COVID-19 initiated the most rapid digital transformation ever witnessed—organizations fast-tracked two-factor and multi-factor authentication to transition millions of employees to work from home. But with remote and hybrid work likely to continue in 2022 and beyond, it’s time to step back and ask: is my in-use authentication as secure as I think it is? Is it phishing resistant? And what is it really costing my organization?
—
Because of COVID-19, organizations may have chosen the quickest route to get users set up with 2FA/MFA, leveraging mobile authentication methods such as SMS-based OTP or authenticator apps because they were easy to deploy and supported by the ubiquity of mobile devices. Yet today, organizations continue to experience cyber attacks that penetrate their defenses. In fact, 74% of organizations attribute recent cyber attacks to remote work vulnerabilities. What’s happening? How is it that you’re spending more to support 2FA and MFA without a net benefit in security?
While mobile authentication is relatively inexpensive to roll out, most organizations can experience hidden costs, productivity losses, and support issues. For example, if you are requiring your employees to use mobile-based MFA, you may have to take on the costs for that device, recurring service costs, enterprise device management software and more. Further, the average company loses $5.2 million annually in productivity due to account lockouts – and password costs such as these only represent the first factor in 2FA and MFA.
As a security lead that oversees digital security across your business, sometimes it’s good to step into your user’s shoes. Let’s walk through a simple exercise. Assume that you are a junior sales employee working from home, who needs to access Salesforce, which is protected with SMS-based OTP for 2FA:
It’s the start of my day and I’m ready to log in to see who has responded to my latest sales cadence. I open up my laptop, log into the device, then navigate to Salesforce where I’m presented with this workflow:
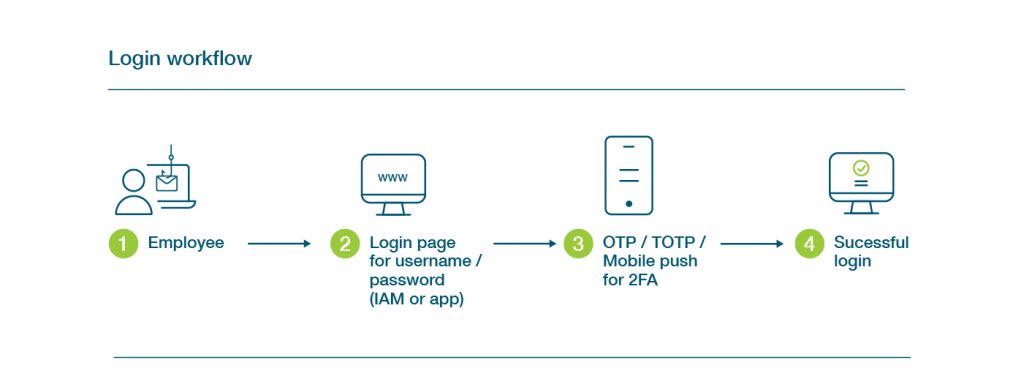
I may have to repeat this process after a period of inactivity or if I navigate to a different corporate app in the network if Single Sign On (SSO) is not deployed. Sometimes there’s a delay with the OTP coming through to my phone or sometimes I have to dig around for the right username and password for an app I may not use as frequently.
From a security perspective, it looks pretty good – right? Each login has two steps of protection. Well, that’s where looks can be deceiving.
Modern phishing attacks can intercept that username and password combo as well as the OTP. Let’s say, in this case, it began with an authentic looking request from the support team with a request to test connectivity for my Gmail.
