Strong authentication practices are based on validating a number of authentication factors to a relying party (RP) or identity provider (IDP) to prove you are who the RP expects. Examples of relying parties could be Dropbox or Salesforce. Identity providers, who can also be a relying party that interacts with the authenticator, include Microsoft Entra ID, Okta, Duo Security and Ping Identity, amongst many others.
The factors commonly used are something you know, something you have, or something you are. Providing two of these factors provides a higher confidence of the user than just one. Two factor authentication (2FA) has become the standard practice and a requirement in many industries. The term multi-factor authentication (MFA) is also commonly used to describe the process of using more than one authentication factor for authentication.
Passwords, something you know, have traditionally been used to provide the initial “first” factor in a MFA flow. That MFA flow requires a second authentication, typically something you have, that may involve additional authentication vendors. The RP validates each authentication factor before allowing access.
Secure passwordless login ushers in a new way of thinking
Modern strong authentication where passwords are no longer used, adheres to MFA principles but the process is different. It’s important to understand these differences to fully protect your systems.
Passwordless authentication, based on smart cards or FIDO2, fundamentally changes how 2FA is processed. In a passwordless model, the validation of the first factor and second factor shifts solely to the authenticator. Typically the first factor is physical possession of the authenticator itself, and the second factor is the PIN or a biometric validation to unlock the authenticator and perform the cryptographic operation.
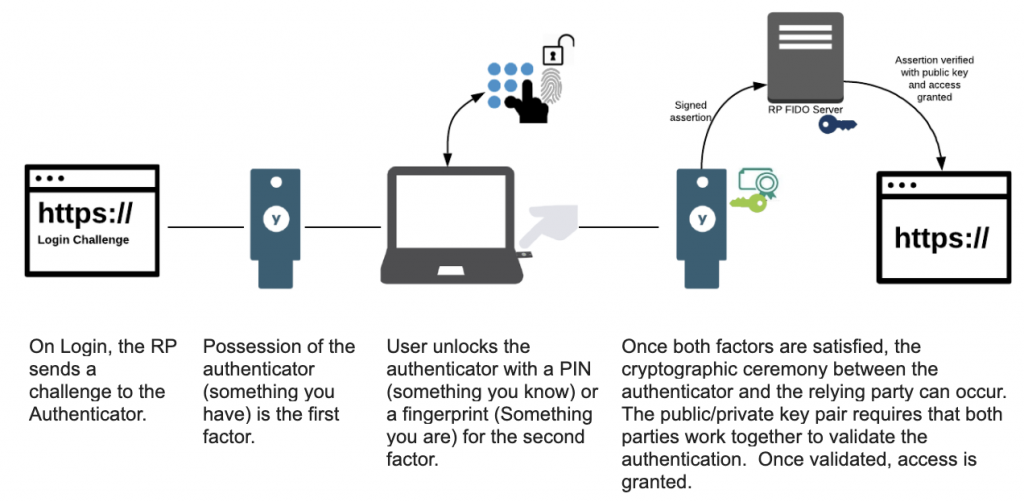
From a FIDO perspective, the authenticator controls the private key. The authenticator can be the smartphone’s secure enclave or trust zone, a computer’s TPM, or a YubiKey’s secure element. It is a vitally important job of the authenticator to ensure the private key is secured so it cannot be stolen or cloned.
Ensuring 2FA is being used and the authenticator is properly storing private key material
Given that passwordless authentication shifts much of the authentication process to the authenticator, how do we know that 2FA is actually being used and that the authenticator is properly storing the private key material?
With the PIV smart card standard, the second factor is via the PIN that unlocks the smart card. FIDO2 authentication can optionally be used as a multi-factor cryptographic authenticator. Within FIDO2, user verification (UV) serves to ensure that the person authenticating to a service is in fact who they say they are for the purposes of the service and is in control of the private key credential. The user is authorized to verify their identity by entering a PIN or a biometric, like a fingerprint via a prompt on the client. The authenticator performs user verification and responds to the RP that UV was successful in a way that is cryptographically verifiable by the RP. When using a FIDO2 credential for the passwordless flow, UV needs to be set to “REQUIRED” and the IDP has to check for and enforce it.
User Verification provides an important authentication factor but as mentioned above, the relying party does not have any visibility into the user verification process. The authenticator validates the user and informs the relying party of the UV action. The RP relies on the authenticator to properly handle the UV processing and return the appropriate response. While this reduces the overall MFA complexity, the relying party needs to trust that the authenticator is doing the authentication process securely. Following Zero Trust principles, how can the authenticator be verified as trustworthy?
What it means for an authenticator to be trustworthy
In order to understand the security properties of an authenticator, relying parties should check device attestation statements. Attestation enables each relying party to use a cryptographically verified chain of trust from the device’s manufacturer so that access decisions can be made based on a risk profile. Attestation information should be captured so current and future decisions can be made, up to and including blocking, if issues arise. The attestation keys are set at manufacturing time and cannot be altered or exported. Attestation provides assurance of the properties of the authenticator as stated by the manufacturer. Attestation is a powerful tool to provide additional assurance that the authenticator is a valid authentication product from a trusted manufacturer. Not all authenticator device manufacturers support attestation across the different authentication protocols. In addition, each platform that has a built-in authenticator may handle attestation differently. It is important to understand how each device and manufacturer implements attestation to take advantage of this security control. Yubico has clear guidance on how to implement attestation for the protocols that generate asymmetric keypairs on the device such as WebAuthn, PIV, and PGP.
The authenticator needs to ensure that processes it performs are secure and key material cannot be copied off the device. If it can be, a cloned authenticator could be developed and used to authenticate. The authenticator manufacturer needs to adhere to security best practices to ensure credentials cannot be extracted. You can learn more about how Yubico performs secure manufacturing here.
Passwordless Authentication Summary
From the beginning of computers, something you know (a password) has been the primary factor and our mindset has been around securing what you know. That is no longer the case when we transition to a passwordless world. The industry has shifted to something you have as being the most important factor whether it be your PC, phone, or YubiKey. The shift has occurred due to the fact that something you have is usually harder to compromise than something you know. Additionally, the industry has matured to support hardware backed authentication that works natively within browsers and operating systems.
But when the industry shifts so do the attackers. Hardware backed passwordless authentication is significantly more secure than legacy forms of authentication, but security professionals still need to be aware of the potential attack vectors. Whether a company realizes it or not, something the user has is the most important factor, and the other factors are designed to secure what you have. As you implement passwordless authentication, security controls and models need to focus on this reality compared to just relying on traditional approaches that are no longer sufficient.
Read Yubico’s Bridge to Passwordless series to learn more about how to plan and execute a passwordless strategy.





