Tag: YubiKey
-

developer-program-email-preferences he Yubico Developer Program provides resources to enable rapid implementation of strong authentication for web and mobile applications. Read more developers Yubico Developer Program YubiKey -
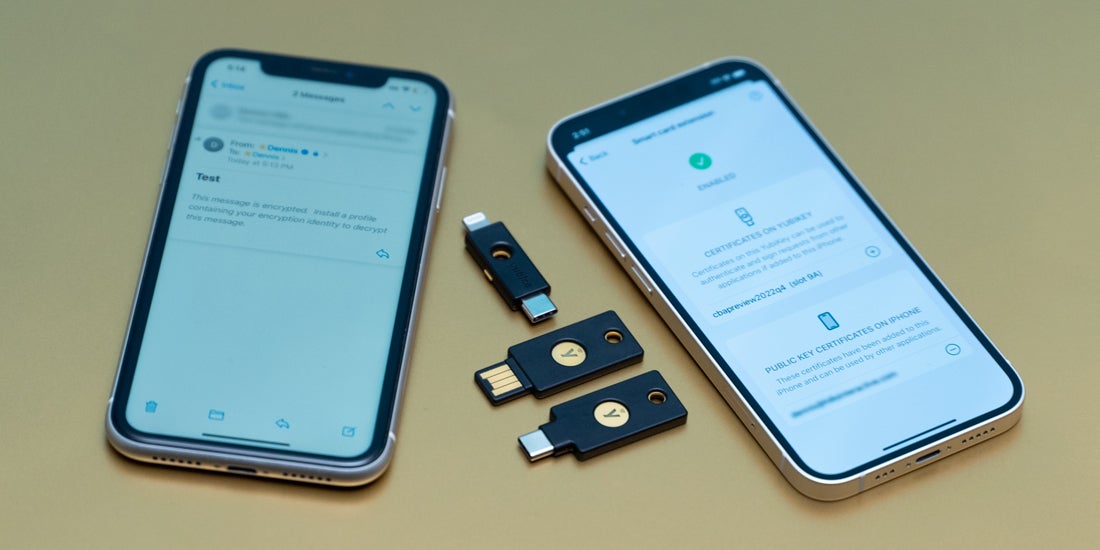
Uncovered PIV use cases on iOS: Using YubiKey as a smart card on iOS In a recent post we discussed the concept of using a YubiKey as a smart card on iOS. Now that we’ve outlined the overall concept, we’d like to expand by exploring the unlocked use cases for using a smart card for authentication, creating digital signatures, and decrypting messages and documents on Apple iPhones and iPads. […] Read more ios authentication PIV smart card Yubico Authenticator YubiKey -

2022: A year of phishing with a solution to calm the seas In 2022, phishing scams continued to hook into consumers and enterprise accounts. In fact, recent research from EMA revealed that 87% of surveyed businesses indicate that their organization experienced an identity-related security breach in the preceding 12 months. Many successes of the sophisticated phishing scams were due to legacy MFA implementations such as SMS, mobile […] Read more MFA phishing Secure It Forward YubiKey -

Apple announces upcoming support for security keys – Yubico In 2022, if one thing has been proven, it has been made very clear that not all multi-factor authentication (MFA) is created equal. Vulnerabilities with legacy forms of MFA, such as SMS, TOTPs, and mobile-based apps, continue to be the target and victims of data breaches, with attackers taking aim in record numbers in 2022. […] Read more Apple FIDO passkeys security key YubiKey -

Phishing attacks are getting smarter Phishing attacks are getting smarter. Your defenses should, too. Most cyber crime relies on stealing account credentials. That’s why it’s so important to use more than just a password to protect your online accounts. Read more MFA phishing-resistant MFA YubiKey -

‘YubiKeys-as-a-Service’ delivered 203% ROI: new Forrester Consulting research and BeyondTrust case study For organizations around the world, cybersecurity often boils down to a few important areas: high reliability, ease-of-use and cost. Forrester Consulting, in a Yubico- commissioned Total Economic Impact™ (TEI) study, examined these areas regarding the adoption and use of YubiKeys, including the potential return on investment (ROI) enterprises may realize by deploying YubiKeys. One of […] Read more BeyondTrust Forrester TEI subscription YubiEnterprise YubiKey -

Halborn case study To support the 100% remote, diverse, and bright team of engineers and ethical hackers, Halborn leverages a unique gamification system designed to reward and incentivize its employees based on proof of work and continuous learning. Read more phishing-resistant MFA strong MFA YubiKey -
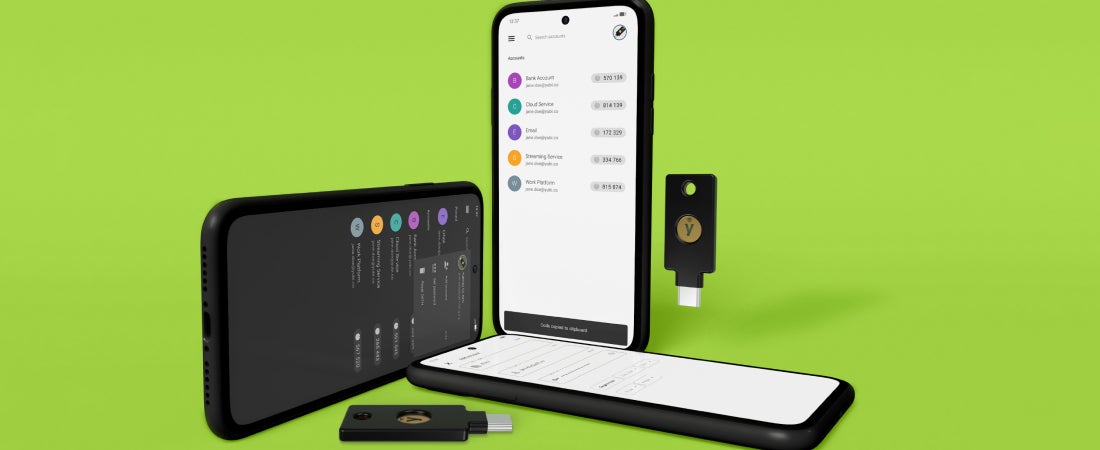
Yubico Authenticator 6 is here! Earlier this year we announced the upcoming release of Yubico Authenticator 6, the next version of our YubiKey authentication and configuration app. We released a beta version, first for desktop, and then for Android, and we solicited your feedback. We got plenty of it, and have been busy incorporating a lot of it into the […] Read more OTP SDK Yubico Authenticator YubiKey -

Ease of use We know traditional authentication methods haven’t always been the most user-friendly, which is why we created the YubiKey––it makes logging into your accounts simple and secure. Read more authentication hardware phishing-resistant authentication wwyk YubiKey -
Protecting the healthcare ecosystem with phishing-resistant MFA Learn how the YubiKey helps healthcare organizations across insurance, providers, clinicians, biotech, and pharmaceuticals drive high security against modern cyber threats and high user productivity with the best user experience Read more healthcare passwordless phishing-resistant MFA YubiKey
