What is 2 Step Verification?
2 Step Verification (Two step verification) is an authentication process requiring users to provide exactly two forms of validation before access is granted. The service provider will typically prompt for a username and password to initiate proceedings, before requesting users to provide a second validation to complete the ceremony.
2 Step Verification (Two Step Verification) Definition
2 step verification (sometimes known as 2SV) requires users to go through exactly two layers of authentication before they are finally granted access to a sensitive digital resource, whether an email account, an enterprise app or network. In a system that has two step verification enabled, a user must typically provide one form of proof pertaining to something “they know” – often a user name and password – and then provide a second form of proof of “something they have”, which can take many forms. More organizations are choosing to set up two step verification as a way to increase their security perimeter against unauthorized access and, in the process, prevent cyber attacks and data breaches.
2 Step Verification FAQs
What Is 2 Step Verification?
Ironically, the simplest way for hackers to gain access to a system, bypass security measures, and reach sensitive IT assets is not to sneak in or even break in; it’s usually to unlock the front door and enter with “permission”. An increasing number of cyber attacks utilize a strategy of stealing, phishing or otherwise exploiting login credentials, which hackers can then use to falsely authenticate themselves and gain entry where they are otherwise not permitted. 2 step verification attempts to resist unauthorized front door entry, by at least making the standard authentication process more complicated to compromise.
A report from Microsoft indicates that requiring 2 step verification stops automated attacks 99.9% of the time. It’s also demonstrably effective against persistent and evasive attacks, plus any attacks that have a human hacker advancing them forward. 2 step verification, like every single other method of cybersecurity, is never effective 100% of the time and cannot singlehandedly prevent unauthorized access as a sole mechanism. Nevertheless, 2SV is one of the easiest, most economical, and most effective ways to prevent cyber attacks and keep important IT assets off limits for everyone except those with explicit permission to access them.
How Does 2 Step Verification Work?
2 step verification can work in any number of ways, since the only strict requirement is that it involves two steps to authenticate a user requesting access. Otherwise, security practitioners who set up two step verification have wide latitude to choose what those steps are and how they are implemented. In all cases, the goal is always to balance the need for strong security to deter or prevent attackers, with the equal need for accessibility and ease of use for authorized users. Some organizations put a greater emphasis on security, while others on accessibility, thus striking a balance between the two will impact what the two step verification process ultimately looks like.
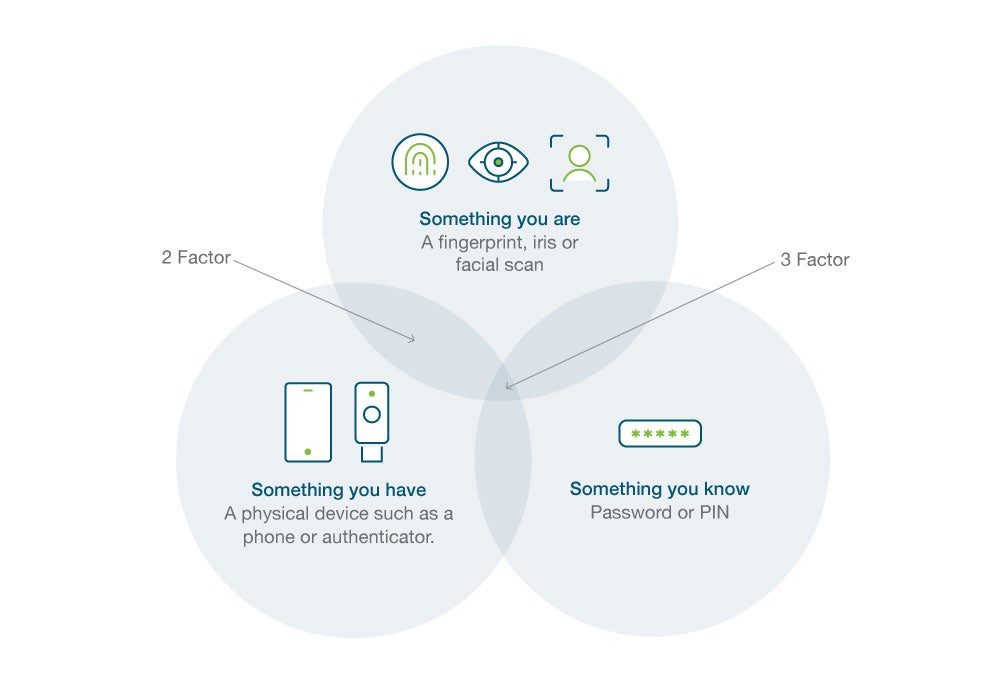
There are many ways to authenticate users, in order to validate who they claim to be. Most require the provision of something that only the user could be in possession of, whether that be a physical object, piece of knowledge, or biometric feature. The most common authentication factors currently in use include:
- Knowledge Factor – “Something you know” such as a password or PIN.
