What is Zero Trust Security?
Zero trust security is based on the premise that any entity – whether human or machine – with access to applications or systems on the network may have been compromised. As a result, any request to a shared network resource must always require verification, as an added layer of security to stop data breaches.
Zero Trust Security Definition
A zero trust security framework authenticates and authorizes all users, both inside and outside the organizational network, and validates them continuously for security posture and permission configuration before granting access or allowing existing access to data and applications to be retained.
Zero Trust security is often accompanied by the motto “Never trust, always verify”, and is applicable not only to enterprises with well defined digital boundaries, but also intended to provide a framework for enterprises undergoing digital transformation. The term endpoint security is sometimes used in conjunction with zero trust, and refers to the need to validate each and every existing endpoint in addition to endpoints added to a network as it expands. By including all endpoints, the coverage will encompass contractors, partners, and guest devices for instance, but also apps and devices used by employees to access work related data, regardless of device ownership. It secures hybrid cloud environments, both on-premises and remote workers, and ultimately aims to prevent attacks and threats from ransomware.
Security analyst John Kindervag originally coined the term zero trust security and shaped the original zero trust approach. The proposed IT security model demanded strict identity verification from each person and device to access network resources, irrespective of network perimeters. Zero trust security is a technology agnostic, holistic network security approach that is not associated with any one specific architecture, vendor, hardware type or application.
Instead, zero trust security draws from encryption, analytics, identity and access management (IAM), file system permissions, orchestration, multi-factor authentication (MFA), and risk analysis technologies. Moreover, zero trust security also relies upon least privileged access and other proven governance policies.

Zero Trust Security FAQs
What are the tenets of a Zero Trust Security Model?
There are several basic tenets of zero trust security. Enterprises that have successfully implemented a zero trust network are focused on reliably identifying their users and the intent of said users, with the below principles always top of mind:
Attackers are everywhere. A zero trust approach assumes that no users or machines can be trusted by default, because attackers can exist anywhere, both inside and outside the network.
Endpoint security. A zero trust security framework also assumes that endpoints cannot be trusted. Endpoint security management techniques are used to continually validate devices to check whether they can present the correct private key or other cryptographic material before being approved as a trusted device.
Least privilege access. Zero trust cloud security should always grant least privilege access. This model gives users only the access they need, to minimize exposing data or sensitive parts of the network that only a select few should have.
Network segmentation vs. microsegmentation. Typically, network segmentation breaks devices and their hosted applications on the network into multiple zones. Microsegmentation goes further, placing each device or application within its own segment. Thus, zero trust networks maintain higher security using microsegmentation, since attackers that manage to gain access to a device or endpoint cannot even move laterally within a designated zone.
Multi-factor authentication (MFA). MFA is a foundational element of zero trust security. Users must be validated using mechanisms that cannot be easily falsified or attacked, so that the implemented security infrastructure can verify the legitimacy of each endpoint reliably. The validation and identification techniques being employed must be both reliable and effective measures.
Access control. Zero trust security frameworks will often minimize the network attack surface by monitoring how devices access the network and placing strict controls on both user and device requests that are considered irregular or unusual. This principle is often highly correlated to least privilege but will almost certainly require step-up authentication in many instances as well.
What is Zero Trust Security Architecture?
How does zero trust security work in the context of practical architecture choices? According to NIST, zero trust security architecture “uses zero trust principles to plan industrial and enterprise infrastructure and workflows”. Typically, a zero trust architecture incorporates many of the aforementioned tenets such as microsegmentation, least privilege access, MFA, ongoing auditing of access, signal monitoring and other controls that are adaptive to risk context, into the overall design of a system or network. Although system architects and administrators must be pragmatic, it is important to realize that a zero trust security architecture is just one aspect of a holistic security strategy. Certainly, enterprises should implement software or hardware to cater to their specific needs, but ideally, should do so only after considerations are made regarding how it may or may not impact security within the bigger picture.
Unfortunately, there is no one-size-fits-all zero trust security strategy or technology that is capable of preventing all attacks and breaches, since all enterprises within different verticals and sectors will have different requirements. Thus, the holistic zero trust security approach should always incorporate a variety of techniques and more importantly, be adapted for the specific enterprise needs and context, to ensure network security worthy of the name, zero trust.
