What is a Sim Swap?
SIM swap fraud is an account takeover scam that targets a weakness in some forms of two-factor authentication in which a call or text message sent to a mobile telephone is the second factor or step. Also known as port-out scam, digital SIM swap, SIM splitting, and simjacking, the SIM swap scam exploits the ability of subscriber identity module (SIM) cards to be ported seamlessly by mobile phone service providers from device to device bearing different telephone numbers. Typically, carriers use this feature when customers buy new phones, switch service, lose their device, or experience theft.
Sim Swapping Definition
At its most basic level, during a SIM swap, a SIM hijacker convinces your mobile carrier to port your phone number over to their SIM card. By transferring those incoming messages, fraudsters can easily access your most sensitive accounts by completing text-based two-factor authentication checks. If you’ve failed to protect accounts with 2FA, they can use the phone number to generate existing and new passwords. They can also take over social media accounts, retail accounts, and any other accounts linked to the phone number—which is probably any online account.
The primary goal of SIM swap fraud is typically financial gain, often in the form of stealing bank and credit card information. However, sometimes a SIM swap attack might be intended to embarrass or humiliate the victim when compromising social media accounts.
How Does a Sim Swap Work?
Subscriber identity module (SIM) cards store user data in Global System for Mobile (GSM) phones. GSM phones without SIM cards are not authorized to use any mobile network.
This is why your phone is essentially dead when you remove your SIM card unless it is on WiFi. SIM swap victims do not receive carrier-facilitated text messages or phone calls once they are disconnected from their original carrier. All communications are routed to the attacker instead. And while WiFi will work, carrier-based internet and telephony will cease.
There are two types of SIM swap fraud. The first technique is based on social engineering directed at both the victim and the mobile phone carrier. The second technique includes an insider, usually a rogue mobile carrier employee, but this is less common.
Typically, the first method—without inside help—is the way the SIM swap scam works. It begins with the SIM swap attacker collecting personal information about the victim, by buying them from organized criminals, with their own phishing emails, or by using social engineering to directly impersonate the victim.
Scammers can use social media profiles to gather relevant information that helps them impersonate a victim. For example, a high school mascot or mother’s maiden name are often apparent on a social media profile—and they are also common answers to security questions.
The attacker can contact the victim’s mobile carrier, impersonating them and claiming to have lost or damaged the SIM card associated with the victim’s number. They request that customer service activate their new SIM card, or just ask for help switching to their new phone.
Once the SIM card swap scam takes place, the attacker receives all phone calls and SMS intended for the victim’s phone, including any one-time passwords, and the phone loses connection to the network. This enables the scammer to gain access and circumvent account-linked security features that rely on calls or text messages.
They can then set up new accounts in your name, for example. If they do so at your existing bank, you may not be notified.
What is a Sim Swap Attack?
SIM swap attacks hijack a core weakness surrounding mobile phones and authentication. Specifically, SIM swap hacks target phone numbers and use them to steal passwords, financial data, cryptocurrencies and other valuable items.
Various businesses, particularly those transitioned online, have placed phone numbers at the heart of customer authentication. Many sites allow users to reset passwords using a one-time SMS code. To successfully mount an attack to this kind of account, all the scammer needs is access to the mobile phone number of the target—nothing more. Phone numbers were never intended to be used as identity documents this way.
How do you know if you’ve been affected by a SIM swap? Here are some warning signs:
- No service at all. The surest sign of a SIM swap is if you completely lose all phone service. Strange texts and phone calls about, for example, a change to your mobile service, are concerning, and something to follow up on. However, if your SIM card has been deactivated, you won’t even be able to call or text customer service.
- Unusual social media activity. Social media activity that isn’t yours is a sign of an account takeover.
- New device. Your carrier tells you your phone number or SIM card has been activated on another device.
- No account access. If you cannot access your credit cards and/or bank accounts, and your login credentials no longer work, you have probably been taken over.
If you suspect you have been the victim of SIM swap fraud, contact your carrier, bank, and other organizations immediately.
Sim Swap Prevention Benefits
The FBI 2019 Internet Crime Report details that SIM swap, phishing, and vishing scams cost victims at least $57 million in losses. There are more victims of these kinds of scams than other kinds of cyber fraud. Business email compromise (BEC) and email account compromise (EAC) scams reported to the FBI in 2019 caused losses of over $1.7 billion.
The effects of a SIM swap attack can be devastating. When SIM hijackers acquire the date of birth, Social Security number, bank account details, credit card number, social media accounts, and other sensitive information of victims, a series of crimes with a long list of perpetrators starts. Years of identity theft can be in the making, not to mention lost money, work, and reputation. Fraudsters can commit other account takeovers, credit card fraud, and identity theft using those details.
The identities of SIM swap hack victims are often never fully restored. The benefits of SIM swap protection are simple: preventing the cycle.
