What is Zero Trust?
The zero trust approach is an IT security model that demands every person and device provide strict identity verification to access network resources, whether or not they are inside the network perimeters. Zero trust is a holistic network security approach that is technology agnostic. Thus there is no single specific technology associated with a zero trust architecture.

Zero Trust Definition
Zero trust security starts with the premise that no one from inside or outside the network is trusted. Instead, as an added layer of security, everyone attempting to gain access to network resources must provide verification. This is intended to prevent data breaches. Zero trust security was coined by Forrester Research security analyst John Kindervag.
The zero trust approach is an IT security model that demands every person and device provide strict identity verification to access network resources, whether or not they are inside the network perimeters. Zero trust is a holistic network security approach that is technology agnostic. Thus there is no single specific technology associated with a zero trust architecture.
Zero trust draws on technologies such as analytics, encryption, file system permissions, identity and access management (IAM), multi-factor authentication (MFA), orchestration, and risk analysis. Zero trust also relies upon governance policies such least privileged access policies.
Traditional IT network security works like a castle-and-moat. It is difficult to gain access from outside the network or castle. However, everyone inside the network (or moat) is implicitly trusted. This means that all an attacker needs to do is gain access once.

This castle-and-moat security model may have worked for traditional IT network systems but becomes less tenable as data is spread across cloud vendors. In this instance, there is no firm network perimeter. Zero trust access shores up this weakness.
There are two primary motivators for a hacker. One is financial, and if money is the motive, a hacker will take the path of least resistance. As breaching the perimeter has become easier, organizations have countered with a zero-trust approach.
The other motive is disinformation or access to strategic information. Nation states and similar entities are willing to make very long term plays to get inside an organization. This broadens the attack landscape and leads naturally to the discussion of zero trust.
How Does Zero Trust Work?
There are several basic principles a zero trust security model is founded on, and all are aimed at reliably identifying the user an their intent:
- Attackers are everywhere. A zero trust approach assumes that attackers exist both inside and outside of the network, so no machines or users can be trusted by default.
- Endpoint security. A zero trust framework assumes the endpoint is untrusted. Endpoint management will validate if a device has adequate security controls. Endpoint security needs to extend to the authenticator as well to ensure only approved devices are used and private key material is properly secured.
- Least-privilege access. Zero trust security grants least-privilege access. This means minimizing exposure between sensitive parts of the network and each user by giving users only the access they need. This moves away from a trust everyone inside or even a trust-but-verify approach and toward more of a never trust always verify, need-to-know model for information.
- Microsegmentation. Zero trust networks use microsegmentation to maintain security. By breaking security perimeters up into smaller regions on separate parts of the network based on data classification with separate access, users cannot access different zones without additional authentication.
- Multi-factor authentication (MFA). MFA is a cornerstone of zero trust security. Ensuring users are properly validated through strong authentication measures before granting them access. It’s worth noting that if a weaker 2-factor authentication (2FA) system is implemented and compromised, it can undermine zero trust by falsely authenticating users.
- Access control. Zero trust frameworks must minimize the network attack surface by placing strict controls on user access and device access, and monitoring how devices access the network to ensure each one is authorized. Based on data classification, access controls will focus on protecting key systems by providing the least privilege to perform a job.
Strong authentication and MFA
Multi-factor authentication (MFA) is one of the best options to establish trust about users, but not everything that is called MFA is strong authentication. Actual strong authentication always has three qualities:
- It does not rely solely on shared secrets/symmetric keys at any point. This includes passwords, codes, and recovery questions.
- It uses hardware to robustly repel credential phishing and impersonation. While cautious users are always welcome, strong authentication assumes some attacks will succeed and prevents them. This requires hardware to store the private key to ensure it cannot be stolen.
It is scalable and easy to use. A strong authentication system must be widely deployed and convenient to be of use.
