What is Strong Authentication
Strong authentication is a way of safely and reliably confirming user identity. Multi-factor authentication (MFA) is one of the best options to establish trust with users, but actual strong authentication goes beyond MFA or two-factor authentication (2FA).
Strong Authentication Definition
Strong authentication confirms user identity reliably and safely, never solely based on shared secrets/symmetric keys such as passwords, codes, and recovery questions. Strong authentication assumes credential phishing and impersonation attacks are inevitable and robustly repels them. Although multi-factor authentication (MFA) remains among the best ways to establish who trusted users are, actual strong authentication goes beyond either two-factor authentication (2FA) or MFA.
When implementing MFA, at a minimum, follow the National Institute for Standards and Technology (NIST) Assurance Level-2 for admin functions. This means using two factors: something you know, such as a code or password, and something you have, such as a push notification or a one-time passcode (OTP) generated by a registered device.
Where possible, increase to NIST Assurance Level-3 for most critical assets. This means 2FA with something you know such as a password, along with a hardware-based cryptographic token, such as a FIDO key or smart card.
The nature of the factors is critical, because actual strong authentication:
- Never relies solely on shared secrets/symmetric keys at any point. This includes passwords, codes, and recovery questions.
- Always robustly repels credential phishing and impersonation. While wary users are always welcome, strong authentication assumes these attacks are inevitable and prevents them.
Strong authentication should also be scalable and easy to use. In a modern world, there is no meaningful strong authentication or zero trust security if there is no easy online translation for everyday users.
Strong authentication builds trust in a user identity. When the user identity and infrastructure itself is more trustworthy, a social engineering attack is less likely.
What Is Strong Authentication?
There is a great deal of confusion surrounding strong authentication (SA). Some sources define strong authentication as any authentication method for a user or device that is inherently secure enough to protect the system from cyberattacks. Others define strong authentication as any form of authentication which achieves verification without password transmission.
However, neither of these definitions is specific enough. To qualify as strong authentication, a system must:
- Not rely solely on shared secrets/symmetric keys at any point. This includes passwords, codes, and recovery questions.
- Robustly repel credential phishing and impersonation. No matter how much user education about phishing or social engineering takes place—some attacks will succeed. Strong authentication assumes lapses are inevitable and prevents them.
In practice, for strong authentication to be effective, it must work at scale on a variety of devices, environments and in different situations. The better the user experience, the easier it is to deploy across and to secure the enterprise — unlike complex point solutions that only protect a niche set of users.
Shared Secrets and Symmetric Keys
To define strong authentication, let’s begin with the concept of access control: the ability to do something, such as logging onto a computer, opening a restricted document, or using an application.
Access control often starts with a shared secret. Both parties know the secret which is used as the means of authentication. The user knows the secret information and shares it with the other party to gain access. However, all it takes is for one party to reveal the information either deliberately or by mistake and the model is broken. Anyone else who knows the shared secret could gain access.
The oldest method of authentication is the shared secret model that goes all the way back to ancient Egyptian times, in the form of the password. Looking ahead as the internet was born, the shared secret became the foundation for sharing information and granting access to people across the globe. In the very early days of the internet, passwords were used at the Massachusetts Institute of Technology to grant access to other researchers in the same facility. Now they are used for all manner of services from banking to entertainment.
However, the shortcomings inherent to using the shared secret model online soon became obvious. There was a need to enhance security. Enter the additional verification factor. This second factor of verification typically comprises something the user knows (the shared secret), plus something the user has (a token), and/or something the user is (a biometric such as a fingerprint).
Passwords and recovery questions—these are both shared secrets. Most platforms and systems are built on them. Unfortunately, with the proliferation of social networks, that secret information typically isn’t very secret anymore and social engineering attacks are rampant. For example, when Facebook users broadcast which city they were born in within a profile and link to a parent’s profile, they are unwittingly providing answers to common shared secret prompts.
As the industry attempts to improve, other forms of authentication come into play. Authentication methods, such as SMS or email, still rely on shared secret models.
For example, two-step verification via SMS is widely adopted, but many SMS codes are merely generated on the server side and then passed along to the user via text. This is just one factor and simply layers two shared secrets on top of each other in sequence. This leaves the system vulnerable to SIM swapping; if an attacker has the user’s phone number, they can get the code.
