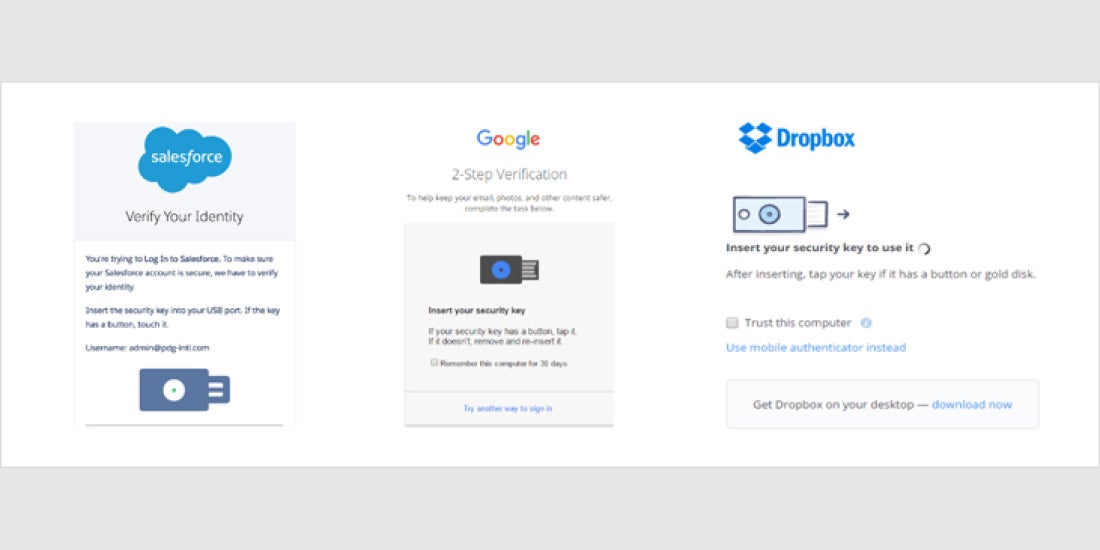
Now more than ever, security must be built into everything. By leveraging open standards, instead of building security protocols from the ground up, organizations can provide strong authentication faster than ever before.
We created the Universal 2nd Factor (U2F) protocol together with Google several years ago and offered it the world for free along with open source clients and server libraries. After years of working with the majority of service providers who have made support for the U2F standard, we have learned a lot about what makes a successful FIDO U2F implementation.
Here are 3 of the top things to consider when implementing FIDO U2F with your service:
1. Backup and Recovery
Just as your users often forget their passwords today, it is possible that the methods they use for two-factor authentication will not always be available. Phones run out of battery, can be lost, stolen, or broken. Hardware-backed keys, such as the YubiKey, and other tokens like RSA SecurID, can be left at home, lost, or stolen. We highly recommend encouraging users to register at least two FIDO U2F security keys for backup, as this is the most secure and affordable option available. Other methods, such as backup codes and email, have their weaknesses and usability challenges.
You need to provide a backup two-factor method but bear in mind that security is never stronger than its weakest link. Some of the most commonly-used backup options are still susceptible to man-in-the-middle and phishing attacks. SMS, for instance, is no longer recommended by the National Institute of Standards and Technology (NIST), section 5.1.3.2 in the latest draft of its Digital Authentication Guidelines.
Providing flexibility for users to select various backup options will substantially reduce the need to perform a full account recovery, which often involves the user calling your customer service help desk. A new technique used by leading services is social recovery (asking a number of friends to authorize the recovery). We do not recommend email as a recovery method since it is common for the user seeking recovery to have lost or forgotten their email credentials as well.
2. Mobile User Experience
If your service is accessible on mobile devices, it is imperative that you take the mobile user experience into account.
Today, both Google and Dropbox services require verification codes as the second factor when accessing from a mobile device. Google will also generate a unique app password for each native application for account access. For example, Google sets a specific password for native apps such as Mail on an iPhone or Mac, or Outlook on a Windows PC when accessing Gmail.
Soon, services will be able to use two wireless transport methods, Near Field Communications (NFC) and Bluetooth Low Energy (BLE), for U2F authentication on mobile devices. Here are some considerations for each of them.
NFC – At this time, we are most confident in NFC as a secure, and reliable contactless U2F communication method. Android mobile devices featuring NFC will soon allow users to authenticate with a tap of an NFC-capable U2F security key as the second factor. However, for iOS devices, Apple only recently added NFC capabilities to their mobile platform but continues to restrict the NFC stack to their applications, such as Apple Pay. Therefore, external U2F authenticators will not work on all mobile devices over NFC.
BLE – For iOS, BLE is a transport option, but the user experience is not optimal. BLE-capable U2F security keys must be paired with each mobile device before registration can occur. This additional pairing process adds friction for users as it is made more difficult in high-density environments where there are many Bluetooth devices in a small area. BLE-capable security keys also require batteries, bringing with them the possibility of running out of power and resulting in shipping and handling regulations as it pertains to dangerous and hazardous goods.
Alternatively, the FIDO ecosystem is currently exploring using a U2F USB security key in conjunction with a mobile app for accessing services on mobile devices. This approach is similar to what is today deployed by several European online services, which combine smart card devices with mobile applications. For the highest level of security, some of these services require a user to first register a smart card device with the service from a computer before allowing the user to then download and use the mobile app. In this scenario, we recommend leveraging U2F device attestation to identify the kind of U2F authenticator during registration (hardware, software, certified, and so on), and implementing assurance policies.
3. Support
You are likely thinking about how the first two considerations will impact your support team. (If you are not, then you should be!) Case studies show dramatic decreases in support costs after implementing U2F security keys. The keys to success are having clear, concise documentation for self-help, and allowing your users to provision more than one U2F security key. For instance, when Google switched employees to FIDO U2F Security Keys by Yubico, support calls and costs were cut in half compared to using mobile phone authenticators. An important part of that success is also due to the user’s ability to register backup keys.
In conclusion, you are not alone in your journey to implement FIDO U2F. More than a dozen organizations (both consumer-facing and B2B) have already rolled it out to their end-users, and countless others are in the process today. We are committed to the success of U2F and will continue to share best practices. And we applaud you for considering FIDO U2F for your service!