What is Ransomware?
Ransomware is an evolving type of malware intended to encrypt data, systems, or files, rendering them unusable or inaccessible. Malicious actors may threaten to publish the sensitive data or demand ransom in exchange for decryption. Simple ransomware may lock the system without damaging any files, while more advanced malware may involve cryptoviral extortion techniques.
In this glossary:
- Definition
- What Is a Ransomware Attack
- Protection Solutions
- Recovery from an Attack
- Yubico Solutions and Offerings
Ransomware Definition
Ransomware is a type of malicious software or malware attack that cybercriminals use to encrypt the data of victims, making it unavailable to access until they receive a ransom payment. The threat actor who does not receive payment will block access to the data permanently or perhaps even publish the data. Malicious attackers rely on enterprise users and individuals alike being so desperate to gain access to their business critical or sensitive data, that they’ll often pay even a substantial ransom.
Ransomware attack victims can attempt to reset the device or remove the malware at the risk of losing their data, or simply pay the ransom—although that last option is neither recommended by authorities nor affordable for many victims. These attacks are often the result of a multi-vector engagement such as social engineering schemes, watering hole attacks, carefully targeted phishing emails, taking control of hosts via the Remote Desktop Protocol, malvertising networks, and unpatched software vulnerabilities.
A ransomware attack can target both individual users and businesses. Most often, the victim introduces the ransomware to their own device by clicking an innocuous but malicious link, and once infected, the ransomware immediately begins to identify and encrypt target files, potentially spread or traverse the network to widen the scope, and ultimately results in the perpetrator demanding a ransom.
Users will need the corresponding decryption key to unlock encrypted files. To get it, however, the victim must pay the attacker according to the ransom instructions, often in Bitcoin. Ransomware allows hackers to exert an enormous amount of pressure on victims without much technical prowess in many cases, which is why ransomware attacks are on the rise.
What is a Ransomware Attack?
Ransomware is a kind of malware attack characterized by taking and keeping control of a device and its locally stored data for a ransom. Typically victims pay the ransom in cryptocurrencies such as Bitcoin to restore access to files or prevent their public release. More advanced ransomware attacks deploy encryption at the disk or file-level, rendering file recovery impossible without paying the ransom.
Classic ransomware attacks often invoke coercive images of logos of law enforcement agencies to scare victims into paying the ransom. For example, they may threaten the victim with criminal prosecution for alleged illegal acts taking place on the computer if they do not pay a “fine.”
Other ransomware attacks simply cut the deception, inform the victim that their device is under control, and tell them that in order to reinstate access, they must pay the ransom. Still other versions of ransomware attacks, such as the WhiteRose ransomware, deliver weird messages to victims that don’t seem to have any special goal beyond confusion or consternation.
File-sharing networks are another popular channel for propagating ransomware attacks, as are malvertising campaigns on networks like Zedo. Phishing emails are another popular approach that disguise their malicious payload attached to emails as images or executables.
WannaCry, among the most famous ransomware attacks, leaves any unpatched, internet-connected computer vulnerable to ransomware infection using a flaw in Microsoft’s Server Message Block (SMB) protocol. Other attacks scan the internet for vulnerable operating systems leveraging unsecured Remote Desktop services.
Regardless of the final outcome for victims in terms of access to data or destruction of property, it is the demand for money that defines ransomware for victims.
7 steps of a ransomware attack
Ransomware is a common form of malware that attacks user hosts to extort a ransom in several steps. In other words, a ransomware attack is the result of a chain of events, and not a singular event.
Phase One: Leading Up to the Lockdown
Steps one through three of a ransomware attack can be difficult to see coming. Prevention and security are the best defenses.
Step One: Initiation
The attacker infiltrates the operating system with the ransomware via malicious websites, phishing email attacks, or by directly attacking software vulnerabilities/flaws in RDP connections for instance. Only one point of entry from the above list is necessary, and this step only takes a few moments.
Step Two: Instantiation
Once embedded, the malicious code from the ransomware establishes a line of communication with the attacker. The ransomware may lay dormant and concealed for extended periods of time as the attacker collects data throughout the system and waits to initiate the attack. Many ransomware virus variants also target backup systems at this stage, so that it is extremely difficult to restore data after the attack has manifested.