So what if we could encrypt the password while it’s in transmission and decrypt it on arrival? Public-key cryptography, also called asymmetric cryptography, uses public and private key pairs. The public keys may be widely disseminated, but the private keys are known only to their owners. Users generate keys with cryptographic algorithms based on one-way mathematical functions. This allows users to distribute the public key openly while still keeping the private key private, and maintaining effective security.
In a public-key cryptography system, any user can encrypt a message with the public key of the recipient, but only the private key of that recipient can decrypt that message. Public-key cryptography enables strong authentication because a sender can create a short digital signature on a message by combining it with a private key. Anyone can then combine that digital signature on the same message with the sender’s corresponding public key to validate the signature, or verify whether the owner of the corresponding private key made it.
Credential Phishing and Impersonation
The symmetric key issue matters because even in an environment that is hypothetically completely secure, the shared secret model is inherently flawed. The problem with the shared secret model is that the secret is shared. Users are giving away the thing that they are using to prove identity. For example, even information stored on a secured server and protected by passwords that are never intentionally revealed is vulnerable to credential phishing.
Phishing attacks are a type of social engineering, a way of using deception via electronic communications — like email or instant messaging on a smartphone — to steal information such as usernames and passwords, money, or access to systems.
Although phishing attacks are not new, they have become far more sophisticated, and will often seem indistinguishable from normal everyday interactions. Email exchanges or phone calls will perhaps appear to come from an employee in your organization who has already been compromised, but will seem to include verifying details such as start dates, employee numbers, and telephone numbers. The experience can be so smooth that the victim doesn’t even know that they were phished.
Sadly, few types of multi-factor authentication are up to the task of preventing modern social engineering and phishing attacks. This is in large part because most of the “secret” information that platforms require users to know and confirm are not actually secrets unless the users are extremely careful all of the time.
Everything that a user can legitimately have access to can be spoofed. In the past, significant work was required to create lookalike templates for various websites. Today replicating a website to a standard that convinces users that it is authentic is fairly simple, rendering phishing attacks fairly easy. All you need is a skilled person to engage in social engineering and a web developer with basic tools and knowledge.
As a result these attacks are common and so sophisticated they can target high-level users, even privileged administrators directly. The organization must prevent every one of the attacks, whereas hackers need only be successful once. This asymmetry combined with the ease of executing the attacks, means that organizations must assume they will be compromised at some point. This is why strong authentication is increasingly important since it prevents the success of such impersonations.
This is borne out by recent headline news, such as the 2020 Twitter hack. This example alone proves that even an advanced shared secret model such as the security system inside a sophisticated company such as Twitter does not stand a chance against sustained phishing attacks.
Scalability and Ease of Use
A strong authentication system must be scalable to all users, including customers, and easy to use (or it will either be circumvented or an easier application used in its place). Core to scalability is using open security protocols so products can be supported by multiple vendors. A single-vendor, proprietary system is arguably not scalable on a global basis, and carries its own risk of abuse and exploitation.
Technically, the ability to eliminate the shared secret and symmetric key alongside robust resistance to phishing exists today. The Department of Defense, for example, can achieve these two goals using smart cards paired with PIN codes right now within their own system.
However, smart cards are not a scalable approach for most users and situations. It takes massive, complex infrastructure to make a smart card system function — which works for government agencies and large enterprises. Authentication hardware such as a smart card reader has not become a standard feature in personal computing. Even an enterprise-level business that wants to deploy a smart card solution will find that it is complex and requires planning. YubiKeys don’t require a card reader, reducing this complexity.
A proprietary management system is also not scalable if users are expected to install or download software or plugins to their device or server. Even if the software is automatically downloaded, it can break or fail to install properly, triggering help desk tickets. This is poor user experience and adds complexity and cost to the deployment.
In contrast, systems, software, and tools based on the open FIDO authentication standards avoid symmetric keys and include built-in phishing protections. Companies such as Apple and Microsoft already support FIDO authentication—so native support and usability out of the box are becoming a reality.

The FIDO Alliance has created a comprehensive ecosystem of open industry standards that enable strong authentication and have now been broadly adopted by trusted technology providers and brands. These standards leverage public key cryptography to strengthen privacy and security while improving usability by preserving on-device user verification.
Today hundreds of billions of FIDO-compliant accounts and millions of devices worldwide comprise the FIDO ecosystem. This ecosystem provides infrastructure that truly scales and has meaningful native support. This means that authentication is natively built into the browser or operating system, without the requirement to download additional software since that creates a risk of malware.