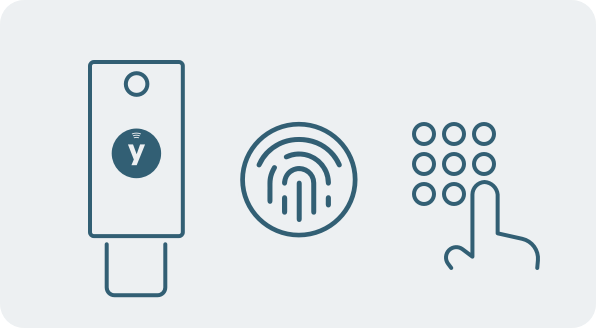
Multi-factor Authentication: Passswordless + PIN or Biometric
Multi-factor with combination of a hardware authenticator with user touch and PIN, to solve high assurance requirements such as financial transactions or submitting a prescription
See more on strong authentication and how to implement zero trust security framework below.
Defense in Depth vs Zero Trust
A defense-in-depth information assurance strategy puts layers of redundant measures in place to defend against a vulnerability exploit or a security control failure. Like the similarly named military strategy, defense-in-depth is centered on the idea that one defense mechanism cannot catch all attacks and thus a defense-in-depth strategy is used to thwart attacks that get by different types of controls.
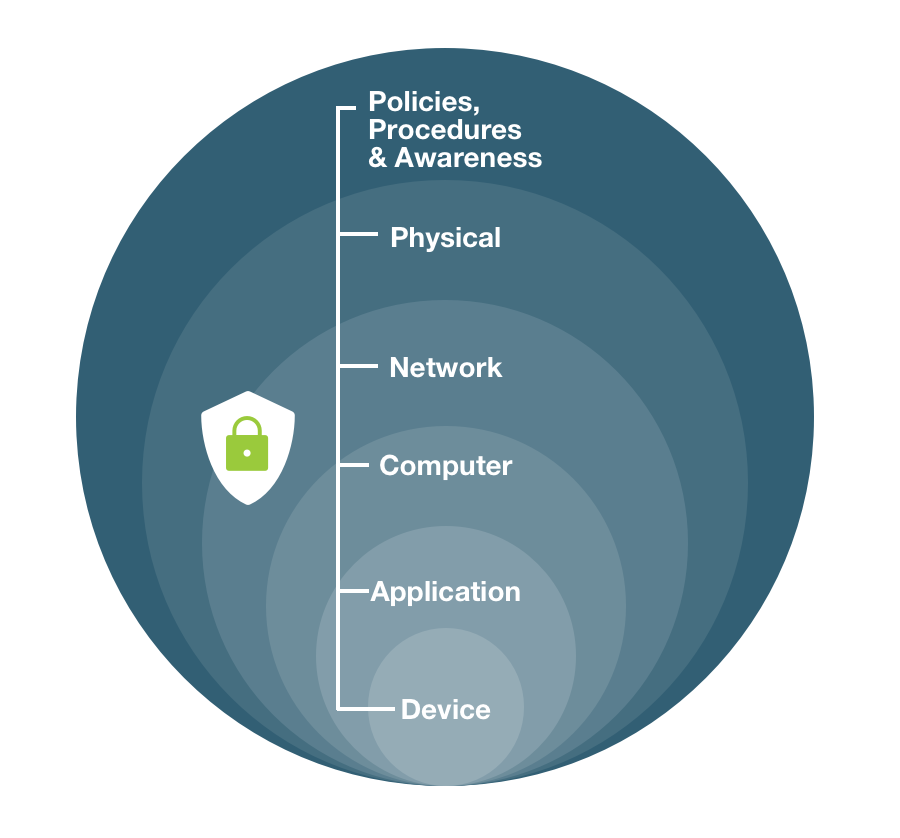
Use cases for traditional defense-in-depth cybersecurity include product design, end-user security, and network security.
A zero trust environment may leverage defense-in-depth security strategies, but the two are not equivalent. The difference is the zero trust refusal to trust all users and devices and requirement of verification for all, inside and outside any network perimeters. This remains the same irrespective of how many layers of controls the defense-in-depth strategy adds, or which kinds of monitoring might also be in place.
