In an effort to protect the nation’s infrastructure and improve cybersecurity, the Executive Order 14028 and the Office of Management and Budget Memo M-22-09 took a strong stance to require phishing-resistant authentication for all federal agencies. The M-22-09 memo also specifies two standards-based authentication protocols that will satisfy the phishing-resistant requirements, FIDO2/WebAuthn and PIV smart cards.
In the Microsoft ecosystem, PIV smart cards have long been supported for desktop systems on Windows and macOS. Recently, the company announced a great win for government agencies and organizations already using smart cards by expanding support for PIV smart cards on mobile devices using YubiKeys.
If you read Joe Scalone’s take on FIDO2 for the federal government, you may be asking about the Microsoft customers that don’t have the PKI infrastructure to support smart card issuance, or for government users that are not PIV eligible. Or, about customers that are wanting to move to more modern FIDO2 based authentication and need to have support on mobile devices. These are great questions.
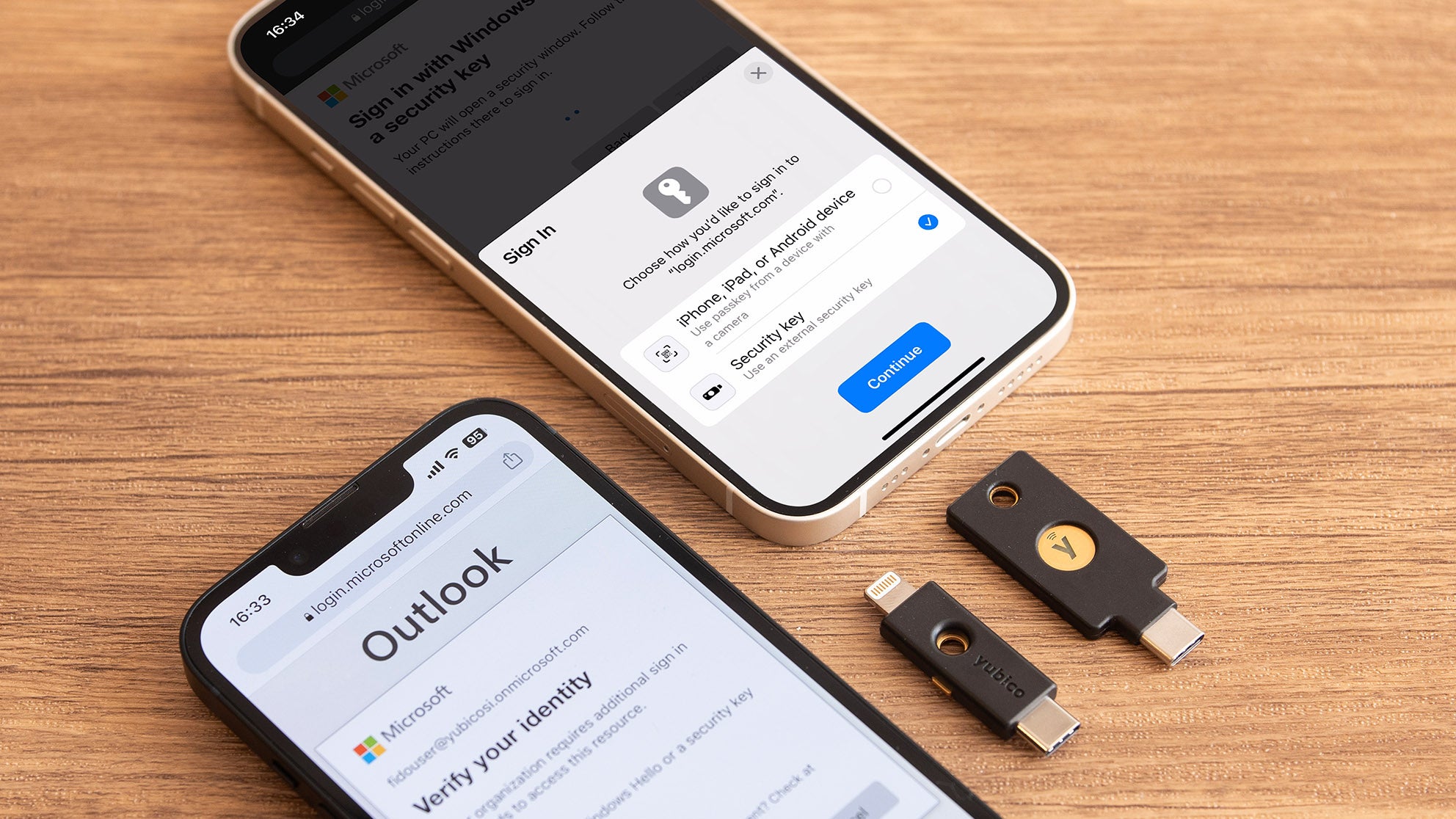
Entra ID (Azure AD) has supported the use of YubiKeys for FIDO2 passwordless sign-in since 2021, and customers have been waiting ever since to sign-in with their YubiKey from their mobile devices. Now, the tide is beginning to change. Microsoft recently announced General Availability for using FIDO2 security keys with Safari, and this new support goes beyond desktops and includes iPhones and iPads.
