What is a Zero Trust Framework?
The term zero trust (ZT) or zero trust network access (ZTNA) refers to a comprehensive security approach and framework that fundamentally redefines the traditional notion of trust in network security.
Zero Trust Framework Definition
The term zero trust (ZT) or zero trust network access (ZTNA) refers to a comprehensive security approach and framework that fundamentally redefines the traditional notion of trust in network security. In a broader sense, it is typically defined by the following characteristics:
No implicit trust. A zero trust security strategy operates on the principle that no user, device, or system, inside or outside the network, should be inherently trusted. Trust is not determined by location or previous access.
Identity-centric. It focuses on verifying user identities and devices attempting to access resources and continuously monitors and authenticates them. Continuous monitoring of network traffic, user behavior, and device health are some of the aspects used to detect anomalies and potential security threats to network infrastructure in real-time.
Micro-segmentation. Zero trust security models divide networks into smaller, isolated segments to limit lateral movement for potential attackers. Access to resources is strictly controlled and only granted when needed.
Least privilege access. Users and devices are only granted the bare minimum level of access necessary to perform their tasks, reducing the attack surface.
Policy-based access. Access control is determined by dynamic policies based on user context, device posture, and the sensitivity of the data or resources being accessed.
Encryption. All sensitive data is encrypted where possible, to protect it from unauthorized access, both in transit and at rest.
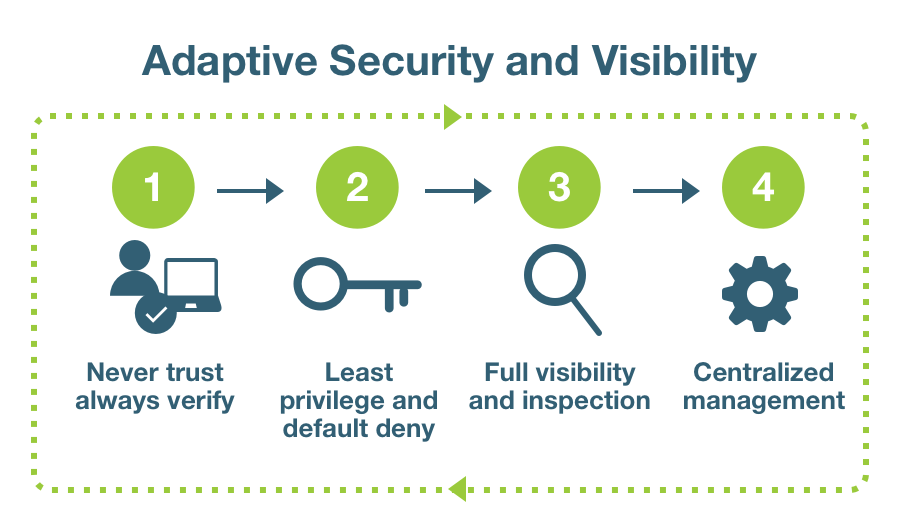
Adaptive security. A zero trust security framework adapts according to the evolving threat landscape, such as baseline user behaviors and the state of devices, allowing for a more resilient and agile security posture.
Zero Trust Framework FAQs
What is a Zero Trust Framework?
The zero trust model is a strategic shift toward a more agile, identity-centric and data-focused approach when compared to existing paradigms. It is designed to mitigate the limitations of traditional security models, address the evolving complexity of modern IT environments, and offer a more robust and adaptable security posture.
Perimeter erosion. Traditional network security models rely heavily on a secure perimeter. However, remote work, cloud computing, mobile devices, IoT, and other modern factors render the network perimeter porous and ill defined. A zero trust framework acknowledges that threats may originate both inside and outside the network.
Advanced persistent threats. Cyberattacks have become more sophisticated and persistent, with attackers often operating undetected within a network for extended periods. A continuous monitoring and verification approach helps detect and respond to these threats in real-time.
