BROCHURE
Phishing-resistant users: The next evolution in authentication
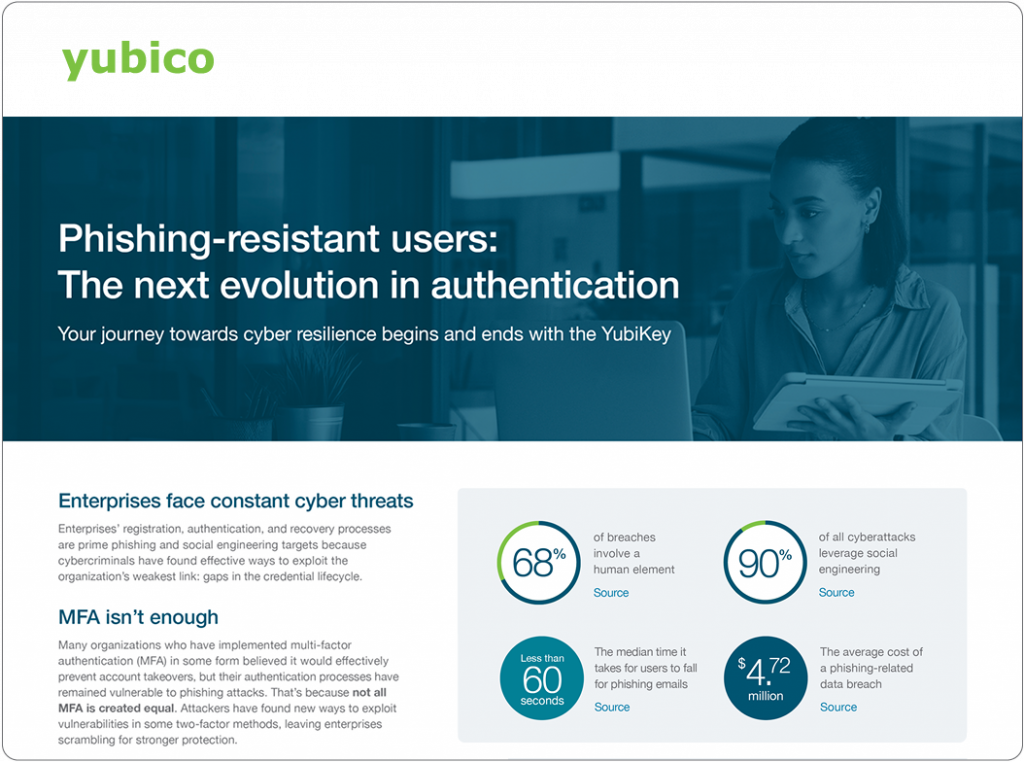
Enterprises’ registration, authentication, and recovery processes are prime phishing and social engineering targets because of the gaps in the credential lifecycle.
Learn why your journey towards cyber resilience begins and ends with the YubiKey to cultivate phishing-resistant users where the authentication moves seamlessly with the user no matter how or where they work.
