What is a Critical Infrastructure?
Critical infrastructure is defined as the systems and assets, both physical and virtual, that are essential for the functioning of a society and its economy. These include the facilities necessary for communication, transportation, energy production and distribution, financial transactions, emergency services, and other essential functions.
Critical Infrastructure Definition
Critical infrastructure and key resources are often managed and maintained by government agencies or trusted private sector organizations. They are typically highly interconnected, with disruptions in one area potentially causing cascading effects across multiple sectors.
Although the classification of what constitutes critical infrastructure may vary across countries (the US has 16 narrowly defined categories, whereas Indonesia has 6 broad categories for example), protecting mission critical infrastructure is crucial for a nation’s security, and their public safety, as disruptions to these systems can have significant economic, social, and political repercussions. Therefore, governments and organizations around the world do and should continue to invest significant resources in securing and safeguarding critical infrastructure against threats such as cyberattacks, natural disasters, and terrorism.
From a global perspective
The Organization for Economic Co-operation and Development (OECD), which is made up of 38 Member countries spanning the globe, commissioned a report to gain an understanding of critical infrastructure across the globe and their resiliency programs.
Figure 1. Sectors of designated critical infrastructure across OECD countries
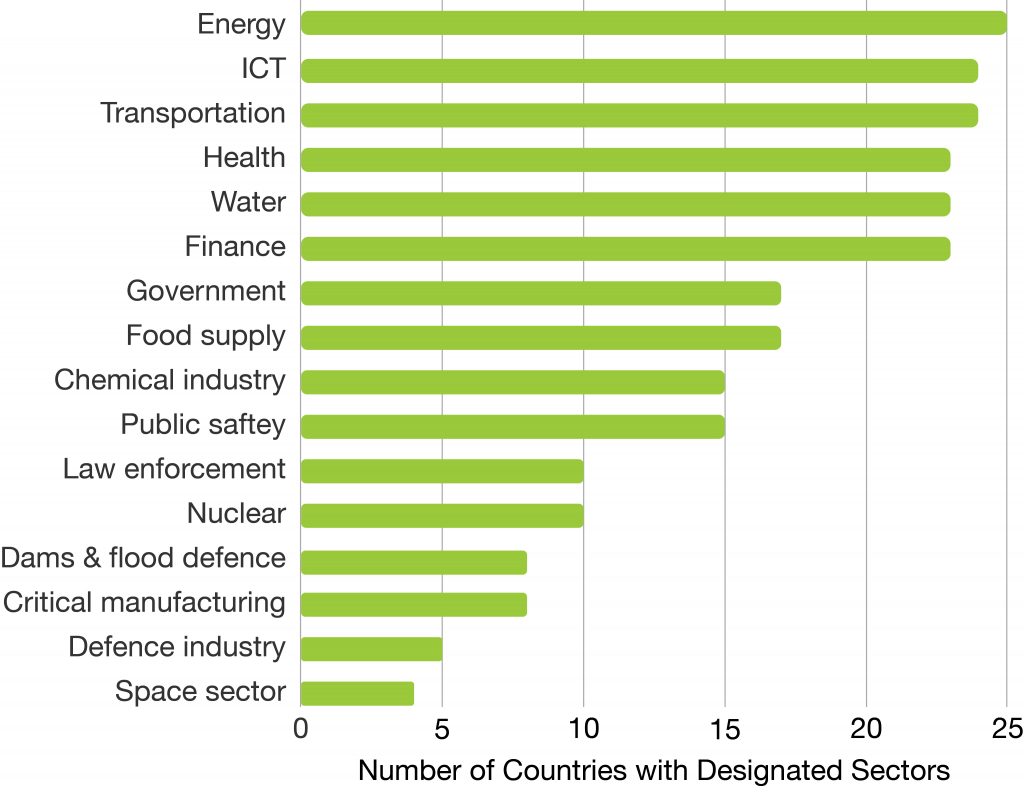
Note: Answers received from 25 OECD countries.
Source: OECD Survey on Critical Infrastructure Resilience and Security (2018)
The report noted that some countries depend on a large number of critical infrastructure sectors and showcased the various approaches taken by countries to define critical infrastructure, target specific infrastructure sectors and assess their criticality. It also discusses the different forms of partnerships between government and operators, and reviews the policy tools used by governments to foster critical infrastructure resilience.
Furthermore, on 16 January 2023, the European Union replaced the Directive on Security of Network and Information Systems 2016/1148 (commonly referred to as NIS) with Directive (EU) 2022/2555 (commonly referred to as NIS2). The primary goal of the legislation is to enhance the overall cybersecurity and resilience of the European Union’s critical infrastructure.
The NIS2 Directive identified two main categories: essential service operator (OES) and digital service provider (DSP).
OES are entities operating in sectors considered critical for the functioning of society and the economy. These sectors include energy (such as electricity, oil, and gas), transport (such as airlines, railways, public transit, and maritime), banking (such as payment services and stock exchanges), healthcare (hospitals and health clinics), water supply, and digital infrastructure (such as internet exchange points and domain name system service providers).
DSPs sit within a broad and dynamic industry encompassing companies that offer a variety of digital products and services such as search engines, information stores, online marketplaces, and social networks. These products and services are considered essential to the well-being and livelihood of both individuals and businesses, and affect how they communicate, transact, and access information online, making them an integral part of the modern digital economy.
Each EU member state is required to identify the OESes and DSPs within its territory and ensure that they meet specific cybersecurity and incident reporting requirements outlined in the Directive.
Specific to the US
The US Cybersecurity and Infrastructure Security Agency (CISA) has thoroughly defined and classified the entire gamut of critical infrastructures. The 16 CISA critical infrastructure sectors are discussed below, along with several others that OECD mentions, but essentially these are sectors of critical infrastructure “whose assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof. Presidential Policy Directive 21 (PPD-21): Critical Infrastructure Security and Resilience advances a national policy to strengthen and maintain secure, functioning, and resilient critical infrastructure.”
The National Institute of Standards and Technology (NIST) Computer Security Resource Center (CSRC) agrees with the CISA definition, but the US Department of Homeland Security (DHS) has provided its own definition of critical infrastructure. And although CISA’s definitions and regulations supersede those of DHS overall, this is still an important appendix to the foundation. Specifically, the DHS critical infrastructure “includes the vast network of highways, connecting bridges and tunnels, railways, utilities and buildings necessary to maintain normalcy in daily life. Transportation, commerce, clean water and electricity all rely on these vital systems.”
Critical Infrastructure FAQs
What are the regulations impacting Critical Infrastructure Sectors?
From a NIS2 perspective
The main objectives of the NIS2 Directive include:
– Improving cybersecurity capabilities. NIS2 requires EU member states to establish a national framework for cybersecurity and designate national competent authorities responsible for overseeing and enforcing cybersecurity measures.
– Enhancing cooperation. NIS2 promotes collaboration and information-sharing among EU member states to better tackle cross-border cyber threats and incidents.
