Tag: wwyk
-

YubiKey for RSA SecurID Access product brief Enterprise security made easy. Read more enterprise security RSA wwyk -

YubiKey 5 Series Highest assurance authentication that’s fast and easy Strongest 2FA A physical security key, that can be added to a keychain and plugged into a computer, tablet or mobile device, adds an extra layer of protection on top of passwords to offer the strongest second factor authentication protection against phishing attacks. Strongest MFA Users can combine […] Read more security key strong authentication wwyk YubiKey 5 -

Works with YubiKey Program – Self Verification Checklist Verify your YubiKey integration and manage your listing on the online catalog. Please use this checklist to verify your product integration’s usability. Applicants that receive a passing mark on the checklist will progress to the catalog listing form requesting details on your product integration. Any questions? Please email wwyk@yubico.com. Read more about how Yubico uses […] Read more wwyk -

Works with YubiKey Program – Catalog Listing Information Use this form to provide high-level product information about your YubiKey integration. We’ll review your submission and let you know once it’s listed on our catalog. Any questions? Please email wwyk-mktg@yubico.com. Read more about how Yubico uses the personal data you submit If the above form isn’t visible to you, you can access it directly on […] Read more survicate Works with YubiKey wwyk -

#YubiSecure: Take your Twitter security to the next level with increased 2FA support Great news YubiFans! As of today, Twitter made it a lot easier for you to tweet safely and keep your accounts secure. Phishing-resistant YubiKey authentication via WebAuthn is now supported on Twitter’s desktop, Android and iOS mobile applications. With native WebAuthn support throughout the Twitter platform, you can register and use a USB-, NFC-, or Lightning-compatible security key, like […] Read more 2FA Works with YubiKey wwyk -
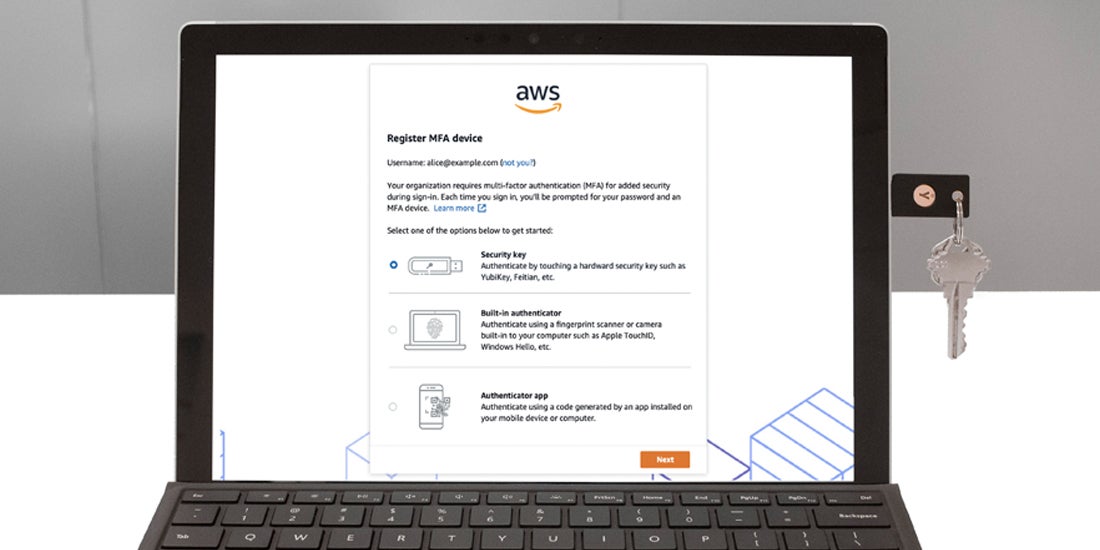
AWS Expands YubiKey Support with AWS SSO WebAuthn Integration Another win for FIDO at the heels of its first industry conference, Authenticate 2020. AWS Single Sign-On (SSO) has introduced native WebAuthn support to secure user access to AWS accounts and business applications using strong, FIDO-based multi-factor authentication (MFA) with YubiKeys. Broader choice of authentication methods by AWS SSO is a win for modern authentication that has historically […] Read more authentication FIDO Works with YubiKey wwyk -

Works with YubiKey Program The Works with YubiKey program One place to showcase your product’s integrations and find all the ways you, your customers, or employees can stay secure with a YubiKey Showcase your commitment to security We welcome all product and solution owners that integrate with the YubiKey to join the hundreds of companies already dedicated to showcasing […] Read more Integration Partner Program wwyk yubico.com -

Protect Office 365 solution brief The YubiKey offers the highest security and best user experience for protecting Microsoft 365. Read more Microsoft Microsoft 365 wwyk -

Improving Performance and Security While Driving Down the Cost of Microsoft 365 – Yubico Microsoft 365 comes with some shortcomings in the areas of security. Read more Microsoft Microsoft 365 Works with YubiKey wwyk
1
2