Benefits of Zero Trust
Effective access control. Zero trust deploys endpoint security, identity verification, least privilege controls, microsegmentation, and other preventative techniques to deter attackers and limit their access to applications, data, and networks. As such, it is one of the most effective means of organizational access control.
Borderless strategy. As the number of endpoints in a network grows and infrastructure expands to include cloud-based servers and applications, establishing, monitoring, and maintaining secure perimeters becomes more difficult. Work from home and remote workforce concerns exacerbate this issue. Zero trust accommodates any number of devices and users with equally high security.
Improve insight. A cloud-based, zero trust model streamlines the security stack and increases visibility into network traffic, as cloud-based vendors monitor, manage, troubleshoot, patch and upgrade infrastructure. Additionally, the model should include insight into endpoint security hygiene and authenticators.
Minimize risk and damage. By restricting user access and segmenting the network to reduce the attack surface, a zero trust model reduces time-to-breach detection and helps the organization minimize damage, prevent the export of customer data, and contain breaches—even from internal users.
Enhance user experience. Eliminate the need for users to re-authenticate throughout the day, based on access policies and risk assessments, and remember complex passwords with mechanisms like single sign-on (SSO) and strong MFA.
How to Implement Zero Trust
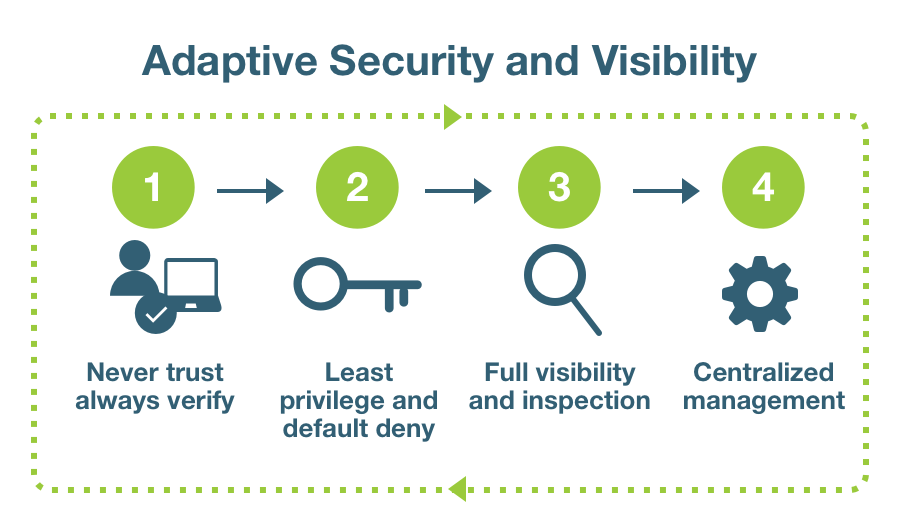
In general, organizations implement zero trust security and a zero trust network model in several steps:
Identify the attack surface to protect
Start by re-examining all default access controls. There is no such thing as a trusted source in a zero trust model, which assumes attackers are present both inside and outside the network. Every point of access is potentially an attack surface, and each access request must be authorized, authenticated, and encrypted.
Identify sensitive data, assets, applications and services (DAAS) to better define the attack surface. Classifying data based on sensitivity and access needs is critical. Identify any gaps within the infrastructure and assess the existing organizational security toolset. The most critical assets must receive the security architecture’s highest level of protection.
Map transaction flows
Map the transaction flows and create a directory of all assets. Determine which users need privileged access to sensitive information and where that information lives. Ensure there are compatible security access controls in place in light of how different DAAS components interact.
