Tag: privileged users
-
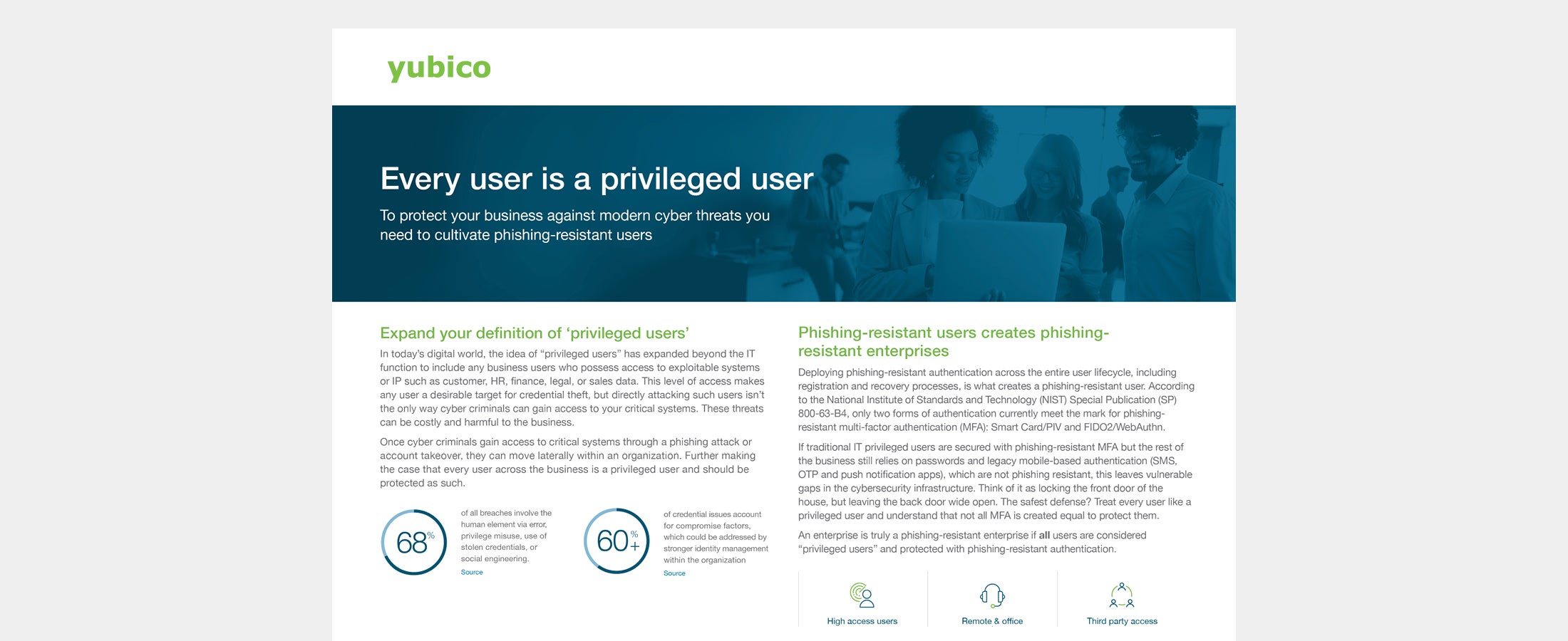
Every user is a privileged user The idea of “privileged users” has expanded beyond the IT function to include any business users who possess access to exploitable systems or IP, making all users target of sophisticated cyber attacks. Learn how to cultivate phishing-resistant users with modern, phishing-resistant multi-factor authentication (MFA). Read more phishing-resistant MFA phishing-resistant users privileged users YubiKey -

Boliden case study Boliden is one of Europe’s leading metal mining companies. Based in Sweden, with presence around the Nordic region and beyond, Boliden produces a vast array of the metals required for modern life: zinc, copper, lead, nickel, gold, palladium, platinum and silver. Read more FIDO2 PIV privileged users YubiKey 5C NFC -

Phoenix Software protects the public sector supply chain with YubiKeys Responding to the growing cybersecurity threat Shaun Tosler, Infrastructure Manager at Phoenix, works closely with the Phoenix CTO and Bytes Technology Group CISO to look after all IT infrastructure internally and those that run managed services. His challenge is to maintain a high-level of security while ensuring ease of access and usability for both their […] Read more phishing-resistant MFA privileged users Public Sector -

BeyondTrust case study More than 20,000 customers trust BeyondTrust with Internet Access Management. As a security company themselves, BeyondTrust takes their brand reputation and internal security seriously, and have invested in strong MFA from a partner like Yubico. The case study walks through how BeyondTrust has increased their security posture with a phased rollout of YubiKeys and has not only strengthened their cybersecurity defenses, but have done it in a predictable and efficient way with YubiEnterprise Subscription and YubiEnterprise Delivery services. Read more privileged users zero trust -

Securing privileged users and accounts with phishing-resistant MFA Learn why securing privileged users and accounts with phishing-resistant multi-factor authentication (MFA) is a critical need across the industry. Read more phishing-resistant MFA privileged users -

Privileged Access Management at CERN: Q&A with Dr. Stefan Lüders In an era of increasing cyber attacks, how do you balance the desire for unrestricted research freedom against the need to protect that research from cyber threats? This is the challenge faced by CERN, leaders in the scientific research community. Their solution? Provide a clear articulation of what constitutes privileged data, and create flexible security […] Read more authentication MFA phishing-resistant MFA privileged access manegement privileged users YubiKey -
Why legacy authentication is putting your users at risk Step one in any effective cyber security program includes securing privileged accounts, credentials, and secrets with modern strong authentication. Download the Yubico White Paper, The critical strong authentication need for privileged users, to learn who really is a privileged user, and industry best practices to secure your privileged users against phishing attacks and account takeovers. Read more authentication privileged users -

Securing your privileged users with phishing-resistant MFA Deploy phishing-resistant authentication to protect privileged users and your organization against modern cyber threats. Read more phishing-resistant MFA privileged users -

Enable secure privileged access management Zero account takeovers with the YubiKey Privileged users are the most highly targeted users by cyber attackers as these users hold higher ‘privileges’ to critical and sensitive applications and data. These could be IT, security, network and database admins, as well as C-suite, HR, finance and marketing employees. Securing privileged users across both IT and business […] Read more account takeovers phishing privileged users -

Authentication: It’s All About the User Experience, SANS Institute How can you prove you are who you say you are? Read more authentication privileged users
