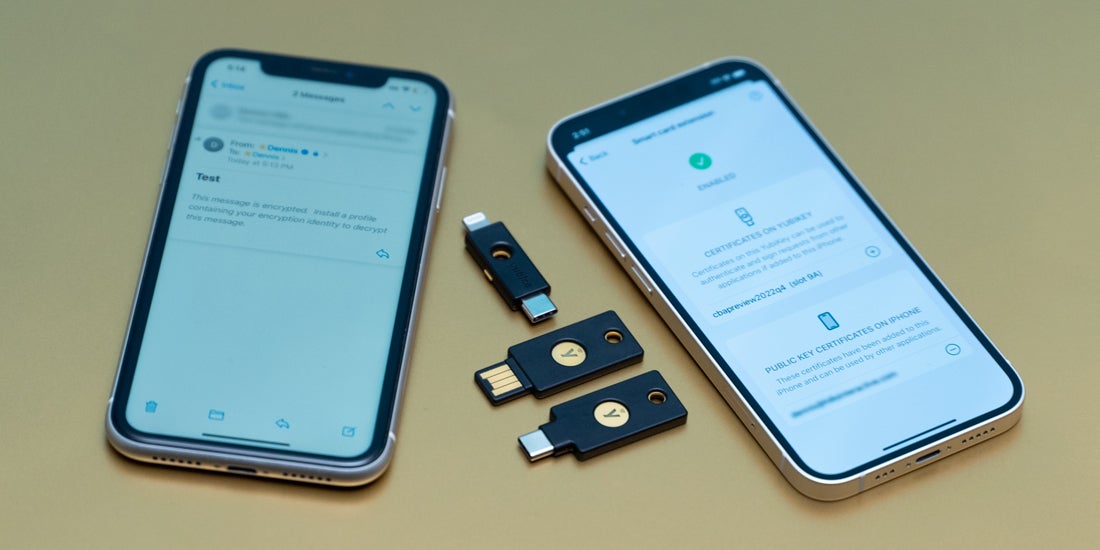
In a recent post we discussed the concept of using a YubiKey as a smart card on iOS. Now that we’ve outlined the overall concept, we’d like to expand by exploring the unlocked use cases for using a smart card for authentication, creating digital signatures, and decrypting messages and documents on Apple iPhones and iPads.
Certificates and smart cards have been around for decades through various hardware and software solutions for desktop, but now we are seeing a huge shift to mobile as these proven strong cryptographic technologies are accessible to anyone with an iOS device and a YubiKey.
In this blog, we’ll uncover the driving forces behind the developing ecosystem contributing to the unlocking of PIV smart card use cases on mobile. We’ll also explain those use cases for authentication, digital signatures, and decryption.
A developing ecosystem
Interacting with a smart card on an iOS device requires four main components:
- Apple’s native support for smart cards on iPhone and iPad running iOS/iPadOS 15
- PIV Middleware app, such as the Yubico Authenticator app for iOS
- A PIV-compatible smart card, such as the YubiKey 5 Series or YubiKey FIPS Series key supporting higher assurance derived credential requirements
- PIV credentials residing on a YubiKey
Let’s go over each component and their role in unlocking common smart card use cases previously only available on desktop.
1. Apple’s Native Support for Smart Cards and Persistent Tokens
Apple’s native support for smart cards enables any PIV-compatible smart card to interact with an iPhone without any additional hardware readers or software. As of iOS 14, mobile users can access certificates, keys, and identities stored on a smart card as if they were part of the iOS Keychain. This means that a user can securely store their credentials (certificates + associated private keys) on a YubiKey as a smart card without ever exporting their private key to the iOS device.
With extended support for iOS CryptoTokenKit, developers can create solutions allowing users to interact with the YubiKey’s PIV module over NFC or a Lightning connector for certificate-based authentication using the Safari browser, sign outbound email using the native iOS mail app, or decrypt email messages or documents.
Why is this significant? Prior to iOS 14, certificate-based authentication, digital signatures, or decryption was only possible by importing the entire identity (certificate + private key) onto the iOS device. Unless your identity is generated and stored in the device’s secure enclave, there’s always a way to extract and export the private key from the device, leaving credentials potentially compromised.