Further, only the destination site that originally registered the FIDO credential (the private key) can match it to its public key for authentication. This eliminates the risk of a phishing attack where the credentials are stolen since only the correct site will match the private and public keys.
Ease of use is equally important to strong authentication. Strong authentication demands technology that offers a seamless experience, yet still requires some element of user intent to access.
For example, consider the requirement to type codes or passwords into a screen. This is a poor user experience, although it does confirm user intent to access (if not identity).
In contrast, a single gesture operation such as a touch, tap, or blink attaches a human action to user intent. Although some advocates argue that strong authentication should be so seamless that user intent is bypassed altogether, this is not the preferred position since it could lead to false authentication.
Strong authentication should retain an element of user intent, because so much is already automated and there are many bad actors—both intentional and unintentional—to contend with. Balancing this requirement with ease of use means that users should have options that offer least friction possible to provide their intent.
Strong Authentication and Mobile Devices as Authenticators

A mobile device, such as a smartphone, can be used as an authenticator. A smartphone can function as a platform authenticator, which itself engages in some authentication processing and solves some important phishing challenges.
However, platform authenticators cannot be used to provide FIDO authentication on other devices. And users change smartphones regularly, causing people to spend time re-registering new devices. This makes for a poor user experience.
For businesses, despite mobile device management tools, there is really no way to prevent a smartphone being compromised. Using a smartphone involves downloading regularly meaning there will be both good and bad apps on the device. The phone will receive emails, SMS, downloads, documents, and other items that pollute the local environment. This contaminates the device and increases the attack surface so the device can be compromised. If the device is compromised and used as an authenticator – it provides a trusted and properly verified tunnel into the organization’s systems.
In practice, for some functions, a smartphone may be an appropriate authenticator—depending on the risk, goals, and intended user outcome. To check a bank balance, for example, a smartphone running on FIDO may be an acceptable authenticator – it’s a low risk activity that does not require strong authentication. To transfer a large sum of money, however, it is better to require an additional unique authentication device.
An additional consideration is the ability to authenticate should the smartphone or other mobile device become destroyed, lost, or inoperable. The backup method should be a replacement authentication device—not a recovery question that is vulnerable. This is particularly important since attackers will select an easier attack vector every time, and a weak back door that relies on a shared secret is just that.
What Is Strong Customer Authentication?
The EU Revised Directive on Payment Services (PSD2) requires strong customer authentication (SCA) of payment service providers within the European Economic Area. Sometimes called strong consumer authentication, SCA is designed to increase the security of electronic payments, the requirement ensures that service providers perform electronic payments with multi-factor authentication—subject to additional requirements.
Article 97(1) of the PSD2 provides a strong customer authentication definition and requires that payment service providers use strong customer authentication solutions where payers:
- access payment accounts online;
- initiate electronic payment transactions;
- carry out any actions through remote channels which are vulnerable to abuses such as phishing and payment fraud.
Article 4(30) defines strong customer authentication as a form of multi-factor authentication itself: two or more factors categorized as something only the user has, something only the user knows, or something the user is. According to Article 4(30), the factors must be independent to satisfy the strong customer authentication requirements, so that the breach of one factor cannot compromise the reliability of the other factors. The system must also be designed to protect authentication data confidentiality, including from phishing.
Physical card transactions using chip and PIN codes usually already boast fairly strong inherent customer authentication for in-person transactions in the EU, but this is not typically true for online transactions, and contactless card payments frequently lack a second authentication factor.
Strong customer authentication SCA requirements have been in effect since September 2019, but several EEA countries announced temporarily delayed or phased implementation with the approval of the European Banking Authority. Now, a full enforcement date of December 31, 2020 has been set.
Strong customer authentication applies to online payments in Europe that are customer-initiated. This means all bank transfers and most card payments require SCA. In contrast, recurring direct debits and in-person card payments are not impacted by the new regulation. The former are considered merchant-initiated and therefore don’t demand strong authentication, while the latter already enjoy the protections that come with in person contact.
How Does Strong Authentication Work?
As described above, there are various ways to achieve strong authentication. Each potential tool, system, or process should be subject to a three-pronged analysis:
- Does it rely solely on symmetric keys or shared secrets at any point, including in recovery?
- Does it offer robust resistance to phishing and other attacks?
- Is it scalable and easy to use?
