A recent announcement by Twitter has begun to rock the multi-factor authentication (MFA) boat, and the ripples have spread throughout the tech world. The company announced that starting on March 20, 2023, unless a user is subscribed to its Twitter Blue program (an $11/month subscription), they will lose access to SMS-based two-factor authentication (2FA). SMS has historically been put forth as a low friction mechanism that offloads several security and recovery functions to users’ mobile carriers.
Recent history has shown not all MFA is created equal, highlighted by weaknesses in SMS-based 2FA from SIM Swapping and Social Engineering attacks. There is also a hard cost that comes to companies that choose to enable SMS 2FA.
When sending SMS codes to devices, the communications is relayed through a third party, like a phone company or messaging service. These messages are automated as part of the login flow. At a small scale, this may seem to be a negligible cost when compared to other methods. However, for large service providers like Twitter, abuse of these mechanisms can be a very costly proposition. Bad actors can use this method by creating fleets of accounts and then sending unanswered MFA messages in SMS Pumping attacks.
Legitimate accounts can also be compromised in account hijacking or identity theft scenarios via SIM Swapping and social engineering. Even for small and medium sized businesses, third party costs related to SMS can expand – especially if the service is that target of pumping.
Fortunately, by adopting alternate modern MFA methods like FIDO2/WebAuthn, service providers can maintain ease of use and flexibility in its MFA workflows and cut out major costs and risks associated with SMS
The future of MFA with FIDO2 and WebAuthn
The WebAuthn standard, also known as FIDO2, describes user-friendly and cryptographically secure authentication methods that are flexible, modern and do not require additional costs for the service provider. It’s supported by all modern operating systems and browsers, and can leverage built-in authentication features of devices such as computers and phones – or even more secure options like external security keys. Yubico, the inventor of the YubiKey, which is the gold standard for hardware security keys, also created and continues to contribute to the FIDO2/WebAuthn standards.
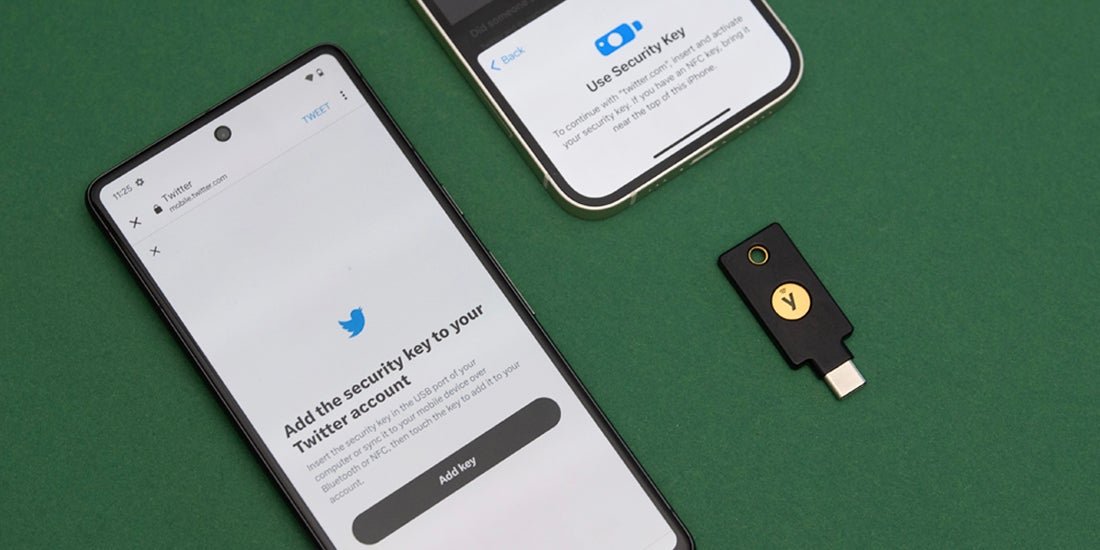
Since mid-2019, Twitter has provided customers the option of WebAuthn, and it is the company’s preferred MFA method for its internal employees as well. Twitter also supports it as the only MFA method that users can select that does not require a phone number – helping to enhance privacy and anonymity. Instructions for enrolling WebAuthn devices can be found on Twitter’s Knowledge Base here.
WebAuthn is the de facto phishing-resistant MFA standard that allows end users to associate their security keys or security devices across a wide array of services. Since users bring their own authenticator, and the standard is free to use, companies can provide highly secure MFA that doesn’t incur unexpected transactional cost. Twitter, by essentially retiring SMS 2FA methods for non Twitter Blue subscribers, is taking a bold step forward in both controlling their costs AND guiding users to stronger, easier to use authentication methods.
To find out which YubiKey is right for you, we encourage Twitter users and others who are looking for a modern MFA alternative to SMS or authenticator apps to take Yubico’s quiz. A great option for Twitter users is the newly updated Security Key Series, which offers high security for all online accounts via FIDO-based phishing-resistant MFA. You can see all of our security key options and form factors via our store.