2. Yubico Authenticator iOS App
Yubico Authenticator for iOS is an authenticator app that adds a layer of security for mobile and desktop users. The Yubico Authenticator app for iOS allows users to interact with X.509 certificates stored in a YubiKey’s PIV module over a Lightning connector or NFC. When using your YubiKey as a smart card, the Yubico Authenticator app is an essential tool providing two functions:
- It provides the intuitive user interaction for extracting the public portion of your certificate(s) on the YubiKey and placing it into the iOS keychain, thereby making the certificate available to any native app like the Safari browser, the Mail app, or any 3rd party app. The Yubico Authenticator app utilizes the latest iOS support for persistent tokens (contributing factor #1 above), allowing users to access certificates, keys, and identities stored in the PIV module of the YubiKey as if they were part of the iOS Keychain, all without compromising the private key.
- It interacts with the YubiKey over Lightning or NFC during authentication, signing, or decryption. This is the 2nd factor part where you enter your PIV PIN to allow interaction with the private key during authentication.
For the use cases below, we use the Yubico Authenticator app to interact with the YubiKey for authentication, email signing, and decryption. The source code is available on GitHub here, if you want to build your own PIV middleware solution.
3. The YubiKey 5 Series key as a PIV smart card
The YubiKey 5 Series key is ideal as a smart card because it provides hardware-backed security and portable credentials, supports the PIV standard, and can communicate with any Apple device physically over the Lightning connector or wirelessly over NFC. Within the PIV module of the YubiKey, you can store multiple digital certificates in individual slots for a variety of different use cases, as we’ll demonstrate below with authentication, digital signatures, and decryption. Each of the PIV slots in the smart card module of the YubiKey is capable of holding an X.509 certificate with its accompanying private key.
For higher assurance requirements, such as derived PIV credentials for US government agencies and their contractors, the YubiKey 5 FIPS Series key includes the same functionality but is FIPS 140-2 validated. Once a derived PIV credential is issued onto a FIPS Series YubiKey, the use cases and interactions are identical to a YubiKey 5 Series.
4. Derived PIV Credentials
PIV Credentials
A Personal Identity Verification (PIV) credentials have certificates, key pairs, pin numbers, biometrics, and other unique identifiers.
PIV credentials allow for a high level of assurance because the credentials are only issued by trusted providers to individuals that have been verified in person. PIV credentials can be issued by any organization using various commercial or open source products and typically this includes an X.509 certificate and key pair provisioned onto a PIV-compatible smart card.
Derived PIV Credentials
The derived credential is an alternate PIV credential that is “derived” from a Personal Identity Verification (PIV) smart card compliant with the PIV standards at NIST.
To date, these derived credentials are normally PKI certificates stored on mobile devices, but this can present security concerns when stored on non-GFE (government furnished equipment) that are not actively managed or patched.
To address the above issues, The National Institute of Standards and Technology (NIST) developed guidance around the issuance of Derived PIV credentials in Special Publication 800-157. Authorization of derived PIV credentials means that these credentials and the associated private key can now be provisioned onto the PIV-compatible secure element of a FIPS 140-2 validated device, such as the FIPS Series YubiKey.
The FIPS Series YubiKey is a YubiKey 5 Series key with the same PIV functionality but is FIPS 140-2 validated, meeting the highest authenticator assurance level 3 (AAL3) of NIST SP800-63B guidance. The FIPS Series YubiKey is only required by US government agencies and their contractors for issuing derived PIV credentials.
To summarize, most of the PIV credentials in use today are issued by US government agencies. Allowing derived PIV credentials on different form factors has opened the floodgates, giving employees and contractors a path to secure authentication on non-GFE mobile devices for the first time.
Following this standard and adoption from NIST, enterprise and commercial applications are building Public Key Infrastructure, issuing certificates, and enabling PIV authentication for their employees and customers as a proven, and endorsed phishing-resistant MFA option.
Breaking down the use cases
Nearly all user scenarios for using a YubiKey as a Smart Card on iOS fall under one of three categories: authentication, digital signatures, or encryption/decryption. Let’s dive into use cases for each category.