How to Prevent Sim Swapping
There are several ways you can protect yourself and avoid SIM swapping:
Modify online behavior
Beware of social engineering attacks such as phishing emails that scammers may use to access your personal data to impersonate you. Sanitize your online presence to reduce risk.
Enhance account security
Use strong, unique passwords and questions-and-answers (Q&A) known only to you to improve your mobile phone’s account security.
Use PIN codes
Add a layer of protection through your carrier by setting a separate PIN or passcode for your communications. AT&T and T-Mobile allow it, and Verizon requires a PIN that you can modify. Never use an obvious PIN such as an anniversary, birthday, or address, and ideally, store PINs in a password manager.
Build IDs without your phone number
Avoid building identity and security authentication solely around your phone number, including text messaging (SMS). This is vulnerable to SIM swap fraud and other attacks, and text messaging is not encrypted.
Alerts
If your mobile carrier offers it, elect to receive additional notifications when a SIM card is reissued on your account. When you choose banks, retailers, and other organizations to use online, look for those that use behavioral analysis technology to discover compromised devices and call-backs to deter identity thieves.
Better two-factor authentication
Some take swapping SIM cards as a case in point against two-factor authentication (2FA), but that’s far from accurate. In fact, SIM swap fraud is an argument in favor of using strong authentication, using a security key for physical authentication.
Physical authentication techniques are superior to standard 2FA, because they require something you know, such as a password, plus something you have: a physical token. A hacker has to physically take your token to gain access.
Strong authentication
It is critical to enforce National Institute for Standards and Technology (NIST) Assurance Level-2 for admin functions at a minimum when implementing MFA. This means two factors: something you know, such as a code or password, and something you have, such as a push notification or an OTP generated by a registered device. However, as mentioned above, some factors are more secure than others.
Where possible, increase to NIST Assurance Level-3 for most critical assets. This means two-factor authentication (2FA) with something you know such as a password, along with a hardware-based cryptographic token, such as a FIDO key or smart card.
