Often times, it’s the little things in life that bring the most satisfaction.
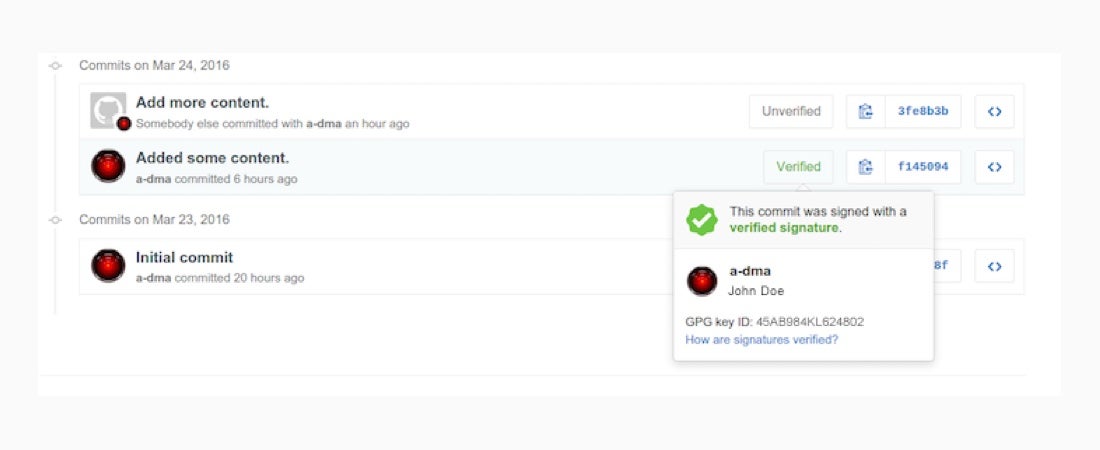
For GitHub users, a shiny new “little thing” is available today. New “Verified” checkmarks in the Web interface document that commits are signed with GPG keys, which ensures the integrity of the code. No more downloading code from GitHub to verify commit signatures.
And, as always, those GPG signing operations can be done with a YubiKey 4 or YubiKey NEO in either of the two form factors.
Signing your work has not been a top feature of Git, even though it ensures data is coming from a trusted source.
With code, integrity is everything. And now GitHub is providing visual audit cues to ensure integrity with just a quick glance. Nothing else has changed in the way either GitHub or YubiKey function, but life just got a little easier. Or as our own devs say, “it’s a quality of life improvement.”
Back in October, GitHub added support for the FIDO Alliance’s Universal 2nd Factor, adding yet another option for strong authentication to their platform and bringing YubiKey owners into the fold. Today signals another platform improvement that is immediately available to YubiKey owners.
Need to figure out how to sign your work using Git and a YubiKey?
We have prepared a tutorial of sorts to walk you through the setup, signing, and verifying tags and commits (with a little merge and pushing thrown in).
Lately, we have been using the word versatility to define Yubico’s concept of modern security and strong authentication. And we’ve been proving it with YubiKey support among partners such as Dashlane, Centrify, Docker, Dropbox, Google, Okta, and, most recently, the UK government and Digidentity.
GitHub is another example, offering developers a set of authentication and content signing features.
There isn’t a silver bullet for security and strong authentication. Progress is measured in stages, and innovation adds up in tangible increments. Some gains are smaller than others, but to Yubico, they all help us build a stronger and more secure Internet.