What is IAM (Identity and access management)?
Identity and Access Management (or IAM) is a key component of cybersecurity focused on authenticating the identity of anyone requesting access to technological resources, and then managing which resources they have access to based on their role and privileges. The central goal of Identity and Access Management is to prevent intrusions into sensitive assets by carefully vetting and limiting who may use or traverse private resources, based on established access policies and governance.
Identity and Access Management
Identity and Access Management (often abbreviated IAM) is a combination of technologies, techniques, and policies employed by companies to manage conditional user access across elements of their tech stack. The form IAM takes can vary widely across different enterprises, but the two primary objectives of Identity and Access Management are undeniably universal. The first objective is to identify who is requesting access to a network, data, application, or other tech assets. The identification, of course, needs to be validated so that hackers are not incorrectly granted access (a false positive) and employees are not incorrectly denied access (a false negative). The second, but equally important, objective is to implement mechanisms that make access configurable and policy driven, such that all users get the exact level of access they need – nothing more and nothing less.
Identity and Access Management FAQs
What Is Identity and Access Management?
Identity and Access Management concepts have been around for almost as long as computing itself. Every system needs a way to grant or deny access and otherwise determine what that access entails based on who is asking for it. In the past, when all employees worked within the same physical corporate network, it was relatively simple to identify who was making a request and whether or not they could be trusted. That has all changed in recent times, however, now that employees work both remotely and at the office, and use a combination of conventional computing equipment but also mobile devices. Meanwhile, many companies now rely on a combination of on-prem and cloud-based services, and cyber attacks use sophisticated and evasive tactics to exploit or maneuver laterally between all of the aforementioned.
With requests for access coming quickly and frequently from a myriad of locations, networks, and devices, it becomes increasingly difficult to identify who is knocking at the door. It also becomes increasingly risky to let the wrong person inside, since any cyber attack can potentially have devastating consequences, from business disruptions to compliance violations and even expensive lawsuits. Identity and Access Management systems are designed to help security teams navigate the challenges and risks involved with permitting someone to access sensitive resources. While they generally offer a litany of bells and whistles to configure access controls under the hood, on the surface, provide a simple and seamless experience so that authorized users can reach the data and applications they need to stay productive from anywhere.
Various other Identity and Access Management security tools (such as Privileged Access Management) also help balance the need to make access easy for a few and difficult for all others. They help security teams administer access at a granular level, granting or revoking privileges at scale and limiting access to the fewest privileges necessary (in accordance with zero trust principles). Allowing just one intruder to enter can result in a large-scale cyber attack with deep and lasting consequences, making it essential to get Identity and Access Management right every time.
How Does Identity and Access Management Work?
There are Identity and Access Management protocols that should be in place everywhere, along with Identity and Access Management frameworks that are relevant to everyone. However, the details of IAM are unique to each company depending on who they need to identify, what they need to restrict access to, and what sort of Identity and Access Management security tools they have to work with. Regardless, there are three key concepts which come into play whenever there is an access request:
- Identification – Being able to identify who is requesting access. Login credentials are the most common way to identify users, but they are also easy to exploit, forcing security teams to consider alternatives or solutions to strengthen this aspect.
- Authentication – Verifying that someone using an identification has a rightful claim to access. Ways to authenticate someone include using something they know (password, PIN), something they have (smart card, security token), or something they are (fingerprint, retina scan).
- Authorization – Granting someone certain privileges – and denying them all others – based on their identification and once they have been authenticated. For example, a low-level employee will have fewer privileges than an IT admin.
