Tag: phishing
-

AI is booming — but proving you’re human matters more than ever If you walked the show floor at the RSA Conference this year, you probably noticed the same thing I did: Artificial Intelligence (AI) is everywhere. Agentic AI. AI in threat detection. AI in firewalls. AI in identity management. AI-generated demos. AI everything. The energy around AI was undeniable, and we’re seeing real innovation, efficiency gains […] Read more AI Artificial Intelligence phishing RSAC -

Breaking down Australia’s plan to combat AI-driven phishing scams Across Australia, cybercrime continues to be a major challenge impacting businesses, critical infrastructure and consumers alike. The use of AI by bad actors across the spectrum of cybercrime is on the rise, and as a result, credential phishing scams are becoming increasingly sophisticated. AI is effectively helping to lower the cost of phishing and increase […] Read more AI APAC Australia phishing -

QR code phishing attacks (Quishing): What to know and how to stay secure If you immediately think of email when you think of phishing, you’re not alone. However, a new form of a text-based scam is making waves – highlighted by a seemingly legitimate text from the USPS which lets receivers know that their “package” arrived at the warehouse. To receive the package, it instructs users to click […] Read more best practices phishing QR Code Phishing Quishing -

Staying safe online this holiday shopping season: Five tips to improve your security habits Americans spent over 200 billion dollars online during the 2022 holiday shopping season, making 2023 a record year for online retailers. This year, 97% of people recently surveyed said they plan to shop online. As holiday revenues grow, so does the temptation for criminals to take a part of the action for themselves – over […] Read more best practices Holiday online shopping phishing survey -
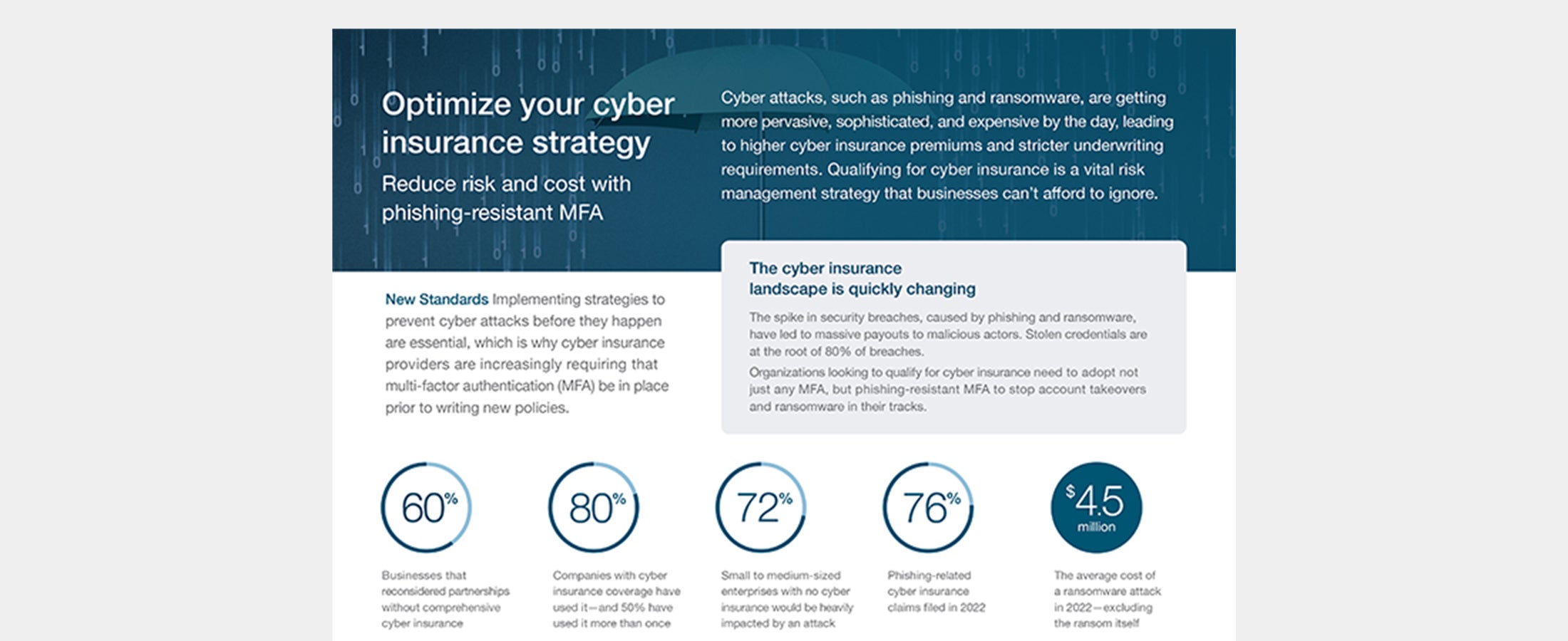
Cyber insurance strategy Cyber attacks are getting more sophisticated, and expensive, leading to higher cyber insurance premiums. Phishing-resistant MFA can help set you up for success and save on costs. Read more cyber insurance phishing phishing-resistant MFA -

Hackers don’t break in. They log in. Cyber crime is surging like never before… 300% Rise in cyber crime since the pandemic began.1 59% Of companies have had a security breach in the last year.2 9 out of 10 Cyber attacks begin with a phishing email.3 Most cyber attacks begin as phishing Phishing is a cybercrime where attackers induce people to reveal […] Read more cybersecurity phishing phishing-resistant MFA -

Forging ahead: A CISOs top recommendations to stay secure in 2023 Last year, we anticipated that 2022 would be challenging for cybersecurity. This was proven true with the countless number of sophisticated high-profile phishing and ransomware attacks like DropBox, Twitter, Rockstar Games and Uber (twice). With the introduction of phishing-as-a-service and other sophisticated toolkits that target weaker forms of 2FA, security teams are now prioritizing phishing […] Read more CISO compliance phishing Public Sector zero trust -

2022: A year of phishing with a solution to calm the seas In 2022, phishing scams continued to hook into consumers and enterprise accounts. In fact, recent research from EMA revealed that 87% of surveyed businesses indicate that their organization experienced an identity-related security breach in the preceding 12 months. Many successes of the sophisticated phishing scams were due to legacy MFA implementations such as SMS, mobile […] Read more MFA phishing Secure It Forward YubiKey -

How hackers use low effort tactics for phishing attacks – Yubico Phishing continues to make headlines with attackers using stolen credentials to gain access to valuable systems and sensitive data. Although phishing has been a known technique for a long time, the industry is still struggling to effectively defend against it. This may seem surprising to many as “phishing” calls to mind poorly written emails, generic […] Read more phishing phishing-as-a-service phishing-resistant MFA security key -

Hackers don’t break in. They log in. Cyber crime is surging like never before… 300% Rise in cyber crime since the pandemic began1. 53% Of companies in Europe & the Middle East have been victims of cyber attacks2. 9 out of 10 Cyber attacks begin with a phishing email3. Most cyber attacks begin as phishing Phishing is the fraudulent practice of inducing […] Read more cybersecurity phishing phishing-resistant MFA