Given these criteria, we can review which approaches classify as strong authentication and which fall short:
Email or SMS One-time Passwords (OTPs)
To use a one-time password (OTP), also called a passcode, via e-mail or SMS as a second factor (2FA), the user requests the OTP which is then sent to a registered cell phone or email address. The user must then enter in both their normal and the second one-time passwords to authenticate and gain access.
This step adds time and inconvenience for users. It is also vulnerable to phishing.
Email and SMS Two-step verification (2SV) does not classify as Strong Authentication since it fails to secure the user against phishing attacks. In fact, it is often the target of attack itself. It is also based on a shared secret which is insecure and technically, the user is not in possession of the email address or phone number. The email provider and phone company “own” them and can switch them without the user knowing.

Out-of-band
Out-of-band authentication involves users verifying their knowledge factor (username and password or code) for the provider bank via a telephone call over a registered phone number before they are allowed to login. In other words, it is a live telephone call version of the similar e-mail or SMS OTP version.
Out-of-band authentication does not classify as Strong Authentication since it fails to secure the user against phishing attacks. It is also based on a shared secret which is insecure.
Biometrics
The use of biometrics as a second factor works by verifying physical characteristics such as a cornea or fingerprint using a dedicated hardware device. This need for a dedicated hardware device such as a fingerprint reader can add significant costs to implementation. If compromised, a biometric authentication system is rendered useless since the user cannot change their physical characteristics.
Biometric authentication systems do not always classify as Strong Authentication. If the biometrics database is centralized, the transmission of biometric data for matching is a form of shared secret solution. There is a risk that the data will be intercepted and used to falsely authenticate an imposter.
In the right context, localized biometrics can enhance strong authentication, but in and of themselves, biometrics cannot be considered strong authentication. A centralized database of biometric identifiers used as a one-to-many match (such as a database used for facial recognition) fails the symmetric key issue. However, a localized, one-to-one match which requires no networked database adds an additional layer of validation. From a FIDO perspective, the biometric data is used to unlock the device so the asymmetric cryptographic process can be performed. Thus, two-factors are involved (the authenticator and the biometric).
Software Authentication Apps
A specialized authentication app or single sign on app is developed solely for authentication. However, this approach asks the user for authentication on a registered device running custom software rather than providing them with a standards-based OTP. The software sends tokens to the third party authentication platform or service for verification directly, eliminating user-entered OTP.
Software authentication apps do not classify as Strong Authentication since they fail the ease of use. They require the user to install software which can be problematic and can introduce vulnerabilities. They are typically proprietary rather than open standards-based, and still use a symmetric key authentication approach which is inherently weak.
Token-based authentication with One Time Passwords (OTP)
Some hardware devices can generate OTP tokens to serve as a constantly-changing stream of second factors that must accompany the first knowledge-based factor. OTP tokens demand that the user keep the hardware device that generates the tokens with them to authenticate.
The tokens themselves must be accepted by many systems to make this device-based authentication method a scalable solution. However, once this is achieved this option benefits from the native support of platforms and services, unlike the authentication app solution. Hardware tokens don’t provide phishing resistant capabilities.
Smartphone as Authentication Factor/Peripheral Device Recognition

Software establishes a device such as a smartphone or computer itself as a second authentication factor to achieve second factor peripheral device recognition. It does this by placing a cryptographic device marker onto the device after installing a small authentication software plug-in. This can also be achieved on an existing device such as a smartphone memory card, a USB flash drive, or another mobile device, and in this case the mobile device with the marker must be connected to the computer when the user authenticates at certain sites.
The marker serves as a second factor which can then be verified during the authentication process. The process as a whole verifies two factors: something you know such as a password and something you have, the marker on the consumer device. This is simple and easy, because you only need to enter the knowledge factor, your code or password; the device marker is always there.
Peripheral device recognition is an alternative to the OTP token that doesn’t require the user to carry an additional device, but it does not provide hardware-backed security. In this model, software is used to create cryptographic private keys. They are not minted in a factory once and stored in a hardware device.
Hardware device authentication, such as smartphone authentication does not classify as Strong Authentication since it fails the easy of use / scalability test. The requirement to download software creates usability issues and vulnerabilities.