Step 3: Activation
The attacker remotely executes the ransomware attack.
Phase Two: The Attack Itself
During an active attack, both the data and operating system are at risk and downtime can stretch on indefinitely.
Step 4: Encryption
The ransomware encrypts the data or holds it behind a lock screen. Different ransomware variants work in different ways; some encrypt individual files, while others can target an entire host. Ransomware may also encrypt or delete backup systems to prevent recovery as previously mentioned.
Step 5: Ransom Request
The attacker delivers information on how to pay the ransom, usually in cryptocurrency. It is highly unlikely that a victim can decrypt the data due to the strength of the underlying encryption, so most have three choices: recover from a backup or replica, lose the data, or pay the ransom.
Step 6: Response
Even the costs of partial data recovery can be exorbitant without an effective recovery method and plan in place. With such a strategy implemented however, it’s possible to recover data faster without paying ransom and escape harmful downtime and reputation damage.
Step 7: Recovery
Even the most successful recovery from a ransomware attack does not always eliminate the malware from the system. It is still essential to detect and remove the malicious files and code, perhaps even avoiding the risk of re-activating the malware by working in an isolated network. The system can resume normal operations once the malware has been completely removed.
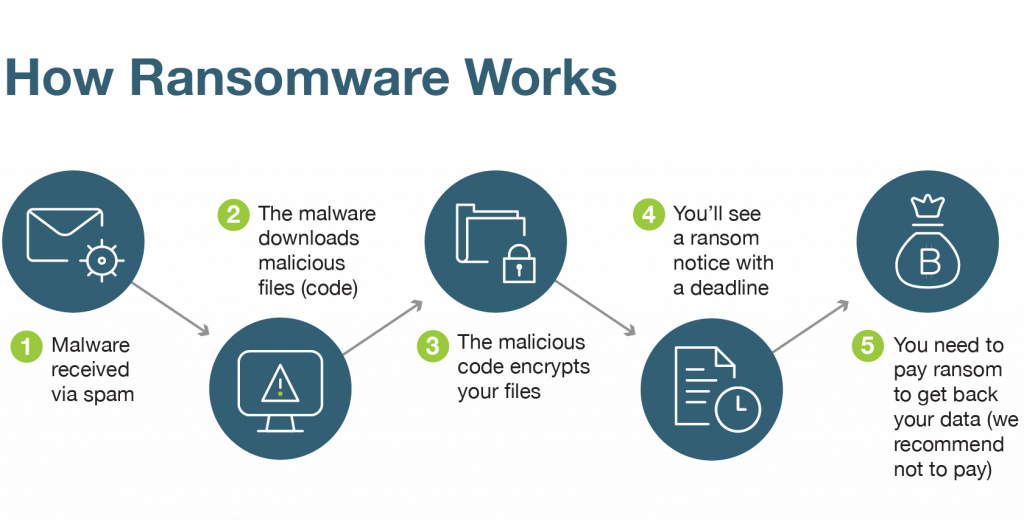
How Does Ransomware Work?
Ransomware aims to deny access to data and files in exchange for restored access at a cost—all made possible by encryption technology. Ransomware manages to access a computer with a built-in list of file extensions, and then checks file types as it works its way through the system. If there is a match with its extension list and a file, the ransomware replaces the original file with an encrypted version, and wipes the system of any record of the original.
Ransomware attacks typically leverage known weaknesses, which means that cybercriminals looking to make a quick buck can do so without doing any hard work or independent research. In general, ransomware attacks are successful for cybercriminals because victims frequently pay the ransom, and as attackers become bolder and target their exploits more specifically, they can make higher ransom demands.
False ransomware attacks are also on the rise, with attackers demanding a ransom and deleting encrypted files regardless of whether the victim pays the ransom. For example, the KillDisk variant demanded a ransom of $247,000, even though if the victim paid it they would still have no way to decrypt their files, since the encryption key is not stored at all, remotely or locally.
