Note: This webinar was recorded on Oct. 27, 2015. The video recording is embedded at the end of this blog.
Ever wonder what’s under the Universal 2nd Factor (U2F) covers? How to build U2F into your own service or project? Or what’s the extended value of your YubiKey?
Now that U2F is catching fire as the protocol that defines strong authentication, we get a lot of these inquiries.
On Oct. 27, Yubico’s lead engineer, Dain Nilsson, will lay out all you need to know to understand the power of the protocol, the basic concepts for implementation, and the value of any U2F-enabled YubiKey.
The webinar, “Integrating U2F: From Concept to Implementation,” is scheduled from 8am to 9am PDT. This webinar is for those who use a U2F YubiKey but don’t quite know what happens behind the scenes. Or for those who want to add U2F into their own service or application.
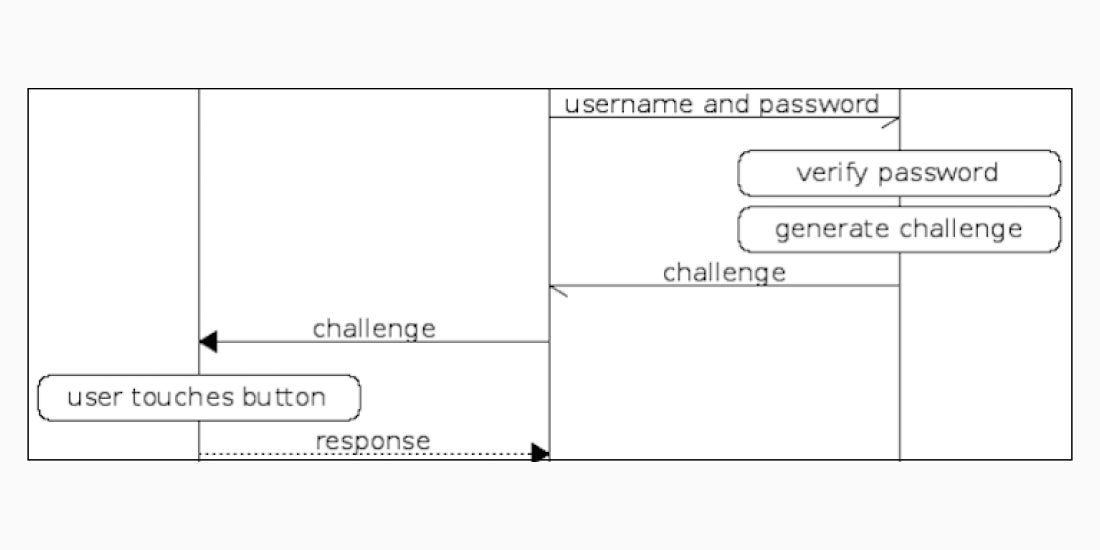
During the webinar’s demonstrations, Nilsson will take an existing service that relies on usernames and passwords and, using Yubico’s open source libraries in combination with U2F, will add the protocol’s two defined flows — key registration and strong authentication based on public key cryptography.
Nilsson will feature code samples using Python, which will be made available on GitHub, and outline the steps for implementing U2F. He will provide other practical details around enabling U2F with an existing online service.
Major online services — such as GitHub, Google, and Dropbox — are leading the way to protect their employees and global users with U2F. Millions of YubiKeys are in the hands of users across the globe. But U2F isn’t exclusive to mega services with giant dev teams — it’s straightforward to implement and simple enough not to require user training courses.
Yubico will show you how.