Tag: FIDO
-
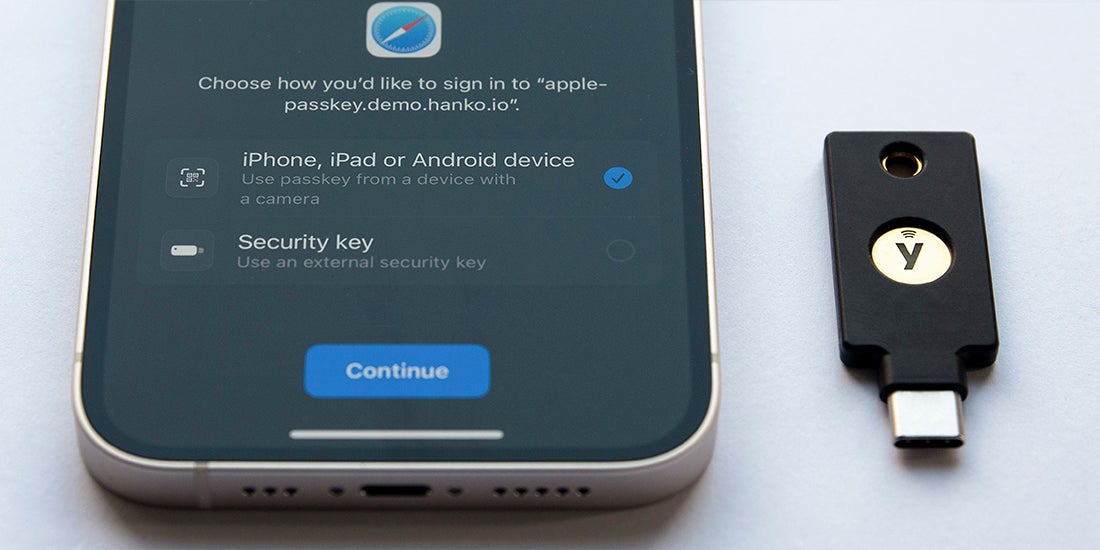
Yubico’s perspective and resource guide to passkeys 101 There has been a lot of information lately about the new ‘password-killing’ solution, the passkey. As we’ve discussed in previous posts on the topic, passkeys are a new industry term to make existing technology standards approachable to users. Passkeys are discoverable FIDO credentials that enable users to authenticate to websites without a password. Two types […] Read more FIDO MFA passkeys phishing-resistant MFA YubiKey -
Introducing Yubico Authenticator 6 for Desktop Today we’re releasing the first public beta version of Yubico Authenticator 6 for Desktop. This new version has some big changes under the hood, so let me explain what they are and why we’re doing them. Or, if you’re just eager to try it out, skip to the bottom of this post and click on […] Read more authentication FIDO WebAuthn Yubico Authenticator YubiKey -

Security considerations for the top 8 mobile device-restricted workplaces When looking at enterprises and organizations, there are many different business scenarios that can be present when addressing secure authentication. Whether those be shared workstations, remote workers, or even privileged accounts, there is one in particular that introduces its own difficulties: mobile device-restricted workplaces. It’s safe to say that there will always be workplaces which, […] Read more authentication FIDO MFA mobile authentication phishing-resistant MFA WebAuthn -
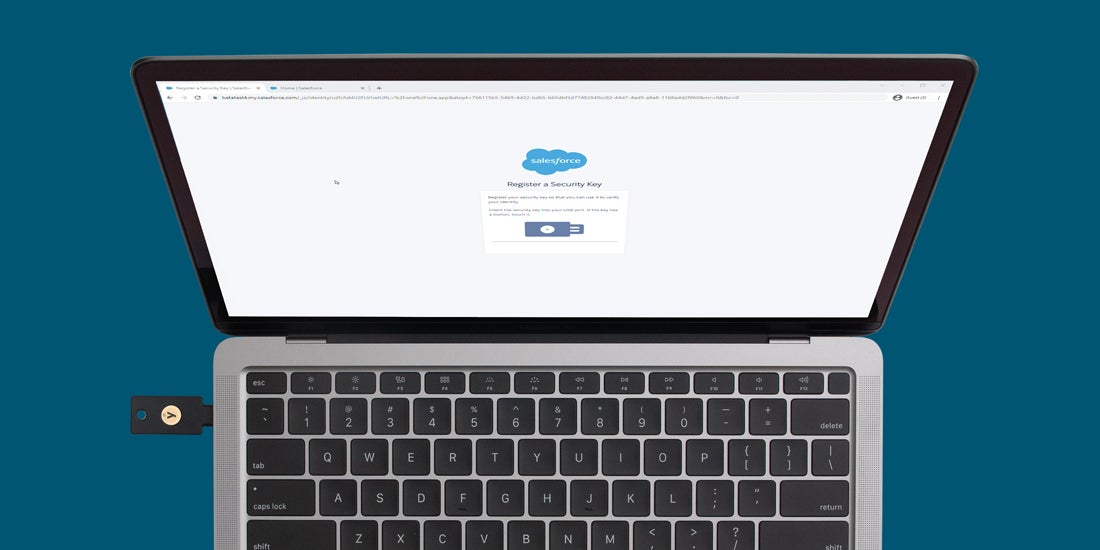
Salesforce is requiring MFA: Why this matters and what you can do As sophisticated cyberattacks continue their relentless pursuit towards SMBs and enterprises, companies must prioritize improvements to their cybersecurity infrastructure to better secure their customers, employees, and partners. Username and passwords no longer provide adequate security against the ever evolving landscape of cyberattacks. Late last year, Salesforce took a strong and decisive stance, announcing that beginning […] Read more authentication FIDO FIDO U2F MFA YubiEnterprise YubiKey -

