Archive
Lorem ipsum dolor sit amet
-
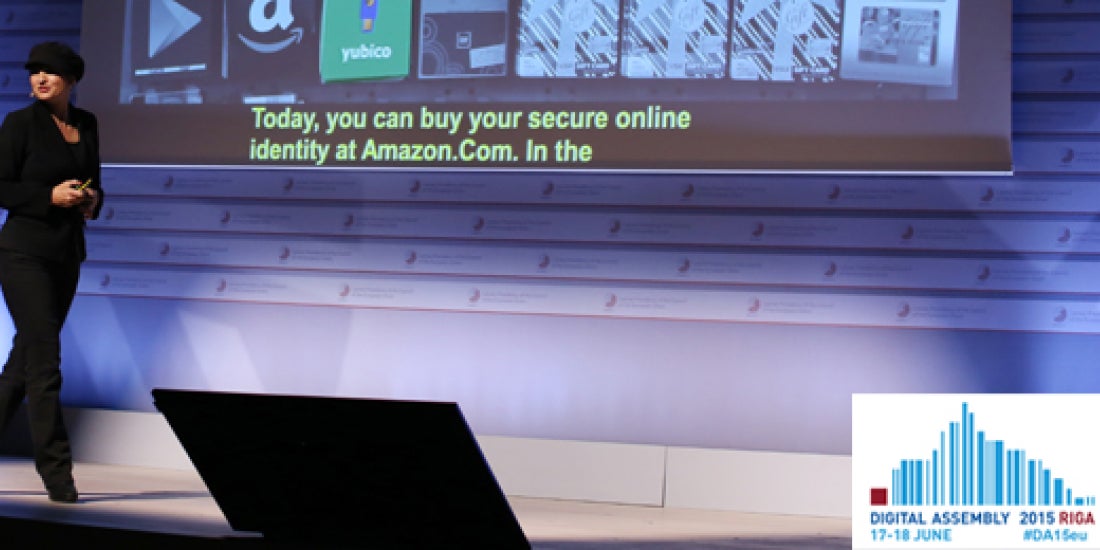 Yubico CEO to EU: Open Standards Nurture Trust
Yubico CEO to EU: Open Standards Nurture TrustTrust has to be a cornerstone in order to protect the online identities of 500 million people doing business across borders, Yubico’s CEO and Founder, Stina Ehrensvard, told an exclusive crowd of 500 EU digital policy makers and industry representatives last week at Digital Assembly 2015 in Riga, Latvia. She held up a single YubiKey […]
Read more -
 Cloud ID Summit Sharpens Focus on Future of IAM Standards
Cloud ID Summit Sharpens Focus on Future of IAM StandardsOne common theme across the talks at last week’s Cloud Identity Summit (CIS) revealed a desire to simplify and unify existing identity and access management (IAM) technologies and standards to build a pragmatic approach to modern identity. For years, authentication, authorization, single sign-on (SSO), federation, governance, risk, compliance, standards, etc., etc. have all been pointing […]
Read more -
 Ode to the value of Backup YubiKey(s)
Ode to the value of Backup YubiKey(s)A few weeks ago, I was in my hotel and reached into my pocket to get my YubiKey. Without it, I can’t log into certain email, CMS or other systems without going through an involved IT administrative process. The key was gone. That is an instantaneous bad feeling, wiped away only by the backup YubiKey […]
Read more -
 YubiKeys Earn FIDO Certified Label
YubiKeys Earn FIDO Certified LabelInteroperability is king and today the FIDO Alliance announced its FIDO Certified program and a list of 31 products that have passed conformance and interoperability testing. The three YubiKeys that support FIDO’s Universal 2nd Factor (U2F) protocol – NEO, Edge and Security Key – are now certified and part of this important maturation in FIDO’s design. […]
Read more -
 An Edge over the Bad Guys
An Edge over the Bad GuysThe one thing end-users don’t seem to have over hackers these days is an edge. Yubico is changing that. Today, we introduce a new key we’ve dubbed the YubiKey Edge. The goal is a cost-effective key with a collection of second-factor authentication options that guard against attacks on your accounts either via malware, phishing and other […]
Read more -
 YubiKey, YubiHSM: Secret Weapons to Guard Secrets
YubiKey, YubiHSM: Secret Weapons to Guard SecretsU.S. intelligence officials in 2013 said they planned to significantly reduce the number of individuals within their network with system administrator privileges. Those privileges gave administrators rights to view and move around any document. “U.S. intelligence has invited so many people into the secret realm,” an official told NBC News, that it left the organization overly exposed to threats […]
Read more -
 Yubikey and the Emerging World of Wireless Mobile Authentication
Yubikey and the Emerging World of Wireless Mobile AuthenticationWireless has become the de-facto connecting point for consumers today and even among enterprises, where employees expect to leave behind desktop Ethernet connections for wireless connectivity in board rooms, conference rooms and common areas. Apple makes this point emphatically with its new MacBook where the message is everything should be done without wires via technology […]
Read more -
 YubiKey’s Hollywood Cameo Trips up Bad Guys
YubiKey’s Hollywood Cameo Trips up Bad GuysThe YubiKey made it into Hollywood’s spotlight last weekend, taking on a plot-turning cameo appearance in the movie Blackhat. (Cue the suspenseful music). When it was all said and done, the YubiKey showed some of the power of two-factor authentication – not in terms of fingering (pun intended) the suspect, but narrowing the field of potential […]
Read more -
 FIDO U2F Ecosystem Coming Alive
FIDO U2F Ecosystem Coming AliveUpdate: New entries added to Enterprise Software list; new section, Governments, added; April 13, 2016 FIDO U2F (Universal 2nd Factor) is, as the name implies, a universal protocol that supports a wide range of modalities and use cases. Many people forget this fact given the current popularity of the USB form factor. But evidence is mounting including biometric, software, […]
Read more -
 Authentication: More Maturity, Choices in 2015
Authentication: More Maturity, Choices in 2015The past 12 months have been stressful given breaches and privacy violations and countries blocking all or part of their citizens’ access to the Internet (which by the way turned 25 in May). As the calendar turns to 2015, there is unprecedented power and pitfalls harnessed in computing devices and digital life. All this connectivity puts […]
Read more
