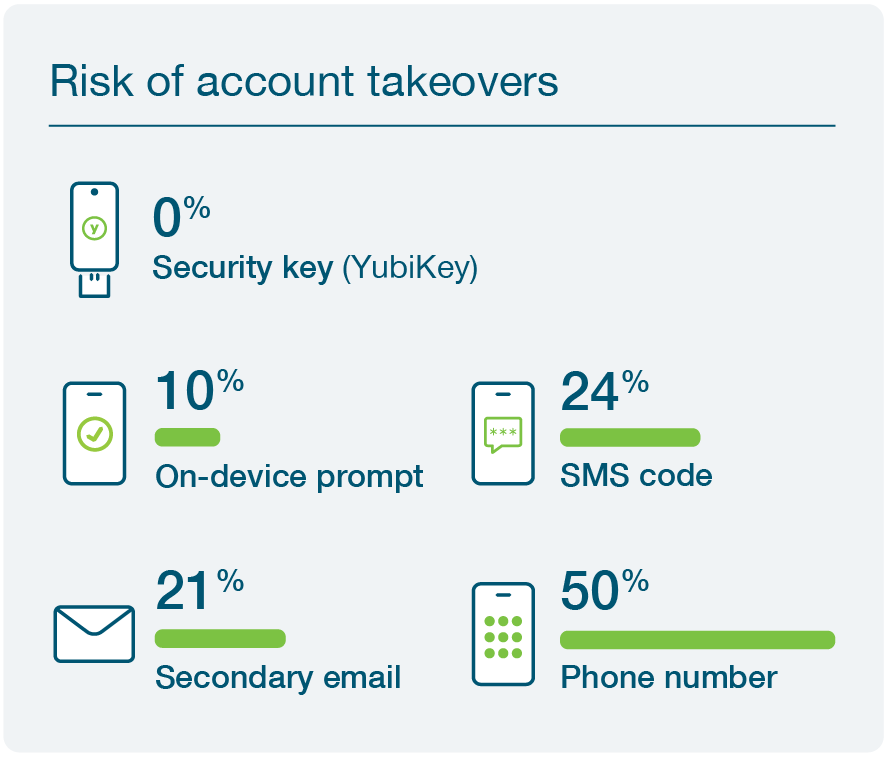
Not all forms of MFA are created equal. Most basic forms of MFA, such as SMS and mobile-based authenticators, are perishable and highly vulnerable to MiTM threats. These methods do not achieve the strongest levels of phishing defense delivered by purpose-built hardware security keys such as the YubiKey from Yubico. So if your users are using these legacy forms to verify their identity as part of your code management practices, you may be compromising your Zero Trust promise. The YubiKey offers phishing-resistant two-factor, multi-factor, and passwordless authentication at scale, ensuring only trusted and validated users have access to critical code repositories
YubiKeys ensure that only authorized people have access to PII data and critical systems. They integrate seamlessly with existing IAM solutions such as Microsoft, Okta, Duo, and Ping, and provide secure authentication for hundreds of applications and services, eliminating any rip or replace of existing solutions. Users get protected in minutes right out-of-the-box.

Ensure integrity of IP and product parts
It is crucial to ensure that all components involved in an end-to-end process are authentic, to avoid unsolicited replication and theft and ensure quality assurance. The traditional approach to protect intellectual property (IP) and prevent counterfeiting involves the use of digital cryptographic signing keys and encryption, with keys stored in a hardware security module (HSM). However, conventional rack-mounted and card-based HSM devices are large and expensive, making them impractical for example on the assembly floor or for IoT devices.
Yubico offers the ultra-portable and low-cost YubiHSM 2, the world’s smallest HSM in a nano form factor. The YubiHSM 2 enables secure, tamper-resistant key storage and operations and can be applied to any process where secrets and the authenticity of components needs to be managed across robotic assembly lines, applications, and IoT devices.

Secure employee and third party access to systems and data
The YubiKey provides phishing-resistant MFA at scale across the supply chain, helping your organization and suppliers implement robust, easy-to-use authentication for any user who has upstream access to the network or at critical IP handoffs.
A single YubiKey works across multiple devices including desktops, laptops, mobile, tablets, notebooks, and shared workstations, enabling users to utilize the same key as they navigate between devices, and helping you deploy phishing-resistant MFA at scale. YubiKeys are also easily re-programmed, making them suitable for temporary workers, and enable self-service password resets, significantly reducing IT support costs.

Meet evolving compliance regulations
The Colonial Pipeline and SolarWinds attacks highlighted supply chain vulnerabilities across critical infrastructure and top federal agencies. In response to these attacks the White House issued Executive Order (EO) 14028, Improving the Nation’s Cybersecurity, outlining new expectations & guidelines for Zero Trust and phishing-resistant multi-factor authentication (MFA) for federal agencies—as well as their suppliers and partners.
Yubico ensures that your organization meets evolving compliance regulations with phishing-resistant security. Both the YubiKey and YubiHSM 2 come in FIPS 140-2 validated form factors, and the YubiKey meets NIST SP 800-63-3 Authenticator Assurance Level (AAL) 3 requirements.
Learn more how Yubico can help secure your supply chain
Risk reduction, business growth, and efficiency enabled by YubiKeys
A recent Forrester Consulting Total Economic Impact™ (TEI) study commissioned by Yubico found that a composite organization representative of interviewed customers who use YubiKeys reduced risk of successful phishing and credential theft attacks by 99.9%, saw a drop in password-related helpdesk tickets by 75%, and experienced a 203% 3-year ROI with YubiKeys.
BUT…. all organizations are different. Enter your own company data to create a custom Dynamic TEI study and instantly see how Yubico’s solutions can help your organization!
YubiKey as a Service: peace of mind and flexibility for less than a cup of coffee per user/month
Simplify purchase and support while also providing financial benefits. Estimate your potential savings with a subscription as compared to a one-time purchasing model.
Let us help you create a custom plan for your business!

Get started

Find the right YubiKey
Contact our sales team for a personalized assessment of your company’s needs.

Get protected today
Browse our online store today and buy the right YubiKey for you.