- Possession Factor – “Something you have” such as a phone, smart card or security key.
- Inherence Factor – “Something you are” such as a fingerprint or face matching a record of an existing scan.
Here’s one common method that 2SV is often implemented: a user must first enter their password, and then enter a six-digit one-time passcode sent to their phone as an SMS text message. Passwords are easily exploited, but even if a hacker was able to exploit the password in this particular example, they would also need to either be in possession of the user’s phone or intercept the text messages to get through the second verification step. Basic hackers either can’t or won’t go to that level of effort, so their attacks will either prove ineffective or else they will simply avoid systems with 2SV in favor of easier targets.
Here’s another example of two step verification in action: a user inserts a smart card or security key into a laptop to establish that the person issued that card or key (and not someone else) wishes to authenticate. The user is then prompted to enter a password or PIN as an additional requirement of entry. Since attackers will not have physical possession necessary to even get to the second step, they will not have the opportunity to exploit the password either. Making the possession factor the first one in the two step verification process creates a formidable obstacle in front of sensitive IT assets.
Two Step Verification vs Two Factor Authentication
The terms two step verification and two factor authentication (2FA) often get used interchangeably. And while they are overlapping concepts, they are not exactly the same. This may not matter from a user’s perspective, but for IT administrators and security teams, however, it’s important to distinguish 2SV vs. 2FA.
For all intents and purposes, the terms authentication and verification mean the same thing. Therefore, the difference between two step verification and two factor authentication comes down to the words in the middle: step compared to factor.
The two step verification definition states that verification needs to involve two separate steps, but they don’t necessarily have to be different. For example, the first step could be to enter a password, followed by a second step to enter another password. This would fit the definition of a two step verification process.
It would not fit the definition of a two factor authentication process, though, because both steps use the same authentication factor. With 2FA, each step must utilize a different authentication factor, similar to the examples outlined in the previous section. In that way, every instance of 2FA is also an instance of 2SV, but not every instance of 2SV fits the definition of 2FA.
Another definition worth bringing into this discussion is multi-factor authentication or MFA. Essentially the same as 2FA, the only difference is that MFA can involve more than two factors. Once again, 2 step verification will also be an example of MFA, but not necessarily the reverse.
Anyone inquiring about what is two step verification should also question which authentication method is the most secure. As a general rule of thumb, the more authentication factors that are required for access, the harder it will be to gain fraudulent access. That means 2 step verification is not as intrinsically secure as 2FA or MFA. How safe is two step verification, then? It’s certainly much safer than single-step verification, and even when it includes two of the same authentication factors, it drastically lowers the likelihood of a successful attack. But it is by no means providing infallible security either, especially to the degree provided by MFA or even 2FA
Benefits of 2 Step Verification
There are many benefits for organizations and individuals that enroll in two step verification. Some are obvious and others unexpected, but in all cases, adding a second step makes authentication more secure and in turn, makes IT more secure. Some of the advantages of a two step verification process include:
- Stronger Security – It’s difficult to quantify but impossible to deny how much 2SV improves upon a single-step authentication process. The second step often proves to be a powerful deterrent for attacks, leading to fewer overall attacks and, more importantly, fewer successful attacks. Few, if any, other security improvements upgrade cybersecurity as significantly as the leap from one step to two step verification does.
- Simpler Security – When considering how to set up two step verification, it’s worth noting that it takes minimal time and effort on the part of the security team. Given how much 2SV upgrades cybersecurity, it is one of the easiest security measures to implement and manage, especially for organizations with a wide IT footprint or a lean security team.
- Increased Productivity – As remote work increasingly becomes the norm, 2 step verification can securely authenticate employees working in diverse locations even with personal devices coming from outside the corporate network. In this manner, employees can efficiently access the data and apps they need to be productive from anywhere, without it becoming a security liability.
