Tag: YubiKey
-
Protecting the healthcare ecosystem with phishing-resistant MFA Learn how the YubiKey helps healthcare organizations across insurance, providers, clinicians, biotech, and pharmaceuticals drive high security against modern cyber threats and high user productivity with the best user experience Read more healthcare passwordless phishing-resistant MFA YubiKey -

Certificate-based authentication with YubiKeys on iOS and Android With Microsoft’s announcement today of its support for Azure AD Certificate-based authentication (CBA) for both iOS and Android devices, Yubico is excited to share that the YubiKey is currently the only external device that supports CBA on Android and iOS. Plus, the YubiKey is the only FIPS certified phishing-resistant solution available for Azure AD on […] Read more Azure AD CBA Microsoft phishing-resistant MFA YubiKey -

Phishing attacks are on the rise: are you prepared with phishing-resistant MFA? It doesn’t have to be Cybersecurity Awareness Month to read a flurry of news about human-based phishing attack stories – also called smishing if the “fishing line” is cast via SMS. These attacks boil down to the art of tricking people into revealing personal information and credentials – including usernames, passwords, authentication codes, and sensitive […] Read more FIDO phishing phishing-resistant MFA smishing YubiKey -

Five Strategies to Scale Phishing-Resistant MFA in 2023 – Yubico Legacy multi-factor authentication (MFA) has not worked against modern cyber threats due to inability to stop phishing and other account takeovers. Modern MFA, such as YubiKeys, have been proven to stop phishing attacks and account takeovers in their tracks. Only solutions based on Smart card/PIV or FIDO protocols are truly phishing-resistant according to the National […] Read more FIDO OTP phishing-resistant MFA smart card YubiKey -

Why banks need to act now or risk non-compliance with new Consumer Financial Protection Bureau (CFPB) guidance If the gauntlet hadn’t been thrown before to protect financial and banking customers’ data, it’s definitely lying on the floor now. The recent circular bulletin from the CFPB makes it clear that financial institutions can’t slow-walk any security upgrades: “Inadequate security for the sensitive consumer information collected, processed, maintained, or stored by the company can […] Read more CFPB Executive Order financial services MFA phishing-resistant MFA YubiKey -
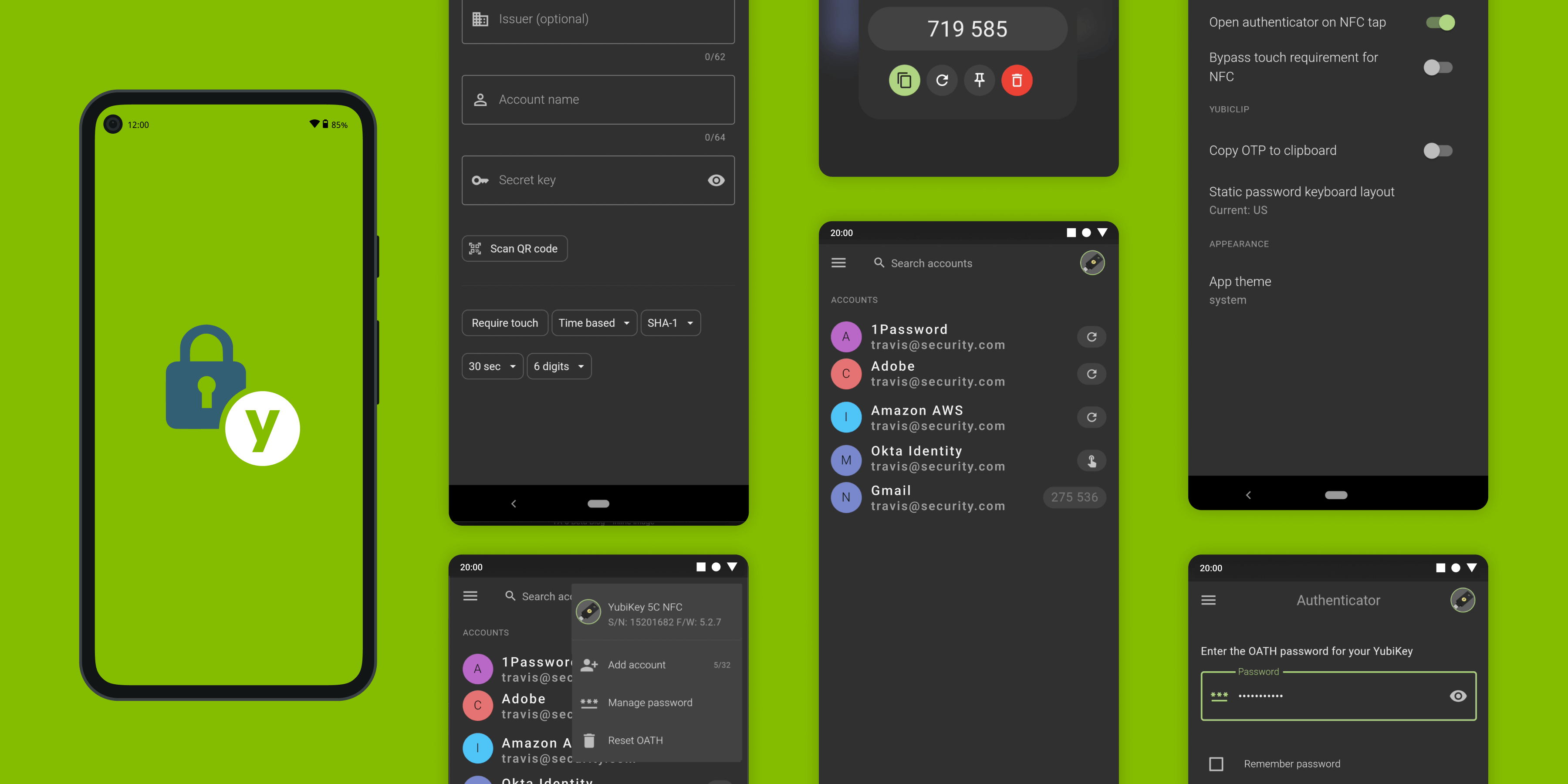
Yubico Authenticator 6 for Android Note: This is a follow-up to our previous announcement of Yubico Authenticator 6 for Desktop. If you haven’t read it yet, we recommend you do so first. If you’re not yet familiar with the app you can read more about it, and about how to use Yubico Authenticator with the services you want to secure. […] Read more android authentication beta Yubico Authenticator YubiKey -

