Resources
Browse our library of white papers, webinars, case studies, product briefs, and more.
- All Categories
- Product briefs
- Solution briefs
- Webinars
- White papers and reports

Proactive Security for Privileged Users Building cyber resilient financial services through proactive security for privileged users Read more 
Passkeys Done Right Learn more about phishing-resistant, passwordless enterprise deployment with YubiKeys. Read more 
2025 Gartner® Hype Cycle™ for Digital Identity Explore this report to gain insights on: critical market insights, passkeys trends and business impact and drivers. Read more Device-bound passkeys MFA passkeys passwordless phishing-resistant MFA user authentication 
Seamless security for your Microsoft ecosystem Not all MFA is created equal—the YubiKey provides phishing-resistant protection at every stage of your Microsoft journey The YubiKey is a modern multi-protocol hardware security key supporting Smart Card (PIV) and FIDO that delivers an optimized user experience and offers phishing-resistant two-factor, multi-factor authentication (MFA) and passwordless authentication at scale across Microsoft environments. The YubiKey […] Read more 
Stop fraud with secure customer banking Download this free asset to learn the six best practices to protect end customers from digital banking scams. Read more 
Securing financial services with proactive passwordless security With the cyberthreat landscape becoming more sophisticated, read this white paper to learn how proactive, passwordless security using hardware passkeys can help. Read more 
Stop banking fraud and secure retail and commercial banking Learn how banks and financial institutions can deliver highest security and the best user experience for retail and commercial banking customers using scalable device-bound passkey solutions. Read more 
Build Cyber Resilience for Manufacturing Learn our top recommendations to accelerate your Zero Trust approach, prioritize operational resilience, and build a cyber resilient authentication strategy. Read more 
Modernizing authentication to support cyber resilience Learn about the most commonly overlooked authentication vulnerabilities that increase cyber risk, how to mitigate these risks, and what contingency measures can be put in place to maintain or restore access in the event of disruption. Read more 
Modern authentication for Defense and Domestic Operations Download the free brochure to learn how the YubiKey solves authentication use cases for the National Guard and Domestic Operations. Read more 
How state and local governments are deploying modern authentication Learn more about how state and local governments around the world are using YubiKeys to go passwordless, drive compliance and accelerate Zero Trust. Read more 
Securing the future of finance Learn how financial institutions can enhance security, streamline operations, and foster customer trust with Yubico and HYPR. Read more 
2025 Gartner® Innovation Insight for Many Flavors of Authentication Token Learn key findings for mitigating risks and planning for migration to phishing-resistant MFA. Read more Device-bound passkeys MFA passkeys passwordless phishing-resistant MFA user authentication YubiKeys 
Think “good enough” is enough? Think again about mobile devices as authenticators Explore the hidden costs and pitfalls of using mobile devices as authenticators. We’ll dive into critical factors such as the user lifecycle, security, phishing resistance, user experience, management, and total cost of ownership. Read more mobile authentication phishing-resistant MFA YubiKey 
Beyond passwords: How Okta secured their global workforce with Yubico Join Yubico and Okta to learn first-hand about some of the challenges that Okta faced and why they chose Yubico as their partner to deliver a large-scale, global, solution with the highest level of phishing-resistant assurance. Read more Okta passwordless phishing-resistant MFA YubiKey 
Lions, Tigers, Bears…and MFA Mandates? Oh my! Join us as we demystify MFA mandates and give you the tools to confidently navigate this evolving landscape. Read more compliance MFA mandates phishing-resistant MFA 
The progression of MFA: How Yubico and key partners work together to provide solutions that make an impact Download our exclusive datasheet and take the first step towards enhancing your organization’s security posture. Read more MFA phishing-resistant MFA YubiKey 
Protecting the supply chain across the DIB with modern authentication Learn how Yubico can help secure critical and modern IT and OT use cases across the Defense Industrial Base (DIB) manufacturing sector. Read more authentication phishing-resistant MFA Yubico YubiKey 
Phishing-resistant MFA for education Learn how you can stop successful cyber attacks in education by cultivating phishing-resistant users across faculty, staff and students. Read more cybersecurity phishing-resistant MFA YubiKey 
Navigating cyber threats: Building resilience with Yubico and Microsoft Join us to learn what Chad Thunberg, Yubico CISO, and Derek Hanson, Yubico VP of Alliances, have to say about cyber resiliency. Read more cyber resilience Microsoft passwordless phishing-resistant MFA 
Modernizing authentication across global critical infrastructure Learn from global critical infrastructure organizations about their journey deploying modern authentication with hardware-backed passkeys to protect from modern cyber threats. Read more securing critical infrastructure Yubico YubiHSM YubiKey 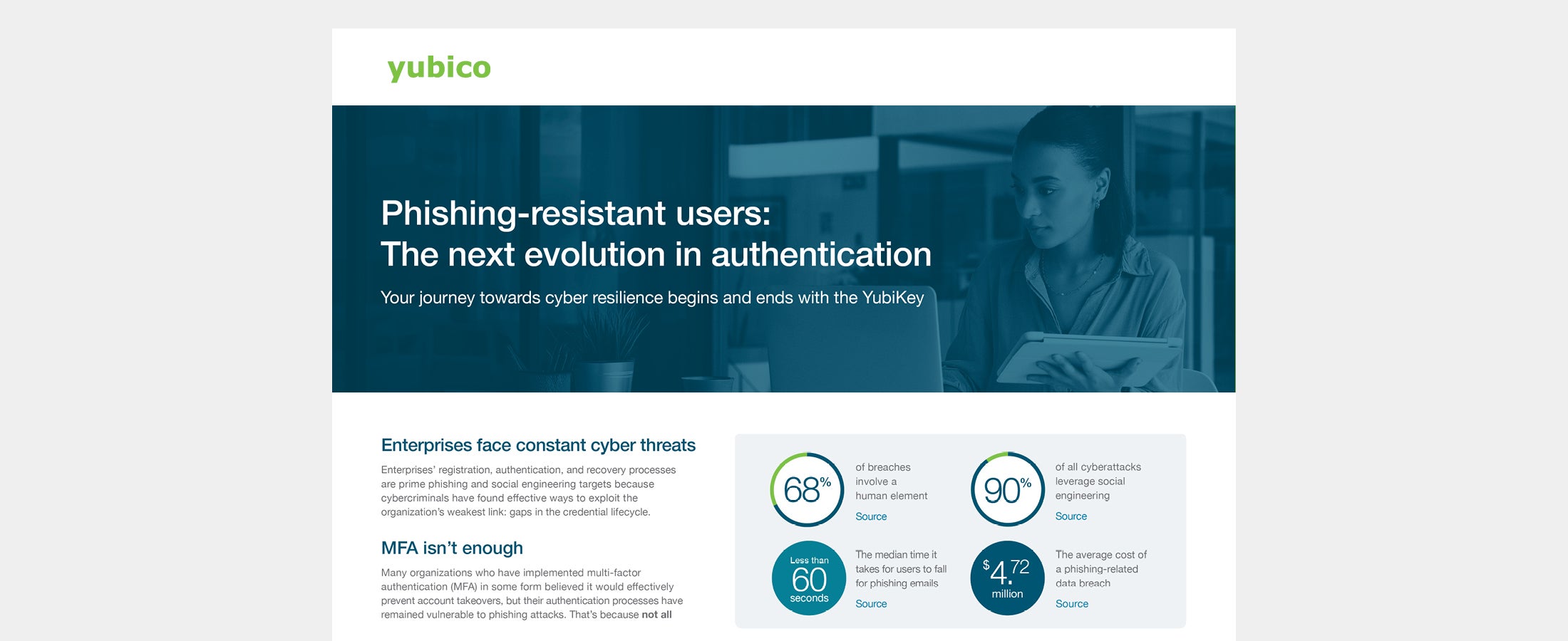
Phishing-resistant users: The next evolution in authentication Protect your enterprise from phishing and social engineering with YubiKey, ensuring phishing resistant authentication wherever users work. Read more Enterprise phishing-resistant authentication Yubico 
Modernizing authentication across retail and hospitality Read this brochure to learn from global retail and hospitality organizations about their journey deploying modern authentication with hardware-backed passkeys to protect from modern cyber threats. Read more retail and hospitality YubiKey 
Cyber risk management guide for authentication in manufacturing In this guide, we will outline how to identify, assess, and prioritize risk mitigation strategies that respect the constraints of today while also creating a bridge to modern, phishing-resistant multi-factor authentication (MFA) and passwordless. Read more manufacturing passwordless phishing-resistant MFA 
Doable and durable cyber defenses for manufacturers Join us and learn more during this session from our three guests about the cyber threats manufacturers face every day and get guidance on strengthening your defenses—for a secure and resilient 2025. Read more cyber resilience manufacturers phishing-resistant MFA 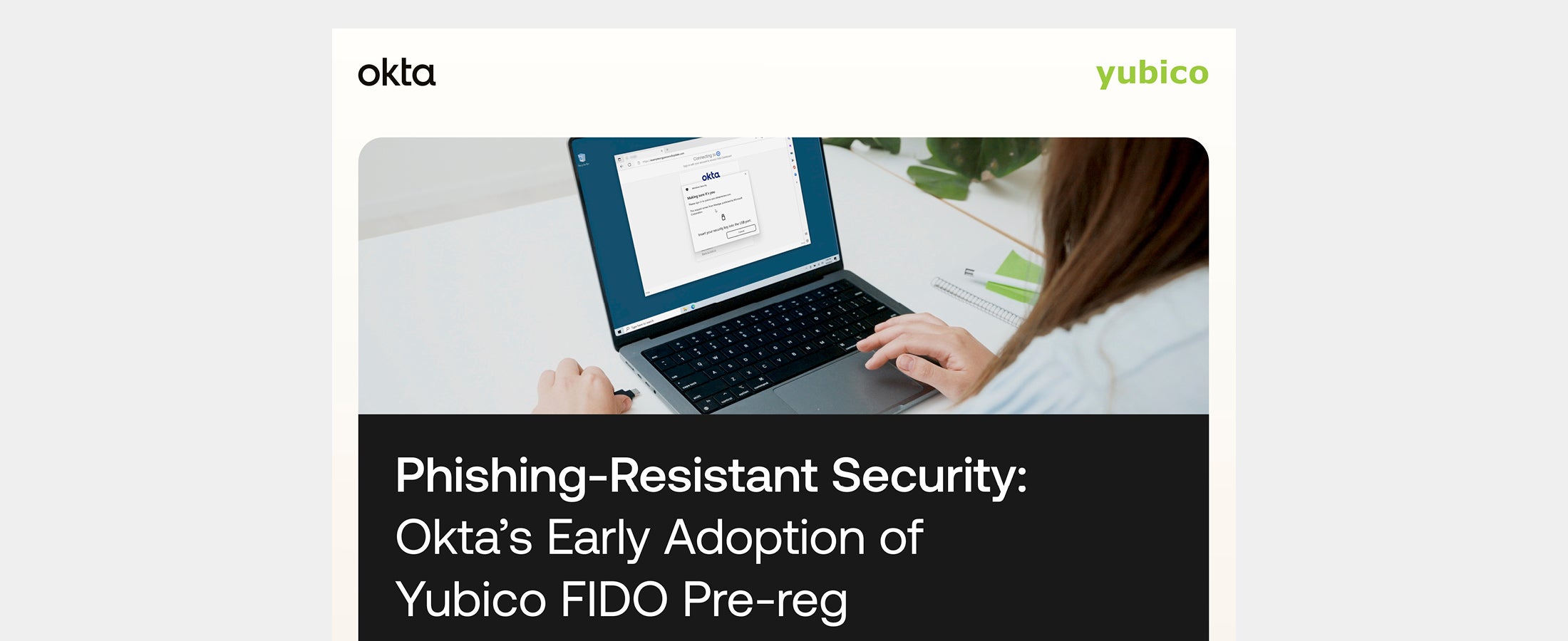
Phishing-Resistant Security: Okta’s Early Adoption of Yubico FIDO Pre-reg Download this free infographic to learn more about how Okta became an early adopter of Yubico FIDO Pre-reg, deploying YubiKeys to its entire global workforce to establish an end-to-end phishing-resistant authentication experience. Read more Okta phishing-resistant MFA Yubico FIDO Pre-reg 
Prepare for DORA Compliance with the YubiKey Learn how Yubico solutions can help your organization prepare for DORA Compliance. Read more compliance DORA phishing-resistant MFA YubiKey 
Cybersecurity for manufacturers In partnership with Smart Industry and Yubico, explore this ebook to learn how to secure manufacturing operations from the factory floor to the boardroom, including OT and IT systems and data, from modern cyber threats. Read more cybersecurity manufacturing phishing-resistant MFA 
Remaining cyber resilient: Top recommendations for 2025 With 2024 soon to be in the rear view mirror, prepare for a safe 2025 by attending this webinar to learn what organizations and individuals should be prioritizing to become phishing-resistant users and become cyber resilient against an ever evolving cyber threat landscape. Read more cyber resilience passwordless phishing-resistant MFA zero trust 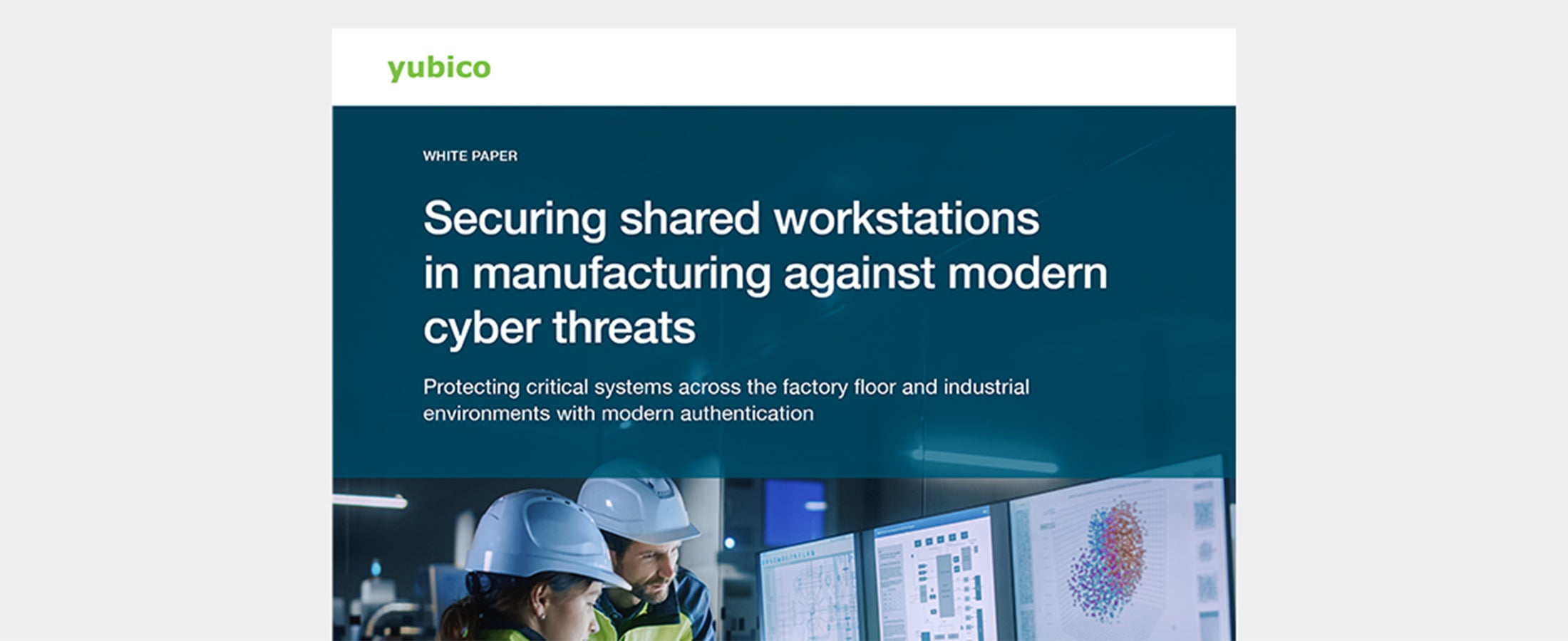