Business networks have been targeted by cybercriminals more often recently, although home users have traditionally been the victims of ransomware. In fact, the modern trend is toward high-profile targets such as healthcare providers, massive servers, and utilities such as the Colonial Pipeline attack. Enterprise class businesses are appealing targets for ransomware attackers despite being more likely to backup frequently and have robust IT operations because larger organizations are also more likely to have the money to make a hefty ransom payment.
Where Do Ransomware Attacks Come From?
Authorities say that many ransomware attacks originate in East European countries such as Belarus and Russia and come from organized groups that operate with relative impunity. Ransomware attackers may be individual people trying to do “business” or organized collectives with dozens or hundreds of hackers directly serving a country like North Korea.
The highest-profile attacks such as Colonial Pipeline in 2021 are frequently executed by sophisticated hacking groups. These groups work much like regular corporate businesses, with internal hierarchies and employees that work in service to revenue goals and other aims. Many of these hacking collectives, such as REvil and DarkSide, spread their wares by selling their malware as “ransomware as a service” to whoever can afford it and can execute it.
Ransomware vs Malware
Malware is a portmanteau of “malicious” and “software,” and the phrase covers a broad range of different types of malware. Malware is designed to achieve different goals, from damaging the computer or host itself to breaching sensitive data.
All ransomware is malware, but there are many types of malware and not all malware is ransomware. Various ransomware hybrids have evolved over time:
- Ransomware Worms. Malware worms can spread themselves by sending emails, exploiting vulnerabilities, etc. Ransomware worms like WannaCry combine the capabilities of ransomware and worms, spreading themselves to new computers to encrypt files.
- Data Breaching Ransomware. Data breaching ransomware variants aim to capture sensitive data for attackers before encryption ever takes place. This is for leverage to convince victims, since some victims refuse to pay and the ransomware profit model is based on the improbability of independent recovery.
- Ransomware Wipers. Like NotPetya, ransomware wipers are designed to look like ransomware but are not true ransomware at all. They are not designed to provide the decryption key even if the ransom is paid. Even ransomware operators of NotPetya don’t have the key, so preventing access to computers or files or by encrypting key files is the goal.
From the perspective of core functionality, all of these varieties are similar, since they achieve their goals using encryption. However, the addition of extra “features” or masquerading as ransomware can be profitable to the attacker.
Types of Ransomware
There are several basic types of ransomware that attackers employ in the field.
Encrypted Ransomware/Crypto Ransomware
Encrypting or crypto ransomware works just like it sounds – it does not interfere with basic computer functions, but instead encrypts crucial data so they cannot be accessed, such as pictures, documents, and videos, to panic users. The threat is then to pay the ransom within a certain amount of time, or see all files destroyed. Since so few users adequately backup their files, the result can be devastating.
Screen Lockers/Locker Ransomware
Screen lockers or locker ransomware render files and applications totally inaccessible by locking the user out of the system or host. A lock screen presents the demand for ransom, and possibly a countdown. Unlike the encrypting version of ransomware, this type of malware blocks basic computer functions and renders the host inoperable except for the ability to pay. The only positive is that locker malware typically just locks users out, and doesn’t target critical files; this means total data destruction is unlikely.
Scareware
Scareware is malicious software that tricks victims into downloading fake and potentially dangerous software to fix an imaginary issue with a computer. For example, it may use popups to make users think there is a virus, ultimately compelling users to download the actual virus.
Malvertising
Malvertising—another portmanteau, this one compressed from “malicious” and “advertising”—is the method of using online ads to install malware and malicious code onto unsuspecting hosts.
Human-Operated Ransomware
Human-operated ransomware, a growing trend in ransomware attacks, is a different, hands-on approach that targets organizations rather than single devices. In this kind of attack, the criminals infiltrate the organization using techniques like credential theft and exploitation of security software misconfigurations to navigate laterally through the enterprise network, and deploy a ransomware payload to selected, high-impact resources. These targeted attacks are much more difficult to recover from than commodity ransomware because they are based on specific knowledge of weaknesses.
Ransomware-as-a-Service
Ransomware-as-a-Service allows attackers with less skill the chance to succeed with ransomware attacks. Software programmers make malware available to buyers, creating a high-gain, low-risk scenario for themselves.