– Protecting critical infrastructure. Ultimately, the Directive identifies certain sectors as critical infrastructure, and requires operators of essential services (OES) in these sectors to implement the aforementioned measures to ensure the continuity, availability and security of their services.
With NIS2, all EU member states have until 17 October 2024 to transpose its measures into their respective national legislative frameworks, meaning there is no ‘one size fits all’ approach to meet the directive. Each approach will require a unified effort involving individual enterprises, local and federal governments and some oversight from ENISA.
However, even if the details of the technological changes that will satisfy the NIS2 obligations are vague, two fundamental practices underpin any notion of enhanced cyber resilience: the use of multi-factor authentication (MFA) to secure all accounts in lieu of passwords, and the use of encryption to protect databases, communications, documents, servers and critical infrastructure. It will be these changes which will collectively fortify Europe’s critical infrastructure whilst enhancing its cybersecurity posture.
Specific to the US
Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA) are recommending phishing-resistant MFA for all critical infrastructure sectors. They collaborated to produce an important new document, “Identity and Access Management: Recommended Best Practices for Administrators” part of the Enduring Security Framework (ESF) it presents a distillation of IAM identity access management (AIM) and cybersecurity guidance put forth by CISA to date, based on NIST standards. It is specifically packaged for the information security and risk management (ISRM) admin, and targeted at the private sector.
Takeaways include:
– Leveraging Identity and Lifecycle Management programs. Protecting both informational technology (IT) and operational technology (OT) with strong programs. Shared accounts, especially those with elevated credentials, break many basic access management controls.
– Embracing MFA. The best practices document validates by dedicating eight pages to this topic alone. Advocating for the use of strong modern phishing-resistant MFA solutions.
– Taking responsibility and action. Critical infrastructure organizations have a particular responsibility to implement, maintain, and monitor secure IAM solutions and processes to protect not only their own business functions and information but also the organizations and individuals with whom they interact.
What are the Critical Infrastructure Sectors?
The OECD and CISA have identified key critical infrastructure sectors that impact the entire world. This list highlights 16 critical infrastructure sectors defined by CISA that are essential to the functioning of the United States and the global economy:
Chemical Sector
The global chemical sector affects agriculture, manufacturing, pharmaceuticals, and many other industries. It plays a crucial role supporting economic development and modern living. To safeguard the chemical sector and its critical infrastructure, several measures must be employed in some way, regardless of the specific location.
Regular security assessments on chemical facilities, transportation systems, and supply chains can identify vulnerabilities and aid in designing appropriate protection strategies. Strict physical security measures such as access controls, perimeter fencing, security personnel, and surveillance systems help prevent unauthorized access and protect against theft, sabotage, or terrorist attacks.
Robust cybersecurity measures safeguard computer systems, industrial control systems, and sensitive data from cyberattacks and data breaches. Well-defined emergency response plans should address accidents, spills, and hazardous material releases coordinated with local emergency services and community outreach to mitigate the impact of incidents.
Compliance with regulations and standards ensure the safe operation of chemical facilities and transportation and improve security throughout the sector. Specialized training for employees allows them to safely handle hazardous materials, respond to emergencies, and follow security protocols.
The international chemical sector engages in information-sharing initiatives with governments, industry associations, and other critical infrastructure sectors to exchange knowledge on emerging threats and best practices. The global nature of the chemical sector requires international cooperation to address cross-border security challenges, share best practices, and collectively respond to potential threats.
Chemical sector supply chain security from manufacturing to transportation and distribution includes ensuring the integrity of containers during transportation and verifying the identities of suppliers and customers. Companies in the sector implement procedures to mitigate insider threats and protect against potential sabotage or unauthorized activities by employees or contractors and collaborate with law enforcement agencies to address security concerns and investigate any suspicious activities that could pose a threat to critical infrastructure.
Presidential Policy Directive (PPD) 21 identifies the Department of Homeland Security (DHS) as the Sector Risk Management Agency (SRMA) for the chemical sector, which includes everything from consumer products and specialty chemicals to agricultural chemicals. CISA completes SRMA responsibilities for this sector on behalf of DHS, leading the collaboration between public and private organizations to develop resources that boost resilience and security.

