Tag: federal government
-

Cybersecurity in 2025 – part two: Insights and predictions from Yubico’s experts In part one of our 2025 cybersecurity predictions, we highlighted insights from our experts on the topic of passkeys, digital identity wallets and the threats of AI-driven phishing – areas that saw a lot of focus in 2024, and ones that we expect to continue being a major focus this year. If you missed our […] Read more critical infrastructure federal government financial services predictions -

National Security Memorandum on AI: Key takeaways and recommendations Late last week, the White House issued a National Security Memorandum (NSM) on Artificial Intelligence (AI) which aims to ensure that ongoing and future advancements in AI technologies are beneficial to the US public. The memorandum also ensures that the US remains the top location to incubate and innovate in this developing space. Yubico applauds […] Read more AI federal government passkeys -

Securing mobile web app browsing for the U.S. military: Q&A with Jason Christensen and Alex Antrim We’ve heard from customers and Yubico employees that have experienced first hand how difficult it can be for government employees to remotely and securely access essential web services like email, MyPay, and Defense Travel System. In the past, they would typically be required to login to a desktop, making access on the go essentially impossible. […] Read more Department of Defense DoD federal government Q&A smart card -

Straxis and Yubico launch secure mobile web app to access essential U.S. military email, pay and travel services SANTA CLARA, CA, STOCKHOLM, SWEDEN and TULSA, OK – July 15th 2024 – Yubico, the leading provider of hardware authentication security keys and Straxis, a mobile application provider, today announced the availability of a new Secure Web browsing application called MilSecure Mobile. This application can be adopted by any Defense Department (DOD) organization to enable […] Read more Department of Defense DoD federal government government smart card -
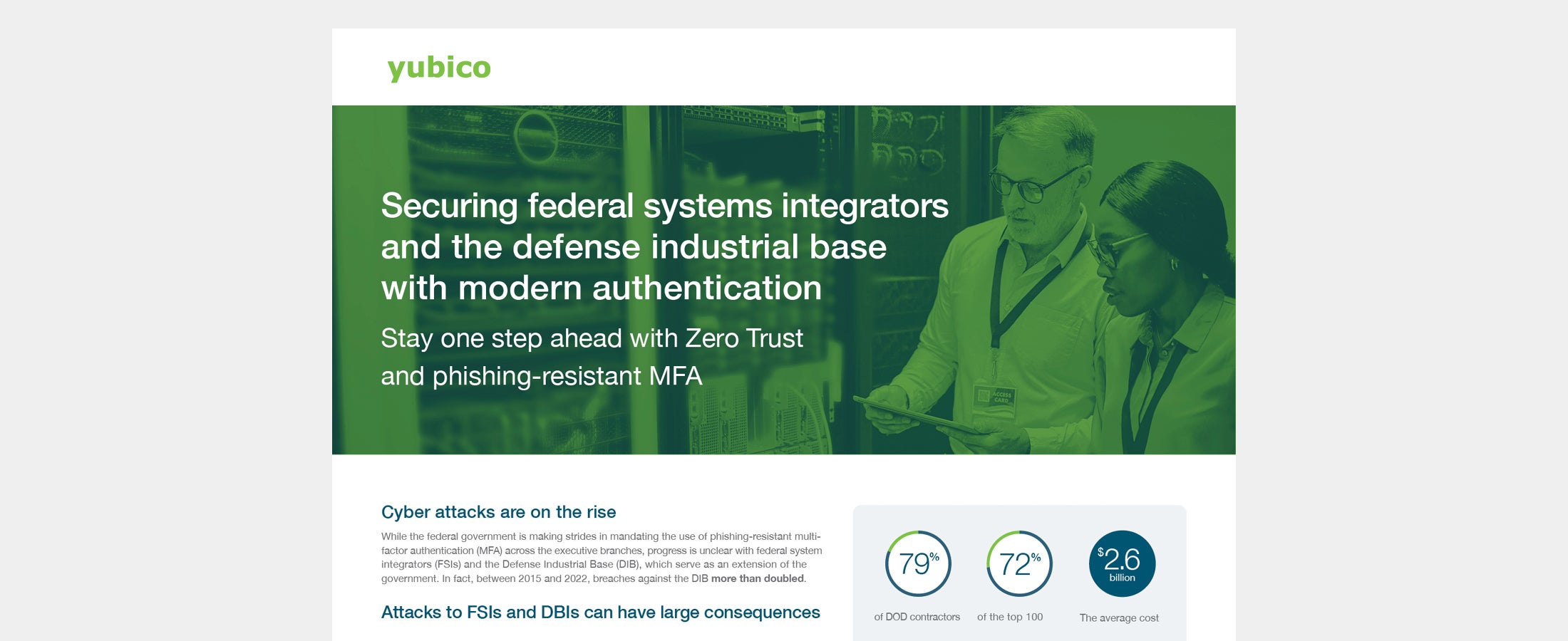
Securing federal systems integrators and the defense industrial base with modern authentication FSIs have access to critical systems and hold large volumes of sensitive and Controlled Unclassified Information (CUI), making them targets of sophisticated cyber attacks. Any MFA is better than a password, but not all MFA is created equal. Download the visual industry brief to learn how FSIs and the DIB can protect themselves with modern, phishing-resistant multi-factor authentication (MFA). Read more federal government federal systems integrators phishing-resistant MFA -

