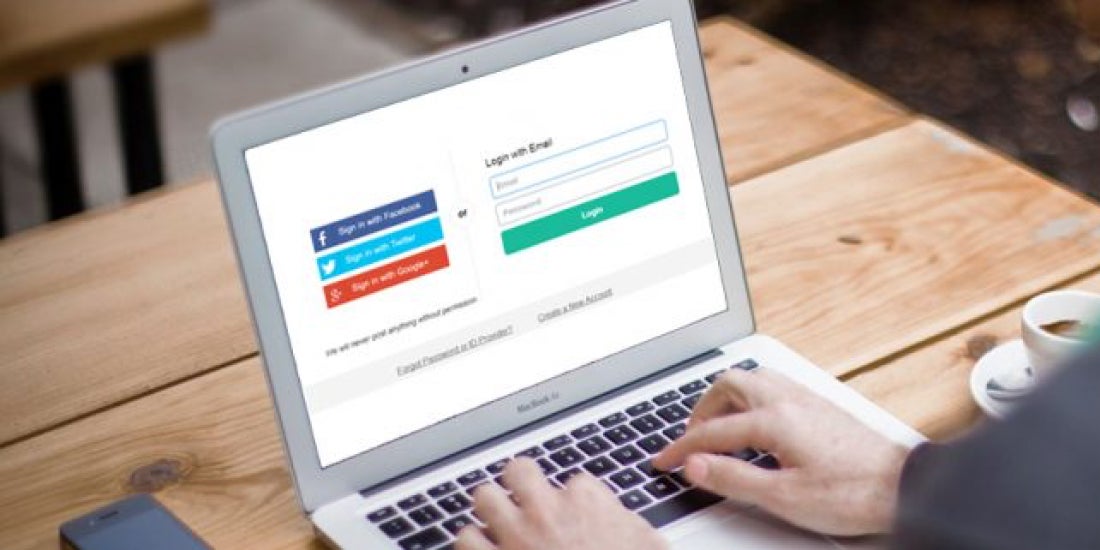
Creating accounts online just got a whole lot easier. Now anyone can log in to or register a new account using their existing credentials from social networking services, such as Facebook and Google. With social logins, users won’t have to rack their brain for another password, saving time and securely authenticating their identity.
Websites that use social login move the responsibility of maintaining cutting-edge data security, identity protection, and login support away from themselves and onto the infrastructures of social networking sites. During the second quarter of 2016, research revealed that 53.1% of social logins went through a Facebook account, with Google accounts pulling 44.8%.
Facebook and Google are among thousands of online services that support FIDO Universal 2nd Factor (U2F). U2F protects against well-known attacks, such as phishing and man-in-the-middle, and other online threats on the horizon. Additionally, all websites supporting U2F work seamlessly with the two-factor authentication (2FA) provided by YubiKeys.
SMS is another commonly used 2FA option, but it is susceptible to both man-in-the-middle and phishing attacks (which we saw in the recent SS7 protocol SMS hack). This is validated by the National Institute of Standards and Technology (NIST), which no longer recommends SMS for 2FA, as highlighted in section 5.1.3.2 in the latest draft of its Digital Authentication Guidelines.
Other websites use push notification-based applications as a second step in the login process. However, much like SMS, push apps do not typically prevent phishing or man-in-the-middle attacks. These can even mislead the freshly phished user into believing that they accessed a legitimate site because they receive the confirmation push message at the same instant that the attacker attempts to log in using their credentials. Most websites also limit the overall effectiveness of 2FA by keeping SMS and/or One-Time Password (OTP) enabled for usability and account recovery. For an in-depth look at credential abuse mitigations, read our Internet Credential Theft white paper here.
So why is social login with U2F and hardware security keys better? Even if an attacker has a user’s password, the attacker won’t be able to access the account. U2F is based on public-key cryptography: when a YubiKey is registered with a U2F service like Google or Facebook, it creates a unique asymmetric key pair with each website. The private key resides on the YubiKey, and the public key on the service.
Think of it as a handshake. When the YubiKey is touched, the public and private keys instantly confirm they are the correct pair, and only that registered YubiKey will allow access. There is no need to re-register the YubiKey. U2F even protects privacy because it was designed to be anonymous, which means no personal data or secrets are shared among service providers, making it impossible to track a user across multiple web sites.That’s it – using the same YubiKey, users get simple and highly secure access to an unlimited number of websites.
Let’s walk through a typical login flow with a U2F- and YubiKey-protected account using Spotify with Facebook social login as an example.

Upon entering a Facebook username and password, the user is prompted to touch their registered YubiKey to authenticate their identity. Just like that, the user is logged in.
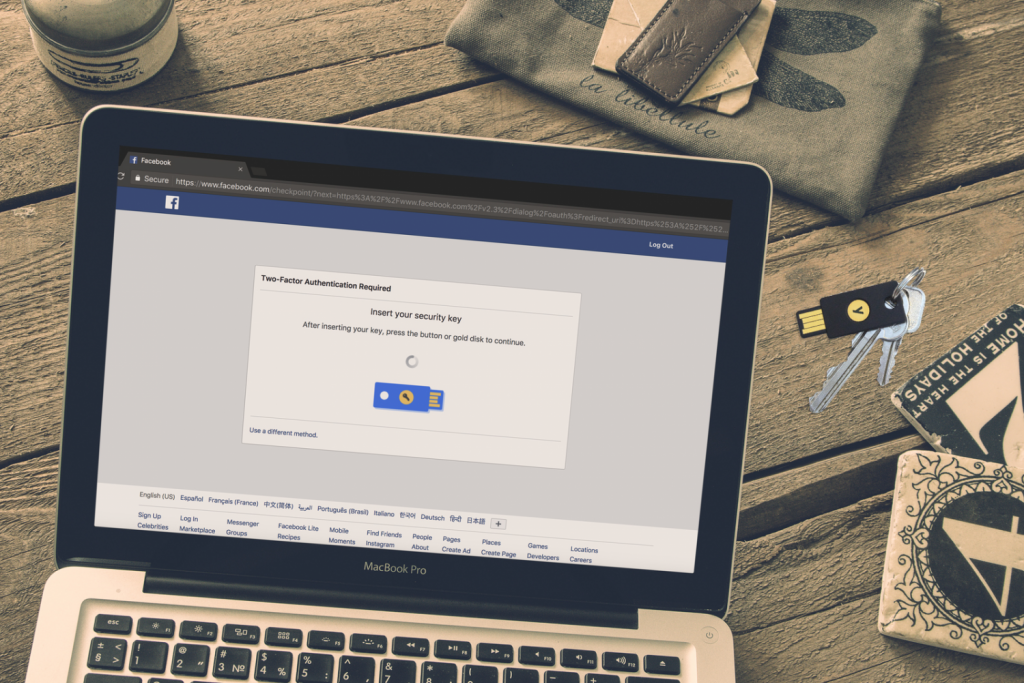
This provides not only a best-in-class authentication experience (all the user has to do is touch the button), but also the peace of mind knowing that the YubiKey ensures user accounts are accessed only by the users themselves.
Now, millions of online stores, games, and applications around the world can eliminate account takeover through phishing by leveraging social login. As more websites and online services do this, our vision of having one device to secure all your online accounts is quickly becoming a reality. To learn more about how to implement social login to websites completely free of charge, visit Google and Facebook for their instructions and code.