Over the past few months, Yubico has been working closely with the U.S. National Institute of Standards (NIST) National Cybersecurity Center of Excellence (NCCoE) to improve mobile authentication methods for public safety professionals and first responders. Today, we’re happy to share that this guidance is now available in the form of a three-volume draft practice guide: NIST Special Publication 1800-13, Mobile Application Single Sign-On: Improving Authentication for Public Safety and First Responders.
This has been an important project for Yubico and the NCCoE as simple, secure access to critical data can often be a matter of life or death in an emergency response scenario. In high-alert situations, first responder and public safety personnel are often dispatched in the field and are heavily reliant on mobile platforms to access data in real-time that’s needed to deliver proper care. This data may include personally identifiable information (PII), law enforcement sensitive information, or protected health information (PHI), and it is imperative that access to this type of information is highly protected. However, complex and cumbersome authentication requirements to access sensitive information that cause even the slightest of delays in the emergency response process, can potentially risk the life of an individual.
To mitigate the security and access challenges for public safety and first responder personnel, the NCCoE collaborated with several technology vendors, including Yubico, to develop mobile authentication requirements and implement a reference design that assembles commercially available technologies that support the following open standards:
- Internet Engineering Task Force (IETF) Request for Comments (RFC) 8252, OAuth 2.0 for Native Apps
- FIDO Universal Second Factor (FIDO U2F) and Universal Authentication Framework (FIDO UAF)
- Security Assertion Markup Language (SAML) 2.0
- OpenID Connect (OIDC) 1.0
Yubico was a core contributor to this process. The reference implementation, which is documented in the practice guide, uses the NFC-enabled YubiKey (YubiKey NEO) in combination with Federation technology OpenID Connect to strongly secure user access to sensitive applications, improve usability and efficiency of user account management, and share identities across organizational boundaries.
It was recognized early on in the project that reliance on passwords alone can expand the scope of a single data compromise from one service to multiple services due to password reuse. The use of FIDO U2F for authentication provides protection beyond the password, and eliminates problems with social engineering, man-in-the-middle attacks, replay attacks, and phishing, which all present real threats to password-based and OTP-based (SMS, mobile push) authentication systems.
The following diagram from the NCCoE practice guide illustrates the recommended authentication flow for a native app on an Android device using standards-based technologies such as OAuth 2.0, OpenID Connect / SAML, and FIDO U2F with the YubiKey as the trusted second factor.
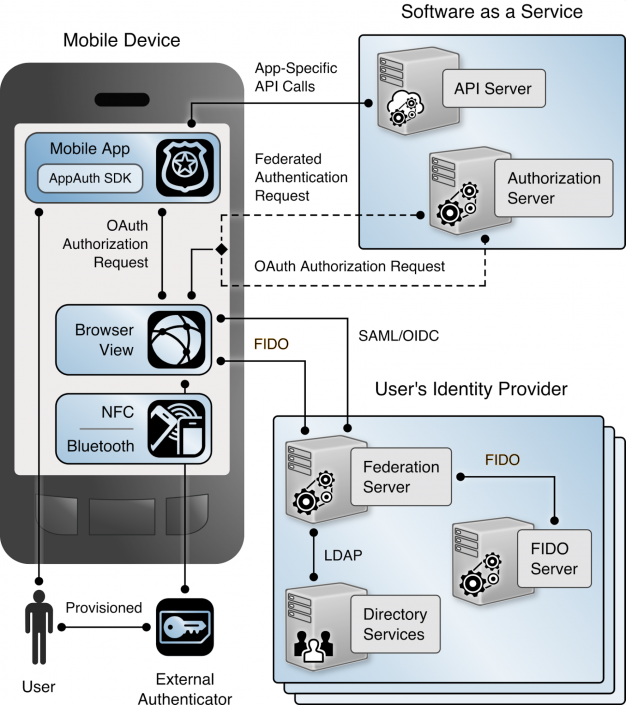
The OAuth 2.0 for native apps specification requires that applications use a system browser for making authorization requests. This allows a Software-as-a-Service (SaaS) provider, such as Motorola Solutions or GIS, to redirect authentication back to the user’s agency or enterprise via a standard authentication protocol such as OpenID Connect or SAML.
Using the system browser also enables the built-in operating system (OS) support for FIDO U2F authentication to be used without requiring special support in the native apps. This allows a generic SaaS application to support thousands of different identity providers, and different types of external FIDO U2F multi-factor authenticators (like the YubiKey) within a single native application. This avoids having to customize native apps for each organization and instead, allows the reuse of generic components that can make these systems available to even the smallest of organizations.
The combination of FIDO, OAuth, and SAML/OpenID Connect has been shown to be a robust and flexible solution for public safety use cases. In fact, one of the collaborators in the practice guide, Motorola Solutions, has incorporated this model into their commercial product PSX Cocpit, which is currently being deployed in a number of verticals.
From an end user perspective, these standards-based technologies are delivering a simple touch-and-go experience while maintaining the highest levels of security. To access sensitive data within a mobile application, first responder personnel will only require an NFC- and FIDO U2F-enabled hardware authentication device such as the YubiKey NEO. By simply touching the device to their phone, they will be securely authenticated to the app within seconds.
This particular project with NCCoE targets a first-responders use case, however the practice guide is equally applicable to many enterprise mobile scenarios. For more information on the project and to download the Mobile Application Single Sign-On practice guide, please visit the National Cybersecurity Center of Excellence (NCCoE) website. The NCCoE is also accepting public comments on the guide until June 18, 2018.