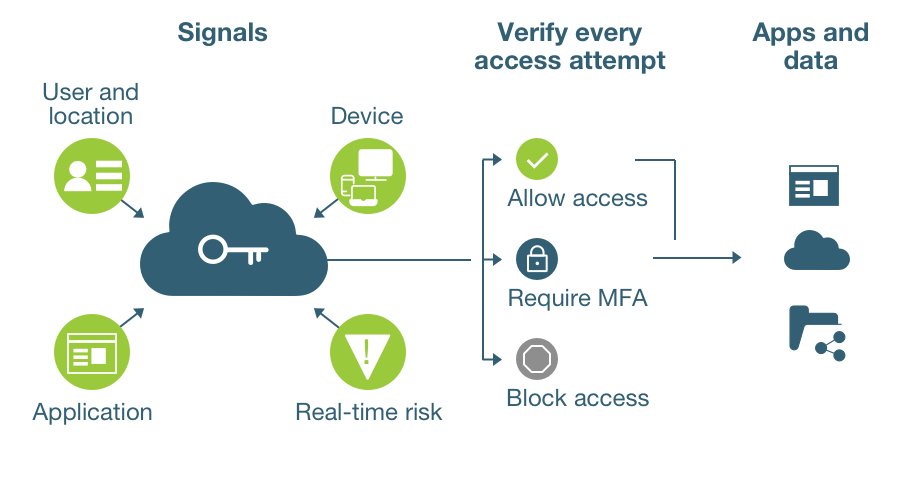
Why Zero Trust Security is Important
The zero trust security concept enhances security, and may reduce long-term costs associated with a breach. Zero trust security principles also offer more support for IT, cybersecurity teams and even end users if implemented correctly, because many of the underlying mechanisms can be automated and only require tuning over time. In practice, this means every user request inside or outside the perimeter will be authorized, authenticated, and potentially have their data encrypted in real time, using the best available tools.
This protects enterprises in several ways that other security models may be unable to, including:
- Extend threat visibility to improve proactive response and remediation since the security model is transparent
- More likely to stop malware or other attack from getting onto the network since all endpoints must be verified before gaining access using strong MFA techniques
- Enhance productivity and security for remote workers due to streamlined authentication and potentially recovery processes
- Reduce complexity of managing enterprise level security operations with automation tools and techniques
Who Uses Zero Trust Security?
There are a number of important use cases for zero trust security, including but not limited to:
Secure remote work. Edge security products may potentially offer a sense of false security for remote workers who connect via insecure channels or public cloud resources. Remote workers do have other reliable options to access the corporate network via virtual desktop infrastructure technologies or a VPN for instance, but these need to be properly managed, and zero-trust security is one potential solution.
IoT security and visibility. Zero trust security delivers two important benefits for IoT deployments. It helps administrators dynamically learn and maintain an inventory of devices, including IoT sensors, during discovery, and zero trust security may also automate security health monitoring since each device must communicate and ultimately authenticate, in a configurable and orderly manner.
Data center microsegmentation. A popular computing trend nowadays is to distribute services across multiple clouds and other hardware infrastructure to avoid singular points of failures and bottlenecks, but generally operate as a single overall entity. This model has several benefits, including improved reliability, performance, and scalability. However, the compromise of any one service can often lead to the compromise of the entire application, so zero trust security within data centers, clouds, and connected systems can protect data integrity, as it prevents free lateral movement between services should an attacker manage to compromise one or more components.
Uniform security. Zero trust security removes inherent bias stemming from device type, user status or device location. This levels the security playing field in a manner of speaking, since it requires the entire corporate infrastructure to enforce objective and granular security mechanisms that work together based on real world and empirical data.
Increased security visibility. Zero trust security streamlines device and end user authentication, whilst potentially centralizing security management and logging, depending on the system architecture. As a result, it offers unprecedented visibility and helps promote a broad view of the data, applications, and services wherever they reside within the enterprise.
Leverage existing and available network infrastructure. Zero trust principles can be deployed anywhere, including with users and devices that connect from or into public cloud and edge computing services.
Enhanced enterprise level security. Zero trust security techniques in the form of strong authentication such as the YubiKey, are currently being deployed by enterprises such as Google and Amazon. This type of MFA technology offers even a large enterprise a high level of assurance about user and device identity, reduces the possibility of a breach or malware, and minimizes or eliminates weak password usage.
What are the Advantages of Zero Trust Security?
There are many benefits of zero trust security:
Effective access control. A comprehensive zero trust security architecture deploys identity verification, endpoint security, microsegmentation, least privilege controls, and other preventative techniques in concert to deter and limit attacker access to data, applications, and networks. It is among the most effective organizational access control strategies on the market.
Borderless strategy. Among the greatest zero trust security benefits, is the ability for an enterprise to create a borderless strategy for any number of users and devices with equally high security as a traditional model. However, it is important to note that this does become more difficult to establish, maintain, and monitor secure perimeters as infrastructure expands to include applications and cloud-based services, and the number of endpoints in a network grows. This issue is exacerbated by remote and work from home concerns, but with continued vigilance, can definitely be overcome under a zero trust model.