Securing shared workstations in manufacturing against modern cyber threats Download the Yubico white paper to learn the key considerations for authentication across manufacturing shared workstation environments. Read more manufacturing phishing-resistant MFA shared workstations 
Yubico’s white glove service Learn how you can simplify security and streamline global distribution of YubiKeys at scale with Yubico’s white glove service. Read more 
Yubico Enrollment Suite Download this brief to learn how Yubico helps organizations pre-enroll YubiKeys, reducing IT burden and enabling phishing-resistant, passwordless users. Read more passwordless phishing-resistant MFA 
How to create phishing-resistant users with fast, out-of-the box YubiKey FIDO activation with Okta Get started on building phishing-resistant security with Yubico FIDO Pre-reg and Okta! For a successful YubiKey deployment, download the guide. This resource outlines a six-step process covering planning, validation, integration, launch, adoption, and success measurement—providing essential strategies to help organizations enhance security and operational efficiency with phishing-resistant MFA. Read more Okta passkey passwordless phishing-resistant MFA 
Streamline Phishing-Resistant MFA: Simplified Passkey Provisioning with Microsoft and Yubico Join us as we explore the seamless adoption of phishing-resistant multi-factor authentication (MFA) through Microsoft’s new Entra ID passkey (FIDO2) provisioning APIs. Read more APIs Microsoft phishing-resistant MFA YubiKey 
Yubico and Versasec: Strengthening Cybersecurity in the Middle East Join us as we explore the ever-growing cyber threats and the essential role that enterprise multi-factor authentication (MFA) plays in enhancing security. Read more cybersecurity phishing-resistant MFA YubiKey 
AI cyber threats: 30 minutes to midnight Join us to learn about the present and future state of AI phishing and how to tackle both today’s and tomorrow’s cyber threats. Read more AI passwordless phishing-resistant MFA 
Phishing-resistant MFA accelerates enterprises to passwordless Join this session to learn how to secure your infrastructure with phishing-resistant MFA and begin your journey to passwordless authentication. Read more passwordless phishing-resistant MFA YubiKey 
YubiKey as a Service Solution Brief A modern way to adopt phishing-resistant MFA and passwordless over traditional perpetual purchasing models. Download the brief to learn more. Read more passwordless phishing-resistant MFA YubiKey as a Service 
Navigate the evolving threat of phishing and social engineering with passkeys Join this session to learn about the evolving threat landscape and how becoming a phishing-resistant user and using the right passkey approach can help stop account takeovers in their tracks. Read more passkeys phishing-resistant users stop account takeovers 
Powering stronger cyber defenses in the energy sector Learn how energy and natural resource organizations can protect themselves with modern phishing-resistant authentication (MFA). Read more energy oil and gas YubiHSM YubiKey 
Creating phishing-resistant users across financial services in a passkey age Download the Yubico e-book, Creating phishing-resistant users across financial services in a passkey age, to learn about the difference between synced passkeys and device-bound passkeys. Read more 
Protecting insurance organizations against modern cyber threats Learn how insurance organizations can alleviate cyber risk by cultivating phishing-resistant users using the YubiKey for phishing-resistant multi-factor and passwordless authentication. Read more insurance phishing-resistant MFA YubiKey 
Drive business continuity and cyber resilience with modern FIDO security keys Learn how modern FIDO security keys drive business continuity and cyber resilience while creating always-on enterprises. Read more cyber resilience FIDO YubiKey 
Embracing critical infrastructure security and resilience with phishing-resistant MFA Learn why the YubiKey for phishing-resistant authentication should be an important part of your cybersecurity strategy to mitigate cyber risk and protect the business continuity of critical infrastructure sectors. Read more critical infrastructure cyber resilience phishing-resistant MFA 
2024 State of Global Authentication: Tackling Cyberthreats at Work & Home Join us to dive into how cybersecurity impacts our daily lives and businesses, and learn about the risks of poor security practices. We’ll break down what makes a solid cybersecurity plan that covers both personal and professional spaces, including tips on using stronger authentication methods to fend off phishing attempts. Read more best practices cybersecurity phishing-resistant MFA 
NIS2 Compliance The NIS2 Directive, effective January 2023, expands the scope of the original NIS Directive to include stricter cybersecurity requirements across more sectors in the EU. It mandates enhanced security measures like incident reporting, multi-factor authentication, and supply chain security, with penalties for non-compliance reaching up to €10M or 2% of annual revenue. Organizations must ensure compliance by October 2024 to avoid significant fines and operational risks. Read more compliance nis2 YubiKey 
How to get started with the YubiKey for education Learn the six deployment best practices to protect your education organization from cyberattacks and accelerate adoption at scale. Read more best practices guide deployment education YubiKey 
Modern authentication for high-tech manufacturers Download this free brochure to learn how Yubico solutions safeguard critical IT and OT systems, sensitive IP, and the supply chain for high tech manufacturers. Read more high-tech manufacturing modern authentication 
Build cyber resilience with Yubico and Microsoft to accelerate to passwordless Join us as we investigate lessons learned from incidents such as Crowdstrike and MGM Grand, and examine different passkey solutions and how they fit into building a resilient, phishing-resistant organization. Read more cyber resilience Microsoft passwordless phishing-resistant MFA 
The evolving threat of phishing and social engineering The report classifies the three major passkey credentials in the market and highlights the benefits of creating phishing-resistant users. Read more 
Active Directory Security Management: From Threat Detection to Effective Response Join us for this informative session to enhance your AD security management skills and safeguard your organization’s critical assets. Read more Active Directory cybersecurity phishing-resistant MFA YubiKey 
Securing Your Organization with YubiKeys at Scale – Part 2 Join us for this in-depth session as we navigate the YubiKey journey, equipping you with the knowledge and tools to elevate your organization’s rollout strategy with confidence. Read more deployment phishing-resistant MFA YubiKey 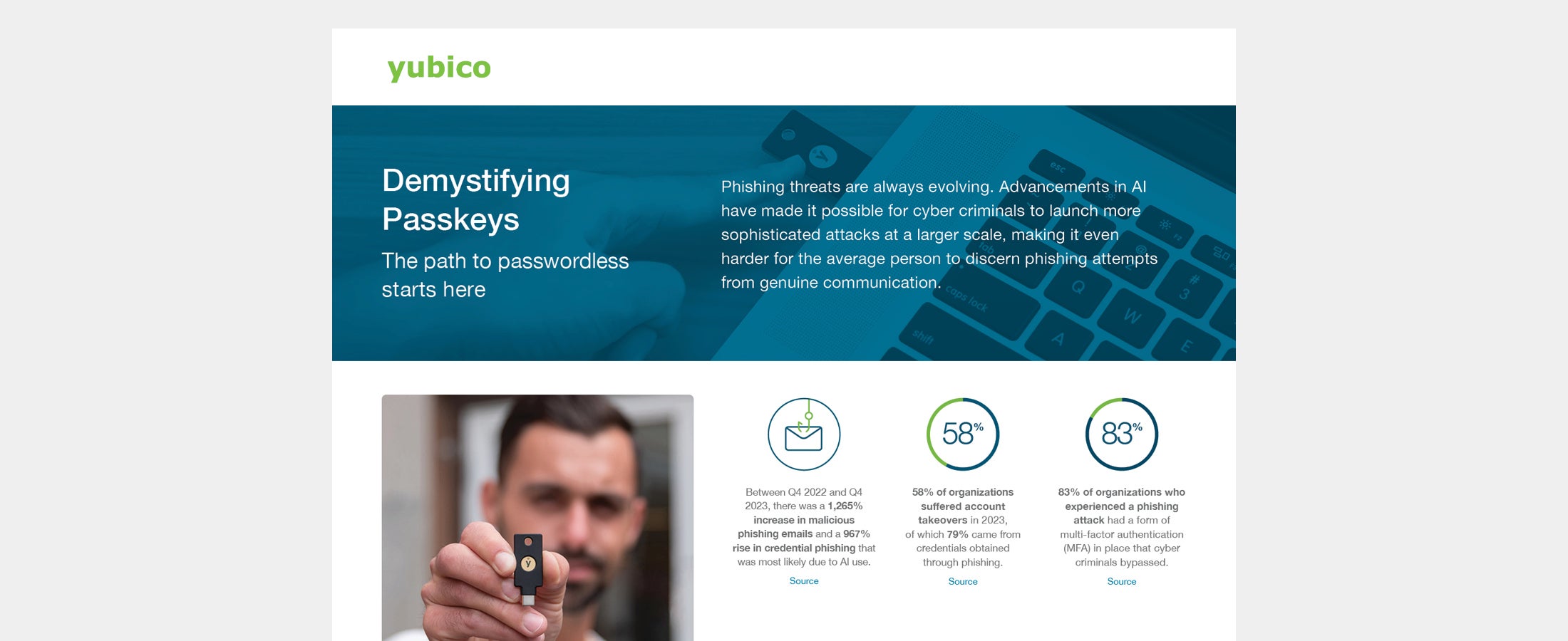
Demystifying passkeys Organizations can avail of three different types of passkey implementations but it is vital to choose the right passkey approach based on your organization’s required security and risk posture. View the Yubico visual industry brief to learn more. Read more passkeys passwordless phishing-resistant users YubiKey 
Going passwordless in a passkey age Read the Yubico white paper to get real guidance on how enterprises can evaluate passwordless authentication options in the age of passkeys. This white paper discusses how enterprises can address and mitigate current and future issues with a sound passwordless deployment. Read more passkeys passwordless YubiKey 
Phishing-Resistant Insurance Enterprises Protect your insurance organization from costly phishing attacks and data breaches with YubiKey’s phishing-resistant authentication. Learn how to enhance security, save on mobile costs, and improve user experience. Read more enterprise security insurance phishing-resistant users 
Modern authentication for the Army Download the free brochure to learn how the YubiKey solves U.S. Army authentication modernization use cases. Read more modern authentication YubiKey zero trust 
YubiKey as a Service product brief Learn how YubiKey as a Service can help you accelerate to passwordless and create phishing-resistant users across the enterprise. Read more Enterprise YubiKey as a Service 