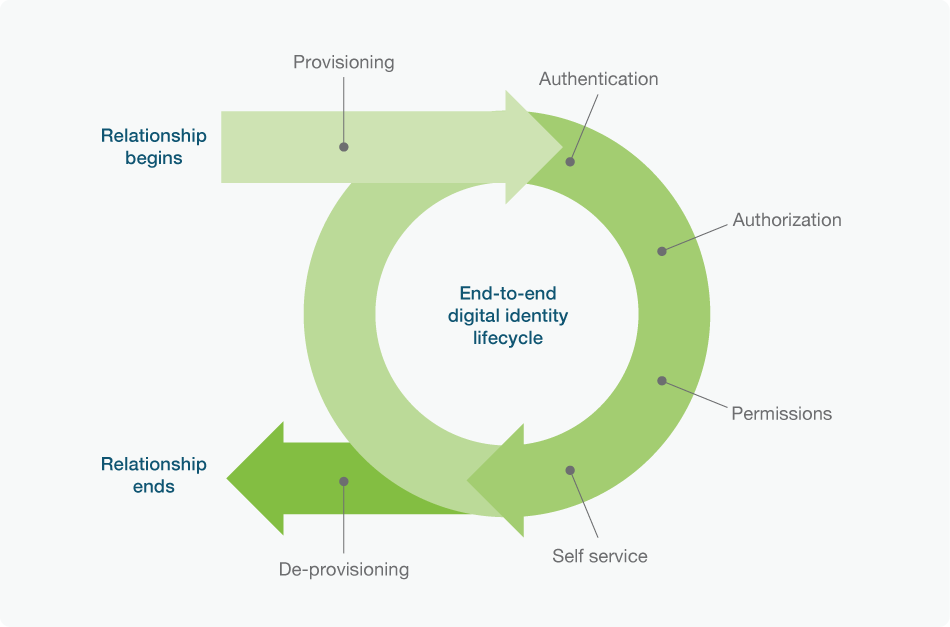
Identity and Access Management addresses each of these concepts individually, but it also groups them collectively, seeking ways to make all three work in concert to either approve or deny access faster and more reliably. Doing so depends on having Identity and Access Management software in place to handle authentication and authorization automatically. There will also need to be defined policies and protocols that dictate how to identify, authenticate, and authorize someone according to internal Identity and Access Management policies and governance.
IAM as an amalgamation of Identity Management and Access Management
Think of them as two separate but interdependent processes. So what is identity management and access management?
Identity management focuses on the first part of the equation: authentication. The overarching objective of identity management is to take the identification provided by a user and compare it against a predetermined list of authorized identities. Different Identity and Access Management vendors use different methods – some stronger than others – to authenticate identities. But authentication alone is not enough. After confirming that someone is in fact who they claim to be, the priority shifts to deciding what privileges to grant them.
Access management focuses on the second half of the equation: authorization. It considers the role, needs, and risks inherent to a specific user, then gives them access to whatever their identity allows. For example, an accountant should have access to financial data but not to personnel records, which might be the opposite of someone working in HR.
From a user’s perspective, there is no difference between Identity Management and Access Management collectively – they are generally both perceived as being part of the same seamless process. For security and IT teams though, it’s important to understand how identity and access each involve their own unique requirements and challenges, and why both must succeed for IAM as a whole, to work as intended. For instance, if access management is not up to date, a fired employee could authenticate their identity to open resources they should be locked out of. Alternatively, if identity management isn’t current, legitimate users might struggle to access the resources they need because they can’t authenticate themselves in the first instance.
Identity and Access Management Concepts
There are a multitude of Identity and Access Management concepts to consider when establishing, extending, or improving any effort at digital gatekeeping. Some to focus on include:
- Immutable Identifiers – People can change their username and password; these are mutable identifiers. But there needs to be an immutable identifier in place that links a person or device to an authorized identity that cannot be changed by users themselves or even by hackers. The authorization part of IAM depends on having a central access system that stores and secures immutable identifiers.
- Multi-Factor Authentication – Passwords are easy to exploit, making it easy for hackers to fraudulently authenticate themselves and be granted access. Multi-factor authentication requires someone to provide two different forms of authentication, such as a password plus a smart card or one-time password.
- Zero Trust – The rapid shift to zero trust cybersecurity principles is driving adoption of Identity and Access Management frameworks. When adopting a “trust nothing, verify everything” mentality, zero trust advocates for authenticating users more frequently and more rigorously, and limiting privileges granted to those users to the absolute minimum necessary. Following zero trust makes IAM more important and, to an equal or greater degree, more complicated too, which is an issue that Identity and Access Management vendors are racing to address.
- Governance – Even though Identity and Access Management systems are primarily the responsibility of the IT or security teams, every department has input about who should have access to what, and there may arise conflicts between stakeholders who want to extend access for productivity purposes versus those that want to restrict it due to security or compliance concerns. The goal of Identity and Access Management governance is to establish enterprise-wide policies and procedures so that any inconsistent practices between departments or conflicting priorities do not compromise either cybersecurity or accessibility of the enterprise.
Identity and Access Management Challenges
When huge numbers of users and devices are requesting access to a similarly huge number of widespread IT resources, IAM can get difficult and it can become surprisingly easy for enterprises to veer towards one of the many security pitfalls. To name just a few of these:
- Unknown Identifiers – As companies begin sharing access to digital resources with more customers and partners, and users start working from new locations with their own personal devices, figuring out who should and should not have access becomes unclear, especially as requests for access become more numerous.