Commercial Facilities Sector
The Commercial Facilities Sector refers to spaces that are occupied by the general public and draw large crowds of people that may be vulnerable to coordinated attacks. This area includes a diverse range of sites such as shopping malls, business, entertainment, or lodging such as media studios, gaming casinos, hotels, amusement parks, parades, public real estate, stadiums, and other locations.
In the US, CISA provides strategic direction across subsectors to enhance resilience and security in these types of locations, and the DHS is designated as the Risk Management Agency for the Commercial Facilities Sector.

Communications Sector
The communications sector is a complex network of interdependent satellite, terrestrial, and wireless systems. Globally, private-public partnerships and cooperation are essential to ensuring that comprehensive security measures are implemented and adhered to.
In the US, communications are mainly protected by the private sector. CISA assists private sector stakeholders in anticipating, predicting, and responding to sector outages and in implementing the protective risk management framework. The DHS is designated as the Risk Management Agency for the communications sector.

Critical Manufacturing Sector
Critical manufacturing is whatever manufacturing a specific country deems essential for its economic and national security. It encompasses all of the industries and processes that are vital for the production of goods, services, and materials that are necessary to maintain a functioning society or retain support of other critical sectors.
The specifics of critical manufacturing vary from country to country, but common themes emerge, regardless of region. Some of them include pharmaceutical and medical supplies, particularly access to drugs and emergency supplies; aerospace and defense; telecommunications equipment and infrastructure; information technology equipment and electronic components; electrical power generation and distribution systems, including generators and power stations; transportation equipment and transit stations; the chemical industry; food and beverage manufacturing; critical materials such as rare earth elements; and health and safety equipment such as firefighting gear, hazmat suits, and safety goggles.
In the US, these include: the manufacture of primary metals such as iron alloy and steel; electrical, component, and motor/generator manufacturing; machinery manufacturing such as engines and equipment; and transportation manufacturing including aerospace, commercial ships, and rail.
CISA identifies, assesses, prioritizes, and protects manufacturing industries with national significance to prevent and mitigate the impact of manmade or natural disasters. The DHS is designated as the Risk Management Agency for the critical manufacturing sector in the US.
Internationally, similar to the chemical sector, various information-sharing initiatives between industry associations, governments, and other critical infrastructure sectors help those managing critical infrastructure to exchange knowledge on emerging threats and best practices. The global nature of the sector demands international cooperation to share best practices, address cross-border security challenges, and collectively respond to potential threats.

Dams Sector
With more than 90,000 dams in the US and over 55,000 entries within the Register of Dams of the International Commission of Large Dams, dams are core to critical infrastructure worldwide, and the sector delivers core water control and retention services. Dams deliver important services including agricultural irrigation, flood and sediment control, hydroelectric power generation, industrial waste management, industrial and municipal water supplies, river navigation for inland bulk shipping, and recreation.
In the US, key dams sector services support various critical infrastructure sectors and industries, and dams sector assets help protect more than 43 percent of the US population from flooding, irrigate at least 10 percent of US cropland, and generate about 60 percent of the Pacific Northwest’s electricity. CISA works with sector partners to protect assets from natural disasters, as well as human-caused and technological events.
Unlike most other sectors, no one federal agency manages the dams sector. Instead, private owners and operators and their peers work together directly to collectively develop industry practices through the Dams Sector Coordinating Council with their government counterparts in accordance with the partnership framework developed in the critical National Infrastructure Protection Plan (NIPP) of 2013.
Defense Industrial Base Sector (DIBS)
The Defense Industrial Base Sector (DIBS) helps more than 100,000 subcontractors and companies supply services, facilities, materials, and other needs for the US military to assist in mobilizing, deploying, and sustaining military operations worldwide. The partnership within the DIBS consists of components of the Department of Defense (DoD), companies providing incidental materials and services to the DoD, over 100,000 DIBS contractor companies and their subcontractors, and both government-owned and operated and government-owned but contractor-operated facilities.
DIBS companies include both domestic and foreign entities, and have production assets located around the world. The DIBS does not include the commercial infrastructure service providers that the DoD uses to meet operational requirements, such as transportation, communications, power, or utilities. As described elsewhere, other Sector Risk Management Agencies manage these commercial infrastructure assets.
The DoD is the designated Sector Risk Management Agency for this sector.
Emergency Services Sector
The global emergency services sector (ESS) plays a critical role in responding to various emergencies and disasters, such as accidents, natural disasters, public health crises, terrorist attacks, and other incidents that pose threats to public safety and well-being. Critical infrastructure associated with emergency services, such as fire stations, police stations, and emergency operations centers, implement physical security measures to prevent unauthorized access and protect against potential threats.
Cybersecurity measures protect critical emergency services data, networks, and communication channels from cyber threats. Emergency services also often have redundant systems in place to ensure continuity of operations even in the face of infrastructure failures or disruptions. To ensure reliable and secure communication systems and the ability to coordinate emergency response efforts under any conditions, emergency services use dedicated and redundant communication networks to ensure constant connectivity.
Collaborative partnerships between emergency service agencies and the critical infrastructure sectors, allow for a more coordinated response during large-scale emergencies. Effective emergency responses also rely upon real-time data and information sharing between emergency services and other relevant stakeholders to facilitate timely decision-making.
Emergency service agencies develop and implement resilience plans and continuity of operations plans to manage and recover from potential disruptions caused by emergencies or disasters and ensure that essential services can be provided during and after emergencies. Standard operating procedures and emergency response protocols guide emergency service personnel during response operations.
Regular equipment, vehicle, and tool maintenance and upgrades ensure their reliability and effectiveness during response operations. Adequate funding, resource allocation, and investment into emergency services agencies and their critical infrastructure are crucial to their maintenance and enhancing the capabilities of emergency services.
The DHS is designated as the Risk Management Agency for the ESS in the US.
The ESS includes equipment and facilities in both paid and volunteer capacities, geographically distributed and organized at all levels of government, state, federal, local, territorial, and tribal. This includes county sheriff’s offices, municipal fire stations and emergency medical services (EMS) providers, city police departments, and town public works departments. The ESS also includes private sector resources, such as private security forces, industrial fire departments, and privately-owned EMS providers.
Energy Sector
The energy sector protects a range of oil, electricity, and natural gas assets and resources to maintain steady supplies of energy and ensure the robust health of the world economy. Like the other sectors, it is highly collaborative, as the need for energy resilience is inherently international.
As with other areas of critical infrastructure, the focus within the energy sector is often on physical security, cybersecurity, emergency response plans, redundancy, monitoring, and reporting of incidents. Transnational security challenges can be monumental in this area as well, and international cooperation is particularly important to resilience planning, supply chain security, cybersecurity, emergency response plans, and intelligence sharing.
The Department of Energy is the designated Sector Risk Management Agency for this sector in the US. On the global stage, the United Nations Framework Convention on Climate Change (UNFCCC), an international treaty that was designed to address climate change and its effects including greenhouse gas emissions, facilitates negotiations among member countries to reduce and promote clean energy solutions.
The World Energy Council (WEC) is a global energy body that provides a platform for energy leaders to share information and collaborate on energy-related issues, including policy, technology, and sustainability. Organization of the Petroleum Exporting Countries (OPEC) is an intergovernmental organization of major oil-exporting countries that coordinates oil production and pricing policies. Finally, International Renewable Energy Agency (IRENA) is an intergovernmental organization that promotes renewable, sustainable energy adoption and use worldwide.