New Global Survey from Yubico finds 59% of Employees Still Rely on Username and Password as Primary Method to Authenticate Their Accounts To kickoff Cybersecurity Awareness Month, Yubico brings top industry leaders together to reveal state of enterprise security SANTA CLARA, CA and STOCKHOLM, SWEDEN – September 28, 2022 – In light of recent phishing-based cyberattacks and in recognition of Cybersecurity Awareness Month, Yubico, the leading provider of hardware authentication security keys, today shared the results of […] Read more authentication passkeys phishing-resistant MFA survey YubiKey -

Yubico’s director of engineering on defending against phishing Yubico’s mission is to make the internet safer for everyone, and at the heart of that is a belief that the best security requires usability. Anyone who accesses the internet is at risk from cybercrime, so YubiKeys are designed to provide phishing-resistant MFA protection for everyone. That’s why YubiKeys are so simple to set up […] Read more authentication phishing-resistant MFA Q&A YubiKey -

How phishing-resistant MFA stops cyberattacks in healthcare Ransomware attacks and other types of cyberattacks in healthcare are growing, not only in amount, but in sophistication as well. The recent State of Ransomware in Healthcare report released by Sophos highlighted a 94 percent increase in ransomware attacks in 2021, with 66 percent of healthcare organizations hit by ransomware – up from 34 percent […] Read more data breach FIDO2 healthcare phishing-resistant MFA YubiKey -

Thoughts on modern cybersecurity for retail and hospitality in advance of RH-ISAC’s Cyber Intelligence Summit Recently Derek Hanson, vice president and product evangelist at Yubico, spoke with Paul Malcomb, cyber threat intelligence analyst and engagement lead at Retail and Hospitality ISAC (RH-ISAC), on their podcast. Derek shared insight on how passwordless authentication using FIDO and phishing-resistant MFA can help retail and hospitality organizations accomplish business goals such as ensuring strong […] Read more passwordless phishing phishing-resistant MFA retail and hospitality YubiKey