Smartcard authentication
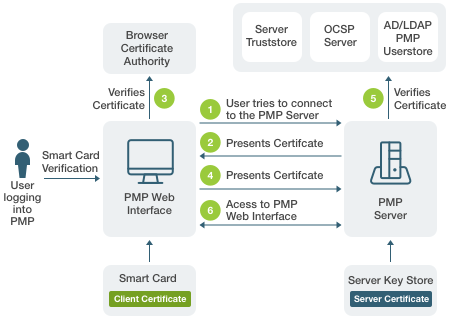
The use of smart cards as a physical authenticator when combined with a knowledge-based token such as a PIN can provide robust authentication. They can prevent phishing since the smart card cannot be replicated – it would need to be physically stolen. Smart cards, such as credit cards in the EU are used to authenticate users for high value transactions, however that use case does not translate well online. This is because the technology is not designed well for the internet, and smart cards are not widely adopted for online use due to implementation complexities.
Smart card authentication does classify as Strong Authentication, but is impractical for internet authentication due to complexity and ease of use limitations.
Multi-protocol Hardware Authentication Keys

Physical authentication keys secure the authentication process with asymmetric encryption algorithms and ensure the private key never exits the device. Examples of this strong authentication method include USBs that connect and authenticate when prompted. These typically adhere to FIDO Alliance standards.
Multi-protocol hardware authentication keys do classify as Strong Authentication since they meet the criteria of avoiding a symmetric key, prevent phishing and are scalable/easy to use being based on open standards.
Two-Step Verification vs Two-Factor Authentication vs Strong Authentication
As a reminder, there are three possible types of authentication factors:
- Something you have (such as a smart device or hardware token)
- Something you know (such as a piece of personal information that has not been shared)
- Something you are (such as biometrics)
Two-step verification is not the same as two-factor authentication although the terms are often incorrectly interchanged. As the name suggests, two-step verification has two stages to the authentication process. Typically this involves entering a username and password, then receiving an email or SMS with a one-time password (OTP) to enter into the service. This is an improvement in terms of security over a basic username/password since it requires access to the phone or email to receive the OTP.
However 2SV should not be considered secure, fails to meet the standard for strong authentication, and can in fact give a false sense of safety. Two-step verification is insecure since the OTP is easily intercepted, especially if the victim’s email account has already been hacked. This gives easy access to other services as the hacker traverses the victim’s accounts.
Typically, two-step verification only uses one factor since it relies on something you know (the password and OTP code). It does not require something you are or something you have (2SV is usually not multi-factor authentication). Being emailed or sent the code via text is the cause of confusion between 2SV and 2FA — 2SV has two-steps, but uses only one factor.
Two-factor authentication (2FA) typically requires the user not just to know the username/password but also to either have an item (the security key or token) and/or to biometrically verify their identity (e.g. with a fingerprint). Any combination of two of the three factors — what you know, what you have, and what you are — is considered two-factor authentication.
How strong is two-factor authentication? The nature of the factors is critical. Two or more factors which are all the same type are still vulnerable to phishing and should not be considered strong authentication. Use of more than one code or password is simply more than one version of something you know. Layering on the same version of security and vulnerability is not strong authentication.
As described above many of the second factors (beyond the username/password) are inherently insecure since they can be hacked or phished from the user. Most 2FA approaches are stronger than just a password but will not protect the user or the organization from a concerted attack. As with 2SV, 2FA can give organizations a false sense of security, when in fact they are still open to common attack techniques. This is problematic since sophisticated hackers will exploit this oversight and can gain access to valuable information or seek gain through techniques such as ransomware. Only strong authentication, such as a multi-protocol hardware authentication key and smart cards, can prevent this attack vector.
Biometrics has an important role in the authentication triad. However, biometrics for on-device verification are far different than online versions of biometrics for authentication.
A system or device only provides strong authentication if the technology behind it is not reliant on a phishable symmetric key. However, many biometric systems capture user biometrics, send them in templates across the internet, and verify identity by doing template matching on their database or server. In other words, the biometric data capture is followed by a symmetric key or shared secret handshake.
An authenticator that engages in on-device verification is a robust option. On-device biometrics mean that any capture of biometric data must happen locally, and attacks cannot be scaled. Biometric data that follows FIDO protocols is safe from phishing and the symmetric key problem.
The overriding issue to consider when evaluating an authentication system for strong vs multi factor authentication is whether it meets the three prongs for SA:
- No reliance on symmetric keys or shared secrets
- Robust resistance to phishing
- Scalable and easy to use
It is a good idea to assess each factor as well to check for less obvious reliance on symmetric keys or shared secrets. Although it is a common misperception, MFA is not inherently more secure than two-step verification. Multi-factor authentication is only as secure as its various factors and how they function together.