Banking and Financial Services Sector
The Financial Services Sector guards financial assets and related institutions of all sizes, as well as the ability to access and use funds during large-scale natural disasters, power outages, and cyberattacks. The sector includes various financial institutions, such as banks, stock exchanges, payment processors, and clearinghouses.
Naturally, the financial infrastructure is often set up to use similar business continuity and disaster recovery plans to ensure continuity of critical operations during emergencies or disruptions as seen in other verticals. Financial institutions also collaborate with law enforcement agencies and intelligence organizations to share information on emerging threats and potential risks as in other infrastructure areas, but there are a few ways that banking and financial infrastructure is unique.
Cybersecurity is a top priority in the financial sector, with the aim of preventing data breaches and protecting against cyber threats such as hacking, phishing attacks, and ransomware. Protecting sensitive financial data such as customer information and financial records with encryption, secure storage, and access controls is essential to preventing unauthorized access and data leaks.

Fraud prevention mechanisms help to detect and safeguard against identity theft, credit card fraud, and account takeovers. Physical security measures protect critical financial infrastructure such as data centers, offices, trading floors, and ATMs from physical threats and unauthorized access. Financial institutions also often implement Anti-Money Laundering (AML) and Know Your Customer (KYC) procedures to identify and verify the customer identities in an attempt to detect suspicious financial activities.
The Department of Treasury (DoT) is the designated Sector Risk Management Agency for this sector in the US. Although the DoT does not have direct enforcement authority, it and several similar international regulatory bodies and organizations, work to promote financial stability, regulatory cooperation, and best practices globally. These groups set standards, issue guidelines, and promote best practices that ultimately influence national and regional regulatory frameworks. They also encourage cooperation and dialogue among regulators from different countries in order to facilitate cross-border cooperation, address global financial challenges, and enhance the stability and integrity of the global banking and financial systems. Some of the notable bodies within this group include:
- The International Monetary Fund (IMF), an international organization that aims to promote global monetary cooperation, secure financial stability, facilitate international trade, and foster sustainable economic growth via policy advice, financial assistance, and economic analysis for member countries.
- The World Bank Group offers policy advice on financial sector reforms and governance and financial and technical assistance to developing countries.
- The Financial Stability Board (FSB) is an international body that monitors and makes recommendations about the global financial system to promote stability and protect against systemic risks. It also coordinates the work of various international regulatory bodies and standard-setting organizations.
- International Organization of Securities Commissions (IOSCO) is an association of securities regulators from different countries that develops, implements, and promotes adherence to globally recognized securities regulation standards.
- The Bank for International Settlements (BIS) serves as a bank for central banks that coordinates monetary and financial stability policies.
- The Basel Committee on Banking Supervision (BCBS) develops and issues banking regulations and supervisory standards including the well-known Basel Accords, Basel II and Basel III, developed to enhance banking sector stability and risk management. It is part of the BIS.
- The Group of Twenty (G20), not itself a formal regulatory body, is a forum for major advanced and emerging economies to discuss financial and economic issues and coordinate policy responses.
Food and Agriculture Sector
Protecting the global food and agriculture sector and its critical infrastructure is essential to ensure food security, economic stability, and the well-being of populations worldwide. The food and agriculture sector encompasses a broad range of activities, including crop production, livestock farming, food processing, distribution, supply chains, and systems for food traceability.
Biosecurity protocols prevent the introduction and spread of pests, diseases, and pathogens that could harm crops, livestock, and the environment. Stringent food safety regulations ensure that all food produced and distributed is safe for consumption. This includes monitoring food quality, hygiene standards, and proper handling practices.
Resilient supply chains ensure continuity and reliability, even in the face of disruptions, natural disasters, or emergencies. Robust investment in agricultural research and innovation helps develop more sustainable, adaptable farming practices, as well as disease-resistant crop varieties and improved livestock breeds. And finally, crop and livestock insurance programs protect farmers against financial losses caused by adverse weather conditions, diseases, or market fluctuations in order to help them endure and continue producing for the greater good.
Sustainable water resource management practices ensure adequate water supply for agriculture without harming the environment. Other adaptation strategies with respect to climate change can help plan for extreme weather events and adverse change during the growing seasons. Encouraging and promoting other sustainable agriculture practices, such as organic farming, crop rotation, and agroforestry, can also contribute to the preservation of natural resources and enhance agricultural resilience.
All countries work to protect critical infrastructure for food storage, such as silos and warehouses, against pests and environmental factors. Another common goal is the maintenance of transportation infrastructure to ensure efficient movement of food products. Moreover, some countries maintain strategic food reserves or buffer stocks to ensure food availability during emergencies or crises.
Access to information is another area that protects critical food and agricultural infrastructure. Agricultural extension services—in the US these are often connected to land-grant universities—provide farmers with access to expert advice, training, and information to improve agricultural practices and productivity. Additionally, regular monitoring and surveillance helps predict, detect and respond to outbreaks of pests and diseases that could threaten crops and livestock.
There are also critical dependencies between the food and agriculture sector and many other sectors, such as the chemical sector that provides the fertilizers and pesticides used in the production of crops; the energy that powers the equipment used in agriculture production and food processing; the transportation systems used to move products and livestock; and the water and wastewater systems used for irrigation, cleaning, and sustain animal life.
There are several notable international organizations and bodies that deal with food and agriculture-related issues, setting standards, promoting best practices, and facilitating cooperation among countries to address global food security, food safety, agricultural development, and sustainable agriculture. Some of the most prominent bodies in the food and agriculture sector include:
- The Food and Agriculture Organization of the United Nations (FAO) is a specialized UN agency that provides technical assistance, policy advice, and research on agriculture, fisheries, and forestry in an international leadership effort to eliminate hunger, promote food security, and foster sustainable agricultural practices.
- The World Food Programme (WFP) is the food assistance branch of the UN that provides food aid to populations in crisis and vulnerable communities.
- International Fund for Agricultural Development (IFAD) is a specialized agency of the UN that focuses on financing and supporting smallholder farmers and rural development projects in developing countries.
- Although not solely focused on food and agriculture, the World Health Organization (WHO) sets international guidelines through the Codex Alimentarius Commission.
- The World Trade Organization (WTO) oversees global trade rules, including agricultural trade, and facilitates negotiations and agreements related to agricultural market access, subsidies, and tariffs.
This sector is mostly under private ownership in the United States. The food and agriculture sector accounts for about one-fifth of the economic activity in the US, and is made up of an estimated 935,000 restaurants, 2.1 million farms, and over 200,000 registered facilities for food manufacturing, processing, and storage.
For this sector, the Departments of Agriculture (DoA) and Health and Human Services (DHHS) are designated as co-sector risk management agencies. CISA collaborates with the various interdependent sectors and agencies to protect against a range of risks and offer guidance and resources.
Government Facilities Sector
The global government facilities sector and its critical infrastructure is focused on ensuring the continued functioning of governments, the safety of public officials, and the continuity of essential services. Government facilities encompass a wide range of buildings, installations, and infrastructure that support the operations of governmental agencies and institutions.
These facilities include courthouses, embassy building, general-use office buildings, national laboratories, special-use military installations, and storage structures for critical equipment, systems, networks, and functions. Along with physical structures, the sector protects cyber assets such as closed-circuit television systems, access control systems, and systems that support government employees who possess operational, tactical, or strategic knowledge or perform critical functions.
Physical security measures include access controls, perimeter fencing, security checkpoints, surveillance cameras, and security personnel to safeguard government buildings and facilities. Public access to certain government facilities is limited to protect against potential external threats.
Governments conduct threat assessments to identify the potential risks and vulnerabilities government facilities face, and develop risk management strategies to address them. Emergency response plans and continuity of operations plans are typically in place to handle crises and ensure that essential services can be provided during natural disasters, terrorist attacks, or other emergencies that could affect government facilities.
Cybersecurity measures protect against cyber threats and ensure the security of sensitive government data and communication networks. Information security measures, including insider mitigation procedures, safeguard sensitive and classified information to prevent unauthorized access and data breaches. It is paramount to secure communication systems and protect sensitive information and ensure communication between government officials within facilities.
Government facilities work closely with law enforcement agencies to address security concerns and investigate any potential threats or suspicious activities. Agency employees and security personnel receive specialized training to respond to security incidents effectively. Governments collaborate and share best practices for the protection of government facilities and critical infrastructure to address potential cross-border security challenges.
The DHS and the General Services Administration (GSA) are designated as the co-sector Risk Management Agencies for the Government Facilities Sector. While there is no single international regulatory body that specifically deals with government facilities as a whole, their protection and security primarily fall under the purview of individual national governments. There are, however, international organizations and agreements that address specific aspects of government facility security in the context of international diplomacy, cooperation, and counterterrorism efforts. Some of these organizations include:
- The United Nations Security and Safety Service (UNSSS) is responsible for ensuring the safety and security of UN personnel, offices, and facilities worldwide.
- International Criminal Police Organization (INTERPOL) assists law enforcement agencies in member countries with international cooperation and counterterrorism efforts, such as securing cooperation in government facilities and agencies.
- The International Atomic Energy Agency (IAEA) is an international organization that focuses on the safety and security of nuclear materials and facilities, including power plants.
- The International Maritime Organization (IMO) deals with the safety and security of international shipping that might have governmental significance, including port facilities and maritime infrastructure.