Ransomware Examples: Recent Ransomware Attacks
There are a number of recent ransomware attacks and groups to be aware of.
DarkSide
In April 2021, the Colonial Pipeline attack revealed a serious weakness in the national critical infrastructure system of the US. This ransomware attack launched by the group DarkSide caused panic and chaos as it disrupted gas supplies all along the East Coast.
The DarkSide gang targeted the company’s internal business network and billing system prompting massive shortages across states. Colonial Pipeline actually paid DarkSide $4.4 million dollars in bitcoin to stop panic—and it was revealed that their security measures had not been adequate.
The FBI traced and recovered much of the $4.4 million ransom payment, albeit not the actual attackers.
In early May 2021, the DarkSide gang also targeted chemical distribution company Brenntag, stealing 150 GB worth of data, and demanding a $7.5 million dollar ransom in bitcoin. Brenntag eventually paid $4.4 million—among the highest ransomware payments in history.
Babuk
Hacker group Babuk targeted the National Basketball Association (NBA) in 2021 with a ransomware attack, claiming to have taken 500 GB of confidential data from the Houston Rockets and threatened to release it.
EvilCorp/CryptoLocker
CNA Insurance was victimized by a ransomware attack that encrypted 15,000 devices in March 2021, including many remote employee computers. This attack used a new type of malware called Phoenix CryptoLocker, and was the work of the hacker group Evil Corp.
HelloKitty
The HelloKitty gang hacker group attacked the video game CDProjekt Red based in Poland in February 2021, accessing and encrypting game and code in development. However, CDProjekt refused to pay the ransom money as they were able to restore the encrypted data from backups.
GoldenEye
In 2017, Petya returned as the ransomware GoldenEye, spreading around the world. GoldenEye hit over 2,000 targets, including several banks and oil producers. It also locked Chernobyl nuclear power plant personnel out of their computers, forcing them to manually check radiation levels.
NotPetya
NotPetya has the worm-like ability to propagate itself across a network but retains the classic features of ransomware. It uses several methods to spread to any hosts running Microsoft Windows.
WIZARD SPIDER/Ryuk
eCrime group WIZARD SPIDER targets enterprise organizations with the Ryuk ransomware for high ransom payments.
REvil/Sodinokibi Ransomware Family
REvil Sodinokibi ransomware usually operates under a ransomware-as-a-service (RaaS) model. The REvil gang attacked computer manufacturer and major partner of Apple, Quanta, demanding a $50 million ransom in April 2021. After Quanta refused to negotiate with REvil, the hackers targeted Apple, leaking product blueprints and sensitive data.
The attack was apparently called off by May, when REvil attacked computer manufacturer Acer in May 2021, leaking sensitive documents and demanding a $50 million ransom, the largest known to date.
In May 2021, REvil launched another high-profile ransomware attack on JBS Foods, among the largest meat processing companies anywhere and a critical piece of US food infrastructure. The group demanded a $11 million ransom, one of the largest ever paid. Americans were told by the government not to panic buy meat in response, although panic buying did happen, and JBS also ultimately paid the ransom.
REvil again made an attack similar to their attempt with Quanta, this time in July against Kaseya, which manages IT infrastructure for many major companies around the world. They achieved the Kaseya attack by encrypting multiple systems with a fake software update sent through Kaseya’s Virtual System Administrator. REvil demanded $70 million in bitcoin as victims like Swedish supermarket chain Coop were closed for a full week.
The FBI were subsequently able to access REvil’s servers and managed to stop the Kaseya hack, so services were restored and no ransom was paid.
WannaCry
WannaCry targets utility companies and healthcare organizations using a Microsoft Windows exploit called EternalBlue.
How to Protect Against Ransomware and Keep it From Spreading
There are several best practices for protecting against ransomware. In essence, most strategies boil down to three basic ideas:
- Prepare to be able to recover from an attack without paying the ransom
- Protect privileged roles to limit the scope of attack damage
- Remove risks one by one to make it harder for a ransomware attacker to get in
Here is a more granular view into multiple ways to achieve those goals.
