Tag: FIDO2
-

Austrian government adds YubiKeys to its electronic ID system With the recent addition of YubiKeys to officially supported FIDO Level 2 certified devices, ID Austria has taken a significant step towards providing even greater security and convenience for its users. ID Austria, an electronic identification system that builds on the country’s existing mobile phone signature system and the Bürgerkarte (Citizen Card), enables all citizens […] Read more FIDO FIDO2 ID Austria YubiKey -
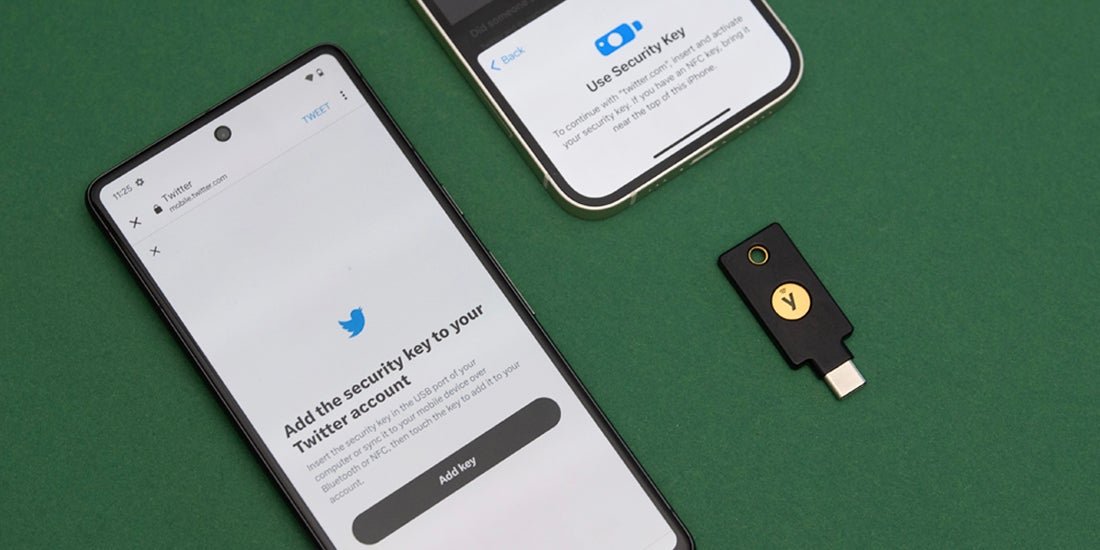
Twitter’s changes to MFA: What the move means for the future of authentication A recent announcement by Twitter has begun to rock the multi-factor authentication (MFA) boat, and the ripples have spread throughout the tech world. The company announced that starting on March 20, 2023, unless a user is subscribed to its Twitter Blue program (an $11/month subscription), they will lose access to SMS-based two-factor authentication (2FA). SMS […] Read more FIDO2 MFA SMS 2FA WebAuthn -

How phishing-resistant MFA stops cyberattacks in healthcare Ransomware attacks and other types of cyberattacks in healthcare are growing, not only in amount, but in sophistication as well. The recent State of Ransomware in Healthcare report released by Sophos highlighted a 94 percent increase in ransomware attacks in 2021, with 66 percent of healthcare organizations hit by ransomware – up from 34 percent […] Read more data breach FIDO2 healthcare phishing-resistant MFA YubiKey -

Q&A: Yubico’s SVP Fredrik Krantz on top cybersecurity trends The world of cybersecurity continues changing rapidly. This has been catalyzed by the sudden shift to remote work, the increasing threat of cybercrime and the complexity of attacks. Understanding the new technological landscape, and what comes next, can be challenging. Hearing from experts who spend their daily lives not only thinking about and facing these […] Read more CISO cybersecurity FIDO2 MFA phishing-resistant MFA YubiKey -

Laying the groundwork for continuous authentication Continuous authentication is an emerging concept—a future ‘nirvana’ state of security that would provide the capability to validate a user’s identity in real-time as they maneuver between systems, applications, and devices. In theory, continuous authentication solutions would use risk signals from a variety of monitoring sources to authenticate users, identify potential threats and proactively remediate […] Read more authentication FIDO U2F FIDO2 MFA phishing-resistant MFA zero trust -
WebAuthn implementation: What’s what, why should you care and new updates from Yubico When it comes to WebAuthn, there’s certainly no shortage of acronyms or protocols. But what do they mean, and which ones do you need to care about? Fret not – both clarity and help are available! In this blog, we’ll share tips on how to implement WebAuthn, as well as share news about java-webauthn-server library […] Read more FIDO U2F FIDO2 MFA passwordless security key WebAuthn -

In passwordless authentication, who is holding the keys? Strong authentication practices are based on validating a number of authentication factors to a relying party (RP) or identity provider (IDP) to prove you are who the RP expects. Examples of relying parties could be Dropbox or Salesforce. Identity providers, who can also be a relying party that interacts with the authenticator, include Microsoft Entra […] Read more 2FA authentication FIDO2 MFA passwordless -

Top five pitfalls companies should avoid when rolling out a passwordless strategy Given the number of breaches in the news today where passwords were at the root of the problem, many companies are now exploring the benefits of a secure passwordless future. Secure passwordless logins not only bring cost efficiencies and a more frictionless user login experience into the organization, but deliver the security that is necessary […] Read more FIDO2 passwordless WebAuthn YubiKey -

How will authentication standards evolve in 2021 and beyond? Authentication standards development is like a slow-moving, winding river. It often takes years of dedicated work to reach new milestones, yet it feeds the entire security ecosystem and sustains digital workflow safety throughout the enterprise. While the benefits of this river are often invisible to the end-user, CISOs and developers are thinking about the river’s […] Read more FIDO2 PIV strong authentication WebAuthn -

What is CTAP? How does CTAP work? FIDO2 consists of two standardized components, a web API (WebAuthn) and a version 2 of CTAP. The two work together and are required to achieve a passwordless experience for login. The earlier FIDO U2F (Link to FIDO U2F Glossary) protocol working with external authenticators is now renamed to CTAP1 in the WebAuthn specifications. […] Read more FIDO Alliance FIDO2 passwordless