Healthcare and Public Health Sector
The healthcare and public health sector aims to protect population health and respond with necessary recovery actions after large-scale hazards such as terrorism, pandemics, disease outbreaks, and natural disasters. Protecting the global healthcare and public health sector, along with its critical infrastructure, is crucial to ensure the well-being of populations. This encompasses effective responses to public health emergencies, and the maintenance of essential medical services. The healthcare and public health sector encompasses a wide range of entities, including hospitals, clinics, public health agencies, laboratories, pharmaceutical manufacturers, and medical supply chains.
Physical security measures, cybersecurity, and supply chain security are all as equally critical as the aforementioned areas discussed above. Additionally, recent trends in ransomware attacks and data breaches as well as threats from stress on continuity of healthcare services and supplies of essential medicines, medical equipment, and personal protective equipment (PPE) during public health emergencies, have shown the need for more resilience in supply chains as well as improved emergency response plans to handle public health crises, such as disease outbreaks, natural disasters, or bioterrorism incidents.
Laboratories and research facilities handling dangerous pathogens or biological materials implement strict biosafety and biosecurity measures to prevent accidental releases or intentional misuse. Robust medical research and development and disease surveillance systems help detect and respond to emerging health threats promptly, and this is another critical area for infrastructure support.
There are many interdependencies with communications, ESS, energy, food and agriculture, IT, transportation, and water services sectors for leaders in this sector.
In the US, DHHS is designated by CISA as the sector’s risk management agency. The Centers for Disease Control and Prevention (CDC) also collaborates with international partners and plays a crucial role in global health, particularly in disease surveillance and control.
There are several international organizations and bodies that deal with healthcare and public health issues, providing guidance, setting standards, and facilitating cooperation among countries to address global health challenges, promote public health initiatives, and improve healthcare systems. A few of these include:
- The World Health Organization (WHO) is a specialized agency of the United Nations (UN) and the primary international agency responsible for public health. It works to promote health, prevent disease, and provide technical assistance to countries in health-related matters.
- Pan American Health Organization (PAHO) is the regional office for the Americas of the WHO.
- The European Centre for Disease Prevention and Control (ECDC) is an agency of the European Union (EU) that works to strengthen Europe’s defense against infectious diseases.
- United Nations Children’s Fund (UNICEF) works to improve the health and well-being of children worldwide, including access to healthcare, nutrition, and immunization.

