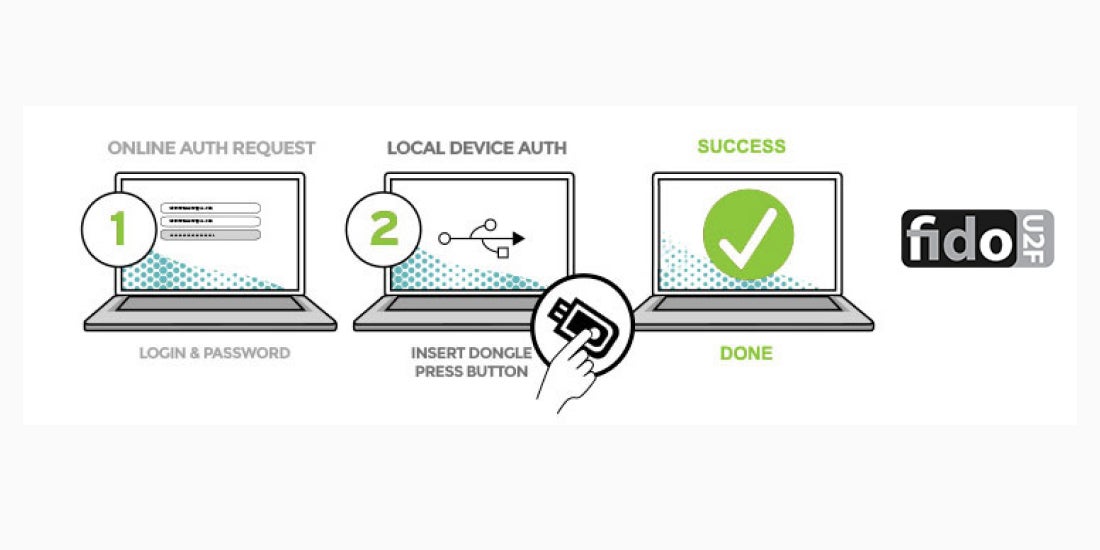
Key words often associated with two-factor authentication focus on simplicity, privacy, and security. Those words, however, are broad terms that need definition in order for consumers and enterprises to form opinions and make educated buying choices.
FIDO Universal Second Factor (U2F) is no different, so Google recently published a research paper titled “Security Keys: Practical Cryptographic Second Factors for the Modern Web” to quantify the benefits the internet giant found in using U2F-based two-factor authentication.
The paper outlines Google’s use of FIDO U2F-based Security Keys, manufactured by Yubico, to harden security, improve user satisfaction, and cut support costs.
This data is far from anecdotal. It represents two years of research. The results, as compared to other two-factor authentication schemes tested by Google, showed the Security Key is simple to implement and deploy, easy to use, preserves privacy, and is secure against attackers.
Here are some eye-opening conclusions from Google’s research on its Security Key rollout:.
- Users reduced, by nearly two-thirds, the time to authenticate with a Security Key as opposed to an OTP via SMS. Most of that time is based on the efficiency of the user since authentication executes in milliseconds.
- In Google’s rollout, authentication failures fell to zero. The company’s support department estimates the switch from OTP tokens to Security Keys saved thousands of hours per year in cost. These efficiencies allowed Google to give each employee two Security Keys and still realize overall cost reductions.
- Security Keys met other Google requirements that mandated simple APIs for developers, no user tracking, no identifiable user information on token as well as protection against password reuse, phishing and man-in-the-middle attacks.
To date, the devices have been deployed to 50,000 employees, and Google reports “our users have been very happy with the switch: we received many instances of unsolicited positive feedback.”
Other technologies referenced and reviewed by Google included OTPs, mobile phones, smart cards, TLS client certificates, and national ID cards. Their research includes a comparison chart of second-factor options based on a respected usability framework published in 2012 by another group of researchers led by Joseph Bonneau, currently a researcher at the Applied Crypto Group at Stanford University.
The paper also spends a significant number of pages describing the technical underpinnings of Security Keys and how they relate to the larger concepts of simplicity, privacy and security.
Research conclusions point to immediate gain from Security Key deployments, but the findings are being offered as a starting point. “We hope this paper serves as an academic foundation to study and improve Security Keys going forward,” Google wrote.
In addition to those stats, Google has publicly presented other figures that compare Google Authenticator and Security Key. Google studies show the Security Key login process was four times faster compared to Google Authenticator (their mobile authentication app), and that use of U2F and public key crypto results in significant fraud reduction.