Going passwordless and meeting CJIS at City of Southgate Join us for a candid discussion with Jason Rucker, Director of IT, City of Southgate, and Robb Ervin, Sr Solutions Engineer, Yubico to learn about the goals, timelines, obstacles and wins along their passwordless deployment journey. Read more CJIS deployment passwordless YubiKey 
How to get started with phishing-resistant MFA for Essential 8 compliance Learn six deployment best practices that can help you accelerate the adoption of modern, phishing-resistant MFA at scale using the YubiKey. Read more best practices guide compliance phishing-resistant MFA 
How to get started with phishing-resistant MFA for Essential 8 compliance thank you We hope you enjoy reading the Yubico Best Practices Guide, How to get started with phishing-resistant MFA for Essential 8 compliance. Read more 
Enhancing Federal Security: Issuing PIV-Compatible Credentials with Axiad Cloud (FedRAMP) and Yubico Join this webinar to gain a comprehensive understanding of how you can streamline the credentialing process and ensure compliance with federal standards while enhancing security and efficiency. Read more government phishing-resistant MFA PIV YubiKey 
Create phishing-resistant users and accelerate your enterprise to passwordless Watch this webinar to learn how phishing-resistant users create phishing-resistant enterprises that can accelerate to enhanced security and operational efficiency, all within a modern passwordless environment. Read more passwordless phishing-resistant users YubiKey 
Build robust cybersecurity postures with cyber insurance & modern authentication Brent Deterding, CISO, Afni and Davis Hake, Co-founder, Insurtech, discuss the current cybersecurity and cyber insurance landscape and how leaders of today and tomorrow should be planning for the new age of cyber offense without breaking the bank. Read more cyber insurance cybersecurity passwordless phishing-resistant users 
The importance of cybersecurity and the impact of AI on the 2024 elections Join Yubico and Defending Digital Campaigns for this webinar as they dive into their recent survey results. Read more elections and political campaigns MFA 
Every user is a privileged user The idea of “privileged users” has expanded beyond the IT function to include any business users who possess access to exploitable systems or IP, making all users target of sophisticated cyber attacks. Learn how to cultivate phishing-resistant users with modern, phishing-resistant multi-factor authentication (MFA). Read more phishing-resistant MFA phishing-resistant users privileged users YubiKey 
Securing federal systems integrators and the defense industrial base with modern authentication FSIs have access to critical systems and hold large volumes of sensitive and Controlled Unclassified Information (CUI), making them targets of sophisticated cyber attacks. Any MFA is better than a password, but not all MFA is created equal. Download the visual industry brief to learn how FSIs and the DIB can protect themselves with modern, phishing-resistant multi-factor authentication (MFA). Read more federal government federal systems integrators phishing-resistant MFA 
Supercharging telcos against modern cyber threats Learn why it is critical that phishing-resistant authentication be the first line of defense for telecommunication organizations. Read more modern cyber threats phishing-resistant MFA Telecommunication 
What’s new in YubiKey 5.7 The new YubiKey 5.7 firmware fast-tracks enterprises to passwordless authentication with a secure, simple, and scalable solution that ensures the highest assurance authentication for modern enterprises. Read more enterprise security passwordless YubiKey 5.7 
Unlocking the future: Fast-tracking modern enterprises to passwordless Join this webinar to discover how Yubico’s latest innovations in YubiKey 5.7 enhance enterprise security, streamline authentication processes, account setups, and fast-track your journey towards a secure, passwordless future. Read more enterprise security passwordless YubiKey 5.7 
Unlocking the future: Navigating passkeys to passwordless security at scale Join this webinar to learn about the benefits of passkeys in the landscape of passwordless options, life cycle considerations for achieving a successful passwordless rollout at scale and the latest enterprise-centric updates for YubiKeys. Read more passkeys passwordless phishing-resistant MFA YubiKey 
Accelerating financial services from legacy MFA to modern passkey authentication Watch this webinar to learn the pros and cons of different types of passkey approaches financial services institutions should consider in their move away from legacy authentication. Read more financial services passkeys passwordless phishing-resistant MFA 
Meeting the Sept 2024 White House phishing-resistant MFA deadline Learn best practices from government executives on their agencies’ journeys, how they navigated challenges and pitfalls to achieve compliance and what steps your agency can take right now to show intent and progress toward phishing-resistant MFA. Read more compliance federal government phishing-resistant MFA 
How to get started with phishing-resistant MFA to secure federal systems integrators Explore best practices for implementing phishing-resistant multi-factor authentication (MFA) tailored for Federal Systems Integrators (FSIs) to enhance security against sophisticated cyber threats. Read more federal systems integrators MFA phishing-resistant authentication 
Securing Federal Systems Integrators with modern authentication Learn how Federal Systems Integrators (FSIs) can modernize their authentication stack and create phishing-resistant users and systems to protect against modern cyber threats. Read more cybersecurity federal government phishing-resistant MFA 
CISOs: Transform Zero Trust to an organization-wide priority Learn why every CISO’s Zero Trust strategy should start with phishing-resistant MFA. Read more CISO phishing-resistant MFA YubiKey zero trust 
What is FIDO and why is it important for business security? Learn what FIDO is, how it works, and how your organization can benefit from deploying FIDO-based authentication across critical business scenarios. Read more FIDO MFA passwordless strong authentication 
Best practices to secure critical infrastructure with phishing-resistant MFA Learn about the need for adopting phishing-resistant MFA to secure critical infrastructure and deployment best practices gathered from numerous global deployments across variety of sectors. Read more best practices critical infrastructure deployment phishing-resistant MFA 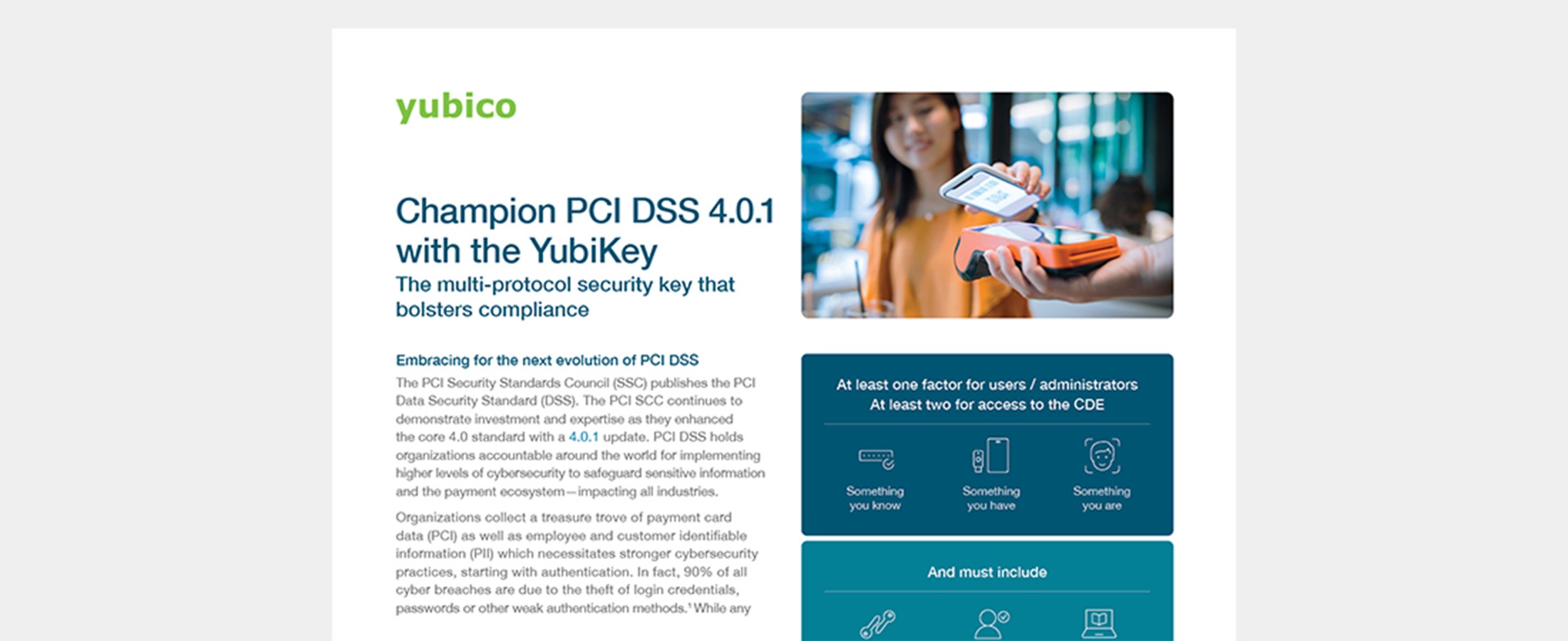
Champion PCI DSS 4.0.1 with the YubiKey Learn what PCI DSS 4.0.1 means for your authentication strategy and how phishing-resistant MFA using the YubiKey bolsters your compliance posture to meet the needs of today and into the future. Read more PCI DSS phishing-resistant MFA YubiKey 
Enhancing Federal Cybersecurity Explore our infographic on YubiKey’s phishing-resistant multi-factor authentication (MFA) solutions tailored for the federal government. Read more federal government modern authentication modern cyber threats 
CFOs: Lower cyber insurance premiums with phishing-resistant MFA Discover how CFOs can strengthen cybersecurity and significantly lower cyber insurance costs with Yubico’s phishing-resistant MFA. Read more cyber insurance cybersecurity phishing-resistant authentication 
CEOs: Secure critical infrastructure starts with you Learn why every CEO’s business continuity strategy should start with phishing-resistant MFA. Read more C-Suite critical infrastructure phishing-resistant MFA 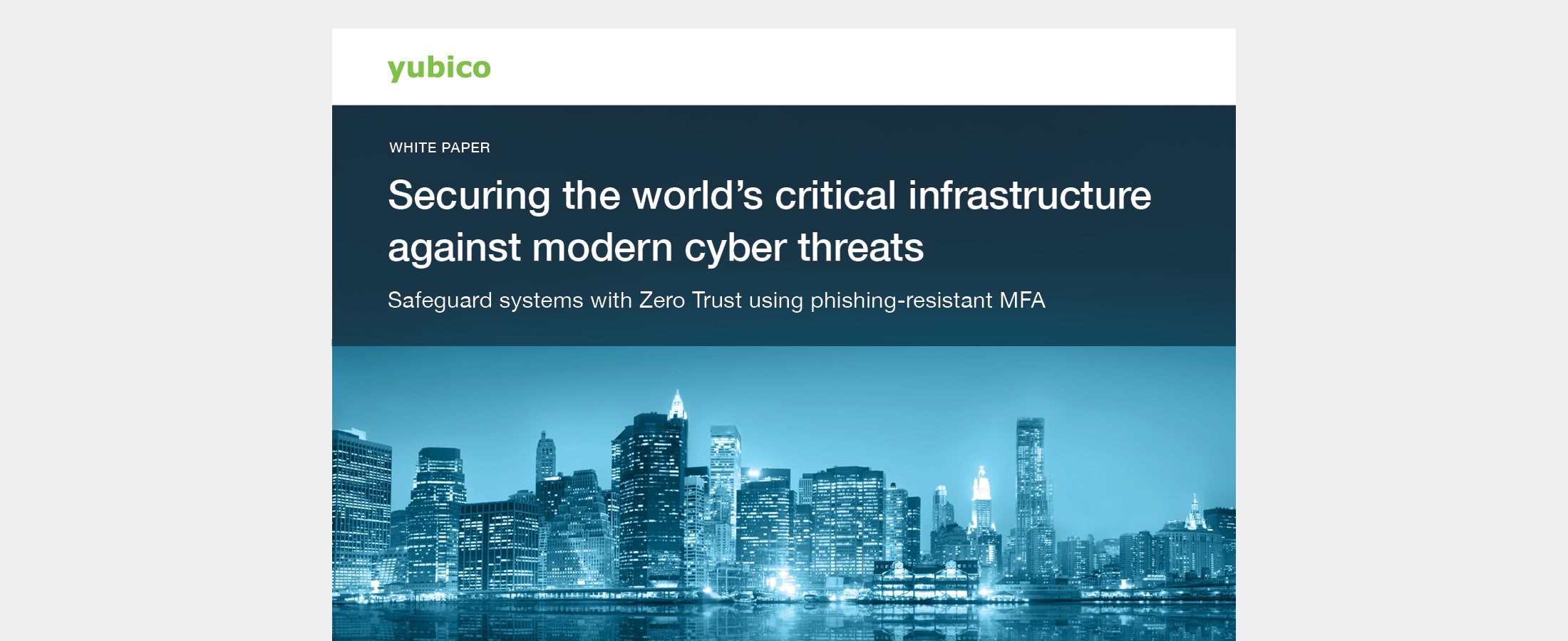
Securing the world’s critical infrastructure against modern cyber threats Learn how to safeguard IT/OT systems and the supply chain with Zero Trust using phishing-resistant MFA and hardware-backed security. Read more critical infrastructure phishing-resistant MFA zero trust 