Information Technology Sector
The information technology (IT) sector exists to identify cyber threats and vulnerabilities that may affect this or any other sectors, but also to protect against them. Safeguarding the sector on a global scale involves protecting cloud services, data centers, hardware manufacturing, internet infrastructure, software development, telecommunications, and other industries against these potential threats.
In the US, CISA designates DHS as the risk management agency for the IT sector, which coordinates actions between a large number of public and private partners. Internationally, while there is no single regulatory body in this space, several bodies and initiatives address specific aspects of the IT sector and its related challenges, setting standards, promoting best practices, and facilitating cooperation among countries and stakeholders:
- International Telecommunication Union (ITU) is a specialized agency of the UN that deals with information and communication technologies (ICTs). It develops global telecommunication standards, allocates radio-frequency spectrum, and works on issues related to broadband connectivity and digital inclusion.
- Internet Corporation for Assigned Names and Numbers (ICANN) is a nonprofit organization responsible for managing and coordinating the Domain Name System (DNS) to ensure the stable and secure operation of the internet.
- Internet Engineering Task Force (IETF) is an open international community of network designers, operators, and researchers responsible for developing and promoting internet standards.
- The World Intellectual Property Organization (WIPO) deals with intellectual property issues, including patents, copyrights, and trademarks, which are relevant to the IT sector.
Nuclear Reactors, Materials, and Waste Sector
This sector includes active nuclear power plants and power reactors that provide electricity, research and test labs that use medical isotopes such as those that treat cancer patients, and reprocessing facilities.
In the US, this sector comprises an extensive civilian nuclear infrastructure that exists throughout the country. Critical interdependencies exist with chemical, ESS, energy, healthcare and public health, transportation, and water services sectors, and the DHS is designated as the Risk Management Agency for the sector.
Internationally, the International Energy Agency (IEA) is an autonomous intergovernmental organization that conducts energy research, analyzes energy policies, and provides recommendations to member countries to promote energy security and sustainability with the goal of ensuring reliable, affordable, and clean energy for member countries. IAEA promotes the peaceful use of nuclear energy, and works to ensure nuclear safety and prevent nuclear proliferation.
Transportation Systems Sector
Critical transportation infrastructure involves roads, bridges, airports, seaports, railways, and public transportation systems. Each country typically has its own national security agency responsible for safeguarding its transportation infrastructure from various threats, including physical attacks, cyber attacks, and acts of terrorism. These agencies often collaborate through organizations like Interpol and Europol to share intelligence and coordinate security efforts.
The International Maritime Organization (IMO) is a specialized agency of the UN responsible for regulating international shipping that works to ensure the safety and security of shipping, as well as the prevention of marine pollution from ships. Likewise, the International Civil Aviation Organization (ICAO) is another specialized UN agency, in this case responsible for regulating civil aviation globally. Finally, the International Rail Transport Union (IRU) is an organization that facilitates cooperation and coordination in the road transport and logistics industry. Each of the aforementioned works to implement and enforce standards internationally. Private sector transportation companies and operators also play a vital role in protecting their assets and ensuring the safety of their passengers and cargo, often collaborating with governmental agencies and international organizations to implement security measures.
The transportation sector in the US includes the aviation, freight rail, highway and motor carrier, mass transit and passenger rail, maritime transportation system, pipeline, and postal and shipping systems. CISA helps the co-sector-specific agencies for the transportation systems sector, DHS and the Department of Transportation (DoT), protect these systems and ensure continuity of operations.
Water and Wastewater Systems Sector
The water and wastewater systems sector is vulnerable to natural disasters, cyberattacks, contamination with deadly agents, and physical attacks with toxic agents such as gaseous chemicals. Although physical disruptions are the obvious concern, critical services, including healthcare (hospitals) and firefighting, and other interdependent sectors, such as food and agriculture, energy, and transportation systems, may create widespread consequences in the event of a cyber attack such as a denial of service, preventing authorities and agencies from deploying or communicating with the appropriate resources.
Each country typically has its own regulatory bodies responsible for overseeing water and wastewater management within their borders. Additionally, regional organizations may even address shared water resources and promote cooperation among neighboring countries. Critical water and wastewater infrastructure are protected through physical security measures, access controls, surveillance, and cybersecurity measures to prevent unauthorized access and potential disruptions.
There are about 16,000 wastewater treatment systems that are publicly-owned and 153,000 public drinking water systems across the US. These systems provide over 80 percent of Americans with their potable water, and about 75 percent of the population treats its sanitary sewerage in these wastewater systems.
CISA classifies both the ability to “supply water” and “manage wastewater” as “national critical functions.” In the US, the Environmental Protection Agency (EPA) is the designated sector risk management agency for water and wastewater systems.
Internationally, no one international regulatory body oversees the entire global water and wastewater sector, but several organizations and initiatives address water-related issues and promote best practices for protection and management.
- The World Health Organization (WHO) plays a significant role in setting international standards and guidelines related to water quality, sanitation, and health. Their recommendations help countries establish effective water and wastewater management practices to safeguard public health.
- The United Nations Environment Programme (UNEP) coordinates international efforts related to environmental issues, including water resources and wastewater management, promotes sustainable practices, and advocates for the protection of water bodies from pollution and degradation.
- The International Water Association (IWA) is a global network of water professionals, researchers, and technology providers dedicated to promoting best practices in water management that develops guidelines and provides expertise to improve water quality, sanitation, and overall water infrastructure.
- The Global Water Partnership (GWP) is an international network that brings together stakeholders from various sectors to address water-related challenges to enhance the governance and management of water resources and facilitate the exchange of knowledge and experiences among countries.
- The International Standards Organization (ISO) develops and publishes international standards that cover various aspects of water and wastewater management, including quality, treatment, and environmental impacts to help ensure consistency and high-quality practices globally.
Although many of the above mentioned sectors are logically independent, in practice they are frequently operationally linked. Any disruption in one sector can have cascading effects, leading to widespread disruption and damage in the others. Therefore, protecting all areas of critical infrastructure is crucial to the overall security and resilience of the United States and ultimately, the entire global economy.
What is Critical Infrastructure Security?
There are various types of critical infrastructure attacks, including:
Cyberattacks. These are attacks launched over the internet or other computer networks, targeting the systems that control or monitor critical infrastructure. Cyber attacks on critical infrastructure can include malware, ransomware, denial-of-service attacks, and other methods that can compromise or disrupt the security and integrity of key computer systems.
Physical attacks. These are attacks that involve the physical destruction or disruption of critical infrastructure, such as bombing, sabotage, theft, or vandalism. Physical attacks might also target critical infrastructure components, such as removing copper wiring from electrical substations.
Natural disasters. Natural disasters such as hurricanes, earthquakes, floods, and wildfires can damage or destroy critical infrastructure, causing widespread disruption and damage.
Human error. Mistakes made by employees or contractors working on critical infrastructure can also lead to disruptions or failures. For example, a construction worker might accidentally damage an underground pipeline, causing a gas leak.
Terrorism. Terrorist groups may target critical infrastructure as a means of causing widespread disruption, fear, and economic damage. The most high profile examples often include terrorist attacks on transportation systems, such as airplanes or trains, that lead to disruption of travel and commerce.
At times, these kinds of attacks might overlap. For example, a terrorist attack might involve both a cyber attack component coupled with a physical attack. Or a natural disaster might open a window for some other kind of physical or cyber attack whilst the security focus of the responsible authority has temporarily shifted.
For this reason and many others, what is often called critical infrastructure cyber security is really a complex and ongoing process of protecting critical infrastructure against all types of attacks, requiring a combination of physical security measures, cybersecurity defenses, emergency planning, and response capabilities.
Critical Infrastructure Protection (CIP)
What combination of physical security measures, cyber security defenses, emergency planning, and response capabilities can ensure critical infrastructure resilience?