Although there are no commonly accepted metrics or algorithms to determine the comparative strengths of one authentication method compared to another, it is possible to estimate how effective a particular cryptographic key or password is likely to be. This is the basis for those “strong” or “weak” assessments of your new password in many systems, for example.
According to NIST in Publication 800-63, there are three authentication assurance levels:
- AAL1 is single factor authentication. This applies to all SFA, including that on a cryptographic hardware device.
- AAL2 is any multi-factor authentication (MFA) with both possession and knowledge factors. At this level, the possession factor can be satisfied by a software solution such as a smartphone app.
- AAL3 is advanced multi-factor authentication. This MFA demands both possession and knowledge factors, and in addition, the possession factor can only be proved using cryptographic hardware authenticators.
NIST also distinguishes between cryptographic and non-cryptographic protocols, and between hardware authenticators and software authenticators.
Strong Authentication Benefits
There are many benefits to strong authentication, falling in three basic areas: security, user experience, and standardization and regulatory compliance.
Security
Strong authentication improves security because it:
- Strengthens authentication mechanisms in workstations and applications, particularly those that are most sensitive
- Adapts authentication level to user context
- Eliminates insecure passwords
- Controls the outsourcing of services and the openness of IS
User Experience
Strong authentication radically improves user experience, in that it:
- Streamlines management and recovery of usernames and passwords
- Implements one ergonomic solution for authentication across all platforms and applications
- Integrates localized biometrics standards, including those for FIDO2, Apple TouchID/FaceID, and Microsoft Windows Hello
Standardization and Regulatory Compliance
Strong authentication ensures peace of mind from a compliance perspective:
- Pool and standardize authorization and authentication infrastructures
- Fulfill regulatory requirements under the PSD2, GDPR, and other applicable laws
Common Use Cases for Strong Authentication
It is easy to argue that there is no good reason not to use strong authentication, because it is accessible, easy to use, secure, and protective. However, there are several common use cases for strong authentication that establish its importance.
Remote Work

As enterprises move toward digital transformation, they accommodate more remote work. Technological advancements enable remote work, but businesses and IT departments with employees who work from anywhere also face a new set of challenges. Unmanaged personal mobile devices, unsecured WiFi networks, and phishing scams all make securely managing geographically dispersed teams difficult and stealing user credentials easy.
Remote work is not a new idea, but it is becoming more prevalent, and numbers of remote workers are growing even higher thanks to recent events. It is imperative for organizations to secure remote workers with systems and processes that do not hinder productivity. As hackers continue to capitalize on business uncertainty with targeted phishing attacks, any business contingency plan must include a plan for protecting the remote workforce.
Consumer Identity Providers (IdP)
The consumer identity provider IdP use case includes the government service provider or online bank, for example. These IdPs must supply identity data to relying parties (RPs). They therefore store sensitive data verified through know-your-customer (KYC) processes that contains user attributes. Only approved RPs should be able to access the identities in the IdPs system assured to standard levels.
Health Data Sharing
Healthcare is among the industries targeted most frequently by cyber criminals, with attacks including business email compromise (BEC), data theft, and ransomware, among others. In fact, one-third of data breaches in the United States occur against hospitals. Any organization that manages a health data sharing protocol requires strong authentication.
Does Yubico Offer Strong Authentication?
Yubico offers one of the only true strong authentication solutions on the market. Multi-protocol YubiKeys, also leveraging the FIDO standard, do not rely on shared secrets, robustly resist phishing, and are both scalable and easy to use.
Typically, a user being phished will click on a link asking for a password or code, receive a sign in page or request that is actually a phishing link, respond to the phishing link with the information, and not even know they were phished. Whether using an app or a website, this works well for attackers. They can send bogus OTP codes, preventing the user from detecting the problem.
Yubico stops this issue and provides a strong user authentication framework for cloud computing and more. A registered YubiKey “talks” to your device. When you click on a bogus phishing link and enter your details, you are then prompted to authenticate using your YubiKey. However, the YubiKey and device can see that even a phishing link or site with a valid SSL security certificate is bogus and will refuse to authenticate. In other words, Yubico offers a protocol that provides strong authentication through secret key cryptography that is accessible to anyone.
Pay as you go for groundbreaking user authentication security.
For less than a coffee per user/month
Get Started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