How to get started with phishing-resistant MFA to secure pharmaceuticals Learn the six deployment best practices that can help the pharmaceutical industry accelerate adoption of modern, phishing-resistant MFA at scale using the YubiKey. Read more best practices guide Pharma phishing-resistant MFA YubiKey 
Yubico|Microsoft: On-the-go enterprise authentication, at speed and scale Learn more about the current cybersecurity landscape and how collaborations like the one between Yubico and Microsoft play a crucial role in driving the adoption of standards and technologies that raise the bar for enterprise security. Read more cybersecurity enterprise authentication Microsoft YubiKey 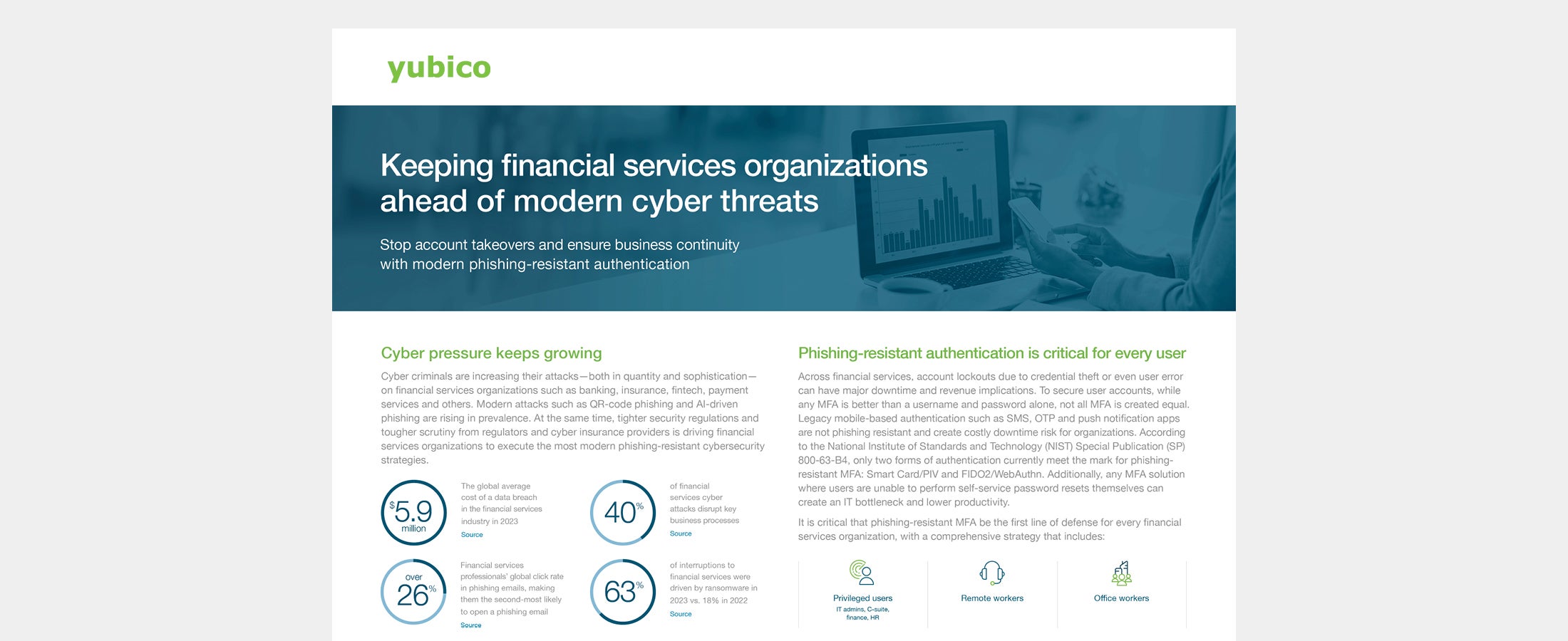
Keeping financial services organizations ahead of modern cyber threats Learn more about stopping account takeovers and ensuring business continuity with modern phishing-resistant authentication for financial services organizations. Read more account takeovers financial services phishing-resistant MFA YubiKey 
How to bolster your authentication strategy for PCI DSS 4.0 Learn about what this new standard means for you and how not all forms of multi-factor authentication (MFA) are created equal in terms of compliance and mitigating cyber risk. Read more compliance MFA PCI DSS 
Professional Services Deployment Best Practices Workshop A targeted workshop which provides guidance, operational tips and best practices to help clients successfully deploy YubiKeys in their organization. Read more best practices guide phishing-resistant MFA professional services YubiKey 
Professional Services YubiHSM Hours Bundle Expert on-demand Professional Services hours providing technical assistance in implementing and managing YubiHSMs in client environments. Read more cybersecurity phishing-resistant MFA professional services YubiHSM 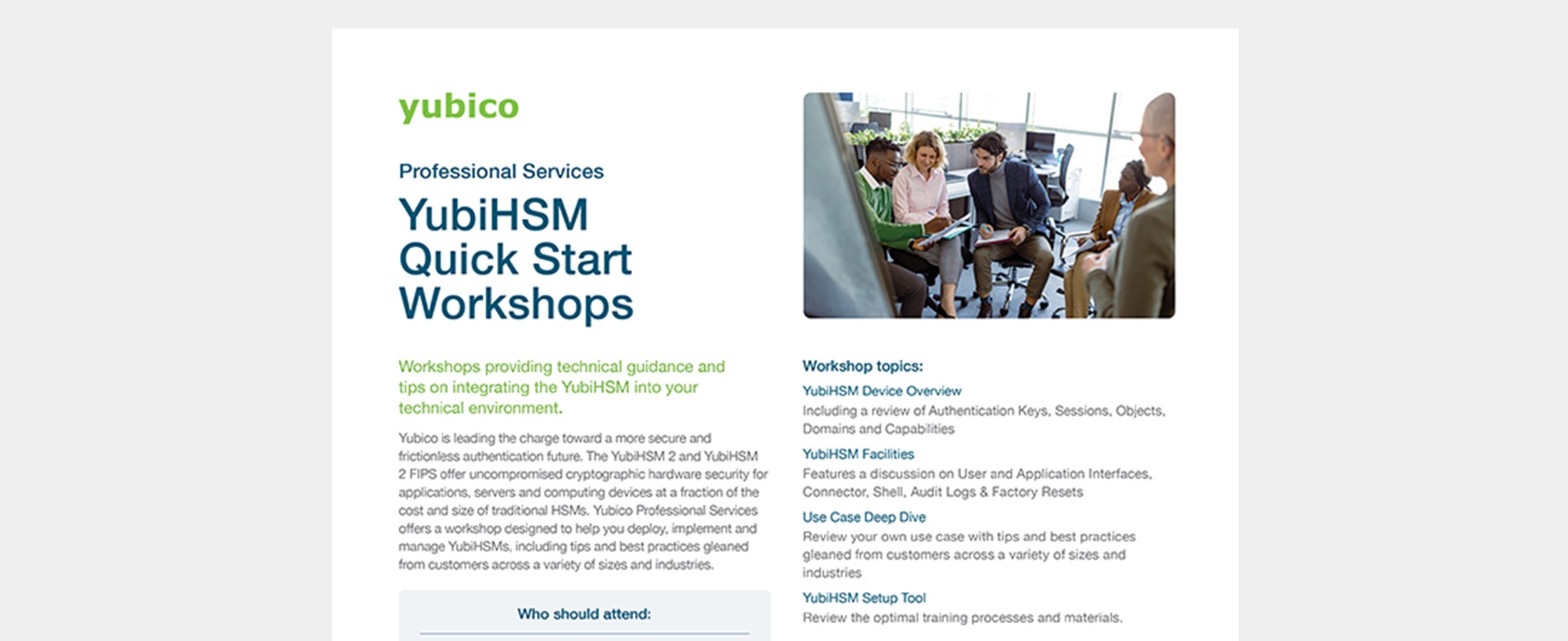
Professional Services YubiHSM Quick Start Workshop A fast track workshop providing expert technical guidance, tips and best practices on integrating and managing YubiHSMs into client environments. Read more best practices guide phishing-resistant MFA professional services YubiHSM 
How to get started with phishing-resistant MFA to secure telecommunications Learn deployment best practices to accelerate adoption at scale and secure your organization from account takeovers for telecommunications. Read more phishing-resistant MFA Telecommunication Yubico 
Securing Department of Defense in 2024 with phishing-resistant MFA Watch this webinar to learn more about how Federal policy makers are increasingly focusing on phishing-resistant MFA. Read more passwordless phishing-resistant authentication zero trust 
Modern authentication for the Department of the Air Force Download the free brochure to learn how the YubiKey solves U.S. Air and Space Force modernization uses cases. Read more government phishing-resistant MFA YubiKey 
Securing Your Organization with YubiKeys at Scale – Unleashing the Advantage & Managing the Challenges with Intercede MyID Join this webinar for an in-depth session as we navigate the YubiKey journey, equipping you with the knowledge and tools to elevate your organization’s rollout strategy with confidence. Read more best practices phishing-resistant MFA YubiKey 
State and local government best practices guide Learn the six deployment best practices that can help your agency accelerate adoption of modern, phishing-resistant MFA at scale. Read more best practices guide phishing-resistant MFA state and local government YubiKey 
Building a phishing-resistant enterprise with device-bound passkeys Building an enterprise that stops account takeovers with phishing-resistant MFA using a device-bound passkey strategy. Read more account takeovers passkeys passwordless phishing-resistant MFA 
Protect manufacturers from modern cyber threats Manufacturers of all kinds are being targeted by ransomware and phishing at an alarming rate. They need modern MFA that protects existing infrastructure while enabling the move to stronger phishing-resistant methods. Learn how Yubico can help safeguard your production and profits with phishing-resistant MFA and hardware-backed security. Read more manufacturers phishing-resistant MFA YubiHSM YubiKey 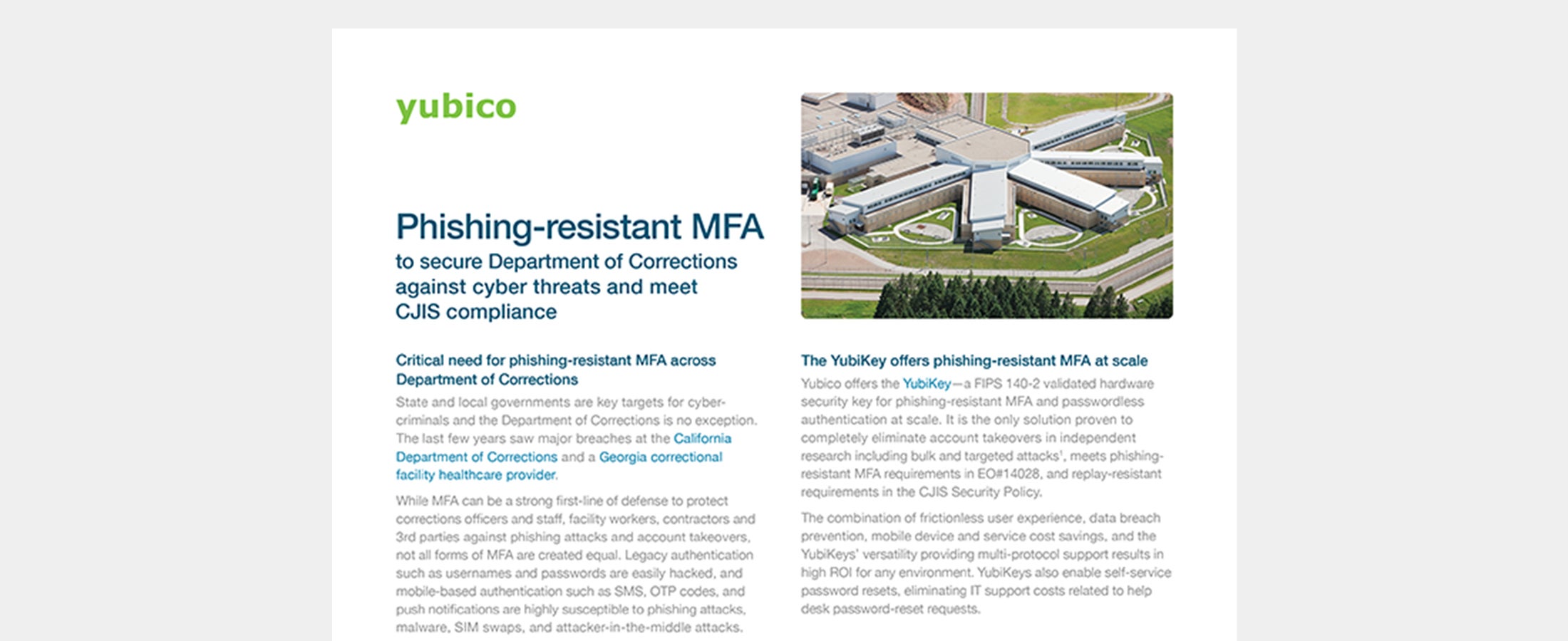
Securing Department of Corrections with modern, phishing-resistant MFA Learn how the YubiKey stops modern cyber threats such as phishing attacks and account takeovers across the Department of Corrections, with CJIS compliant phishing-resistant multi-factor and passwordless authentication. Read more government passwordless phishing-resistant MFA YubiKey 
Modern authentication for the modern naval war fighter Download the free brochure to learn how the YubiKey solves U.S. Navy modernization uses cases. Read more CAC FIPS 140-2 modern authentication 
How to get started with phishing-resistant MFA to secure healthcare Download the healthcare best practices guide to learn six deployment best practices to accelerate adoption at scale. Read more best practices guide healthcare 
Secure your AWS environment with highest-assurance phishing-resistant MFA Download the best practice guide to learn more how you can stop account takeovers and go passwordless for a wide variety of AWS use cases Read more AWS passwordless phishing-resistant MFA 
Enterprise passkey implementations: Key considerations and tradeoffs Join this webinar to learn more about the different types of passkey implementations and gain an understanding of real life enterprise scenarios. Read more Enterprise passkey 
Securing financial services with modern, phishing-resistant MFA Learn how the YubiKey helps financial organizations drive high security against modern cyber threats and high user productivity with the best user experience. Read more financial services passwordless phishing-resistant MFA 
Securing remote workers with phishing-resistant MFA Learn why legacy authentication such as usernames and passwords, and mobile-based authenticators don’t protect remote workers against phishing attacks and account takeovers, and how the YubiKey ensures phishing-resistant multi-factor and passwordless authentication for critical remote work authentication business scenarios. Read more phishing-resistant MFA remote and hybrid workers YubiKey 
Cyber hygiene: Enterprise resource guide for getting started with your YubiKey The YubiKey works with hundreds of applications and services, making strong security across multiple accounts simple and effective. Yubico is giving you a jumpstart on your multi-factor authentication journey by providing an enterprise resource guide to help you get your YubiKey up and running to protect applications and services within your organization. Download our ‘Enterprise […] Read more cybersecurity Enterprise security 
Okta and Yubico: Delivering phishing-resistant MFA and a bridge to passwordless Learn how YubiKeys and Okta FastPass work together to provide the strongest levels of identity assurance against phishing while delivering a fast and easy user experience. Read more Okta passwordless phishing-resistant MFA YubiKey 
How to get started with phishing-resistant MFA for your Microsoft environment Learn about the six key best practices to accelerate the adoption of phishing-resistant MFA and how to ensure secure Microsoft environments. Read more best practices guide Microsoft phishing-resistant MFA 
Secure your AWS environment phishing-resistant MFA Explore the YubiKey by Yubico for secure AWS authentication: phishing-resistant, multi-protocol support, and easy integration. Read more AWS MFA phishing-resistant authentication 
AWS Best practices guide Download this Best Practices Guide to learn about six deployment best practices to accelerate your adoption of phishing-resistant MFA for your AWS environment at scale. Read more AWS best practices guide phishing-resistant MFA 
Modernizing authentication across the Department of Defense with phishing-resistant MFA Learn how the DOD-approved and FIPS 140-2 validated YubiKey is helping the federal government with phishing-resistant multi-factor authentication (MFA) for modern use cases not supported by the PIV and CAC Read more government modern authentication phishing-resistant authentication 