1. Authentication
PIV Authentication using certificate-based smart cards has been one of the most trusted and proven implementations of multi-factor authentication for over 20 years. That was the story for desktop users until now.
With the latest PIV-compatible smart card integrations on iOS and the updated derived credentials requirements satisfied by FIPS 140-2 validated YubiKeys, multi-factor PIV authentication is now unlocked for mobile iOS users.
As part of the developing ecosystem, Microsoft has announced Azure Active Directory certificate-based authentication on iOS for commercial and US Government use. PIV Authentication directly against Azure AD is critical for Federal Government organizations using either a PIV/CAC card or derived credential to comply with the Executive Order 14028 requirements.
To demonstrate this strong 2FA requirement, we’ll use an X.509 certificate, a YubiKey 5 series key, and the Yubico Authenticator app to authenticate into an Office365 Mail account via Azure AD CBA on a supported iOS device.
This entire PIV authentication process via Azure AD CBA is demonstrated in this video.
2. Digital Signatures
A digital signature, based on public key cryptography, is a technique used to validate authenticity, integrity, and non-repudiation of a message, digital document, source code, or software application. For digital signatures, a very common use case is sending a digitally signed Email message following the Secure/Multipurpose Internet Mail Extensions (S/MIME) protocol along with a certificate. S/MIME certificates offer two important email security functionalities — digital signatures and encryption. The S/MIME protocol is used in conjunction with a digital certificate for data encryption, message integrity, and non-repudiation of message origin.
For this use case, a digital S/MIME certificate could be from a derived PIV credential or issued from a certificate authority (CA) and stored on a PIV-compatible YubiKey. For this scenario, you need to configure the native Apple Mail app to send email messages with your digital signature by referencing a pointer to the private key of the signing certificate on the YubiKey. We are using the Yubico Authenticator app to copy the certificate’s public key to the iOS Keychain (one-time) and then to act as the middleware between the PIV module of YubiKey and the device. Whenever an email is sent with digital signatures enabled, the system will prompt you to launch the Yubico Authenticator to interact with the YubiKey for signing. This gives you message integrity and non-repudiation.
Here’s what it looks like to use an S/MIME certificate residing on a YubiKey as a smart card to send digitally signed outbound emails using the native iOS Mail App:
Important Note: Digitally signed emails are sent as clear text (unencrypted) and the digital signature is sent along as an attachment to the clear text message.
In the next section, we’ll use the same certificate to cover the encryption/decryption use case to ensure message privacy and protect sensitive data.
3. Encryption/Decryption
In this use case, we’ll showcase encrypting/decrypting the message content of an email using the same S/MIME certificate used for digitally signing outbound emails. The process of encryption/decryption of messages is not as straightforward as signing because it involves two parties. For example, to encrypt an outbound email message you use the recipient’s public key.To decrypt an incoming message (that was encrypted by the sender using your public key), you use your private key.
So, there’s really two parts to this:
- The sending of the encrypted message using the recipient’s public key.
- Decryption of the incoming message using the recipient’s private key.
The use case here is focused on decryption because it’s the only part that requires interaction with the private key that resides on the YubiKey. As we did with Email signatures, we’ll be using the Yubico Authenticator app to act as the middleware between the PIV module of YubiKey and the device. Since we are using the same S/MIME certificate for the Email signatures, the pointer to the public key already exists on the iOS Keychain.
This is an important distinction to remember; the private key used for signing or decryption never leaves the YubiKey.
Whenever an encrypted email is received, Apple Mail will prompt you to interact with the Yubico Authenticator to perform decryption of the inbound message using the private key that resides on the YubiKey.
Note: If you are not using an Exchange account, you need to send and receive signed emails before you can send an encrypted message. For simplicity of demonstrating this use case, we’ll use the same S/MIME certificate and send an encrypted email message using the public key and then decrypt that message using the associated private key residing on the YubiKey. Yes, for demonstration purposes, we are sending encrypted email messages to our self:
Try it out for yourself!
We hope you now feel informed and inspired to start thinking about your next smart card integration for mobile. Learn more about YubiKey as a smart card on iOS or start building your own solution with the Yubico iOS SDK today.
——
To learn more about Apple’s recently announced support for security keys, check out our blog post here.