Use Cloud-Based Solutions
Cloud-based ransomware protection tools including backup as a service (BaaS) and other similar SaaS-delivered solutions offer segregated copies of data that do not require physical network connections to the enterprise, and may be inaccessible to attackers. This ensures that when ransomware attacks do successfully penetrate user environments, clean backup and restore operations can be run from a quarantined source.
Train Employees on Best Practices
Employees at every level should be well-trained in the best practices of security, including ransomware protection. Every team member should practice good digital hygiene, including connecting only to secure Wi-Fi, using strong password protection, multi-factor authentication, and never clicking on links from unsolicited emails. Train employees on how threat actors work to socially engineer users into clicking on links and malicious attachments, and how to identify phishing emails.
Keep OS, Software Patched and Up To Date
Always patch software and keep the ecosystem up to date, as cyber attackers often succeed by searching for backdoors and vulnerabilities to exploit. Conversely, software vendors generally strive to maintain the greatest protection against new and emerging threats. Minimize the ways intruders can access the system by vigilantly updating all software and systems and you’ll also reduce your exposure.
Implement Secure Email
Use a secure email solution that conducts attachment sandboxing and URL filtering. Some tools allow for retroactive quarantining of delivered emails using an automated response capability before the user interacts with them to make this process safer and easier.
Create Offline Backups that are Ransomware-Proof
While it’s a good practice to use cloud-based and other online solutions, it is also a best practice to create and maintain a backup infrastructure that is essentially ransomware-proof — an offline backup. This ensures recovery is possible even when attackers have deployed ransomware to an environment in addition to any targeted online backups.
Implement a Strong Identity Protection Program
Implement a strong identity protection program to improve the organization’s security posture. Analyze gaps, behavior, and anomalies for each account, including privileged accounts, human users, and service accounts. As you engage in ransomware detection activity, seek out any lateral movement, a clear sign of ransomware threats, and implement only risk-based conditional access.
Use MFA. Enable multi-factor authentication on all company accounts, including social media accounts, user accounts, service accounts, and implement strong spam filters.
Prepare in Advance
Create a detailed incident response plan to clarify who is responsible for what in the event of a ransomware attack. Review the organization’s cyber insurance policy to ensure that ransom is covered and that the coverage level is realistic. Establish a secure texting app communication channel for senior management to use in the event of a cyberattack and ensure that they are properly trained on how to use it.
Look for Insider Risks
Identify high-risk users who could help launch an insider attack, such as those with administrative rights. Use a reputable digital forensic firm to assess insider threats as needed. Some organizations anticipated the move toward work from home en masse as a reason to engage such firms to assess insider threats surrounding a “data security event”.
Along the same lines and perhaps equally important, assess the cybersecurity protocols of all key clients and vendors, especially any that handle critical company resources or sensitive data.
Ransomware Protection Benefits
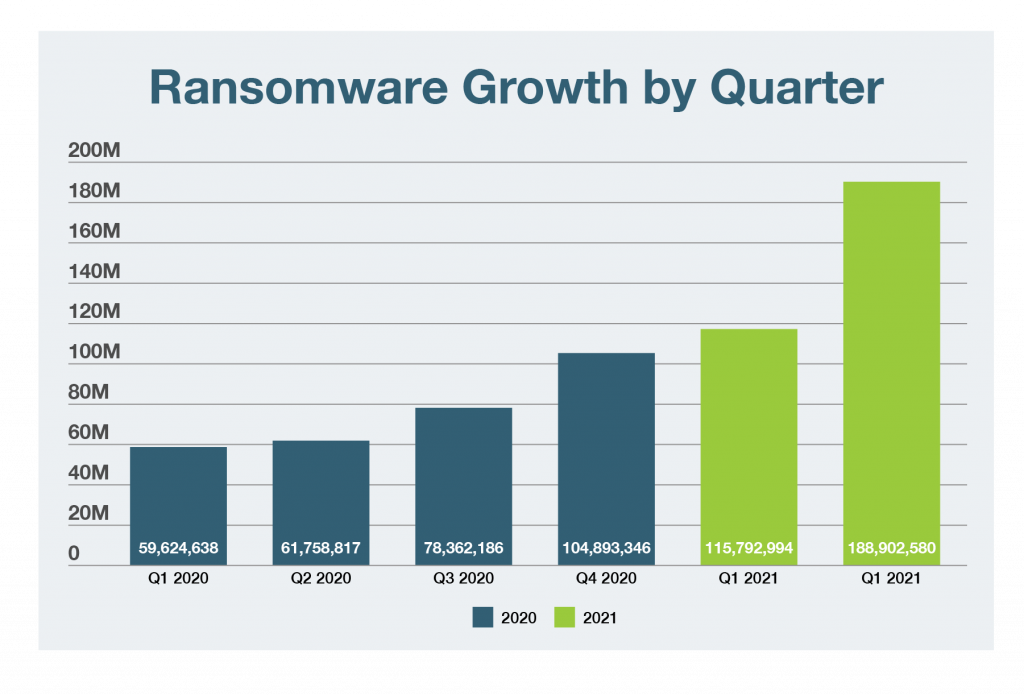
