Phishing attacks are getting smarter. Your defenses should, too.
Most cyber crime relies on stealing account credentials. That’s why it’s so important to use more than just a password to protect your online accounts.
Not all Multi-Factor Authentication is created equal
Any MFA is better than just a password, but common methods are flawed. A common way to log in is with mobile devices, but mobile authentication can still be exploited by hackers. True protection requires multi-factor authentication (MFA) that is phishing-resistant, such as hardware security keys.

SMS
Despite still being a popular method of MFA, SMS-based MFA is easily compromised using sim-swapping and interception techniques.

Push notifications
In recent successful attacks, hackers have bombarded targets with push notifications. Users only need to slip up once for their accounts to be compromised.

Authenticator apps
Though more secure than many alternatives, professional hackers can bypass authenticator apps using Man-In-the-Middle phishing attacks.
Stopping phishing attacks requires MFA. But legacy forms of MFA can still be hacked.
In the video below, ethical hacker Rachel Tobac explains how a typical modern cyber attack works, and shows how security keys offer better security than mobile authentication.
Risk of account takeovers
Research by Google proves these mobile-based methods of authentication don’t offer the same level of security as purpose-built MFA, like Security Keys.
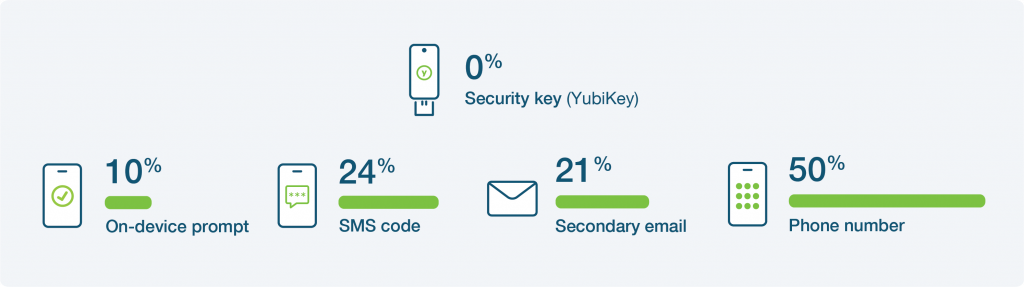
Security keys qualify as phishing-resistant MFA, recommended by security experts around the world for individuals who want top-level security at an affordable price, without sacrificing user experience.
The top 5 mobile authentication misconceptions
YubiKey: Built for high security. Phone: Built for communication. Only one stops phishing. Learn more in our exclusive white paper.

Introducing the YubiKey
YubiKeys are the most effective tool to prevent cyber attacks. They work with any device to add secure and easy-to-use protection against phishing for all online accounts.
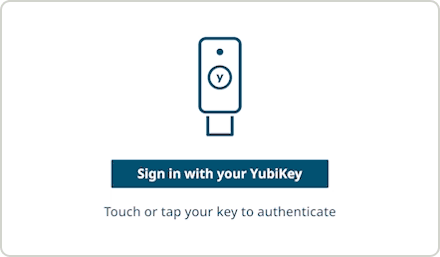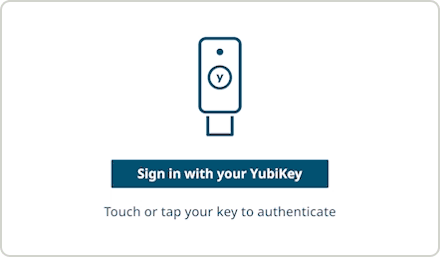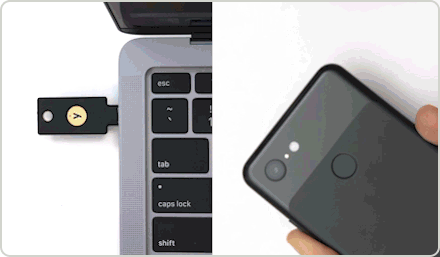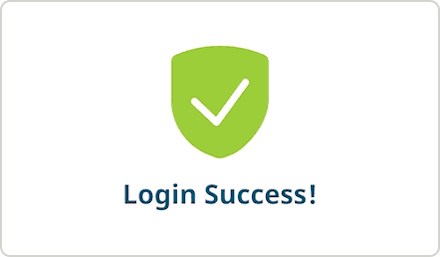
What makes YubiKeys the most effective method of stopping phishing attacks?
YubiKeys are purpose-built for security, and so don’t have the same vulnerabilities as mobile authentication. To safely access your online accounts, you only need to connect your key to your device – and touch.

The power of touch
YubiKeys require a user to be physically present, so remote attacks are impossible.

No shared secrets
Security keys contain a unique cryptographic code which cannot be stolen, meaning one key can secure hundreds of different online services.
The key to trust
FIDO protocols ensure that keys will only respond to trusted sources, so they will never fall for fake websites.
Why are YubiKeys used?
YubiKeys protect against 99.9% of phishing attacks1, while offering an affordable and user-friendly experience.

Works with all devices
YubiKeys work with USB-A, USB-C, Lightning & NFC, to easily interface with more devices.

Easy to set up
YubiKeys work straight out of the box with hundreds of online services, requiring no additional drivers or software.

A bridge to modern protocols
YubiKeys work with legacy systems like smartcards, while offering a first step to passwordless.
Who do YubiKeys protect?
YubiKeys are used around the world by businesses of every size, in all industries, as well as by individuals – anyone with an online account can benefit from phishing-resistant MFA.
YubiKeys can help you or your business secure:

Privileged users
Protecting an organization’s critical employees and their sensitive data

Remote workers
Allow employees to safely log in wherever anywhere: at an office or remotely
Shared devices
Safely allowing multiple users to securely access a shared device

Mobile-restricted areas
Protecting account security even in areas where phone use is limited

Personal accounts
Making the internet safer by securing the online services people care about most
That’s why the world’s leading companies protect their accounts with YubiKeys
“We have had no reported or confirmed account takeovers since implementing security keys at Google.”

“YubiKeys are fast, robust and best-in-class: a best-in-class device and best-in-class security.”

“We chose YubiKey because we found that it integrates rather easily with any operating system and with any client.”

Have any questions?
We’re here to help. Contact Sales to become more secure today.
1.The Total Economic Impact™ Of Yubico YubiKeys
Risk Reduction, Business Growth, And Efficiency Enabled By YubiKeys