Transcending Passwords: Emerging Trends in Authentication Watch this webinar to learn more about the business impact and trends of authentication practices, with consequences for security, productivity and employee retention. Read more passwordless phishing-resistant MFA strong authentication 
How to get started with passwordless using device-bound passkeys Read the Yubico deployment best practices guide to get started with device-bound passkeys for your passwordless authentication journey. Read more best practices guide passkeys passwordless YubiKey 
Go Passwordless with Windows Hello for Business and YubiKeys Learn how Windows Hello for Business and YubiKeys work in concert to provide solutions for your organization and your customers. Read more Microsoft passwordless phishing-resistant MFA YubiKey 
Safeguard your Microsoft ecosystem with a Zero Trust strategy Learn why there is a critical need for phishing-resistant MFA to support Zero Trust for Microsoft environments. Read more Microsoft phishing-resistant MFA YubiKey zero trust 
Making the internet safer with modern authentication Learn more about how Yubico helps secure global enterprises, SMBs, and individuals with modern phishing-resistant multi-factor authentication (MFA) and passwordless. Elevate your cyber resilience and accelerate your zero trust strategy with modern authentication that stops phishing attacks and account takeovers before they start. Read more modern authentication phishing-resistant MFA YubiKey 
Transcending Passwords: The Next Generation of Authentication The report exposes the business impact of authentication practices, with consequences for security, productivity and employee retention. Read more authentication cybersecurity passwordless 
Transcending passwords: Emerging trends in authentication Enterprises that eliminate passwords report better business and security outcomes. New research finds organizations using passwordless technologies experience the fewest phishing attacks, are more productive and achieve greater levels of employee satisfaction. Read more authentication passwordless 
Yubico and Okta: Raising the bar for security Download the Yubico and Okta eBook to learn the importance of a strong security posture and actions you can take today to secure your organization’s future. Read more cybersecurity Okta phishing-resistant MFA 
Secure retailers and hoteliers Embrace a customer-centric security solution with phishing-resistant MFA that champions security and usability. Read more cybersecurity phishing-resistant MFA retail and hospitality 
Fast, Out-of-the-Box FIDO Activation with Yubico and Okta Learn more about the approach of “Accelerating Phishing-Resistant MFA and Passwordless with Fast, Out-of-the-Box FIDO Activation with Okta.” Read more Okta phishing-resistant MFA YubiKey 
Holiday shopping is underway: are you protecting yourself online? Join this webinar, and hear from our security experts to better understand the current cyber threat landscape, and learn best practices to stay secure online through the holiday season and beyond. Read more cybersecurity Holiday 
Many roads to passwordless: How passkeys fit in the modern landscape Passkeys are the long awaited replacement for passwords. Come learn how passkeys help accelerate widespread adoption of passwordless authentication for consumers and organizations. Read more passkeys passwordless 
Protecting Federal Systems Integrators Learn how phishing-resistant MFA can help federal systems integrators stop phishing attacks and account takeovers with phishing-resistant MFA Read more account takeovers phishing-resistant MFA ransomware 
Manufacturers across the globe are investing in modern authentication See real stories of how global manufacturers and other leading brands changed the game for modern enterprise authentication security. Read more cybersecurity manufacturing supply chain YubiKey 
Yubico and HYPR Learn how Yubico and HYPR provide a seamless passwordless authentication experience that meets your security needs. Read more HYPR passwordless 
Energy and Natural Resources Deployment Best Practices Guide Learn the six deployment best practices that can help accelerate the adoption of modern, phishing-resistant MFA at scale using the YubiKey. Read more best practices guide energy and natural resources YubiKey 
The dark side of mobile authentication Modern cyber threats are increasing in scale so ensuring strong security for access to enterprise applications and services is a critical need across all industries. Join this webinar to learn the top 5 mobile authentication misconceptions and much more! Read more mobile authentication phishing-resistant MFA 
Retail and Hospitality Deployment Best Practices Guide Learn deployment best practices for retail and hospitality to accelerate adoption of phishing-resistant MFA at scale using the YubiKey. Read more best practices guide phishing-resistant MFA retail and hospitality 
The dark side of your mobile authentication strategy Learn the key misconceptions related to mobile-based MFA that are putting your organization at risk of being hacked. Read more mobile authentication phishing-resistant MFA 
Not all MFA is created equal ebook Explore advanced MFA methods and boost online security with Yubico’s expert insights. Download now for essential digital protection. Read more MFA phishing-resistant authentication 
How to get started with modern, phishing-resistant MFA Learn the six deployment best practices that can help your organization accelerate the adoption of modern, phishing-resistant MFA at scale using YubiKeys. Read more modern authentication phishing-resistant MFA 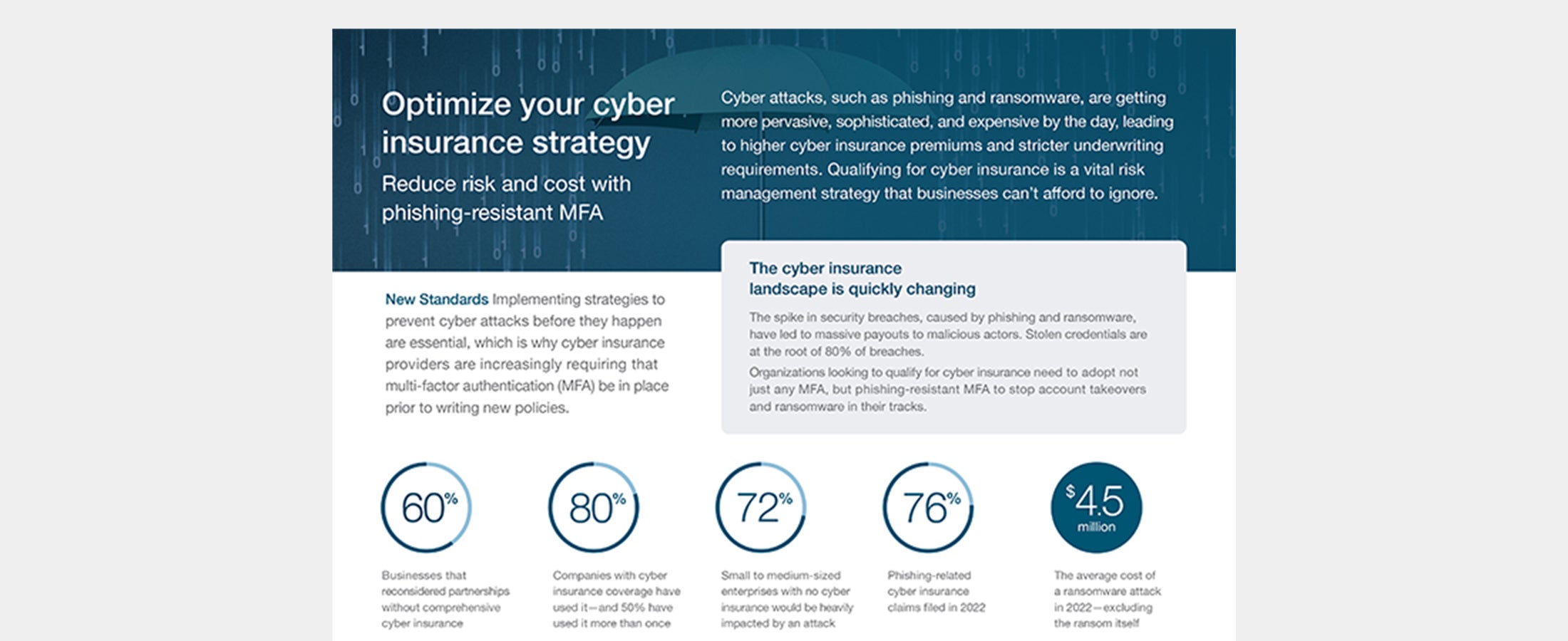
Cyber insurance strategy Cyber attacks are getting more sophisticated, and expensive, leading to higher cyber insurance premiums. Phishing-resistant MFA can help set you up for success and save on costs. Read more cyber insurance phishing phishing-resistant MFA 
Securing Critical Infrastructure Discover how phishing-resistant MFA shields global critical infrastructure. Yubico’s infographic reveals key stats and modern defense strategies. Read more critical infrastructure cybersecurity phishing-resistant MFA 
Demystifying modern, phishing-resistant MFA and deployment approaches Ensuring strong security for access to enterprise apps and services is an urgent need across all industries to protect against modern cyber threats. Join this webinar to learn deployment best practices to adopt phishing-resistant MFA and speed and scale. Read more deployment phishing-resistant MFA 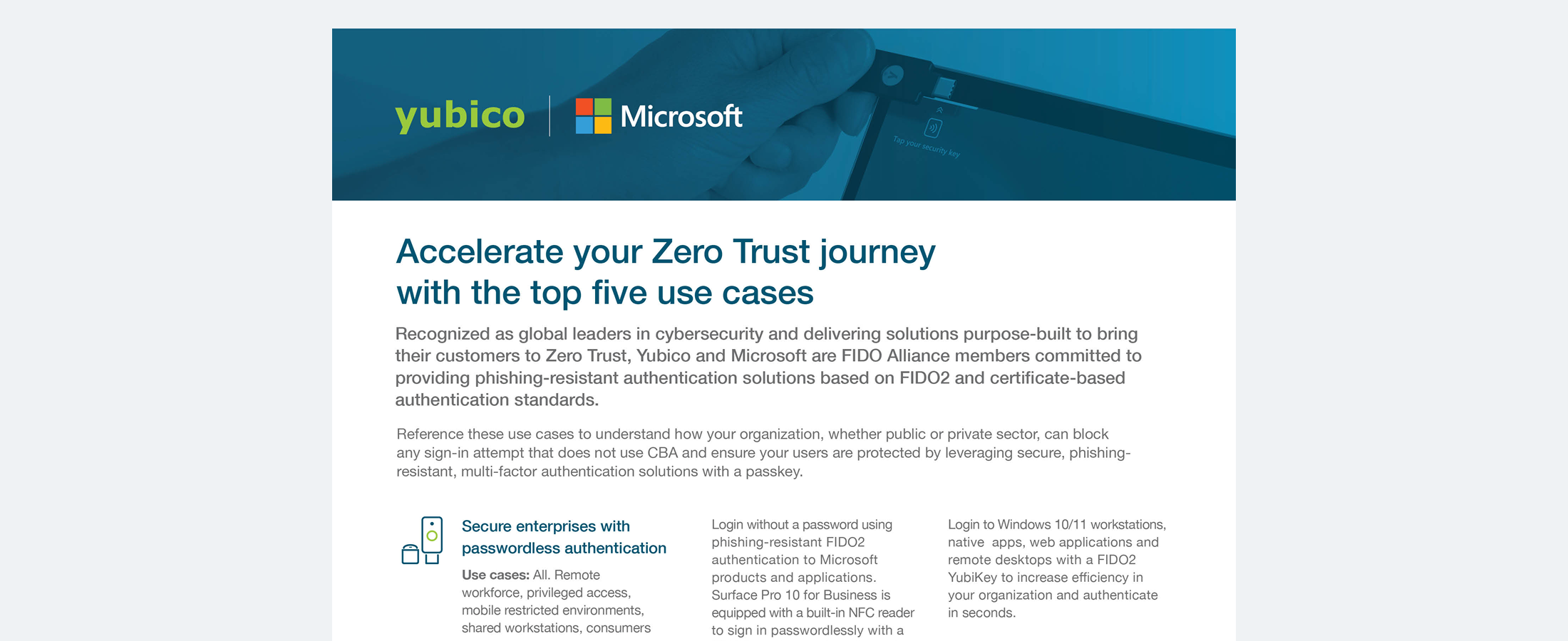
Microsoft top 5 use cases Explore how Yubico and Microsoft are revolutionizing Zero Trust cybersecurity with phishing-resistant multi-factor authentication solutions. Read more Microsoft Yubico zero trust 
Passkeys for your Enterprise? Key considerations for success Join our webinar to learn about common enterprise scenarios where synced passkeys may create some chilling failure points, and other more effective and secure passkey alternatives that put your business in the best security and compliance posture. Read more Enterprise MFA passkey 
Federal Government Deployment Best Practices Guide Learn the six deployment best practices that can help your agency accelerate adoption of modern, phishing-resistant MFA at scale using the YubiKey. Read more best practices guide federal government zero trust 
Cybersecurity Insiders report: Path to Zero Trust Rapid digital transformation, increased remote work, and evolving cybersecurity threats have catapulted Zero Trust from an IT buzzword to a foundational cybersecurity model. In our comprehensive report, “The Path to Zero Trust: Industry Insights and Best Practices”, we delve into the latest adoption trends, challenges, and the current state of Zero Trust, based on a […] Read more cybersecurity zero trust 
Best Practices Guide: How to get started with phishing-resistant MFA for Zero Trust Read the Yubico deployment best practices guide to learn how to get started with phishing-resistant MFA to meet Zero Trust security requirements. Read more deployment phishing-resistant MFA security zero trust 
