I work as a developer at Yubico. Like a lot of developers these days I’m empowered to not only develop software, but to publish it and configure the servers it runs on. This means that I have access to many systems, to which I authenticate using different keys, requiring the flexibility of a YubiKey.
 |
|
| The Key to Henrik’s Day | |
| YubiKey NEO Feature | Authentication uses |
| OTP | Salesforce, Yubico Forums, WordPress |
| U2F | Gmail |
| PGP | Signing code changes |
| SSH (via PGP) | Servers |
| NFC (+ OTP) | Unlocking office door |
| NFC (+TOTP) | Facebook, GitHub |
| Mifare Classic ID (+ code) | Unlocking door to office building |
I store these keys on my YubiKey NEO, from which they can never leave, and let it do all authentication and signing. This means I am assured no one accesses systems in my name, even if they’ve stolen my laptop or have my passwords.
To make this more concrete, I have documented a regular workday.
Morning:
Entering the office building
The office building doors are unlocked using plastic fobs. Fobs are identified using their ID (Mifare Classic UID). Since my YubiKey NEO supports Mifare, I use it instead.
The office
A few minutes later I swipe my NEO again to unlock the door to the Yubico Stockholm office. This lock (sold by KEYnTO) is more secure since it uses YubiKey One-Time Passwords.
Reading e-mail
Yubico, like many other companies, uses Google for e-mail, calendar and documents. Google encourages you to use a Security Key (U2F device) to protect your account.
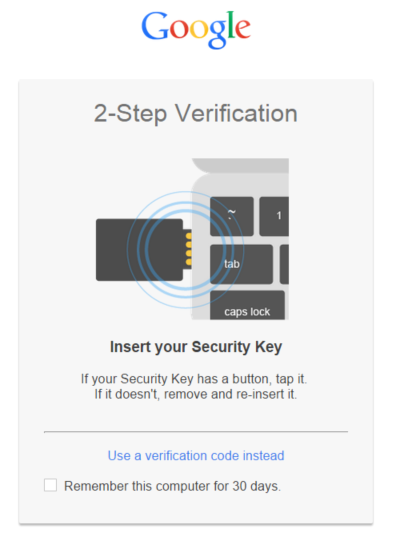
Needless to say (since Yubico is a driving force behind U2F), I use my YubiKey for this as well.
Checking the forum
Yubico’s forum runs PhpBB and uses YubiKey One-Time Passwords as a second factor for authentication.
Afternoon:
Checking Facebook during lunch
I’ve configured Facebook to “keep me logged in” on trusted devices. But when I login to Facebook (and Dropbox, GitHub, etc.) from untrusted devices, I’m asked to enter a 6 digit time-based code. To get the code, I just tap my NEO to my phone (the code is transferred using NFC). This has a couple of advantages:
- The secrets used to generate the codes never leaves my YubiKey, so I don’t have to worry about phone malware or securely wiping the phone when selling it.
- I’m not tied to a single phone. I can even use a friends phone if mine is out of battery.
Pushing code to Git
Today, I’m working on our developer portal, developers.yubico.com. After a few hours of coding, I’ve got something that I’m ready to publish. I type “git push” in the terminal, enter my YubiKey’s PIN and let it authenticate me to GitHub. My private SSH key never leaves the YubiKey.
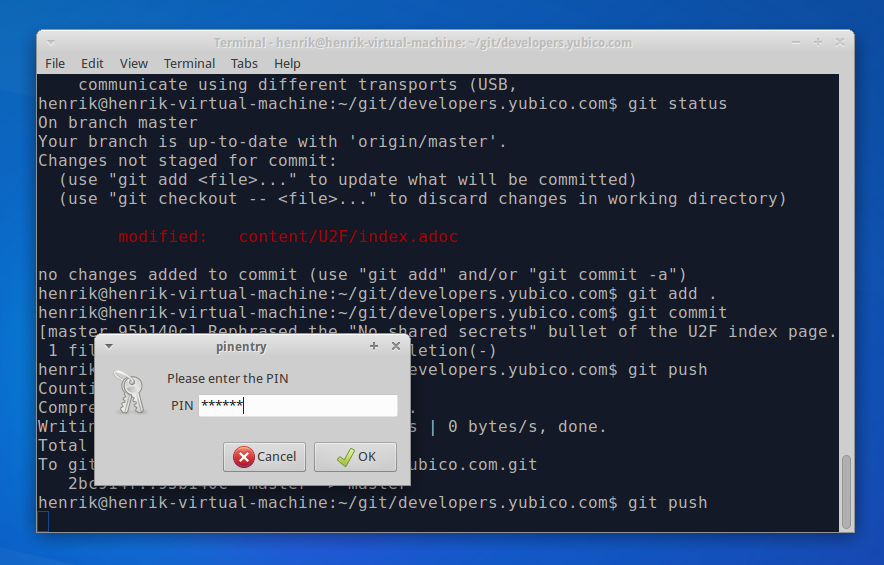
Connecting to a server via SSH
My new code isn’t working as expected, so I SSH into the web server hosting developers.yubico.com to have a look in the logs. Once again, my YubiKey does the authentication.
Signing released software
I spent the afternoon adding some features to our U2F library for Java. In order to publish the release, I have to sign the artifacts using OpenPGP. Luckily, the build system (Maven) has a plugin for this. All I have to do is to type “mvn deploy -P release” and the YubiKey will sign the files using my PGP key.
Things I didn’t do today
I use my YubiKey for even more things. Here are some of the things that I didn’t do today:
- Logging into Yubico’s website that’s running WordPress, using FIDO U2F.
- Logging into Yubico’s Salesforce instance, using a YubiKey One-Time Password.





