Note: This is a follow-up to our previous announcement of Yubico Authenticator 6 for Desktop. If you haven’t read it yet, we recommend you do so first. If you’re not yet familiar with the app you can read more about it, and about how to use Yubico Authenticator with the services you want to secure.
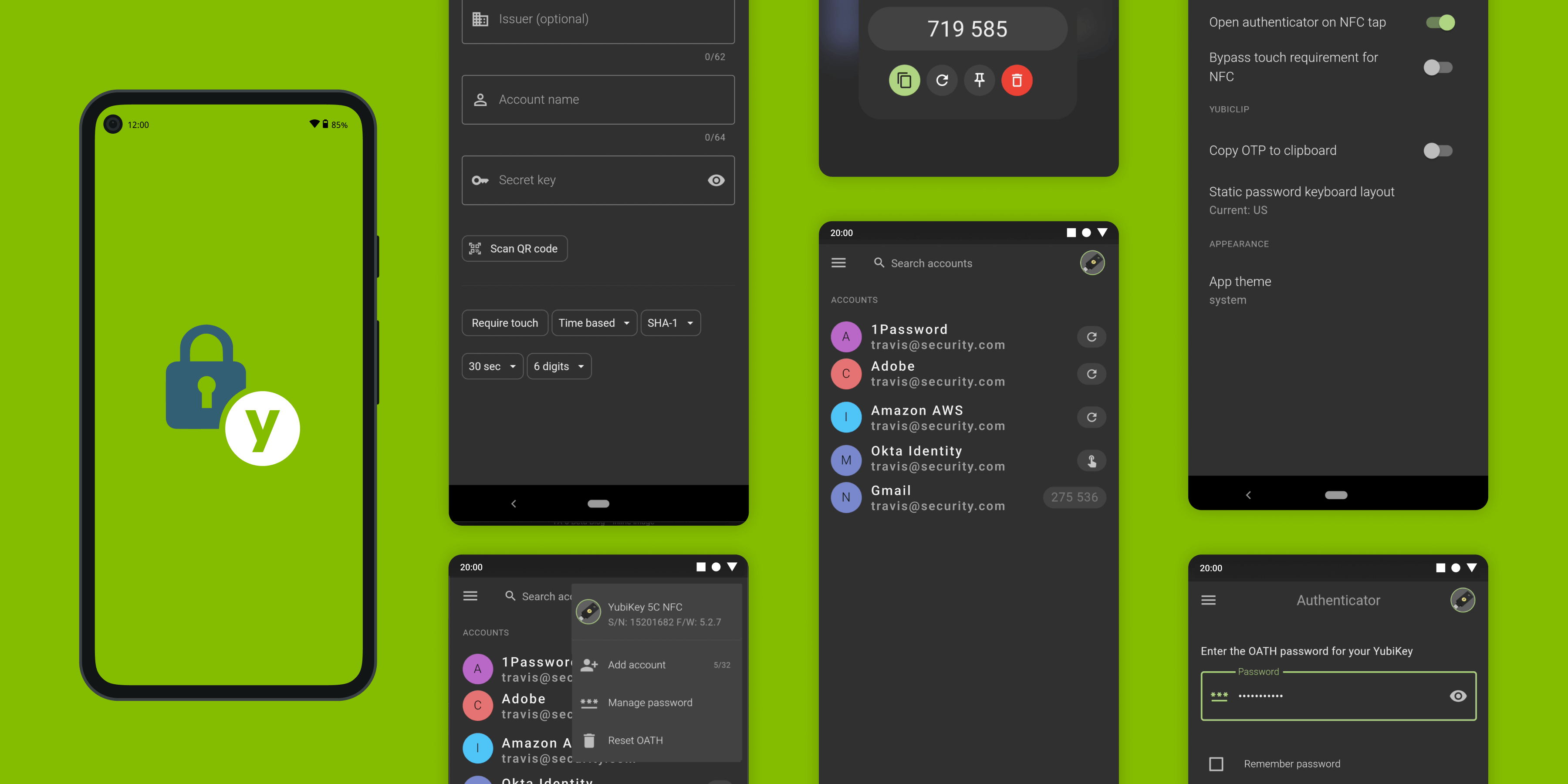
Over the past several months we’ve been hard at work building the next generation of our Yubico Authenticator app. Last June, we released a beta version of it for Desktop and gave our users the opportunity to try it out and give us feedback. Since then, based on that feedback, we’ve continued to improve the app and bring this new version to Android. Today we are releasing the first public beta version of Yubico Authenticator 6 for Android. If you’d like to head right into signing up for the beta program, the link can be found at the bottom of the post.