Build a zero trust architecture
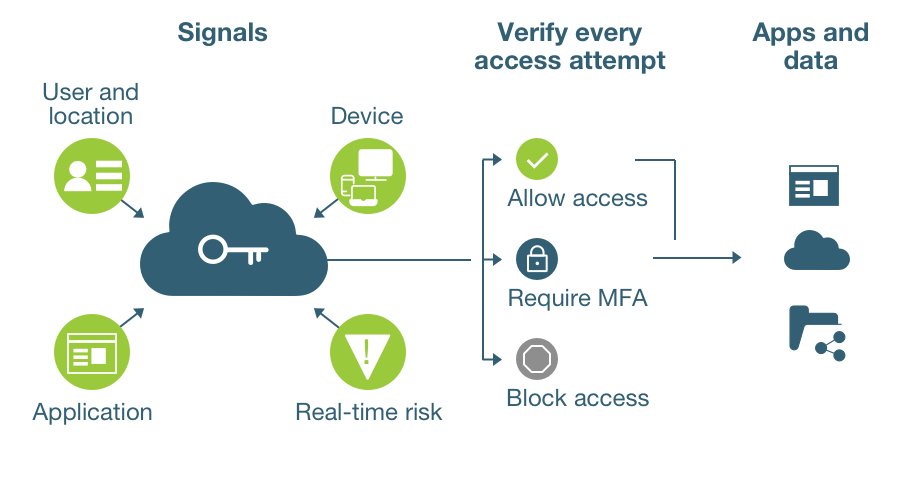
A zero trust model minimizes damage from breaches and stops them altogether relying on a variety of preventative techniques as described above. Build a zero trust security architecture using MFA, least-privilege access, and microsegmentation, ongoing auditing, and controls that are adaptive to the risk context.
Create the zero trust policy
Access-list rules are an import part of zero trust policies. These rules allow only authorized users to access specific resources with specified applications in the right locations at the right times. The firewall blocks traffic that doesn’t match a rule automatically. This is a crucial starting point for several reasons.
First, the task of identifying and blocking every application that should be denied access is endless. It’s far easier to identify the applications that support your business.
In addition, all malicious activity and breaches necessarily happen on allowed rules. Allow only the traffic required for business and focus security on that allowed traffic.
Zero trust policy asks and answers “who, what, when, where, why, and how” questions to determine: whether to block or allow traffic; and how to protect each attack surface with a unified security policy.
Q: Who should access a resource?
Answer this question with User-ID, authentication policy, and strong MFA. Granting least-privileged access only to groups, individuals, and devices that have legitimate business reasons to require access to a resource maximizes access control.
Authentication policy should verify user identities for every attempt to access resources. Protect sensitive applications and services with strong MFA by requiring at least one additional strong authentication factor before allowing access to sensitive resources.
Q: Which application is used to access the resource?
Answer this query by creating application-based Layer 7 policy, rather than Layer 3 or Layer 4. Layer 7 policy identifies applications regardless of protocol, port, or evasive tactics so only the right applications can access the network. Layer 3 and Layer 4 policy leaves ports open to invasive applications because it relies on IP addresses an attacker can spoof.
Prevent invasive applications from accessing the network via non-standard ports by setting the service to application-default to enable applications safely on their default ports.
Q: When do users access the resource?
Address this question for applications users access only at certain times and prevent suspicious access during off-hours by applying a schedule to the zero trust policy rule. This prevents attackers who attempt to reduce the chance of discovery by exfiltrating data outside of normal business hours.
Q: Where is the resource located?
Answer this by including the destination resource location in the zero trust policy. Restrict the source (IP address and zone) of the traffic as appropriate.
Q: Why do users access the data, and what is its toxicity or value if lost?
It is critical to understand the toxicity of data to best decide how to tag it for use in policy, what to do with data after use, and how to protect it most effectively. Understand data’s toxicity by classifying the data. What makes the data worth protecting? If an attacker exfiltrated the data, would you have to disclose the data loss?
Use data classification tools to gain insight into metadata. Set up data filtering to prevent loss of sensitive data.
Q: How should resource access be allowed?
Answer this question by applying best practices to guard against application traffic threats:
- Apply the least-privileged access philosophy to security policy. Only users with legitimate business reasons should access only the applications they need for business purposes, and only in the proper way and at only the proper times.
