What is a root of trust?
A root of trust in an external hardware authenticator that can be used with any computer or mobile device to identify that the person accessing an account is the rightful owner.
Why is a root of trust important?
Today, you may have several devices that you use on a day-to-day basis to log into websites, services and applications. A WebAuthn root of trust, such as the one offered by a hardware security key, ensures that you can always authenticate to any website or service, across any platform, rapidly and securely.
Account access and recovery
2 devices lost
Every 3 years, an average user will lose two devices which they never see again.
10.9 hours
Overall, the average user spends 10.9 hours per year managing passwords.*
$5.2M lost
The average company loses $5.2M annually in productivity due to account lockouts.*
* Source: Ponemon Report – 2019 State of Password and Authentication Security Behaviors Report
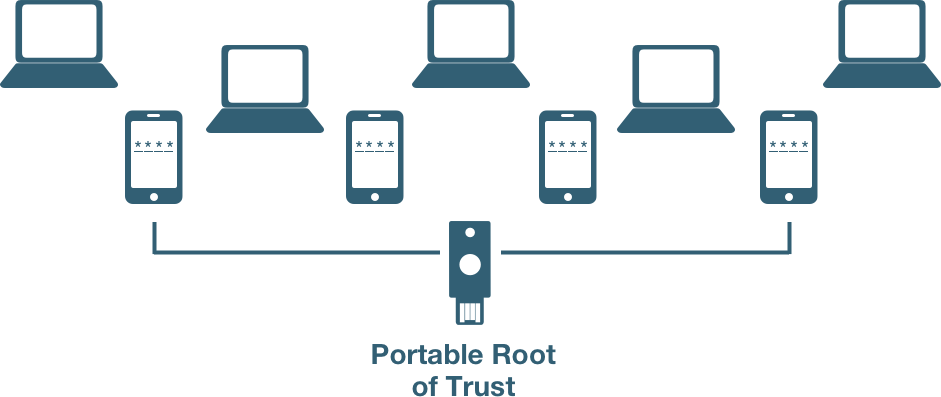
How a root of trust works
Powered by WebAuthn and PIV
Easy and fast user registration
When a user registers on a website the device platform offers the user several options to start their journey.
The user may be offered to use either an external authenticator, such as a hardware security key, or an internal authenticator built into the OS platform itself, such as a fingerprint touchpad on the user’s laptop, to secure their new account. The best practice is first use the external authenticator before enabling the internal authenticator.
Greater user choice and control
During the registration process, a credential is created which is stored on the authenticator of choice. For fast recovery and bootstrapping of a new device it is recommended that the user always first register using the external authenticator, such as a hardware security key, and then bootstrap the internal authenticator using the external key. If a device is lost the security key credential is still usable on a replacement device, unlike the built-in authenticator which is no longer accessible if the device is lost.
Once this has been completed, the user can authenticate to the web service or other resources using whichever authenticator they prefer on a day-to-day basis.
Fast-track onboarding a new device or account recovery
If the user wants to add a new device to authenticate to the web service, or in the event of a lost or stolen device, having a portable root of trust, such as a security key, greatly accelerates the onboarding and account recovery process.
The user no longer needs cellular connectivity, or to wait for SMS codes to be sent from each web service, or to enter multi-digit codes one by one for each web service. With a security key a user can quickly insert the key into the USB port of a laptop or desktop, simply tap a mobile device and instantly be re-authenticated to a variety of web services quickly and efficiently, without any need for cellular connectivity or calls to the helpdesk.
A security key root of trust delivers high security
A root of trust, such as a hardware security key, offers a physical and cryptographic guarantee of possession of a unique hardware device. The private key material or “secret” cannot be extracted as the external authenticator cannot be cloned or tampered with, and the privacy secrets cannot be revealed.
A root of trust can be used for step-up authentication. With an external portable root of trust, a user can be easily and quickly re-authenticated when initiating sensitive transactions such as making a large financial transaction, or when submitting a prescription.
User experience:
User gets a new device and is trying to log into a mobile app using 2FA
NO PORTABLE ROOT OF TRUST
User installs mobile application
User signs in using username and password
User is prompted on which phone number to receive SMS OTP
User waits for the SMS OTP
User receives message
User taps on message
User memorizes or copies the code in the message
User switches to mobile app
User enters OTP into mobile app
User submits the code
User gains access to the service
WITH PORTABLE ROOT OF TRUST
User installs mobile application
User signs in using username and password
User inserts the YubiKey into device and touches the key
User gains access to the service