Critical infrastructure security requires a multi-layered approach that involves a combination of physical security measures, cybersecurity defenses, emergency planning, and response capabilities. Some specific examples of these measures include:
Physical Security. This might include measures such as access controls, armed guards, intrusion detection systems, perimeter fencing, and surveillance cameras. Physical security measures may help deter and detect physical attacks on critical infrastructure, or reduce their impact if they do occur.
Critical Infrastructure Cybersecurity. This might include anti-virus software, data encryption, firewalls, and both intrusion detection and prevention systems. Cybersecurity defenses can help to prevent and detect cyberattacks on critical infrastructure, and hopefully mitigate the damage they cause.
Emergency Planning. This involves creating emergency plans and protocols to help organizations respond to and recover from attacks on critical infrastructure. Emergency planning can include procedures for evacuating people from affected areas, shutting down systems, and restoring operations.
Response Capabilities. This involves maintaining the necessary resources and capabilities to respond to attacks on critical infrastructure, such as emergency responders, backup systems, and spare parts. Response capabilities can help to minimize the impact of attacks and restore critical infrastructure systems as quickly as possible.
How to Implement Critical Infrastructure Security
There is no single best framework for improving critical infrastructure cybersecurity or protecting against all types of attacks. The specific combination of measures that organizations need to implement will depend on a variety of factors such as the type of the critical infrastructure, the nature of the potential threats faced, and the resources available to both prevent and mitigate.
Generally speaking though, a zero trust approach is recommended from the get go, and requires strict access controls and verification for every user, device, and network connection, regardless of whether they are inside or outside of the network perimeter. Zero trust assumes that every user, device, and network connection is potentially malicious, and uses strong authentication and authorization mechanisms to ensure that only authorized users and devices can access critical infrastructure. Using this principle as a basis, many cyber attacks can be prevented before they can even manifest as issues.
As such, a zero trust approach is an essential component of critical infrastructure guidance:
Reduced attack surface. By requiring strict authentication and authorization for every user and device, a zero trust approach can help shrink the attack surface of critical infrastructure. This reduces opportunities attackers have to gain unauthorized access to critical systems and data.
Improved visibility. A zero trust approach can provide improved visibility of suspicious activity within network traffic and unusual user activity, and help to detect unauthorized access.
Stronger security controls. A zero trust approach requires the use of strong security controls such as encryption, multi-factor authentication (MFA), and segmentation. These controls can help prevent unauthorized access, but also limit the impact of security breaches if they do occur.
Improved response capabilities. In the event of a security breach, a zero trust approach can improve response capabilities by enabling organizations to identify the source of the breach, and take appropriate action to contain and remediate the situation more rapidly.
Challenges of Protecting Critical Infrastructure
Protecting critical infrastructure is a complex challenge that involves multiple stakeholders and requires a coordinated, comprehensive approach. Some of the key challenges that both organizations and critical infrastructure protection solution companies face include:
Complexity. Critical infrastructure systems are often highly complex and interconnected, with multiple components and layers that can be difficult to secure and protect holistically.
Limited resources. Even larger organizations that operate critical infrastructure systems have limited resources and face budget constraints, which can make it difficult to implement optimal security measures.
Aging infrastructure. Many critical infrastructure systems were not designed with modern security threats in mind, making them more vulnerable to attack.
Insider threats. Insider threats, such as disgruntled employees, contractors with access to critical systems, or even careless managers, pose a major risk to critical infrastructure security.
Cybersecurity threats. Cyber attacks on critical infrastructure are becoming increasingly sophisticated and frequent, and can be difficult to detect and prevent without the proper measures in place. For example, the dark web marketplace potentially offers both credentials and phishing kits, or the emergence of AI and how it may offer new possibilities for writing malware without skills. Every team tasked with protecting critical infrastructure should at least be ready for a steady stream of these kinds of low effort tactics from hackers.
Geographical dispersion. Critical infrastructure systems are often spread out geographically, making it difficult to monitor and secure all components effectively.
Interdependency. Critical infrastructure systems are interdependent, so a disruption in one system typically has cascading effects on others. Containing and managing the impact of an attack is difficult, if the cross and downstream consequences are not fully understood.
Compliance. Compliance with regulations and standards can be a challenge for organizations that operate critical infrastructure, as these requirements may be complex and costly to implement.
Public access. Many critical infrastructure systems, such as transportation or energy systems, require public access, making it difficult to implement robust physical security measures without disrupting normal operations.
Does Yubico Support Critical Infrastructure?
Yes. Yubico has designed and created a guide to deploy a Zero Trust framework, detailing the ideal way to protect the modern supply chain – which at times contains all product parts, hardware, software, and code needed to support an organization, including intellectual property (IP) and the protected personal information (PPI) of customers.
The SolarWinds and Colonial Pipeline attacks highlighted vulnerabilities in the supply chain across top federal agencies and critical infrastructure. The White House responded by outlining new Zero Trust guidelines and expectations for phishing-resistant, multi-factor authentication (MFA) for federal agencies — as well as their partners and suppliers — under Executive Order (EO) 14028, Improving the Nation’s Cybersecurity.
Furthermore, the Cyber Safety Review Board (CSRB) within CISA – which was established pursuant to President Biden’s EO 14028 – released a report on the attacks associated with Lapsus$ and related threat groups. Lapsus$, an international extortion-focused group of hackers, with members known to base themselves in the U.K. and Brazil, acted between 2021 and 2022 to breach dozens of organizations with a strong security posture leveraging SIM swapping.
This report urgently recommends that more stringent authentication solutions be implemented, transitioning away from SMS-based MFA and instead adopting easy-to-use passwordless solutions such as FIDO compliant phishing-resistant methods.

