What do a PC manufacturer, a meat supplier and a mental health clinic have in common? They have all been victims of ransomware attacks. They’re not alone. Ransomware attacks grew by over 485% in 2020, leveraging the new ransomware-as-a-service (RaaS) model of profit-sharing in exchange for ransomware tools.
One of the most infamous recent ransomware attacks shut down the Colonial Pipeline, creating havoc for millions of people across the East Coast of the U.S.. And this month, the White House announced a range of initiatives to disrupt attackers and assist victims. When it comes to ransomware it’s likely not a question of if your organization will be targeted but when. So, how can you prepare? Read on to learn about the activities and technologies that can help, and how hardware-based authentication, like a YubiKey, can act as part of that solution.
Let’s first define ransomware. Most cyber attacks rely on malicious software, or malware for short, that has been designed to harm or exploit a target system. Ransomware is one kind of malware, designed to attack a system and its data and hold it hostage with encryption until a ransom has been paid, often be difficult to trace digital currencies such as Bitcoin. Valuable data is typically first copied to an attacker controlled system, adding the threat of data exposure extortion/blackmail to the ransom demand.
The average ransomware recovery cost in 2021 is $1.85 million, including the ransom, business downtime, lost sales, operational costs, and legal fees. Ransomware attacks with more sensitive or critical data or systems involved brought costs closer to $4.44 million, higher than even the average “normal” data breach cost ($3.86 million). Over 57% of victims end up making a payment to recover their data or to prevent its exposure – yet only 8% of victims actually get all their data back after paying the ransom.
Who is Behind Ransomware Attacks?
The growth in ransomware has been driven by organized criminal groups, mostly out of Russia, other former Soviet states, and China, with names such as DoppelPaymer, REvil, Ryuk, Darkside, and Maze.
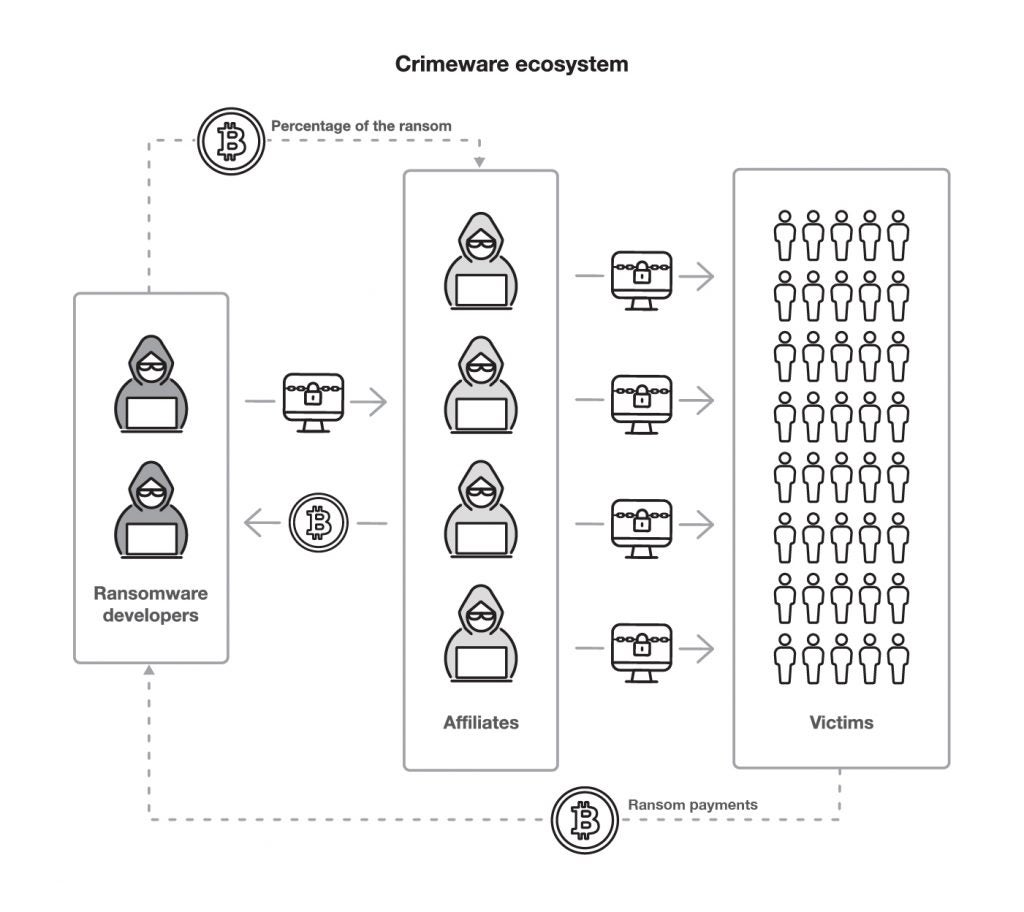
These ransomware groups are often dynamically constructed from criminal networks where software developers create ransomware, and operators called affiliates find vulnerable points in companies to deploy the ransomware. They both share any payments received from the victims.