The same app, but different
This new version of Yubico Authenticator for Android builds from the same codebase as the Desktop version, which brings with it several benefits. A lot of the code is shared between the platforms which allows us to roll out new features more quickly, and helps us to keep a more consistent experience between them.
That said, we are also very aware that there are inherent differences between the platforms. For example, desktop users most often have a physical mouse/trackpad and keyboard – whereas phones and tablets primarily utilize a touch screen. We are trying to accommodate all this in one app as much as we can. For the most part, this can be done without sacrificing one platform for the other. The experience on Android isn’t diminished by having keyboard shortcuts, or right-click context menus. But we know that strictly enforcing a “one size fits all” policy often leads to a worse user experience overall, and we are not afraid of taking different approaches between platforms when it is needed. Likewise, some features may be specific to one platform, because they don’t make sense on the other, or due to platform limitations.
As mentioned in our previous blog post, we are using the Flutter framework to build this new version of the app. This gives us a common codebase for the visual parts, with separate backends for handling lower-level operations like configuring a YubiKey. It also leaves a lot of platform specific implementation, but we already had a good foundation to build upon.
Powered by a new engine
In 2020, we released version 1.0 of our YubiKey SDK for Android, YubiKit. Then a year later we followed it up with version 2.0. Last summer, we released version 2.1, which added (among several other things) support for the Java Cryptography Architecture (JCA) API. This allows developers to store and use RSA and Elliptic Curve private keys on a YubiKey, through standardized Java APIs, resulting in much improved interoperability with existing applications.
Our previous version of Yubico Authenticator for Android predates this SDK by a lot, and therefore doesn’t use it. Rectifying this is something that has been on our to-do list for some time, and with this new version we’ve fully integrated the SDK in order to take advantage of the functionality it offers. As a result, we’ve been able to put our focus on the application specific parts while remaining confident that the underlying low-level communication and protocols work as they should.
Utilizing this SDK will also allow us to more easily bring additional functionality to the application outside the OATH (time and counter based 6-8 digit OTPs) protocol. As the YubiKey supports many different protocols and more use cases move to mobile devices, we know that we’ll be able to support this going forward. One small example of this is the ability to configure what happens when you tap a YubiKey against the NFC reader of your phone when the app isn’t running. By default, it will launch the app and display your OATH accounts. If you’re a user of Yubico OTP instead, you can choose to have the app copy the OTP from your configured slot into the system clipboard, without launching the app at all. Or you can even configure the app to do both, the choice is yours.
A preview of what’s to come
As the larger part of this version is a re-write compared to the older app, some parts of it may work slightly differently from what you are used to. Overall, we believe this app brings a lot of improvements (with more to come!). You may also notice that there’s been a jump in version from 2.x to 6.x, which is due to the fact that we’re now sharing this version number between Desktop and Android. We encourage you to try out the new app and to provide us with your feedback so that we can make it even better. We expect to release Yubico Authenticator 6 for general availability on both Android and Desktop later this year.
This new beta version of the app is available for download using the Google Play Store, where you can select to join our beta program. If needed, you can also opt out of the beta program to revert to the older version of the app. Please let us know what you think by providing us with your feedback, or by signing up for our usability study.