Blog
Stay up to date on company and partner news, product tips, and industry trends.
-

Yubico named finalists of German digital identity innovation competition In 2023, Yubico began collaborating on an exciting open standards identity project – wwWallet – to shape the future of digital identity across Europe and beyond. The project saw immediate success solving problems for global identity, and was submitted in the German SPRIN-D European Digital Identity (EUDI) Funke competition which aims to develop and test […] Read more EU Digital Identity Wallet EUDI wwWalet -

Introducing new features for Yubico Authenticator for iOS We’re excited to share the new features now available for Yubico Authenticator for iOS in the latest app update on the App Store. Many of these improvements aim to address frequently requested features from our customers, while providing additional new functionalities for a seamless authentication experience on iOS. With increased interest in going passwordless and […] Read more iOS Yubico Authenticator -

Platform independent digital identity for all Many are understandably concerned that the great invention called the Internet, initially created by researchers for sharing information, has become a major threat to democracy, security and trust. The majority of these challenges are caused by stolen, misused or fake identities. To mitigate these risks, some claim that we have to choose between security, usability […] Read more Digital Identity EUDI Founder Stina Ehrensvard -

Q&A with Yubico’s CEO: Our move to the main Nasdaq market in Stockholm As 2024 draws to a close, it’s the perfect time to reflect on the incredible journey we’ve had this year and how it has shaped where we stand today as a company. To mark this moment, I sat down with our CEO, Mattias Danielsson, to look back on the milestones and achievements of 2024—culminating in […] Read more CEO Mattias Danielsson -

Exploring DORA: A look at the next major EU mandate Financial institutions have historically managed operational risk using capital allocation, but under EU Regulation 2022/2554 – also known as the Digital Operational Resilience Act (DORA) – the financial sector and associated entities in the European Economic Area (EEA) must also soon follow new rules. These new rules focus on the protection, detection, containment, and the […] Read more DORA EU -