Recent Ransomware Attacks
Ransomware groups attack all industries and geographies, but the profit-driven nature of these criminal gangs often targets large businesses and government entities. In March 2021, REvil claimed responsibility for a $50 million ransom attack against Acer, revealing some stolen documents as proof of the breach, and hitting a new record for the largest individual demand to date. JBS S.A., a Brazil-based meat conglomerate whose US subsidiary accounts for more than one-fifth of the nation’s meat supply, also paid a $11 million ransom to REvil this June after an attack took their IT systems offline, halting operations.
While the size of these ransom demands is shocking, the impact on operations is frequently the most devastating. For Ireland’s Health Service Executive (HSE), the spread of a Conti ransomware variant triggered a full IT system shut down, impacting patient appointments and access to Electronic Health Records, with several systems still offline weeks later. While HSE did not pay a ransom to the responsible group (Wizard Spider), the impact has been over $118 million (€100m). In Finland, mental health provider Vastaamo was attacked by ransomware; the attacker blackmailed both Vastaamo as well as individual patients under threat of exposing therapy session notes. As a result of the attack, Vastaamo filed for bankruptcy.
In April 2021, a compromised password was used by the DarkSide group to introduce malware that shut down the Colonial Pipeline (as mentioned above) until a $4.4 million ransom was paid. While the FBI’s seizure of a Bitcoin wallet recovered a portion of this ransom, estimates suggest that DarkSide has netted over $90 million in Bitcoin from their combined efforts during the last two years.
Cyber criminals also operate by infiltrating the supply chain. In July 2021, the CISA and FBI began responding to a series of ransomware attacks that leveraged an exploit in the Kaseya VSA (virtual system administration) software. The attack hit as many as 1500 businesses this month, beginning with around 60 direct customers then trickling out to their downstream customers with varying impacts, including a weeklong shutdown of 800 grocery stores in Sweden due to the company who managed their point of sale systems being breached. Criminals and opportunists are further pursuing victim companies and interested parties by sending out phishing emails that appear to be updates related to the ransomware attack.
How to Combat Ransomware Attacks
There is no “silver bullet” for ransomware, but a multi-pronged approach can help organizations respond to and recover from ransomware attacks.
Our take on preparing for, and preventing issues like this at your organization follows:
- Know what data you have that’s critical, and why. Validate the list regularly via all business owners. Become an ally in evaluating what systems hold, operate on, or transmit critical data.
- Don’t forget to include which other systems are trusted even if they don’t handle critical data directly. The reason supply chain attacks can be so devastating is that people often overlook systems that control access to or administer other systems. These centralized points of control, whether on-premise, in the cloud, or operated by third parties, require a very high security bar.
- Make sure you have reliable backups by testing them. Focus on critical data and the ability to restore mission critical business systems easily. This means not just making backups, but also testing restores, and understanding the permissions model of your backup system to ensure backups can’t be deleted easily.
- Make isolating critical systems a priority. Most depth-focused infiltrations will compromise as much data and as many systems as possible before demanding ransom. Zero Trust principles say everything should be isolated but focus on your most critical systems first after you gain confidence in your design and deployment. Include vulnerability management and patching strategies. Make sure to focus not just on access to a system, but access from a system; the easier it is to extract data from a system without being detected, the greater likelihood of pressure and impact from ransomware gangs.
- Don’t use phishable authentication for any accounts. Again and again weak passwords, reused passwords, and SMS, OTP, or push app-based multi-factor solutions are the root cause and/or significant enablers for ransomware and other attacks. Mutual TLS and WebAuthn/FIDO both protect against these weaknesses, and YubiKeys can help with these modern phishing resistant protocols as well as with legacy authentication needs like One Time Passwords (OTP) where needed.
- Only keep the data you need. Consider keeping data not being actively used offline, or destroying it entirely. What isn’t there can’t be stolen and used against you or those who trust you with their information.
- Use experts to routinely test your systems. Don’t scope only “prove to me you can break this” style penetration tests. Use collaborative tabletop exercises where you assume that a “zero day” vulnerability exists in one or more of your systems, and determine if you could detect a breach, isolate it, and recover quickly.
- Don’t pay ransoms. Paying is unlikely to return full data or access and only fuels further ransomware attacks. In some cases, it could be illegal because the entity receiving the payment may be sanctioned.
We hope this helps you better understand what’s been happening and what steps you can take to prepare. Stay safe, and feel free to contact us if we can help with your quest to be ready!





