Security Advisory YSA-2024-02
Security Advisory YSA-2024-02 FIDO Relying Party Enumeration
Published Date: 2024-05-21
Tracking IDs: YSA-2024-02
CVE: CVE-2024-35311
CVSS Severity: 3.3
Summary
To address a low severity privacy issue, Yubico has released updated firmware for YubiKey 5 Series, Security Key Series, and YubiKey Bio Series. The YubiKey CSPN Series and YubiKey 5 FIPS series are also affected. The YubiKey 5 FIPS series will receive this privacy update in the next release of that series of keys.
In order to exploit this low rated privacy issue, an attacker would need physical access to the YubiKey/Security Key or local access to the user’s computer or phone where the YubiKey is used. This issue does not expose the credential or any other associated data on the secure element. Impact is also limited to applications and services with FIDO2 discoverable credentials*, often used in passwordless login without a username prompt. Non-discoverable FIDO2 credentials, often used in combination with a password, are not affected.
If an attacker had possession of the key or local access, they could potentially exploit this issue to discover a subset of the applications and services (not the user’s credentials) that have been paired with the YubiKey. They could then bypass an expected user verification prompt and see applications and services for which a user has registered FIDO2 discoverable credentials on the YubiKey. All other YubiKey protocols (FIDO U2F, OATH, OpenPGP, OTP, Smart Card, YubiHSM Auth) are not affected. For technical details of this issue, see Issue Details below.
*For more details about identifying discoverable credentials, see How to Tell if You Are Affected below.
Affected
All YubiKey 5 Series versions up to and including 5.4.3. Fixed in versions 5.7.0 and newer
All Security Key Series up to and including 5.4.3. Fixed in version 5.7.0 and newer
All YubiKey Bio Series up to and including 5.6.3. Fixed in version 5.6.4 and newer
All YubiKey FIPS Series up to and including 5.4.3. Fixed in version 5.7.2 which is being submitted to FIPS for certification
YubiKey CSPN Series 5.4.2.
Not affected software and Devices
YubiHSM 2
YubiHSM 2 FIPS
All YubiKey and/or Security Key models prior to YubiKey 5 Series
All other Yubico software and services
How to tell if you are affected
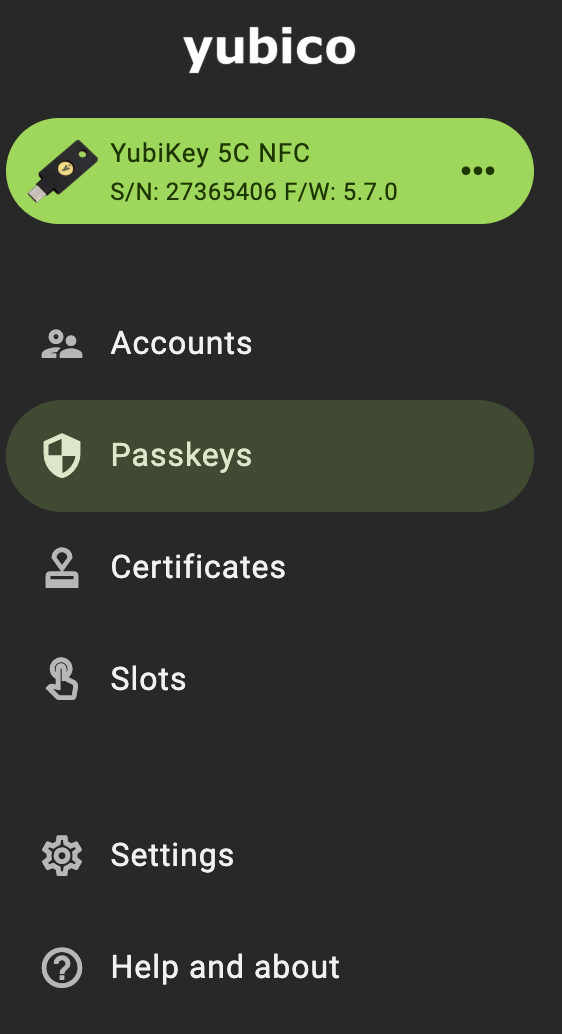
To identify the YubiKey, use Yubico Authenticator to identify the model and version of the YubiKey. The series and model of the key will be listed in the upper left corner of the Home screen. In the following example, the YubiKey is a YubiKey 5C NFC version 5.7.0.