User mobility. Users may access network resources from various devices and locations, which makes authentication and authorization for every attempted connection critical.
Data-centric security. A zero trust framework shifts the focus from protecting the network itself to protecting the data, which is often the primary target of cyberattacks.
Compliance and privacy. Many industries and regions have stringent data protection and compliance requirements, such as GDPR and HIPAA. A zero trust framework helps meet these requirements by providing granular control and monitoring of data access.
Cloud and virtualization. Zero trust is well-suited to securing data and applications in the dynamic environments that cloud and virtualized infrastructures present.
Endpoint diversity. The proliferation of various endpoint devices, including smartphones, tablets, and IoT devices, requires a more flexible approach to securing access to resources.

What is Zero Trust Architecture?
A zero trust network architecture security framework provides a structured, comprehensive approach to designing and implementing an adaptive security environment:
Micro-segmentation. Within a zero trust architecture, network segments are divided into smaller, isolated zones, and access between them is controlled on a per-application or per-resource basis. This reduces lateral movement within the network in the event an attacker – internal or external – is attempting to collect sensitive data or stage an attack.
Least privilege access. Users and devices are always granted the minimum level of access required for their specific tasks to minimize the attack surface.
Encryption. Within a zero trust architecture framework, data is encrypted both in transit and at rest, to render it much more difficult for attackers to consume or exploit, even if unauthorized access occurs.
Automation and orchestration. Zero trust architecture leverages automation to enforce security policies, respond to security incidents, and adapt to changing security requirements and threats in real-time.
How Does a Zero Trust Framework Work?
While largely non-prescriptive from a technical point of view, a few key principles do inform a zero trust framework:
Identity-centric security. A zero trust strategy verifies users, devices, and application identities with rigorous authentication processes before granting access to network resources.
Continuous monitoring and analytics. A zero trust framework monitors network traffic, both user and account behavior, and even application usage in real-time, to differentiate nominal from suspicious activity.
Policy-based access. Dynamic policies that consider various factors, including user context, device geography, and data or resource sensitivity, are used to determine access control.
Adaptive security. Zero trust principles allow the system to adapt to evolving threat landscapes, user behaviors, and the state of devices, in order to take a more flexible, resilient security posture.
Advantages of a Zero Trust Framework
There are several advantages a zero trust framework offers organizations, in terms of security, risk mitigation, and adaptability:
Enhanced security. Zero trust significantly improves security by reducing the attack surface and restricting lateral movement within the network. It focuses on identity verification and data protection, which are critical components of modern security, as opposed to network surface protection, often the goal of legacy frameworks.

Adaptive response to risk. The more resilient and agile security posture of a zero trust framework enables organizations to stay ahead of emerging security risks, since each risk can be mitigated or actioned without affecting the entire network at the same time.
Data protection. A data-centric zero trust approach ensures that data remains encrypted and protected, so that even if unauthorized users gain access to it, the damage is potentially minimized.
Real-time monitoring and response. Real-time monitoring and threat detection enable rapid responses to security incidents and more effective threat mitigation.
Reduced insider threats. Eliminating implicit trust reduces the risk of insider threats, an often overlooked facet of both hacks and leaks.
Improved compliance. Many regulatory requirements, such as GDPR and HIPAA, mandate a granular level of data protection and access control that zero trust innately provides.
Remote work support. Zero trust is well-suited for securing remote access to cloud-based services and resources, ensuring that users and devices in all locations are subject to the same rigorous identity verification and security controls.
Segregation of duties. Micro-segmented zero trust architecture and granular access controls allow organizations to segregate tasks, preventing conflicts of interest and unauthorized access to sensitive data and other resources.
Cost-effective. While implementing a zero trust framework may involve initial investments in technology and training, it can ultimately lead to cost savings by reducing the risk of data breaches and their associated financial and reputational costs in the event a breach or attack does occur.
