Tag: PIV
-

Available now: YubiKey Bio Series – Multi-protocol Edition keys expand phishing-resistant authentication options for enterprises As adoption of biometric logins continues to increase globally, enterprises and cybersecurity teams require stronger security combined with user convenience to improve user adoption of multi-factor authentication (MFA) and ensure productivity. Hardware security keys that leverage biometrics, like the YubiKey Bio Series, enable organizations to do so by offering portable, user-friendly seamless functionality – all […] Read more PIV smart card YubiKey 5.7 YubiKey as a Service YubiKey Bio YubiKey Bio Multi-protocol Edition -

Enhancing Federal Security: Issuing PIV-Compatible Credentials with Axiad Cloud (FedRAMP) and Yubico Join this webinar to gain a comprehensive understanding of how you can streamline the credentialing process and ensure compliance with federal standards while enhancing security and efficiency. Read more government phishing-resistant MFA PIV YubiKey -

Introducing the expanded YubiKey Bio Series: YubiKey Bio Multi-protocol Edition (Early Access) As the threat of sophisticated attacks like phishing continue to rise, enterprise users and cybersecurity teams are seeking a solution that offers robust security and user-friendly functionality. With the increasing adoption of biometric logins, enterprises aim to marry strong security with user convenience to boost productivity and job satisfaction. Hardware security keys that leverage biometrics, […] Read more Early Access PIV smart card YubiEnterprise Subscription YubiKey Bio -

Resolve to be cyber resilient: Moving on from legacy MFA in energy and natural resources Every November, Critical Infrastructure Security and Resilience (CISR) Month focuses on educating the vital role critical infrastructure plays in the nation’s well being. Led by Cybersecurity and Infrastructure Security Agency (CISA), the conversation centers around why it’s important to strengthen critical infrastructure security and resilience. One of the critical infrastructures, energy and natural resources, is […] Read more CISA energy and natural resources PIV smart card -

Boliden case study Boliden is one of Europe’s leading metal mining companies. Based in Sweden, with presence around the Nordic region and beyond, Boliden produces a vast array of the metals required for modern life: zinc, copper, lead, nickel, gold, palladium, platinum and silver. Read more FIDO2 PIV privileged users YubiKey 5C NFC -
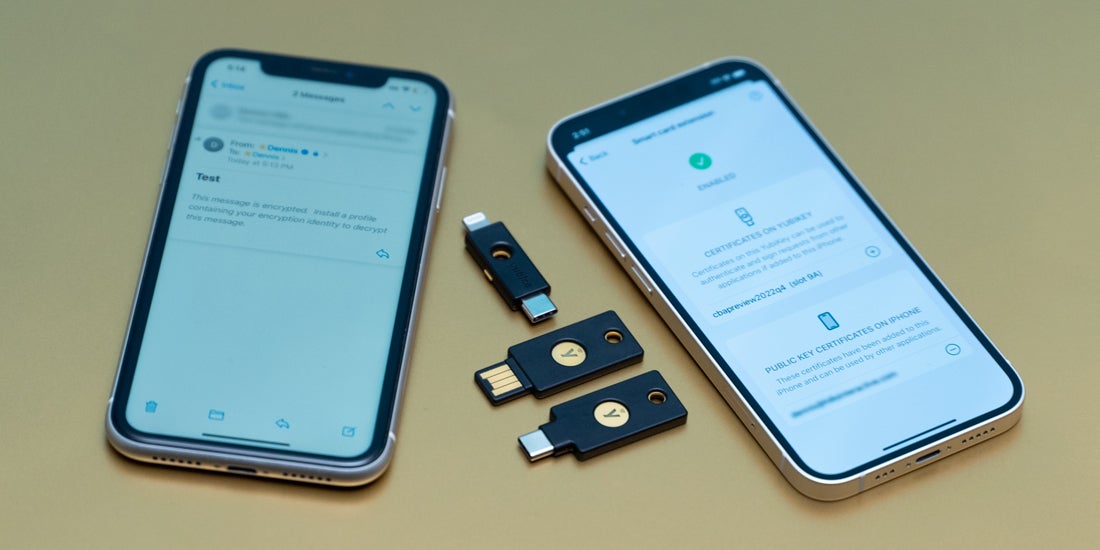
Uncovered PIV use cases on iOS: Using YubiKey as a smart card on iOS In a recent post we discussed the concept of using a YubiKey as a smart card on iOS. Now that we’ve outlined the overall concept, we’d like to expand by exploring the unlocked use cases for using a smart card for authentication, creating digital signatures, and decrypting messages and documents on Apple iPhones and iPads. […] Read more ios authentication PIV smart card Yubico Authenticator YubiKey -

How to implement a CryptoTokenKit extension on iOS In previous blog posts here and here, we’ve shared how you can use a YubiKey and its PIV Smart Card application together with the Yubico Authenticator app for iOS. Essentially, you can now use your YubiKey to authenticate in Safari and many other applications on iOS using certificate-based authentication backed by the PIV Smart Card […] Read more PIV smart card Yubico Authenticator YubiKey -

Seven tips if you’re still scratching your head after reading Biden’s cybersecurity executive order Yubico works with a lot of federal agencies and contractors, as well as with customers in regulated industries, so we understand the challenges new compliance regulations can bring. The executive order that was released May 12 can be seen as the federal government fully embracing the move toward multi-factor authentication (MFA) for use cases where […] Read more government PIV Public Sector YubiKey FIPS Series -

Yubico brings the YubiKey to the .NET ecosystem with its new desktop SDK In continuation with our mission to bring strong authentication to the world, Yubico is excited to announce that integrating the YubiKey into your .NET application or workflow will now be easier than ever before. This is enabled with the introduction of the new YubiKey SDK for Desktop. With this Desktop SDK, you can now add […] Read more developers PIV Yubico Developer Program -

Entrust to add support for YubiKeys with PIV – Yubico Today marks an important day for expanding Yubico’s reach to support the growing requirement for Government agencies to issue government credentials beyond Personal Identity Verification (PIV) cards. We are celebrating that our partner Entrust will soon launch support for derived PIV credentials for YubiKeys. Customers will be able to take advantage of YubiKeys with derived […] Read more government PIV Public Sector