Meeting the Sept 2024 White House phishing-resistant MFA deadline Learn best practices from government executives on their agencies’ journeys, how they navigated challenges and pitfalls to achieve compliance and what steps your agency can take right now to show intent and progress toward phishing-resistant MFA. Read more compliance federal government phishing-resistant MFA -

Securing Federal Systems Integrators with modern authentication Learn how Federal Systems Integrators (FSIs) can modernize their authentication stack and create phishing-resistant users and systems to protect against modern cyber threats. Read more cybersecurity federal government phishing-resistant MFA -
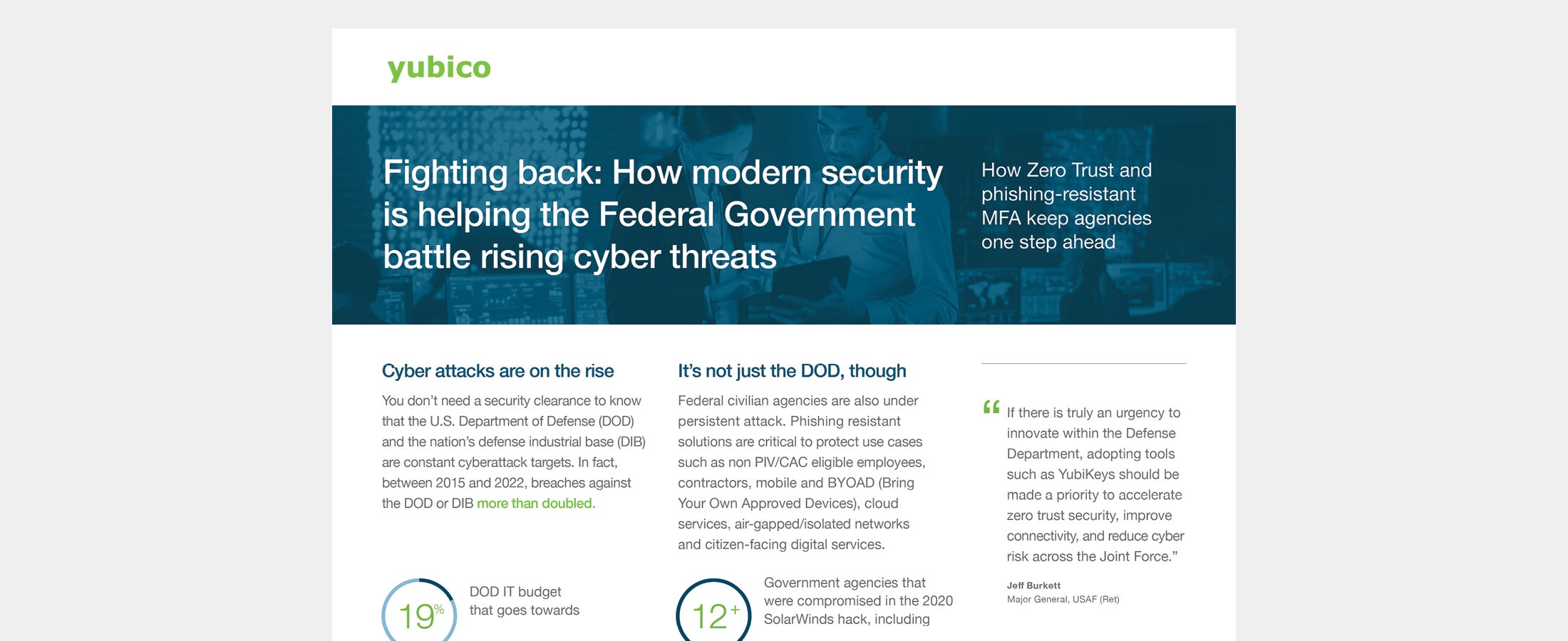
Enhancing Federal Cybersecurity Explore our infographic on YubiKey’s phishing-resistant multi-factor authentication (MFA) solutions tailored for the federal government. Read more federal government modern authentication modern cyber threats -

Yubico joins industry cybersecurity leaders at White House symposium to collaborate, discuss top security challenges and solutions Last week, several Yubico leaders traveled to Washington, DC to attend the White House’s symposium focused on modernizing authentication in support of Executive Order 14028 on Improving the Nation’s Cybersecurity, and the OMB Memo M-22-09 describing the Federal Zero Trust architecture. This event, organized by the Federal CIO & CISO and the Cybersecurity and Infrastructure […] Read more Executive Order federal government OMB Memo-22-09 zero trust -

Federal Government Deployment Best Practices Guide Learn the six deployment best practices that can help your agency accelerate adoption of modern, phishing-resistant MFA at scale using the YubiKey. Read more best practices guide federal government zero trust