Yubico ensures that organizations can meet these evolving compliance regulations with phishing-resistant security. Both the YubiKey and YubiHSM 2 come in FIPS 140-2 validated form factors, and the YubiKey also meets NIST SP 800-63-3 Authenticator Assurance Level (AAL) 3 requirements.
The YubiKey helps secure authentication from external sources and between IT and OT systems, while the YubiHSM 2 (a hardware security module) and YubiHSM FIPS enable secure key storage and operations on a physical device for cryptographic protection.
With NIS2, all EU member states have until 17 October 2024 to transpose its measures into their respective national legislative frameworks. Because each country has different resources and existing infrastructure, there is no ‘one size fits all’ approach to meet the directive. Each approach will require a unified effort involving individual enterprises, local and federal governments and some oversight from ENISA.
However, even if the details of the technological changes that will satisfy the NIS2 obligations are vague, two fundamental practices underpin any notion of enhanced cyber resilience: the use of multi-factor authentication (MFA) to secure all accounts in lieu of passwords, and the use of encryption to protect databases, communications, documents, servers and critical infrastructure.
It is simple to integrate these measures into both new and existing infrastructure with Yubico, which offers a range of options for enterprises looking to enhance their cyber resilience. The YubiKey, which supports both PIV and FIDO2, can augment or even replace a password-based authentication flow with a strong phishing-resistant one.
There are also many YubiKey options and form factors to suit the full spectrum of enterprises from very large to very small. This includes CSPN and FIPS certified variants – such as the YuiKey 5 FIPS Series or 5 CPSN Series – for those looking for a government recognised device, or the YubiKey 5C NFC which offers FIDO2 and PIV support with both USB-C and NFC capabilities for compatibility with a wide range of devices.
For enterprise encryption needs, the YubiHSM is a useful toolbox for storing and generating private keys and other cryptographic material securely. It arrives at a fraction of the cost of a traditional HSM, is packaged into a diminutive form factor the size of a fingernail, and supports common interfaces such as PKCS11 and Microsoft CNG.
Although the NIS2 Directive has felt like a formidable challenge and can be difficult to implement, strong cyber security is straightforward. Investing in cyber resilience is worthwhile, and is now required—but it’s also easier than it seems. Yubico can help any enterprise willing to embrace the challenges of cybersecurity, well beyond just the need to satisfy NIS2.

Modern, strong authentication based on phishing-resistant public key cryptography is a core foundation of Zero Trust, and it is important to always deploy phishing-resistant multi-factor authentication (MFA) for code access and implement trusted code-signing. However, not all forms of MFA are created equal.
Most basic forms of MFA, such as SMS and mobile-based authenticators, are perishable and highly vulnerable to MiTM threats. These methods do not achieve the strongest levels of phishing defense delivered by purpose-built hardware security keys such as the YubiKey from Yubico.
If these legacy forms of identity verification are part of your code management practices, your Zero Trust promise may be compromised. The YubiKey offers phishing-resistant two-factor, multi-factor, and passwordless authentication at scale, ensuring only trusted and validated users have access to critical code repositories.
They integrate seamlessly with existing IAM solutions such as Microsoft, Okta, Duo, and Ping, and provide secure authentication for hundreds of applications and services, eliminating any rip or replace of existing solutions. Users get protected in minutes right out-of-the-box.
A single YubiKey works across multiple devices, enabling users to deploy phishing-resistant MFA at scale. YubiKeys are also easily re-programmed, making them suitable for temporary workers, and enable self-service password resets, significantly reducing IT support costs.

As a practical example, during the Russian invasion of Ukraine, information warfare has played a critical role, with the biggest cyber attack vector and threat being weak login credentials. According to a Ukraine cybersecurity executive at a major government-owned energy company, attempted attacks to its infrastructure rose from 21,000 events in all of 2021 to 760,000+ attempts just from February 24, 2022 to March 24, 2022 — an increase of 3519%.
Yubico paired with authentication partner Hideez to help to protect critical infrastructure in Ukraine by donating 20,000 YubiKeys and lending technical support. The keys were distributed to a dozen government agencies and companies providing critical infrastructure, including:
- SSSCIP, State Service of Special Communication and Information Protection of Ukraine
- Ministry of Digital Transformation, heading IT modernization and next generation of government e-services
- Government owned energy companies and power plants
- Ukraine’s .UA domain managing organization Hostmaster.UA
This is one of the many real-world examples of how Yubico’s technology can protect the most critical infrastructure under the worst circumstances with minimal support and resourcing.

A U.S. State uses the YubiKey to protect voter registration databases from hackers

Schneider Electric enhances global supply chain security with YubiKeys and YubiHSM

YubiKeys are defending Ukraine’s national oil and gas company against cyberattacks
Get started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