Strong authentication builds trust in a user’s identity. When the user identity and infrastructure itself are more trustworthy, a social engineering attack via SMS or call is less likely.
Go phoneless
For especially sensitive accounts, it can be worthwhile to attempt to remove your phone number entirely where possible. This can be a challenge at scale, but for high-value targets may be necessary.
Sim Swap Examples
Several high-profile SIM swap hacks have taken place in recent years:
In 2019, the Twitter account of Jack Dorsey, CEO of Twitter, was hacked via SIM swapping. The world noticed when unusual Twitter activity in the form of offensive Tweets started appearing for about 15 minutes—the time it took to regain control. The attackers gained control of Dorsey’s Twitter account through his phone carrier, who reassigned Dorsey’s phone number to an attacker’s SIM card in error.
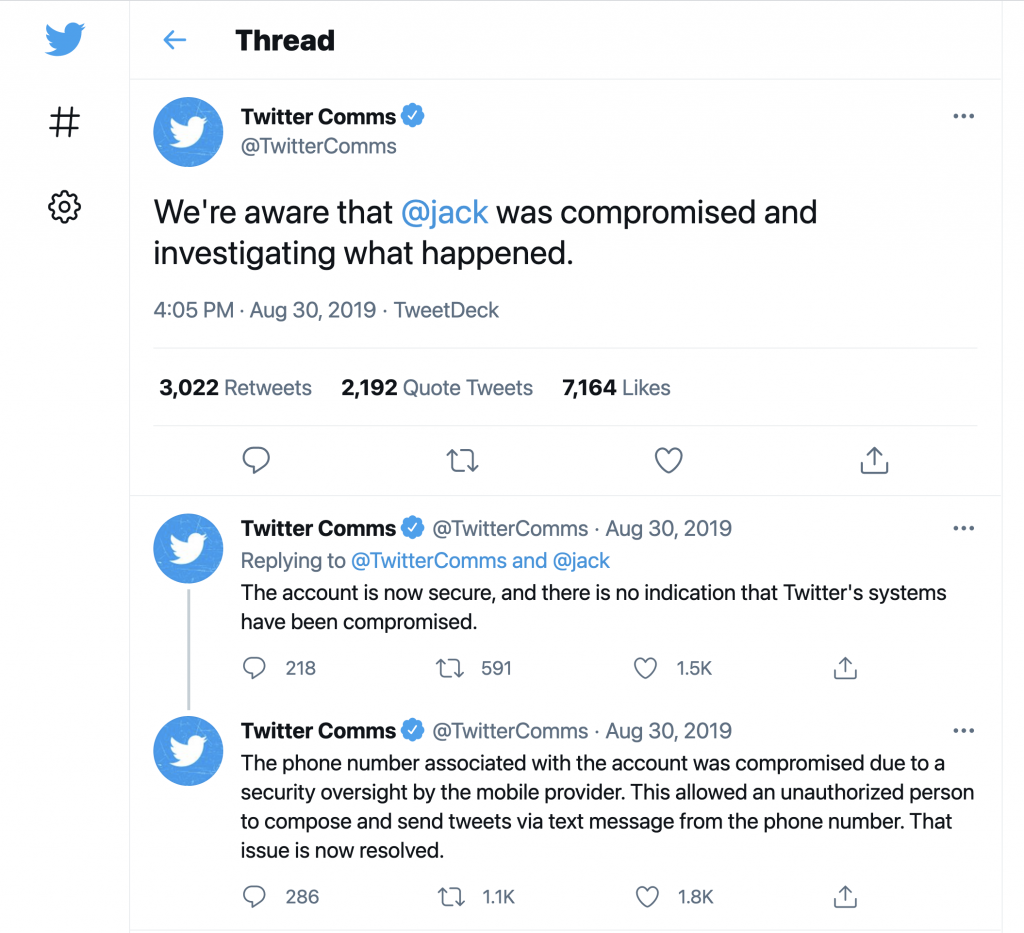
@TwitterComms. “We’re aware that @jack was compromised and investigating what happened.” 30 Aug. 2019, 1:05 pm. https://twitter.com/TwitterComms/status/1167528672523210752
Another incident happened in May 2020. Michael Terpin, CEO of Transform Group, filed a lawsuit against 18 year old high school student Ellis Pinsky. The SIM swap scam from 2018 was worth more than $23.8 million, and Pinsky was 15 years old at the time, according to the lawsuit. A connected case has already been settled in favor of the plaintiffs.
Does Yubico Offer Sim Swap Protection?
Any kind of 2FA is better than none, but SMS codes are no match against advanced cyber security threats like SIM swapping. Vulnerabilities will persist and human error will remain possible as long as your 2FA method relies on you—or your carrier—to recognize that a hacker is targeting you.
A security key like the YubiKey is a better solution. Starting at just $20, YubiKey removes the SMS factor from 2FA.
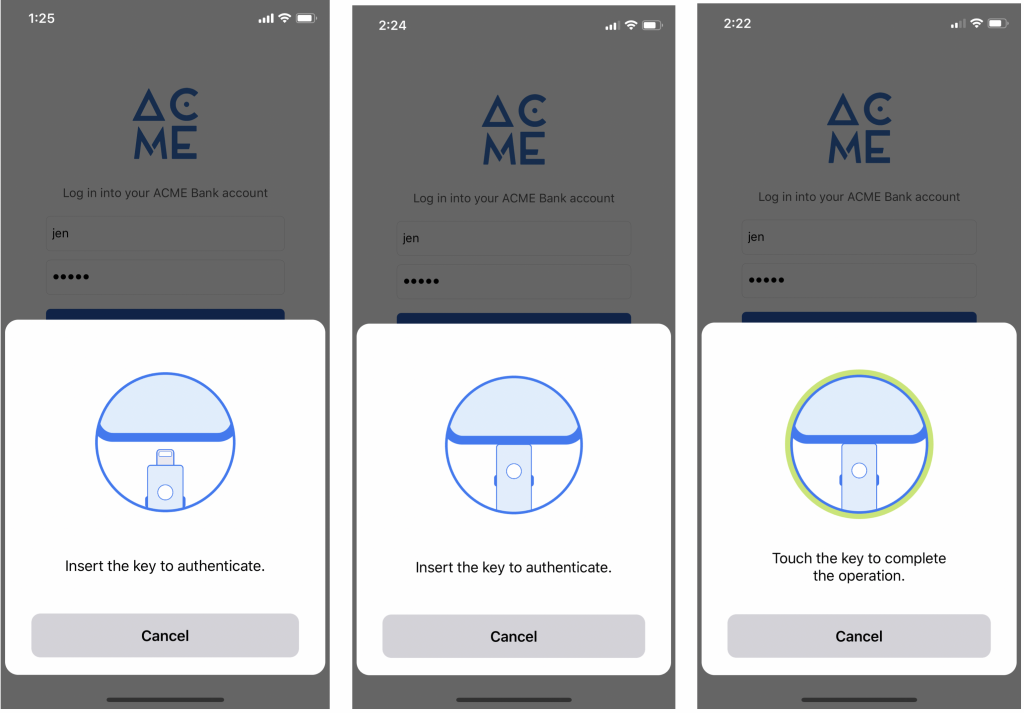
YubiKey also explodes the misconception that two-factor authentication without your phone is a hassle, because it doesn’t always involve one-time passcodes and copying and pasting. One-touch solutions exist that are easy to use, as well as keys for specific trusted devices that are not tethered to a vulnerable phone number.
Learn more about how to protect against SIM swap with YubiKey here.
Get Started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