Safeguard IT/OT Ecosystems Join us to hear from thought leaders at Schneider Electric and Yubico as they discuss the role of phishing-resistant authentication and hardware-backed security using Zero Trust principles across your company and supply chain. Read more hardware supply chain zero trust 
Prevent phishing with Azure AD CBA and YubiKeys on mobile devices In this webinar, you’ll hear how Yubico is working closely with Microsoft on its CBA mobile solutions to play a critical part in the fight against phishing. The companies are working together to support organizations to provide consistent and strong phishing-resistance across all platforms Read more Azure AD CBA mobile authentication phishing-resistant MFA 
Manufacturing authentication compliance checklist Learn how phishing-resistant MFA can help manufacturers embrace data protection compliance with confidence. Read more compliance manufacturing phishing-resistant MFA 
Best Practices Guide: How to get started with phishing-resistant MFA to secure manufacturing Learn the six deployment best practices that can help your manufacturing organization accelerate adoption of modern, phishing-resistant MFA and cryptographic protection using Yubico solutions. Read more manufacturing phishing-resistant MFA 
Best Practices Guide: How to get started with phishing-resistant MFA to secure financial services Learn the six deployment best practices that can help your organization accelerate adoption of modern, phishing-resistant MFA at scale using the YubiKey. Read more best practices guide financial services phishing-resistant MFA 
Phishing-resistant MFA for financial services Learn why legacy forms of MFA such as mobile-based authenticators are putting your employees at risk of being hacked, and how the phishing-resistant YubiKey can strengthen your security posture. Read more financial services modern authentication phishing-resistant MFA 
What the Authn? How Passkeys Offer a Fresh Take to Authentication Dilemmas Join our webinar to learn everything you need to know about passkeys and how you can utilize passkey technology to protect your business. Read more passkey 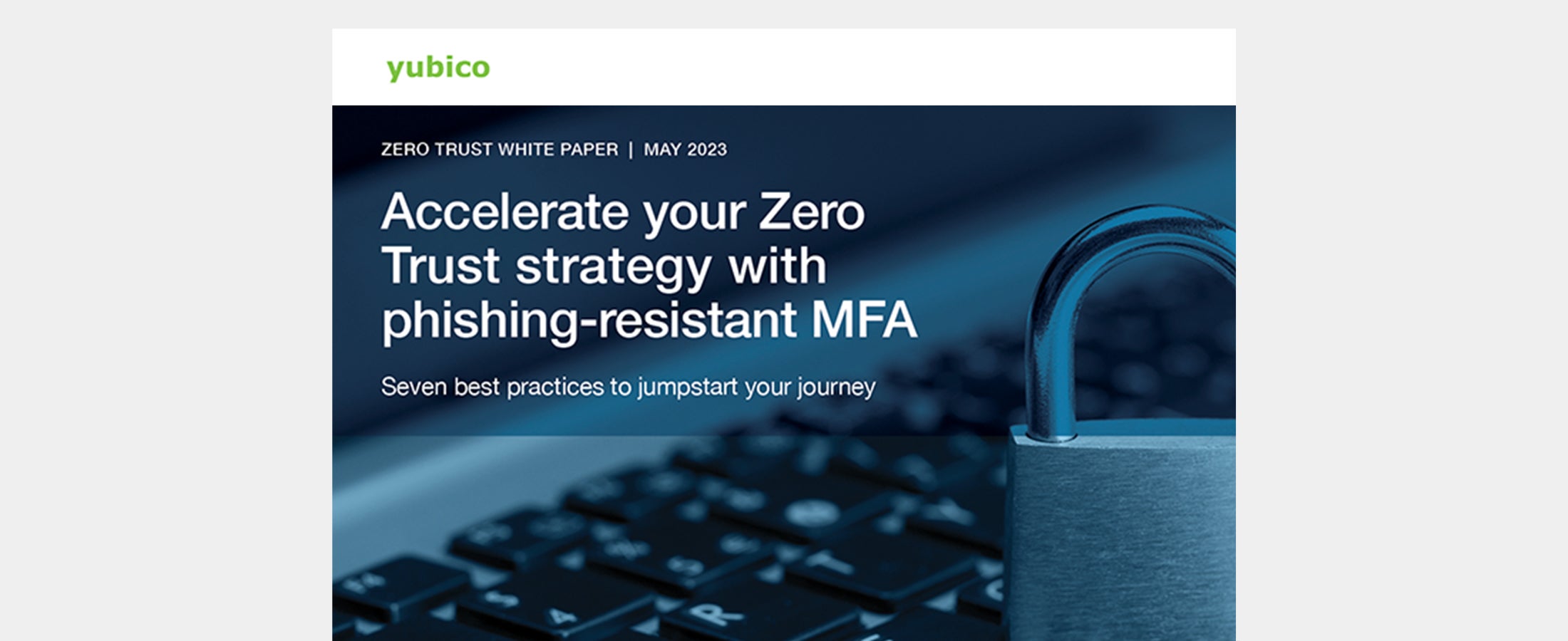
Accelerate Your Zero Trust Strategy w/ Strong Authentication Learn about strong authentication best practices that will put you on the right track to implementing your Zero Trust framework. Read more strong authentication zero trust 
The Total Economic Impact™ Of Yubico YubiKeys Read the Forrester Consulting study commissioned by Yubico and see how a composite organization reduced risk by 99.9%, saw a drop in password-related helpdesk tickets by 75%, and experienced a 203% 3-year ROI with YubiKeys. Read more modern authentication YubiKey 
Professional Services Deployment 360 Program Learn about Yubico’s Deployment 360 program which packages up all of the essential elements needed in getting your organization jump started on deploying YubiKeys. Read more deployment professional services YubiKey 
Professional Services Microsoft Entra ID CBA Implementation Learn how you can enlist dedicated technical engagement designed to help you implement YubiKeys and MFA with Microsoft Entra ID Hybrid using Certificate-Based Authentication (CBA). Read more CBA Microsoft Azure professional services 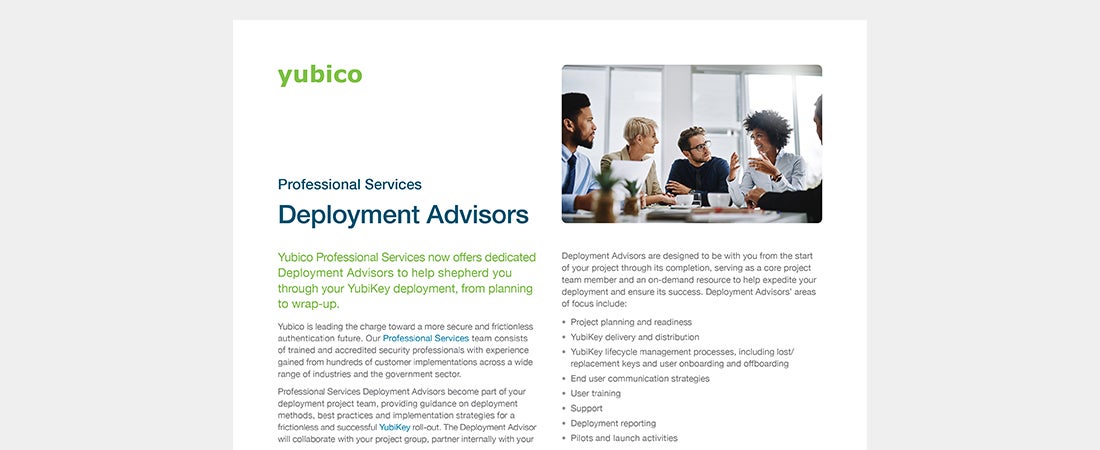
Professional Services Deployment Advisors Consultants Read the solution brief to learn more about how Yubico Professional Services now offers dedicated Deployment Advisors to help shepherd you through your YubiKey deployment, from planning to wrap-up. Read more deployment professional services 
Professional Services Microsoft Entra ID Quick Start Workshop Join us for a comprehensive review and technical tips on integrating YubiKeys with Microsoft Azure. In addition, the workshop includes best practices on operational deployment topics plus post-workshop technical consulting hours. Read more Microsoft Azure professional services 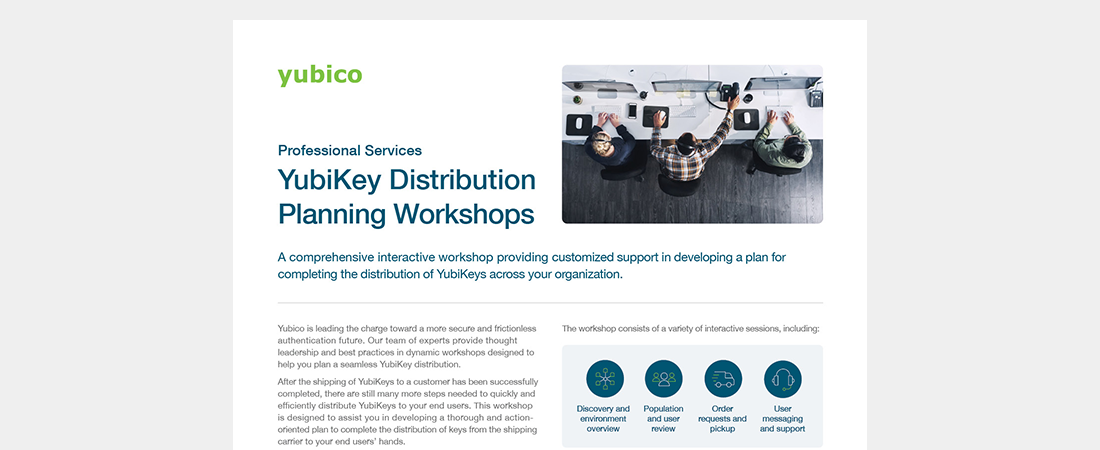
Professional Services YubiKey Distribution Planning Workshops Let us help you plan a comprehensive interactive workshop providing customized support in developing a plan for completing the distribution of YubiKeys across your organization. Read more professional services 
Considering Passkeys for your Enterprise? Avoid common pitfalls of synced passkeys Navigating the new passkey landscape? Read the ebook to learn about synced passkeys that are copyable versus device-bound passkeys, and how synced passkeys can create some failure points in the enterprise. Read more Enterprise passkey passwordless 
Need cyber insurance in 2023? Reduce risk and cost with phishing-resistant MFA Attend this webinar to learn how the cyber threat landscape is changing, why modern, phishing-resistant MFA has never been more critical to thwart account takeovers and ransomware attacks and how organizations can make raising the bar for security, simple, affordable and easy, and more easily qualify for cyber insurance. Read more account takeovers cyber insurance phishing-resistant MFA 
Move over passwords: Now is the time to move to modern, phishing-resistant MFA Only 46% of respondents protect their enterprise applications with MFA according to a new report. Learn how businesses can protect themselves against growing cyber threats. Read more cyberattack modernize mfa phishing-resistant MFA 
Not all MFA is created equal: Mobile MFA lures cybercriminals Legacy MFA such as mobile authentication is highly vulnerable to phishing and other forms of account takeovers. Learn about the pitfalls of mobile MFA and best practices to stop account takeovers. Read more mobile authentication phishing-resistant MFA 
Yubico and S&P Global Market Intelligence Research Report Yubico commissioned a research report conducted by S&P Global Market Intelligence, to survey senior professionals and executives in IT security, compliance, and cyber risk. Read more authentication MFA phishing-resistant MFA security 
Implications of outdated federal identity strategies Join Yubico and our esteemed panel for a roundtable discussion on challenges with current ICAM strategies and what’s needed for the makings of a modern identity strategy to enable digital modernization and cyber risk reduction. Read more federal government modern authentication 
Cybersecurity and our planet: The role of modern authentication Join Yubico and and our esteemed panel as we discuss the role of cybersecurity and how securing user access to critical infrastructure services with modern phishing-resistant authentication is integral in safeguarding the most sensitive information, processes, and systems that our society depends on. Read more cybersecurity Earth Day modern authentication 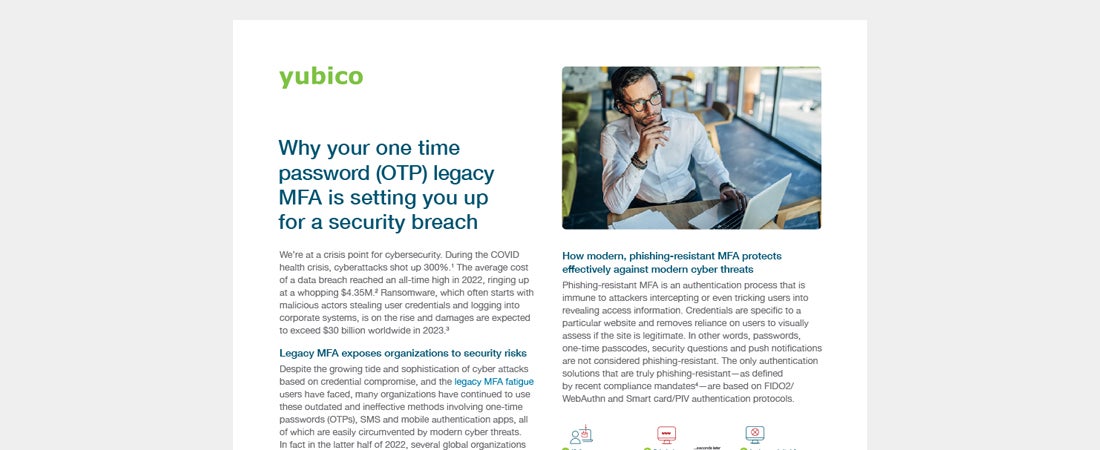
Why your one time OTP legacy MFA is setting you up for a security breach Learn how phishing-resistant MFA addresses the gaps that legacy MFA creates. Read more MFA OTP security 
Yubico and Versasec: The Winning Combination for Implementing Phishing-Resistant MFA Yubico and Versasec join forces to provide government agencies and enterprises the winning combination to implement phishing-resistant Multi Factor Authentication (MFA). Read more phishing-resistant MFA Yubico YubiKey 
Phishing-resistant MFA for Federal Government Learn how you can meet Zero Trust and phishing-resistant MFA per EO 14028 and OMB M-22-09 mandates with the DOD-approved and FIPS 140-2 validated YubiKey. Read more FIPS 140-2 phishing-resistant MFA YubiKey zero trust 
Best practices to secure call centers with phishing-resistant MFA Join Yubico for a roundtable discussion to learn phishing-resistant MFA and deployment best practices for call centers, gathered from numerous global deployments across critical industries such as financial services, healthcare, hospitality, retail, technology and others. Read more call center phishing-resistant MFA Yubico 
Accelerate your MFA and YubiKey deployment with Yubico Professional Services Watch this webinar to learn more about deployment tips and best practices, the value of Yubico Professional Services, and new offerings available. Read more MFA professional services YubiKey 
YubiKeys as a Service enable faster and wider rollouts of modern MFA in 2023 Watch this webinar to learn about how to procure YubiKeys as a Service with the new and expanded YubiEnterprise Subscription offering for greater business agility and predictability. Read more MFA modernize mfa YubiKey 