- Consistent threat protection. Consistently apply threat prevention and policy across all locations (cloud, endpoints, network), for all users, local and remote. This way, the policy follows all users, applications, and resources everywhere.
- Manage sensitive data throughout its life cycle. After use, abstract sensitive data using tokenization, encryption, or masking. Dispose of stale data by deleting or archiving it.
- Holistic security approach. A zero trust network architecture remains one piece of a holistic security strategy. A single technology or strategy cannot prevent all breaches. A holistic approach ensures network safety by incorporating a variety of detection, endpoint monitoring, and response capabilities.
Q: How do you trust the authentication mechanism?
Answer
- Authentication mechanism should be based on asymmetric cryptography compared to share secrets which can easily be copied, stolen and reused
- Authenticators need to store private key material in hardware where it cannot be stolen
- Validate authenticators by attesting to their validity
Monitor and maintain
Monitor, analyze, and log all data and traffic without interruption. Determine where anomalous activity occurs and monitor surrounding activity closely. Although a zero trust model is mostly preventative, real-time monitoring capabilities are essential to the ability to identify and remediate intrusions.
Strong authentication
It is critical to implement and enforce strong authentication that is based on the highest authentication standards. Authentication needs to be based on asymmetric cryptographic mechanisms compared to shared secrets. Shared secrets, such as passwords, are easily stolen or phished. With asymmetric cryptography, that is built into the PIV (smartcard) and FIDO standards, a unique key pair is generated where the web site (relying party) holds a public key and the user holds the private key. When the user attempts to authenticate, an authentication ceremony is performed requiring both keys. If the public key is stolen, it is no use without the private key. Given that the private key needs to remain private, strong authentication needs to ensure that private key material is generated and stored in hardware. Private keys stored in hardware cannot be copied or stolen.
Besides using asymmetric cryptography that is stored in hardware, the credentials need to be bound and limited to the service that is registered to use the credential. This is another level of strong authentication that ensures that the authentication ceremony cannot be performed by a phishing site.
Ideally strong authentication would fully leverage an asymmetric cryptography approach eliminating the need for passwords. This is not always possible in all circumstances but at a minimum implement MFA that leverages these security approaches.
This means enhancing basic two-factor authentication (2FA) with something you know such as a password, along with a hardware-based cryptographic token, such as a FIDO key or smart card.
Strong authentication builds trust in user identity. When the user identity and infrastructure itself are more trustworthy, users can be more confident in their interactions and the incidence of phishing will be eliminated. However, it should be noted that while phishing of login credentials can be prevented, strong authentication would not stop a user downloading malware from a malicious link since there’s no authentication involved in that exploit. This is why organizations use layered security, of which strong authentication is a vital part.
Current Use Cases for Zero Trust
Zero trust is in some sense a security goal. But in reality, you can’t operate in a truly zero trust environment and provide a satisfactory user experience. Could you imagine walking down the street, and thinking that everybody posed a potential threat? You wouldn’t want to operate a business or be on the street at all.
The zero trust paradigm is based on the idea that trust and security must have small, finite perimeters. At an absolute extreme, zero trust means nothing can be trusted: not the user, not the computer, not the communication.
But that’s a losing, endless battle. The ultimate goal in the zero trust conversation, then, is to change it from zero trust to some very limited trust based on strong proof of identity that then binds to strong authentication. Strong authentication brings that trust factor to the conversation, offering a route toward zones of safe limited trust.
With strong proof of identity, bad actors lack anonymity, and are less likely to do malicious things. Ordinary people might even be more likely to take care of their actions when repercussions can always be tied back to them as individuals.
The traditional approach on the market is that you can’t trust anything. This results in installing numerous agents on every computer, expiring user sessions and making them re-authenticate repeatedly—all of the things that make for poor user experience.
A rational, evidence-based technology for trust decisions is valuable. It allows for a practical approach to zero trust security with an appealing user experience. The Yubico zero trust solution starts with hardware-based authentication keys that provide the foundation to making zero trust pragmatic.