Ransomware protection refers to the prevention of ransomware attacks from occurring in the first instance and then mitigating the fallout from successful attacks if and when they occur. Ransomware presents cyberthreats that are more numerous than ever, exploiting security gaps introduced by the broader attack surface created by Work-From-Home (WFH) policies and remote logins. Cybercrime and ransomware threats represent a potential multibillion-dollar organized crime industry, so businesses must make ransomware prevention a top priority.
When businesses and their employees become more educated about how ransomware works and why ransomware is dangerous, they see real benefits:
Increased safety and security. Ransomware threats hit a record high in 2021, with no signs of slowing. Robust ransomware protection helps ensure your organization doesn’t fall victim to attacks—risking security threats, data loss, and costly downtime. At a time when consumers and users demand constant access to data, downtime is almost incalculably damaging.
Data protection. Ransomware protection safeguards data. Without it, data is vulnerable to potential corruption and loss without any recourse. Ransomware prevention preserves data integrity and retains usable copies of lost data so recovery can follow attacks.
Enhanced growth. Applications and digital data drive business growth, and so the inability to access either can mean sudden death for any organization. Guarding business-critical resources to keep them safe from ransomware attacks helps prevent data loss or theft, and is vital for business growth.
Business continuity. Even an average IT disruption or outage can cause serious problems for a business. An unplanned, unpredictable shutdown with wholesale data loss can be a real catastrophe. Ransomware protection in the form of ransomware solutions that save data and configurations limit the potential of attacks to succeed, reducing the likelihood of an extended shutdown, and shortening the window needed for business recovery.
Disaster recovery. Ransomware protection is an important piece of any disaster recovery plan. A successful ransomware attack can be reminiscent of the serious, rippling effects of any other form of conventional disaster. Any IT environment can face the corruption of resources or data loss from unplanned, malicious ransomware events that could disrupt operations.
Risk mitigation. A proactive security posture designed with risk mitigation top of mind, must include ransomware prevention. Robust anomaly detection, access management, hardened security, data encryption, and comprehensive user access controls are all critical to successfully defending users, devices, and systems against cyberattacks. A strong plan for how to prevent ransomware is a piece of this puzzle.
Lower costs. It is far less expensive to implement ransomware protection than it is to recover from a successful ransomware attack. Expensive downtime and astronomical payouts can stop operations, and the attack itself can result in permanent data loss detrimental to longer term growth. Be proactive and secure valuable data with ransomware prevention.
Ransomware Recovery: What To Do If You Get Hit By Ransomware
Once ransomware penetrates your system, network, or even just a single device, acting the right way immediately is essential. Here are the ransomware recovery steps you should take if you find yourself or your enterprise under attack:
Identify Infected Systems and Devices
If the network is penetrated by ransomware, identify all devices that may have been infected before the ransomware can spread. Look for suspicious network activity such as changing file extensions or file renaming. Interview employees, as they may have information about suspicious activity since systems are often targeted through employees. Carefully inspect all victim computers for evidence of the attack.