Securing call centers with phishing-resistant MFA Read the white paper to learn how to secure your call center environments against phishing and account takeovers using the phishing-resistant YubiKey Read more call center modern authentication phishing-resistant MFA 
State of Global Enterprise Authentication Survey: UK The Yubico State of Global Enterprise Authentication Survey asked employees, including in the UK, how modern enterprises embrace phishing-resistant MFA. Read more authentication Enterprise MFA Yubico 
State of Global Enterprise Authentication Survey: Singapore The Yubico State of Global Enterprise Authentication Survey asked employees, including in Singapore, how modern enterprises embrace phishing-resistant MFA. Read more authentication Enterprise MFA Yubico 
State of Global Enterprise Authentication Survey: including exclusive data from Australia & New Zealand The Yubico State of Global Enterprise Authentication Survey asked employees, including in Australia and New Zealand, how enterprises embrace phishing-resistant MFA. Read more authentication Enterprise MFA Yubico 
Phishing resistant MFA for state and local government Download the Yubico White Paper, Modernize authentication across state, local, tribal and territorial governments, to learn authentication best practices on how to achieve 100% MFA coverage, ensure zero account takeovers and meet your cyber insurance MFA requirements. Read more account takeovers MFA state and local government 
Infographic: Everything you need to know about passkeys Why are passkeys so phishing-resistant? What’s the difference between a synced passkey and a hardware passkey? Passkeys done right: Top 5 Takeaways Read more 
How to best secure your call center environments with against modern cyber threats Learn key considerations in choosing the right authentication solution for call centers. Read more call center modern cyber threats phishing-resistant MFA shared workstation 
Five ways Yubico can help you accelerate and scale phishing-resistant MFA in 2023 Learn about the 5 ways Yubico can help you accelerate and scale phishing-resistant MFA, starting now through 2023, to stop phishing, ransomware and other forms of account takeovers in their tracks. Read more enterprise security modern authentication phishing-resistant MFA 
Securing telecommunications against modern cyber threats Read the white paper to learn how phishing-resistant MFA protects telecommunication organizations from modern cyber threats and prevents account takeovers with an easy to use experience that removes roadblocks that legacy forms of authentication such as passwords, mobile-based MFA provides. Read more modern cyber threats phishing-resistant MFA Telecommunication 
State Global Enterprise Authentication Survey The Yubico State of Global Enterprise Authentication Survey asked 16,000 employees in 8 countries how modern enterprises are embracing phishing-resistant MFA. Read more authentication Enterprise MFA Yubico 
Widespread SMS phishing attack thwarted with Cloudflare Zero Trust and YubiKeys Learn how physical security keys played a crucial role in not allowing Cloudflare to be another victim in a widespread phishing attack. Read more phishing-resistant MFA strong MFA zero trust 
Devising Your Authentication Strategy: Passkey Implementations and Tradeoffs Join this webinar to learn the benefits and challenges of different forms of passkeys and what to look for in a passkey solution. Read more modern authentication passkey strong MFA 
Devising Your Enterprise Authentication Strategy with Passkey Read the ESG Showcase for guidance on the benefits and challenges of different forms of passkeys and discuss what to look for in a passkey solution. Read more authentication passkey passwordless 
Passkey Guidance for Web and Mobile Apps Learn what passkeys are, their benefits, deployment considerations, and how to implement WebAuthn passkey best practices. Read more mobile authentication passkey WebAuthn 
New tools to prevent phishing with Azure AD and YubiKeys Learn how these new features combined with a YubiKey should be an integral part of your Zero Trust strategy. Read more Azure AD CBA Microsoft zero trust 
The Rise of Low-Friction Access: Emerging Requirements and Solutions for Boosting Workforce Productivity and Security Assurance To provide businesses with actionable guidance to streamline authentication processes, Yubico commissioned a study with Enterprise Management Associates (EMA) to identify current requirements, challenges, and solutions in relation to mitigating access friction. Read more authentication modernize mfa strong MFA 
Protecting the healthcare ecosystem with phishing-resistant MFA Learn how the YubiKey helps healthcare organizations across insurance, providers, clinicians, biotech, and pharmaceuticals drive high security against modern cyber threats and high user productivity with the best user experience Read more healthcare passwordless phishing-resistant MFA YubiKey 
Achieve 100% MFA across state and local government Learn how state and local governments can ensure 100% MFA coverage to protect against modern cyber threats and meet cyber insurance requirements with the YubiKey. Read more cyber insurance phishing-resistant MFA state and local government strong authentication 
Meeting enhanced cyber insurance requirements with strong authentication Cyber risk is becoming an ever-greater business liability, with 40% of business leaders reporting cyber threats as the No. 1 business risk. As a result, organizations have increasingly turned to cyber insurance to help them recover from damage or minimize impact. Read this whitepaper to learn about the changing cyber threat and cyber insurance landscape, and the best way to position your organization to qualify more easily for cyber insurance. Read more cyber insurance cybersecurity phishing-resistant MFA strong authentication 
The importance of hybrid authentication in zero trust architectures Come learn key differences between PKI and FIDO, how to deploy FIDO within federal security policies, how to deploy FIDO within federal security policies, and more. Read more federal government FIDO OMB Memo-22-09 zero trust 
Okta EO Ping Identity | EO 14028 compliance – Yubico Learn how you can achieve federal compliance with YubiKeys and Okta. Read more 
Microsoft | Yubico Phishing-resistant MFA for Telecoms Learn how you can achieve modern security with Microsoft Azure AD and YubiKey to bolster cyber security. Read more Microsoft phishing-resistant MFA Telecoms 
Zero Trust with phishing-resistant MFA is mission-critical Join Yubico and Okta on September 22nd to learn how YubiKey, combined with Okta Adaptive MFA, work together to provide modern phishing-resistant MFA as well as a simplified user experience for the strongest levels of protection. Read more modern authentication Okta phishing-resistant MFA zero trust 
How PCI DSS 4.0 and CFPB Circular 2022-04 are re-shaping authentication across financial services The recent PCI DSS 4.0 and Consumer Financial Protection Circular 2022-24 setting guidelines for phishing-resistant multi-factor authentication (MFA) for user access to critical systems and customer-facing digital services have set the stage to change how financial services organizations should be thinking about their security investments not just for today but for future regulatory changes. Read more authentication compliance financial services 
YubiKey as a Service: YubiEnterprise Subscription Attend this webinar to learn about the latest in the cyberthreat landscape, the critical need for phishing-resistant MFA and how organizations can introduce agility, flexibility and peace of mind with a hardware authentication as a service model. Read more phishing-resistant MFA YubiEnterprise Subscription 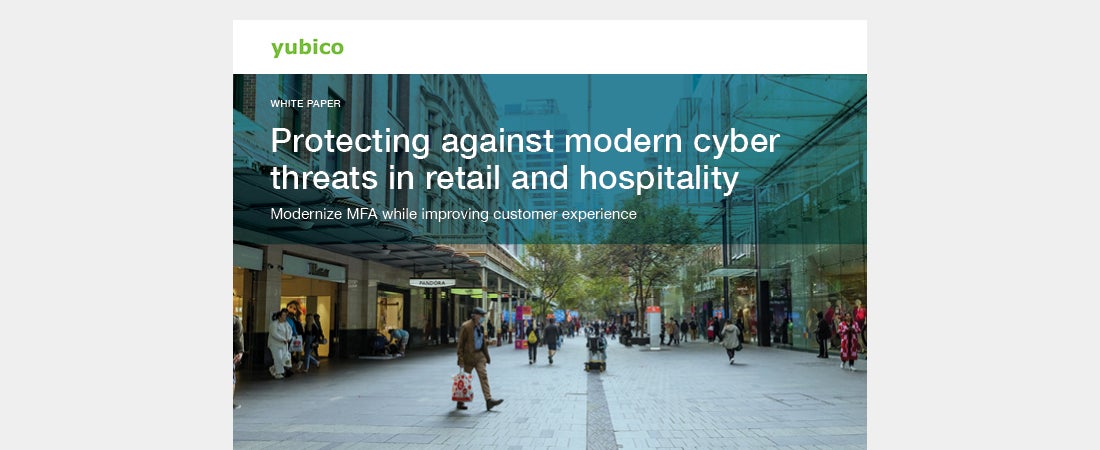
Protecting retail and hospitality against cyber threats Learn how modernizing authentication can secure shared devices, protect sensitive data, and prevent account takeovers while enhancing customer experience. Read more cybersecurity modern authentication phishing-resistant MFA retail and hospitality YubiKey 