Types of Zero Trust Frameworks
Zero trust frameworks are often implemented using a combination of technologies and strategies to achieve a balance of core zero trust principles and organizational goals. Not all solutions are applicable or required for every use case, but there are a few tools, however, that are commonly associated with robust zero trust frameworks.
Identity and access management (IAM). IAM solutions manage user and device identities and enforce access policies based on identity verification.
Multi-factor authentication (MFA). MFA enhances identity verification by requiring users to provide multiple forms of authentication before granting access. These may include something the user knows (such as a one-time password), something they have (such as a token or smartphone), or something they are (such as biometrics).
Software-defined perimeters (SDP). SDP solutions create a veil around resources, hiding them from unauthorized users, limiting exposure to attackers and reducing the attack surface.
Network access control (NAC). NAC solutions ensure that devices meet specific security requirements before allowing network access and reject any devices that don’t meet the criteria.
Endpoint detection and response (EDR). EDR tools continuously monitor endpoints for suspicious activity, help to identify and ultimately alert administrators so that they may respond to potential threats with as little delay as possible.
Data encryption. Data encryption solutions protect data from unauthorized access even if it is copied or leaked, using technologies like SSL/TLS and symmetric key encryption.
Security information and event management (SIEM). SIEM systems collect and analyze log data from networks and devices to help identify, aggregate, correlate and present security incidents in real-time. Such tools are invaluable when conducting forensic analysis after a breach, for instance.
Policy-based access control. Administrators often create policies based on context, device posture, and other factors. They then create dynamic access control solutions, often integrated with IAM, to enforce said policies.
Secure access anywhere. Zero trust security frameworks provide identity-based access to applications and resources, irrespective of their location (data centers, cloud, or remote).
Automation and orchestration tools. Automation tools, such as platforms for security orchestration, automation, and response (SOAR), help to automatically enforce security policies, respond to incidents, and adapt to changing security requirements.
Cloud security solutions. Cloud-native security services and tools, such as Cloud Access Security Brokers (CASBs), help extend zero trust principles to cloud environments.
How to Implement Zero Trust Frameworks
A successful implementation typically demands a combination of strategies, technologies, and best practices to establish a zero trust security framework based on the core principles of identity verification, least privilege access, micro-segmentation, and continuous monitoring:
Assessment and planning. Conduct a thorough assessment of the current IT environment, including networks, devices, applications, and data flows. Identify critical assets, sensitive data, and potential security risks.
Define a zero trust strategy. Determine specific security goals and objectives for implementing zero trust. Most importantly, identify the zero trust principles that align with your organization’s needs.
Create policies for access control. Create dynamic access control policies based on user context, device posture, and data sensitivity.
Compliance alignment. Ensure the zero trust implementation aligns with industry-specific compliance requirements applicable to the organization, such as GDPR or HIPAA.
Testing and validation. Conduct thorough testing and validation of the zero trust framework to ensure it meets security goals and operates as expected. This should be repeated as often as required, especially as the goal posts are moved in lockstep with the organization’s growth.
Increment and adjust. A successful implementation is the result of incremental improvements and adjustments over time, as fixes are deployed and issues or weaknesses are discovered, and never the initial setup.
Does Yubico Support Zero Trust Frameworks?
Yes. Yubico solutions like the YubiKey support zero trust frameworks, enhance security, and deliver secure access with strong authentication. YubiKeys are commonly used as a factor in MFA implementations within zero trust frameworks and offer a superior user experience. YubiKeys are resistant to phishing attacks because they require physical interaction to generate one-time codes. And Yubico’s solutions adhere to the FIDO (Fast Identity Online) Alliance and its open and standardized authentication protocols and standards, making them interoperable with various FIDO-compliant services and applications.
Learn more:
- Yubico Q&A with John Kindervag, creator of Zero Trust
- Zero Trust Architecture
- Zero Trust Network
- Zero Trust Security
- Zero Trust Solutions
- Zero Trust Strategy
Get started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