Improved insights. A cloud-based, zero trust security approach increases network traffic visibility with real-time monitoring, patching, troubleshooting, and infrastructure upgrades. Most importantly, it also streamlines the security stack, and offers insight into authentication processes and endpoint security hygiene.Cloud security solutions. Cloud-native security services and tools, such as Cloud Access Security Brokers (CASBs), help extend zero trust principles to cloud environments.
Minimize risk and damage. By reducing the attack surface—segmenting the network and restricting user access, for example—a zero trust security model reduces detection, minimizes damage and mitigation time for breaches—even from internal threats.
Enhance user experience. Enterprise productivity and effectiveness can be increased by using mechanisms such as strong multi-factor authentication (MFA) and sign-on (SSO) to eliminate the need to remember complex passwords, reduce account recovery overhead and enable enterprises to re-authenticate users throughout the day, based on risk assessments and access policies without the need to distract users.
How to Implement Zero Trust Security
There are several steps to implementing a zero trust security framework:
Strong authentication and MFA. Among the best ways to establish a strong zero trust security foundation throughout an enterprise is by implementing multi-factor authentication (MFA). However, not all MFA is created equal and there exists varying degrees of strength. Strong MFA in particular, must always possess the following two characteristics:
- It does not rely solely on a shared secret or symmetric key. This includes codes, passwords, and even recovery questions. The authentication process must require the user or device to present a number of unique identifiers when prompted.
- It robustly repels impersonation and is even phishing-resistant. Strong authentication stems from the premise that some attacks will inevitably circumvent or breach one or more factors, but will ultimately be halted by the combination of all factors – such as the need to present a password, but also a private key that has been stored on hardware that remote attackers will not have physical access to.
After authentication has been considered, enterprises in general implement zero trust security platforms and a zero trust network model in several steps:
Identify the attack surface. Every point of access is potentially an attack surface, so the first step is to assess all default access controls and identify sensitive data, assets, applications and services (DAAS). Identify existing organizational security tools and any gaps in infrastructure. The most sensitive assets should receive the highest level of protection within the security architecture, but every access request must ultimately be authorized, authenticated, and potentially encrypted.
Create an inventory of assets and flows. Determine which users must have privileged access to sensitive information, where data and transaction flows are occurring, and finally, create an asset directory so that all endpoints are accounted for. Place security access controls that are compatible and suitable with the various DAAS components.
Incorporate zero trust architecture principles. A zero trust model stops breaches and minimizes damage from those that succeed using preventative techniques. Build a zero trust network security architecture using adaptive controls, microsegmentation, least-privilege access, automation and ongoing auditing.
Create a zero trust security policy. Start with access rules that allow only specific authorized users to access specific applications and resources, in the right geographical locations, and only at particular times. It’s easier to identify and allow authorized users than it is to identify and block every attacker, possible entry avenue or illicit application. A zero trust cyber security policy asks and answers questions about how and why to block or allow traffic and how to deploy a unified security policy to protect each attack surface.
Monitor and maintain. Monitor, log, and analyze all traffic and data continuously over time. Identify anomalous activity, determine where and why it occurs, and closely monitor surrounding areas. Real-time monitoring is critical to remediating against attacks, although zero trust security solutions are mostly preventative.
Does Yubico Support Zero Trust Security?
Yes. Yubico offers a range of strong authentication hardware keys and even a hardware security module (HSM), that serve to enable zero-trust architecture. By validating users with strong authentication, and storing their private keys in hardware, enterprises can offer secure access to networks, applications, services, and information.
YubiKeys integrate into network based zero trust security products and existing Identity Providers based on open standards. YubiKeys support smartphones, laptops, servers, and other devices, using widely adopted protocols such as FIDO2 and PIV.
The YubiHSM product lineup delivers advanced protection for certificate authority (CA) keys, database master keys, code signing, authentication/access tokens, manufacturing processes and component authenticity checks, IoT gateways or proxies, file encryption, cryptocurrency exchanges and more. The rise of threats like zero day exploits and malware makes software-based cryptographic key storage increasingly vulnerable for enterprises.
Finally, Yubico’s YubiEnterprise Services includes upgrades and technical support, YubiEnterprise Subscription eases procurement, and YubiEnterprise Delivery places devices safely into the hands of a distributed workforce, in-office or remote.
Learn more:
- Zero Trust
- Zero Trust Architecture
- Zero Trust Framework
- Zero Trust Network
- Zero Trust Solutions
- Zero Trust Strategy
- Yubico Q&A with John Kindervag, creator of Zero Trust
Get started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

