The PCI Security Standards Council (PCI SSC) published version 4.0 of the PCI Data Security Standard (DSS) at the end of March, kickstarting the transition from PCI DSS v3.2.1, which will be retired on March 31, 2024. Some new requirements may not take full effect until 2025, but that’s no reason to put them off. PCI DSS v4.0 was designed to address the emerging threat landscape, introducing a number of changes – 77 of which are marked as evolving and/or new requirements.
While much attention is being given to the more technical requirements like network hardening (Requirements 1 & 2), protection of account data (Requirements 3 & 4), and the mandate to implement multi-factor authentication (MFA) for all access into the cardholder data environment (Requirement 8), there are other sections to consider. In particular, special attention should be paid to Requirement 12, which sets forth requirements for an information security policy. In fact, there is a great deal of synergy between Requirement 8 and 12 – a synergy we think retail and hospitality organizations should pay particular attention to.
What does PCI DSS v4.0 say about MFA?
First, let’s take a look at Requirement 8 of PCI DSS v4.0, which expands MFA requirements to include at least one factor for users and administrators and at least two factors of MFA for all access into the cardholder data environment (CDE). This new guidance is consistent with NIST Special Publication 800-63. The Requirement specifically references the FIDO Alliance when choosing authentication factors.
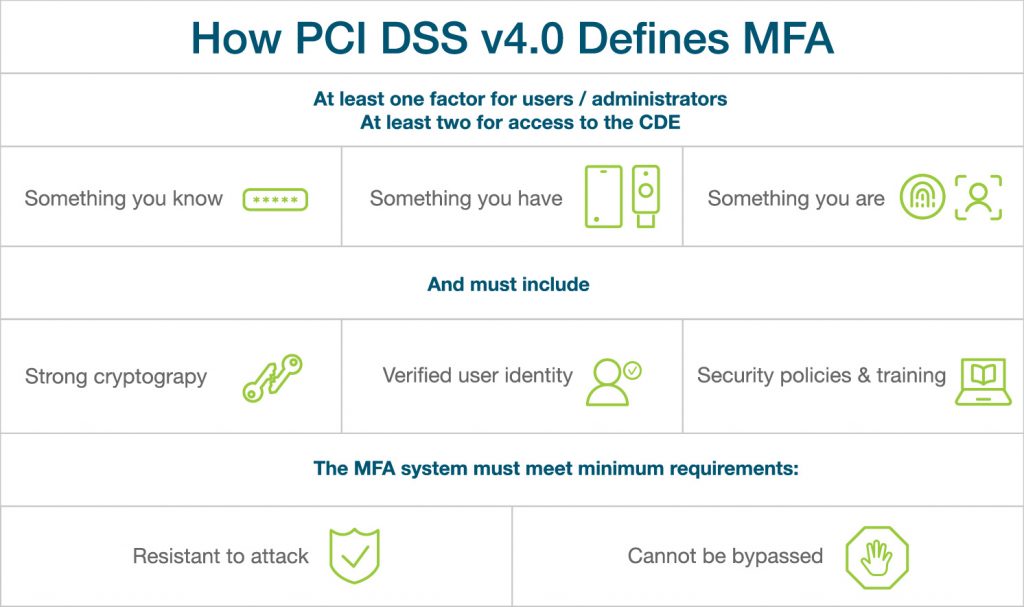
If this sounds like “phishing-resistant MFA,” you’re correct. The language in PCI DSS v4.0 specifically references the NIST SP 800-63 update on phishing-resistant MFA. These guidelines state that all MFA processes using shared secrets are vulnerable to phishing attacks — including common factors such as passwords, security questions, mobile-based authentication (SMS) and magnetic stripe cards. NIST defines strong MFA by its use of asymmetric key cryptography to protect against phishing attacks.
Phishing-resistant MFA is the focus of many regulatory agencies: a recent example came from the US Federal Trade Commission (FTC) who took action against Drizly for the data breach that exposed data of 2.5 million consumers. The FTC explicitly noted security requirements that should be taken into account – implementing MFA that “shall not include telephone or SMS-based authentication methods and must be resistant to phishing attacks.”
Today the only two authentication processes that meet the above requirements of phishing-resistant authentication for access to the CDE include:
Retail and hospitality organizations must now roll out phishing-resistant authentication for all access to the CDE and must consider carefully the authentication factors for other user and administrative access.
Currently, the only exclusion to Requirement 8 is for those user accounts on point-of-sale (POS) terminals that have access to only one card number at a time to facilitate a single transaction. However, this is where we need to take a more careful look at Requirement 12 – because your choice in authentication factors at every level has a huge impact on how easy or difficult Requirement 12 compliance will be.
How are Requirements 8 and 12 related?
Requirement 12 of PCI DSS v4.0 details the need for an information security policy and programs, including user training, technical control oversight, and ongoing risk analysis. In combination with other areas of PCI (such as anti-phishing mechanisms), the goal of Requirement 12 is to create and enforce policies to manage evolving threats.
One of those threats specifically outlined is credentials (12.3.1), which are vulnerable to external threat, misuse, or high staff turnover. Further, in instances where passwords/passphrases are used, the compliance requirements increase. In retail, this means checking the box for every new POS user that they have full understanding of information security standards.
Long story short: the weaker your MFA posture, the greater your compliance burden. Longer policies. More user training. More controls to manage risk.
The solution? Apply strong phishing-resistant MFA to all users.
Making the case for phishing-resistant MFA for POS users
Retail and hospitality industries are now among the top three most compromised industries, with 75% of POS compromises directly linked to social engineering or phishing attacks. While some (not all) of these POS users may be exempt from the PCI DSS v4.0 requirements for strong phishing-resistant MFA, there is a need to optimize authentication across POS and shared kiosk environments to address security and ease of authentication.
The use of less secure authentication methods carries an increased risk that attacks will be successful – attacks which carry a high price tag (on average $3.28 million in retail, $2.94 million in hospitality for a breach). Now organizations also need to consider the high cost of information security training, controls and risk assessments for PCI DSS v4.0.
Lastly, there’s the strong drive to make authentication easy for POS users, while also having it be very secure. No risk of forgetting a password, getting a new barcode every day to log into POS terminals or taking time away from the customer to authenticate. Imagine, for example, how a guest would feel if a front desk representative had to refer to their mobile phone to engage with a mobile-based authenticator during a customer interaction?
To learn more about the drive to modernize MFA in retail and hospitality, and specifically how security can help boost customer loyalty and elevate the customer experience, read our whitepaper, Protecting against modern cyber threats in retail and hospitality.