Now is the time to accelerate phishing resistant MFA While 2021 isn’t quite over yet, at Yubico, we took a moment to reflect on many of the changes and impacts that have happened in the cybersecurity industry. This year has marked some of the biggest security breaches in history including the SolarWinds and Colonial Pipeline hacks. And with these cybersecurity attacks, we’ve seen: Action […] Read more AWS FIDO phishing YubiKey zero trust -

Mitigation and incident response plans to help prevent ransomware attacks We’ve all grown accustomed to a flood of ransomware attack news almost every week, with no end in sight. The recent arrest of two Ukrainian ransomware attackers demonstrates that the White House is serious about going on the offensive against ransomware distributors. But often enforcement could end up being a game of whack-a-mole — hit […] Read more authentication FIDO MFA ransomware security key -

FIDO authenticators and YubiKeys are making the internet safer In 2007, Yubico set out to protect as many people as possible by making secure login easy and available for everyone. We are happy Apple has joined Yubico, Google, and Microsoft on this journey by implementing W3C WebAuthn/FIDO compatible platform authenticators and are pleased to say that now all major platforms have adopted the standards […] Read more FIDO FIDO Alliance WebAuthn YubiKey -

What is a Man-in-the-Middle (MiTM) Attack? What is the goal of a Man-in-the-Middle attack? The goal of these attacks are to steal personal user information. Examples are usernames and passwords, credit card information, or account details. Attackers then use obtained information to access account information, change login credentials, or initiate unapproved fund transfers. How do I prevent Man-in-the-Middle attacks? Security keys […] Read more authentication FIDO FIDO U2F security key -

What is FIDO U2F? Where did U2F come from? FIDO U2F was created by Google and Yubico, and support from NXP, with the vision to take strong public key crypto to the mass market. Today, the technical specifications are hosted by the open-authentication industry consortium known as the FIDO Alliance. U2F has been successfully deployed by large scale services, […] Read more FIDO mobile authentication U2F -
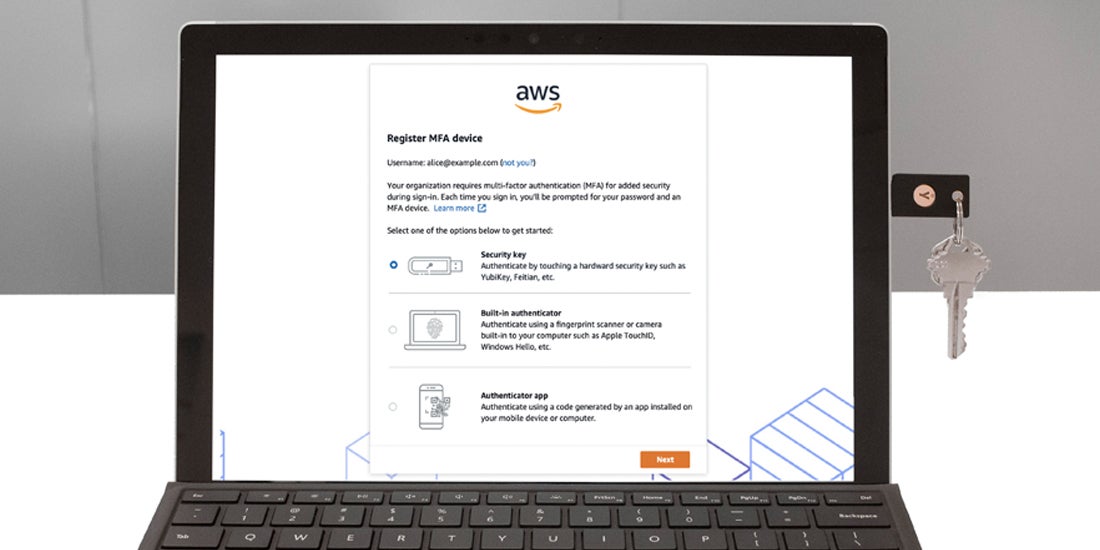
AWS Expands YubiKey Support with AWS SSO WebAuthn Integration Another win for FIDO at the heels of its first industry conference, Authenticate 2020. AWS Single Sign-On (SSO) has introduced native WebAuthn support to secure user access to AWS accounts and business applications using strong, FIDO-based multi-factor authentication (MFA) with YubiKeys. Broader choice of authentication methods by AWS SSO is a win for modern authentication that has historically […] Read more authentication FIDO Works with YubiKey wwyk