Stop the Spread of Ransomware
Reaction time can make or break your response. Cut or restrict network access for every device connected on and off-site immediately to stop ransomware from infecting new devices. If necessary, disable any wireless connectivity including Bluetooth and Wi-Fi as well to stop ransomware from moving around on the network. The goal is to isolate, contain and quarantine.
Assess the Extent of the Damage
To design the right response, carefully review the problem the breach caused.
First inspect all devices that have been identified and isolated. Inspect them using digital forensics, to help identify which devices may have been the point of access for the ransomware.
Create an inventory of infected devices, networks, systems, and data centers. Each compromised device should have been loaded with both antivirus and antimalware software, but if not, then they must be installed immediately to begin the purging process. This is a crucial part of the remediation process to ensure the encryption process does not restart when operations eventually resume.
Inspect Backups
Separate backups of all digital data are essential to minimizing downtime and quickly getting operational again in the event of a breach. After you have decrypted each infected device and equipped it with the software it needs, you’re ready to restore from the backup files—but only if they remain uncompromised.
Inspect them carefully before accessing them to ensure you’re not back to square one.
Report the Attack
Although no one enjoys publicizing an attack, compromised data from ransomware attacks affects not only victim businesses but also their clients and employees. Organizations that are breached have a duty to report data leaks and ransomware attacks to the relevant authorities with all due speed.
Ransomware Removal Tips
Ransomware removal is a tricky business, but there are a few basic tips to keep in mind:
Reboot to safe mode. Although it doesn’t work with every variant, some ransomware can be stopped by rebooting and restarting the device in safe mode. Some trojans such as Snatch and REvil can operate during a safe-mode boot, but others can’t, and the reboot can buy time enough to install anti-malware software. This will still leave the job of restoring encrypted files via data backup, however.
Install anti-ransomware software. You need to remove the ransomware once you’ve identified and disconnected the infected device(s) from the network. Do this with anti-malware software before attempting normal use while the devices are still encrypted, or the undetected malware may spread even further and compromise more files.
Scan for ransomware programs. Now that your devices are free of ransomware and other malware, scan the system. Use next-generation firewalls, antivirus software and even scan manually by searching for suspicious behavior like changes to file extensions.
Restore the computer from backups. Minimize disruption and downtime with an isolated backup stored apart from other business operations.
Report the attack. Because ransomware attackers are often known cybercriminals they sometimes use documented weaknesses and exploits. Every documented report helps others, and reporting your breach may help you by giving you access to new information that helps you with your ransomware removal process.
Ransomware Prevention From Yubico
Ransomware and its connection to strong authentication and phishing-resistant multi-factor authentication (MFA) is generally not well understood. After all, ransomware is a type of malware designed to attack a system and its data, then hold it hostage with encryption until a ransom has been paid.
Strong authentication involves establishing a trusted identity of a user or machine before authorizing access to data. The connection between strong authentication and ransomware lies in thinking about the ways actors using ransomware can infiltrate your organization. While a common way it occurs is by users clicking on spurious links and unwittingly downloading malware on to their system, a secondary and more insidious way is for an attacker to take over an account through stolen credentials and then enter the network guised as a legitimate user and installing malware on to a system themselves and watching the harmful process play out. This is a very deliberate chain of events which, if organizations could thwart with stronger forms of authentication beyond passwords and legacy multi-factor authentication (MFA), can significantly foil the plans of attackers.
Highly phishing-resistant solutions such as hardware-based authentication delivered by the YubiKey, can help organizations avoid using phishable authentication for any accounts. Again and again we see reused passwords, weak passwords, SMS, OTP, or push app-based multi-factor solutions serving as the root cause—or at least as significant enablers—for ransomware attacks.
The best ransomware protection starts with modern phishing resistant protocols such as FIDO2/WebAuthn and FIDO U2F. YubiKeys can not only support these modern authentication protocols, but is a multi-protocol security key that supports smartcard-based authentication which offers high security, and is even compatible with legacy authentication like One Time Passwords (OTP) where needed, if your enterprise is not quite FIDO ready. As the old adage goes, an ounce of prevention is better than a pound of cure.