Phishing-Resistant MFA fact vs fiction Phishing-resistant multi-factor authentication (MFA) is a critical call to action per the White House Executive Order 14028 on Protecting the nation’s cybersecurity, and Office of Management and Budget Memo M-22-09 Read more authentication MFA phishing-resistant MFA 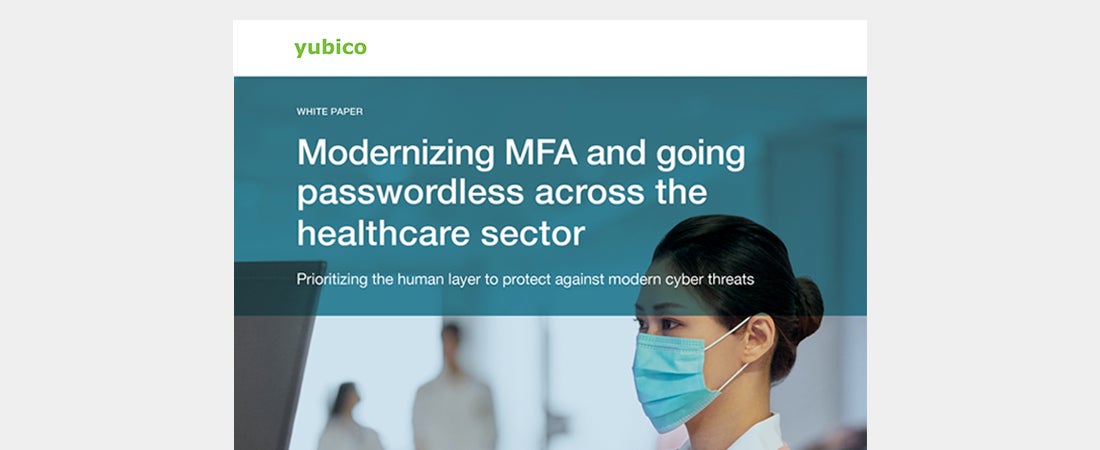
Modernizing MFA and going passwordless in healthcare – Yubico Read the white paper to learn how to protect against phishing and ransomware across the healthcare sector using YubiKeys for phishing-resistant MFA and passwordless authentication Read more healthcare modern authentication passwordless 
The Total Economic Impact Of Yubico YubiKeys Attend this webinar to learn about the latest in: – The evolving cyberthreat and compliance landscape – How to procure YubiKeys as a Service for greater business agility and predictability – The findings from the Forrester Total Economic Impact (TEI) report that showcases YubiKeys delivering 203% Return on Investment (ROI) Read more enterprise security YubiEnterprise YubiEnterprise Delivery YubiEnterprise Subscription 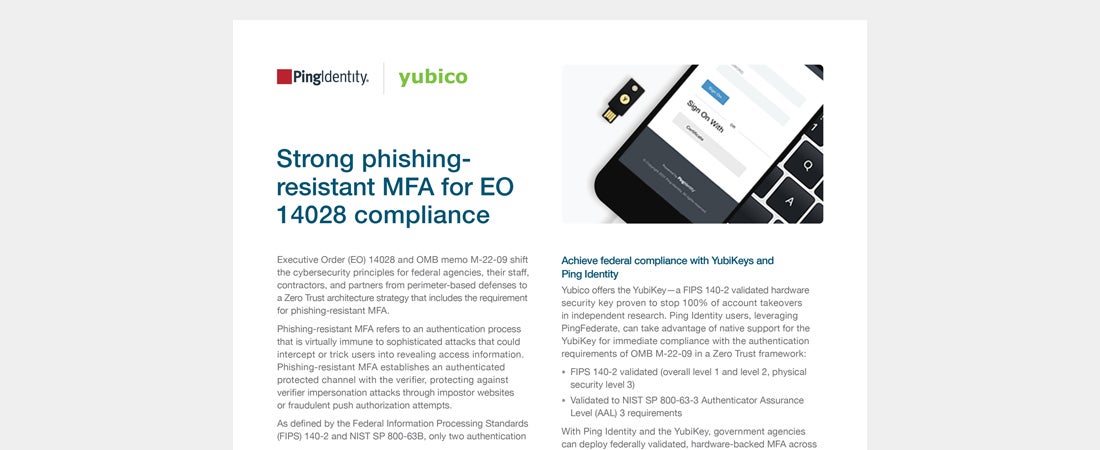
Ping Identity | EO 14028 compliance – Yubico Learn how YubiKey and Ping Identity together offer phishing-resistant MFA to protect against account takeovers within government agencies Read more compliance Executive Order phishing-resistant MFA Ping Identity 
WebAuthn Explained: Advancing Authentication with Hardware Security Keys & Establishing a Root of Trust – Yubico Insights Establishing a “root of trust” is the mechanism in which a user recovers an account or establishes their identity on a new device Read more root of trust WebAuthn 
One northeastern U.S. state secured elections using MFA Election security is an increasing concern. One Northeastern state adopted mfa using hardware security keys to protect its voters Read more elections and political campaigns government MFA phishing-resistant MFA state and local government 
Protecting the supply chain with modern security Learn how Yubico solutions such as the YubiKey and YubiHSM 2 can help you secure your software supply chain, ensure IP security and product integrity, and provide highest-assurance security for third party access to critical systems and data. Read more modern authentication phishing-resistant MFA supply chain 
A cybersecurity roadmap for securing shared workstations Learn critical authentication requirements for shared workstations and devices, and best practices to ensure your organization stays protected against modern threats. Read more cybersecurity modern authentication shared workstation 
Best practices for securing mobile-restricted environments with MFA Attend this webinar to learn the key security best practices to secure mobile-restricted environments. Read more mobile-restricted modern authentication phishing-resistant MFA 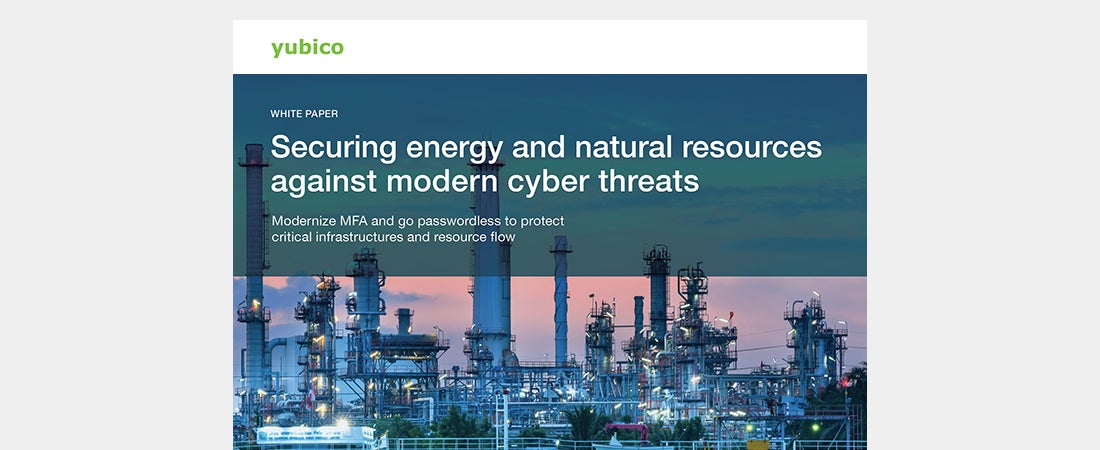
Securing energy and natural resources against modern cyber threats Learn the critical need for phishing-resistant multi-factor authentication to safeguard this critical infrastructure and authentication best practices to close the critical threat gap that emerges from legacy authentication. Read more energy and natural resources modern authentication oil and gas phishing-resistant MFA 
How governments and higher education can achieve 100% MFA Learn how state and local governments and higher education can drive 100 percent MFA coverage to protect against phishing and account takeovers Read more education phishing-resistant MFA state and local government 
Modernizing authentication across energy and natural resource organizations Learn best practices to modernize cybersecurity across your critical IT and OT environments with Yubico solutions, to stop modern cyber threats and drive cyber insurance hygiene. Read more cybersecurity energy and natural resources modern authentication 
Strong phishing resistant MFA for EO compliance Learn how you can achieve federal compliance with YubiKeys and Microsoft Read more Executive Order Microsoft phishing-resistant MFA 
Phishing-resistant MFA for Telecoms Learn how the YubiKey can bolster existing security approaches by providing a future-proof layer of protection to safeguard people, technology, and data. Read more modern authentication phishing-resistant MFA Telecommunication Telecoms 
Passkeys and the future of modern authentication: Q&A with Yubico’s CTO Learn the role passkeys play in modern authentication and some of the most common misconceptions. Read more modern authentication passkey phishing-resistant MFA 
AWS Marketplace Yubico Partner Brief Learn how YubiKeys work to secure your AWS services and resources. Read more AWS phishing-resistant MFA 
Graduating from legacy MFA to modern authentication Download the Yubico White Paper, Graduating from legacy MFA to modern authentication: The critical need for increased security across education, to learn authentication best practices in modernizing authentication to stop modern day cyber threats. Read more authentication education MFA 
Demystifying phishing-resistant MFA: Fact versus fiction Join to understand the different types of MFA in the market and whether they are truly phishing-resistant or not. Read more modern authentication phishing-resistant MFA 
Protecting the supply chain with highest-assurance security Download the Yubico White Paper, Protecting the supply chain with highest-assurance security: Go passwordless, ensure product integrity, and protect the software supply chain, to learn authentication best practices in securing supply chain integrity. Read more MFA supply chain 
Modernizing authentication across education Learn how you can modernize cybersecurity across the education sector with the easy-to-use, affordable YubiKey, to stop modern threats and drive cyber insurance hygiene. Read more education modern authentication phishing-resistant MFA 
Smart Cards Simplified – Private sector Smartcards provide strong security but they can be complex for to adopt both for the organization and the end users alike. Users may even have to carry smart card readers and additional peripherals to use the solution. Read this solution to understand how a modern and simplified smart card approach can either replace your legacy smart card approach, or get you on the road to raising the security bar, by providing strong phishing defense in the modern cyber threat landscape. All while being very well suited for your hybrid or remote workforce, with users working across a range of modern desktops, tablets and smart phones. Read more smart card state and local government strong authentication 
The future of Federal cybersecurity is here Smart cards, while they provide strong security, can be complex for to adopt both for the organization and the end users alike. Users may even have to carry smart card readers and additional peripherals to use the solution. Read this solution to understand how a modern and simplified smart card approach can augment your existing smart card strategy and provide strong phishing defense in the modern cyber threat landscape. All while being very well suited for your hybrid or remote workforce, with users working across a range of modern desktops, tablets and smart phones. Read more cybersecurity Executive Order smart card 
New Cyber Insurance Requirements: Critical need for Phishing-Resistant MFA Come learn new cyber insurance requirements and ways to adopt true phishing-resistant MFA that keeps your business and users protected. Read more cyber insurance modern authentication phishing-resistant MFA 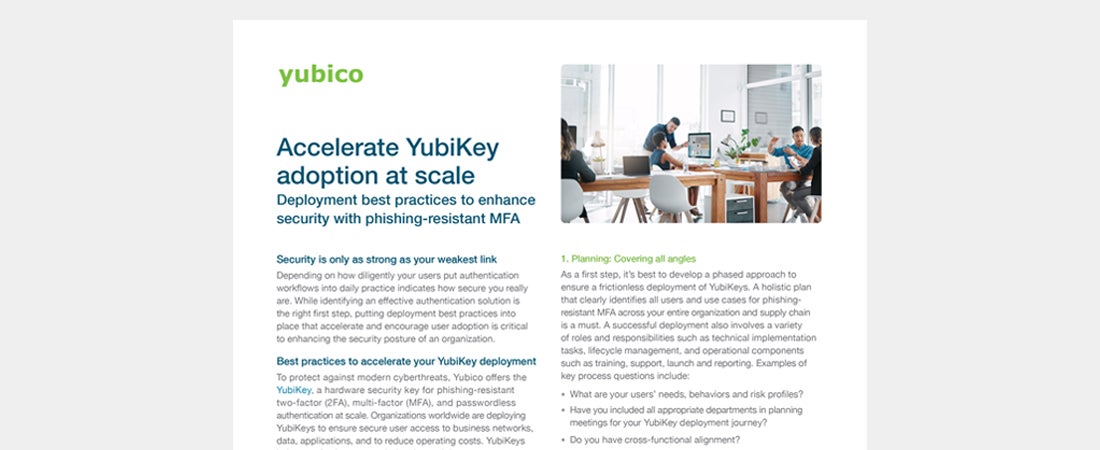
Accelerate YubiKey adoption at scale Learn deployment best practices to enhance your security posture with phishing-resistant MFA Read more authentication phishing-resistant MFA security 
Securing federal government with phishing-resistant MFA Join to hear from government executives on how they are planning for OMB M-22-09, to ensure the highest protection for mobile, cloud platforms and systems that don’t support PIV and CAC Read more Executive Order federal government phishing-resistant MFA