- Remote Provisioning – The shift to remote work makes it harder to provision smart cards, a common tool of Identity and Access Management, to employees in far flung locations. They also can’t use smart cards on phones or any device without a card reader. The concept of smart cards remains one of the strongest Identity and Access Management tools, but the card itself has become an obstacle in need of alternatives.
- Granular Permissions – Granting users access to everything they need without going any further – and affecting enterprise-wide security or compliance as a result – depends on defining and granting granular privileges; more than just “employee,” “manager,” and “administrator.” Making this work requires improvements to identity management to learn more about who is requesting access, followed by improvements to access management to slice and dice their privileges accordingly. Zero trust principles help to define an overarching architecture to verify each access request and to be less dependent upon a defined perimeter by tying these concepts together, and all but emphasizes the need for continued IAM vigilance.
- Evolving Threats – There was a time when multi-factor authentication was the gold standard for Identity and Access Management solutions regardless of the type or implementation. But now, only phishing-resistant forms of MFA hold that title. Threats evolve and become more sophisticated over time, and in ways that make optimal IAM and security at large a moving target. What works today won’t necessarily work tomorrow, and managing this challenge requires Identity and Access Management tools that can adapt as companies and security requirements inevitably change.
Identity and Access Management Benefits
Identity and Access Management has many benefits, as outlined below. Prioritizing Identity and Access Management and addressing the associated challenges is something companies absolutely must do for the sake of their cybersecurity, compliance, business continuity, and potentially even survival in a digital world.
- Stronger Security – Preventing hackers from even penetrating their way through the initial access points, makes them significantly less threatening. Strong Identity and Access Management governance can also prevent many internal or accidental data breaches. Overall, improvements to IAM makes data breaches far less likely and prevents attacks before they become incidents.
- Greater User Access – Productivity in a digital world depends on users having anytime, anywhere access to all the data and tools their work requires on any device they would like to use. Identity and Access Management solutions that make that possible enable employees to stay productive outside the office while helping their employers embrace a remote work strategy with confidence it can work.
- Better IT Utilization – With the right Identity and Access Management tools handling the bulk of the work – and preventing more breaches – the IT team can focus their time and attention elsewhere. Making authentication and authorization into something that’s manageable, scalable, and automatic to a large extent, frees up more resources (i.e. time, staff, budget) for other priorities.
Identity and Access Management Protocols
Any company vetting or weighing various Identity and Access Management vendors or implementing an Identity and Access Management project plan should keep some important practices in mind:
- Strive for Zero Trust – Embrace the zero trust philosophy of strictly limiting access by authenticating users early and often, and by granting them role-based permissions for access.
- Use Phishing-Resistant MFA – Enterprise Identity and Access Management makes MFA essential, but authentication factors like passwords, one-time passwords, security questions, and push notifications are all vulnerable to phishing and should be avoided.
- Enable Self-Service Onboarding – Making it possible for users to provision and maintain their digital identity, including personal authentication methods, makes life easier for end users and IT teams alike, especially as the physical office becomes less relevant.
- Build a Bridge to Passwordless – Both an annoyance and a security risk, passwords are becoming a relic of the past. It may not be possible or prudent to go passwordless tomorrow, but any Identity and Access Management solution should build a bridge to a future without passwords.
Does Yubico Enable Identity and Access Management Prevention?
Yubico makes Identity and Access Management easier, more effective, and better suited to the realities of both today and tomorrow.
The YubiKey is a hardware security key that can be easily attached to a keyring alongside other physical keys, such as house or office keys. Companies can send their employees (or even business partners who require network access) a YubiKey that they can then use to self provision access, or depending on company policies, is even pre-registered to enable easier central management. Afterwards, plugging the YubiKey into any USB port or tapping it against an NFC reader, securely authenticates who they are and what device they are on.
Unlike traditional smart cards, the YubiKey does not require a dedicated card reader, and it works natively with most tablets and phones for authentication across the full spectrum of devices. The YubiKey also adds to any Identity and Access Management framework, a form of phishing-resistant MFA, which many public and private sector organizations are increasingly required to adopt due to stricter universal data protection regulations. The twin priorities of IAM, security and accessibility, each improve with the use of security keys. But the most exciting changes lie ahead because the YubiKey also makes passwordless authentication a real possibility, potentially changing the entire landscape that has historically been defined by passwords.
Find out more about how Yubico supports Identity and Access Management here.
Get started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