Now users can sign-in to any Entra ID protected web application on their iPhone or iPad using any of the supported browsers. This is what it looks like when you sign-in to office.com on an iPhone with a YubiKey 5Ci.
| 1. Open Safari and go to office.com | 2. Select Sign-in options | 3. Select Sign-in with a security key | 4. Select Security key or simply touch the YubiKey if it’s already plugged in. |
| 5. Insert and touch the YubiKey | 6. Enter the YubiKey PIN | 7. Touch the YubiKey again | 8. You are signed in! |
Conditional Access Policy Authentication Strengths
By now, every organization should be well on their way to a passwordless and Zero Trust journey. With support for mobile, organizations can now get a step further in their journey.
Conditional Access Policy Authentication Strengths was also announced by Microsoft this spring, allowing customers the flexibility to require PIV or FIDO2 everywhere except for the edge-cases where the protocols aren’t supported yet. This enables organizations to get closer and closer to a modern passwordless end-state where end-users are no longer allowed to use phishable authentication methods when accessing applications.
These Conditional Access Policies are powerful and flexible. With authentication strengths, organizations will be able to enable:
- Out-of-the-box policies that require phishing-resistant authentication including enforcing:
- Users use FIDO2 security keys, certificate-based authentication, or Windows Hello for Business
- Custom policies that require FIDO2 security keys, including enforcing:
- Users use any FIDO2 security keys like YubiKeys to access the environment.
- Users use specific YubiKey 5 FIPS series or other models by specifying the exact AAGUIDs. AAGUIDs are the IDs that FIDO2 security key vendors use to uniquely identify their device models.
- Custom policies that require certificate-based authentication, including enforcing:
- Users use YubiKeys as PIV smart cards to access the environment.
Remember how I said it was a journey? Well, native apps don’t support FIDO2 authentication yet on macOS and iOS. And yes, Android does not support FIDO2 authentication yet. Microsoft has committed to deliver these features, but they aren’t here yet. Nevertheless, we celebrate these great milestones and look forward to when organizations can finally get to passwordless everywhere.
How to get started using YubiKeys with Safari
If your YubiKey does not have a PIN set on it yet, then you will first need to set a PIN since Safari will not support setting the PIN. On iOS, there are not any convenient options to do this. The following steps will use macOS desktop with Yubico Authenticator to set the PIN, but other options exist such as using YubiKey Manager or using Chrome on macOS.
Set a PIN on macOS.
- Install Yubico Authenticator on macOS
- Open Yubico Authenticator
- Insert the YubiKey
- Select WebAuthn and select the Configure YubiKey options in the top-right
- Select Set PIN
- Set the desired PIN and select Save
A FIDO2 PIN is now set on the YubiKey. You can now register the YubiKey with Entra ID. You can now register using Safari on your iPhone, iPad or macOS desktop.
| 1. Open Safari and go to aka.ms/mysecurityinfo and type in username and select Next. | 2. Sign-in to your account using an authentication method(s) that is considered multi-factor, here we will use Temporary Access Pass (TAP). Type in TAP code and select Sign in | 3.Select + Add sign-in method | 4. Select Security key and continue to follow the prompts |
| 5.Indicate whether you are using NFC or USB (this also includes Lightning connector) | 6. Select Security key or simply touch the YubiKey if it is already inserted | 7. Insert the YubiKey or tap the YubiKey on the back of the phone and type in the PIN | 8. Scan or insert the YubiKey again and touch it |
| 9. Provide a nickname for the YubiKey and select Next | 10. Select Done | 11. Verify the new YubiKey is listed as a new authentication method |
——
For more information on how Yubico and Microsoft work together to help organizations prevent phishing with enforced FIDO and Azure AD CBA and YubiKeys on mobile devices, check out our webinar series here.