Securing critical infrastructure from modern cyber threats with phishing-resistant authentication Across the globe, 2024 has seen a whirlwind of change. With ongoing wars, recent political change-ups and more, growth in data breaches targeting critical infrastructure continue to be on the rise. Critical infrastructure is integral to our everyday life – from the energy and natural resources powering our hospitals and providing clean drinking water, telco […] Read more CISA critical infrastructure zero trust -
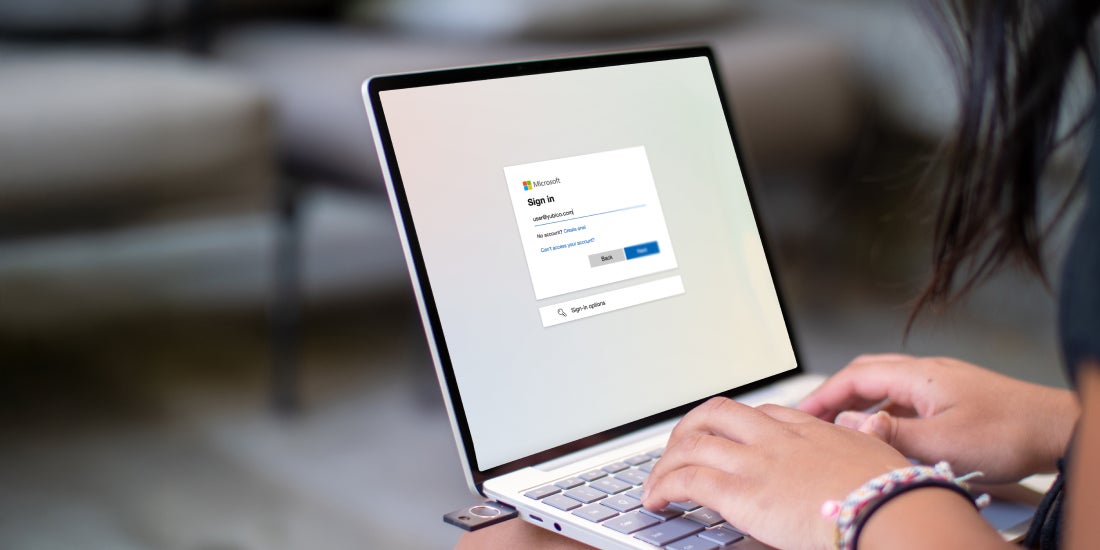
Yubico Enrollment Suite for Microsoft users is here: Meet Yubico at Microsoft Ignite 2024 On the heels of announcing the availability of Yubico Enrollment Suite for Microsoft users today, we’re excited to be back at Microsoft Ignite in Chicago this week to meet with all our valued customers and partners. If you’ll be at the conference, be sure to visit us at booth #333 to see live demos of […] Read more Microsoft Microsoft Ignite Yubico Enrollment Suite Yubico FIDO Pre-reg YubiEnroll -
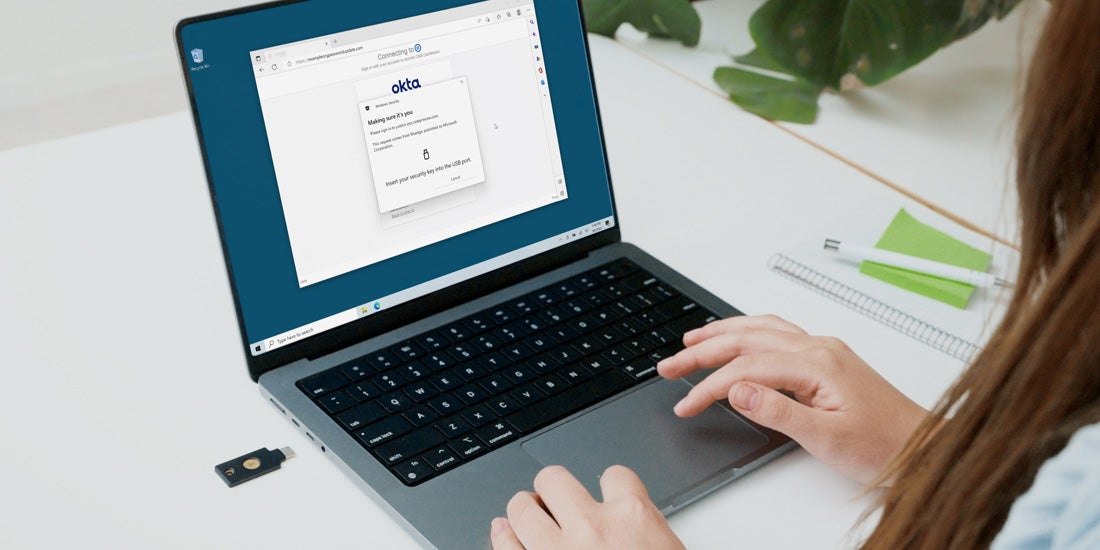
Yubico Enrollment Suite with Okta now available: An inside look at how Okta became a phishing-resistant enterprise Phishing-resistant users build phishing-resistant enterprises. With the growing sophistication of cyber threats, enterprises that can efficiently raise the bar for security helps ensure protection of users and their data to effectively drive digital acceleration. To help organizations achieve phishing-resistance at scale, we recently announced the general availability of Yubico Enrollment Suite – a set of […] Read more Okta Yubico Enrollment Suite Yubico FIDO Pre-reg YubiEnroll -

Yubico submits YubiKey 5 FIPS Series for FIPS 140-3 validation We’re excited to share that the YubiKey 5 FIPS Series latest 5.7 firmware has completed testing by our NIST accredited testing lab, and has been submitted to the Cryptographic Module Validation Program (CMVP) for FIPS 140-3 validation, Overall Level 2 and Physical Level 3. This marks a significant milestone in our ongoing commitment to providing […] Read more FIPS NIST YubiKey 5.7 YubiKey FIPS Series -

Available now: YubiKey Bio Series – Multi-protocol Edition keys expand phishing-resistant authentication options for enterprises As adoption of biometric logins continues to increase globally, enterprises and cybersecurity teams require stronger security combined with user convenience to improve user adoption of multi-factor authentication (MFA) and ensure productivity. Hardware security keys that leverage biometrics, like the YubiKey Bio Series, enable organizations to do so by offering portable, user-friendly seamless functionality – all […] Read more PIV smart card YubiKey 5.7 YubiKey as a Service YubiKey Bio YubiKey Bio Multi-protocol Edition