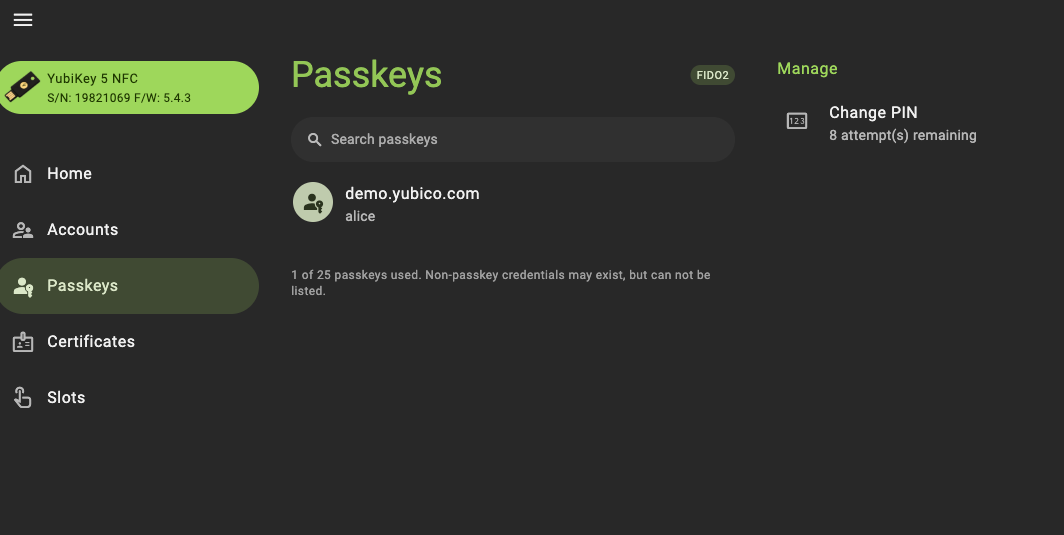
To identify discoverable credentials, use Yubico Authenticator. Go to Passkeys in the menu on the left. Passkeys listed are discoverable. In the following example, there is a discoverable credential for Alice at demo.yubico.com.
Customer Actions
Mitigation
To help avoid local and physical threats, users should continue to exercise due diligence when installing software on their devices and maintain control of YubiKeys.
This can be mitigated by registering non-discoverable credentials in place of discoverable credentials. FIDO discoverable credentials are used in flows that do not require a username as part of registration or authentication, whereas non-discoverable credentials will require a username or other identifier. Second factor FIDO credentials used in combination with passwords are typically non-discoverable credentials.
Issue Details
It is possible for an attacker with the ability to programmatically interact with the YubiKey to enumerate the relying parties (RP) for which a user has registered discoverable FIDO2 credentials on the YubiKey without a user verification prompt. This is due to an issue in the RP enumeration commands implementation in the YubiKey.
FIDO2 has an extension called credential protection which allows a relying party to configure the requirements to retrieve discoverable credential relying party information from an authenticator. FIDO2 credentials can be created with one of three credential protection policies: “userVerificationOptional”, “userVerificationOptionalWithCredentialIDList”, or “userVerificationRequired”.
Credentials created with a FIDO2 credential protection policy of “userVerificationOptionalWithCredentialIDList” or “userVerificationRequired” require a user be prompted for a PIN to allow relying parties to be disclosed to a FIDO2 client. Due to this issue, the user is not prompted for a PIN as they should be which can be used by an attacker to discover what relying parties the user has discoverable credentials for on the YubiKey without the expected user verification prompt.
Severity
Yubico has rated this issue as Low. It has a CVSS score of 3.3
Timeline
| December 18, 2023 | Finder informs Yubico of the issue |
| May 21, 2024 | Yubico releases advisory |
