Tag: authentication
-

Yubico Authenticator Yubico Authenticator adds a layer of security for online accounts Generate 2-step verification codes on a mobile or desktop device Experience stronger security for online accounts by adding a layer of security beyond passwords Secure all services currently compatible with other authenticator apps, including Google Authenticator Hardware-backed security Add your credential to the YubiKey with […] Read more authentication authenticator app mobile authentication Yubico Authenticator -

What is OATH – TOTP (Time)? What is OATH? Open Authentication (OATH) is an initiative addressing challenges making standard, open technology available to all. Learn more about OATH How to use OATH with the YubiKey? When using OATH with a YubiKey, the shared secrets are stored and processed in the YubiKey’s secure element. This has two advantages over storing secrets on […] Read more authentication TOTP YubiKey -

What is a Man-in-the-Middle (MiTM) Attack? What is the goal of a Man-in-the-Middle attack? The goal of these attacks are to steal personal user information. Examples are usernames and passwords, credit card information, or account details. Attackers then use obtained information to access account information, change login credentials, or initiate unapproved fund transfers. How do I prevent Man-in-the-Middle attacks? Security keys […] Read more authentication FIDO FIDO U2F security key -

What is a YubiKey? The authentication challenge Our mission is making secure login easy and available for everyone. Balancing security and usability has always been a challenge. And the more secure hardware authentication solutions are difficult to use and deploy. The YubiKey changes this. YubiKey is trusted by the world’s leading companies Read more authentication multifactor authentication YubiKey -

What are Biometrics? How do Biometrics work in a security key? Biometrics are biological measurements or physical characteristics. Once biometric data is obtained, like in a security key or example, it is then saved so it can be used for the future to authenticate into a device or application. Biometric fingerprint credentials are stored in the secure element that helps […] Read more authentication biometrics security key YubiKey -

What is the FIDO Alliance? What is the mission of the FIDO Alliance? •Developing technical specifications that define an open, scalable, interoperable set of mechanisms that reduce the reliance on passwords to authenticate users •Operating industry certification programs to help ensure successful worldwide adoption of the specifications •Submitting mature technical specification(s) to recognized standards development organization(s) for formal standardization Who […] Read more authentication FIDO Alliance yubico.com -

Web Authentication How does WebAuthn work? WebAuthn is an API that makes it very easy for a relying party, such as a web service, to integrate strong authentication into applications using support built in to all leading browsers and platforms. This means that web services can now easily offer their users strong authentication with a choice of […] Read more authentication WebAuthn -

Two-factor authentication (2FA) What is two-factor authentication? Two-factor authentication (also known as 2FA or two-step verification) is a method to confirm a user’s claimed online identity by using a combination of two different types of factors. A password is typically considered one factor, and with 2FA that is combined with another factor to increase login security. Factors used […] Read more 2FA authentication security -
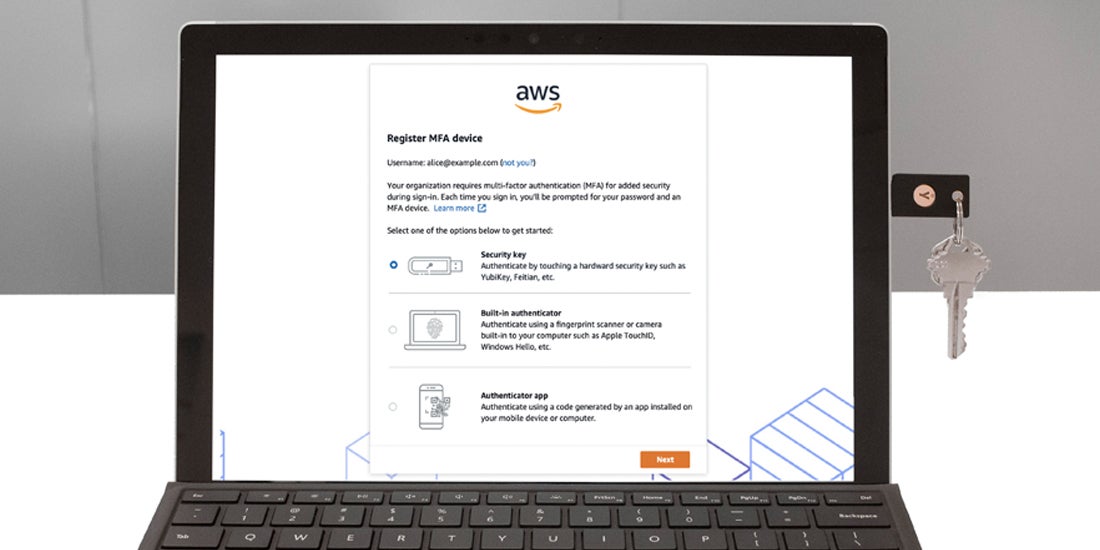
AWS Expands YubiKey Support with AWS SSO WebAuthn Integration Another win for FIDO at the heels of its first industry conference, Authenticate 2020. AWS Single Sign-On (SSO) has introduced native WebAuthn support to secure user access to AWS accounts and business applications using strong, FIDO-based multi-factor authentication (MFA) with YubiKeys. Broader choice of authentication methods by AWS SSO is a win for modern authentication that has historically […] Read more authentication FIDO Works with YubiKey wwyk -

Authentication standards Making the internet safer for everyone Strong security Stolen credentials from employees, vendors and customers are at the root of the majority of account takeovers. The YubiKey provides advanced phishing protection to stop account takeovers. Ease of use The YubiKey is crush-resistant and water-resistant. It requires no battery or cellular network connectivity and its simple […] Read more authentication FIDO2 WebAuthn