- Lower Cost – There are many solutions on the market to secure access and even more intended to stop attacks. Two step verification is one of the most economical overall: it’s relatively inexpensive to implement or enroll in two step verification, but doing so drastically lowers the risk of expensive attacks.
2 Step Verification Process
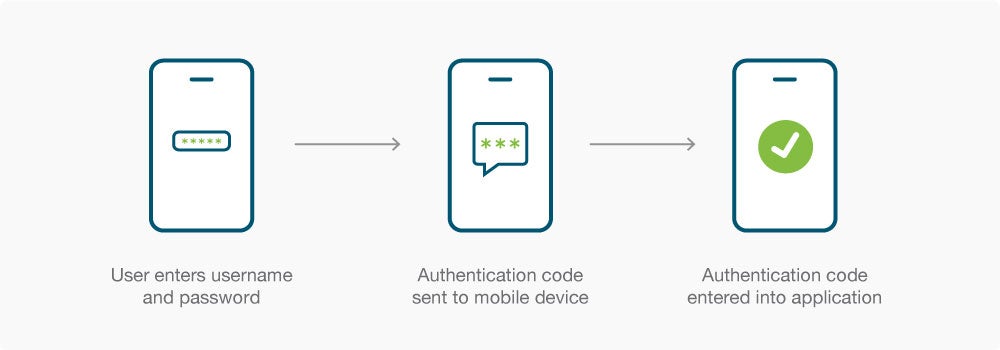
Although the benefits should now be clear with everything written to this point, you may now be wondering what to actually implement in order to require two step verification from a user? The two step verification process depends on the specific steps involved. Many instances rely on login credentials – user name and password – as the first step. However, it’s important to stress that involving a password anywhere in the two step verification process is neither mandatory nor desirable, since passwords can be easily discovered or stolen, even if they are long, complicated, and changed regularly. Not to mention the fact that they’re easy to forget and difficult to manage at scale.
In response, there’s a push to move towards passwordless access as a way to improve both security and accessibility. 2 step verification makes that possible – but the process matters. Here’s why: the simplest way to set up 2 step verification is typically to have a code sent as a text message or email. The problem with that approach is that codes sent as digital information are vulnerable. Email accounts in particular are easy to break into or redirect, and intercepting text messages isn’t much harder. Is it possible to hack two step verification? The odds for a successful attack get a lot better when one of the steps requires a password or something that isn’t resistant to phishing. The ideal two step verification process, therefore, involves neither, but rather factors such as biometrics, a hardware security key or notifications sent to a secondary or mobile device.
Also important to consider is how to turn off two step verification. While the process should make this possible, it should not be up to individual users to decide but determined at a policy level. The ideal process requires users to undergo both verification steps every time, but also takes measures to ensure those steps are simple and seamless.
Does Yubico Offer 2 Step Verification?
Yubico offers a form of 2 step verification that combines passwordless protection with phishing-resistant authentication incorporated into a device that’s affordable and accessible to deploy while being intuitive and efficient to use.
Our signature product, the YubiKey, is a security key that someone must plug into the USB port of their laptop or tap against their phone using NFC before they can access a computer, network, or online service. Yubikeys can be used on their own to make single-step verification more secure in a passwordless capacity, but they are can also instrumental in making two step verification harder to compromise.
An important facet of the YubiKey is that it must be connected to the nominated device before the authentication process can proceed. Activation is achieved by pressing a small button on the device when prompted, which ensures that a real person is sitting at the device seeking access and not a remote attacker. This is a simple but proven countermeasure against sophisticated attacks.
Another factor largely depends on how IT admins elect to implement the end-to-end flow. Instead of utilizing a two step verification code sent to an email or as an SMS, which we have established can be risky, they can complement YubiKeys with other authentication factors like biometrics (for peak security) or PIV smart cards (if they are already incorporated into the infrastructure). PINs are also an option with smart cards, since they are easy to deploy and require no additional hardware. And since the PIN is associated with a specific YubiKey locally, someone must steal the PIN and the right security key to compromise the authentication process.
For companies that have yet to set up 2 step verification but now need to because of remote workers, security concerns, or data regulations, the YubiKey offers an easy entry point. And for those companies already relying on 2SV but are struggling to balance security with accessibility, the YubiKey offers a fresh approach to authentication designed for the realities of both today and tomorrow. In either case, a company striving to make 2 step verification work will find a lot to like about the YubiKey.
Get started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