That email asked me to click a link and log into Gmail as per normal. Except, the process was not normal – it was a successful phishing attempt that resulted in an account takeover:
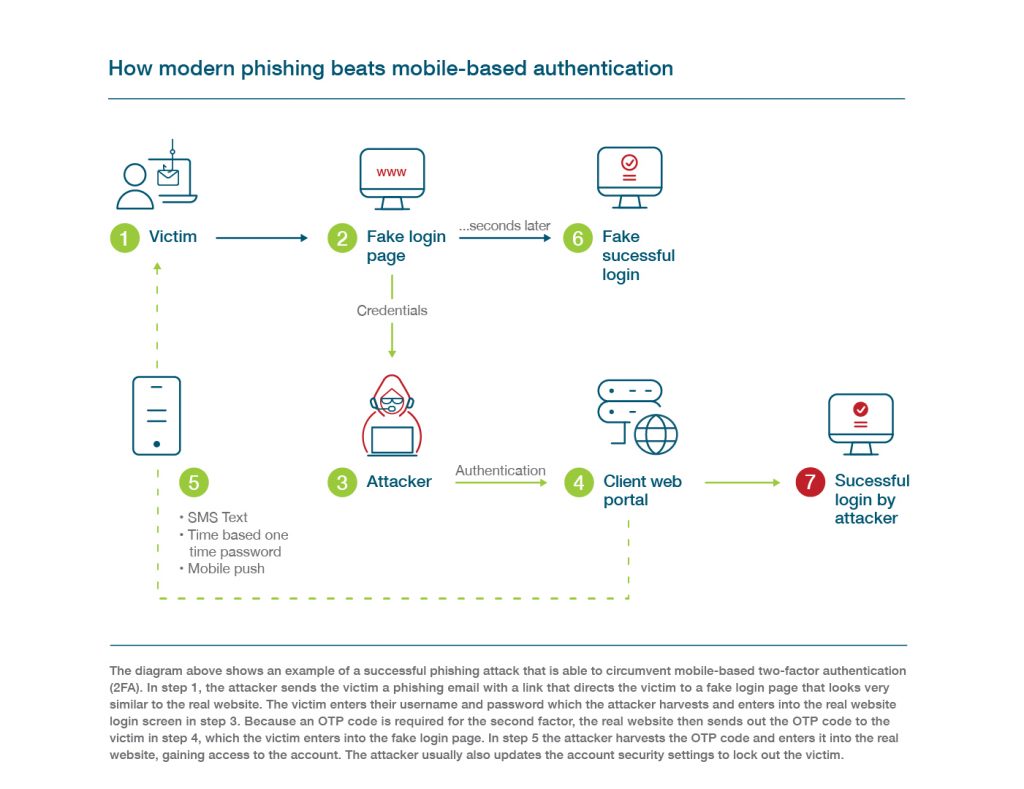
In this example, I (as the employee) have no idea I have been phished or that my credentials have been successfully intercepted.
It may seem far-fetched, but few organizations are aware of the fact that SMS-based OTP only blocks about 76% of today’s targeted attacks. In fact, only 22% of respondents we surveyed are aware that security issues such as these even exist with SMS-based authentication.
The belief that mobile authentication is secure is a key misconception we see related to mobile-based authenticators. The reality is that mobile authenticators can still be phished – even if some are more secure than others.
Let’s take a look at that employee again, who’s having to authenticate with a password and wait for an SMS OTP every time they need to log into a different app – over the course of the day, this could mean several dozen authentication attempts, some of which may have delayed codes or issues with network connection or a forgotten password. If this doesn’t sound fun, it’s because it isn’t. User experience has become the top obstacle to using MFA. All these obstacles just add to the overall IT security and support burden.
It’s time to demystify the myth vs. reality of legacy MFA such as usernames and passwords and mobile authentication. Now is the time to create a long-term MFA strategy that understands all the importance of security, cost, and user experience, among other factors, that will lend to a successful and secure business long term.
Moving Past Legacy MFA
Whether your organization has already deployed mobile authentication, or is actively considering authentication solutions to beef up security, it’s important to understand that MFA is a spectrum and that not all MFA is created equal.
We know that legacy authentication such as usernames and passwords don’t offer much in the way of security, and actually come with a pretty hefty support cost (Forrester estimates $1 million). We saw how easily that SMS OTP was intercepted, so that all that extra time spent authenticating wasn’t actually adding much to security. What it was doing, however, was creating more support burden – time spent setting up new devices and apps, training users, and supporting help desk requests for password resets and OTP issues.
Let’s step into a user role again. This time, I use my YubiKey, a hardware key for modern strong authentication to log into Salesforce (or my IAM dashboard) by simply plugging it into my USB port and touching the button, or tapping it against my phone for NFC authentication on the go. I have instant access to what I need without needing to rely on phone battery or cellular data availability (user friendly!).
My IT team can now relax knowing that the YubiKey provides 100% coverage against phishing and account takeovers.
The YubiKey is game changing for security and for user experience, offering support for strong 2FA, MFA, and passwordless authentication. YubiKeys also come with flexible purchasing ‘as a service’, turnkey delivery, inventory management, and self-provisioning, ensuring that your organization and all employees, whether in-person or remote, are always protected.
MFA myths are everywhere.
To learn more about the truths of mobile authentication, read our whitepaper, The Top 5 Mobile Authentication Misconceptions: Demystifying the myth versus reality of legacy MFA.
Don’t miss our webinar where we’ll take a deep dive into mobile authentication misconceptions on December 9 at 9 am PT – reserve your spot and register here.