Ultimately, users are human meaning they are mobile, unpredictable and access systems from a variety of locations and on different devices. This means they need strong authentication. The ability to establish the identity of a trusted user provides a new level of confidence.
Use case: transitioning online during a pandemic

In 2020 as the coronavirus pandemic unfolded, CIOs and CISOs of traditional brick and mortar companies such as financial services, insurance companies, and healthcare organizations were all faced with a tremendous challenge: determining whether their existing infrastructure would be able to support a workforce now working from home. That includes everything from licensing to bandwidth to the core technologies—such as VPNs and related technologies which are at this point considered antiquated.
The next step for those companies by necessity was to shore up those gaps, and there were many. For example, whereas a cloud-based organization doesn’t have a VPN or an accompanying need to be in a physical office in order to access any such network-attached device, many brick and mortar companies were now quickly forced to move to the cloud. They in turn lost their old network perimeters and thus traditional control of their environment.
Now forced by the pandemic and remote work to consider zero trust, many businesses are considering what a service-based model could look like. It might start with one identity that is used in multiple places—a federated identity and a single sign-on experience.
However, months into a pandemic, even a Fortune 500 company is probably still planning this scale of pivot. For small-medium size organizations, it’s a more significant transition, and achieving a zero trust environment may not even top the organizational list. In reality, IT is hoping to adopt best of breed technologies that are going to meet organizational needs, and these are probably cloud-based.
The ongoing struggle will always be between cost and functionality. If businesses need to deploy large quantities of infrastructure in order to enable zero trust, it costs more money, and they will struggle with it.
Solution: A single sign-on, zero trust environment
Currently, enterprises such as Google deploy strong authentication systems, such as Yubico, as part of their zero trust strategy. This offers them high assurance about the status of their computers, including whether they have malware, device encryption, and passwords.
This type of single sign-on technology enables apps and programs to have an understanding of the health of the user’s computer and some high level of trust about the user themselves. Whether the gatekeeping sign-on programs are Microsoft Office 365, Google, or others, enabling true multi-factor strong authentication is the first step toward a successful zero trust initiative.
It’s worth noting given the ease of use of YubiKey, that identity providers can make SSO trust zones more targeted to risk levels. If a user needs to access a more sensitive site, the identity provider will require the user to re-authenticate. With a YubiKey, this could be as simple as touching the device to proceed. So it’s easy for varied levels of security to be provided with the same user workflow.
Just as critical is the ability to make an assessment about the health of an endpoint. From a hardware perspective, the challenge with any tool for authentication is health assessment of that device. If malware is installed on an endpoint that the user accessed to strongly authenticate, this introduces risk and undermines the zero trust environment. A YubiKey is a dedicated hardware authenticator and as a result, malware cannot be installed on the device. As part of a zero trust model, YubiKeys provide the ability to cryptographically validate the manufacture of the authenticator on registration. This is the root of trust. In fact Yubico goes further to ensure a trusted supply chain in the manufacture of that authenticator which is critical if the Yubikeys are to be the foundation of the trusted environment. This solves problems with supply chain infiltration and challenges in using mobile devices such as a smartphone app as the root of trust.
Does Yubico Offer Zero Trust Solutions?
Yes – Yubico provides a range of strong authentication keys that can form the foundation of a zero-trust architecture. By validating a user using strong authentication, organizations can provide secure access to applications, networks, information and services. Based on open standards, YubiKeys integrate into Identity Providers and network based zero trust solutions. YubiKeys support multiple devices (PCs, smartphones, servers) and multiple authentication protocols, including FIDO 2. Yubico’s YubiEnterprise Services include YubiEnterprise Subscription easing procurement, upgrades and support and YubiEnterprise Delivery which safely puts the devices into the hands of a distributed workforce both remote and in-office.
Learn more:
- Zero Trust Architecture
- Zero Trust Framework
- Zero Trust Network
- Zero Trust Security
- Zero Trust Solutions
- Zero Trust Strategy
- Yubico Q&A with John Kindervag, creator of Zero Trust
Get Started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

