Resources
Browse our library of white papers, webinars, case studies, product briefs, and more.
-

The evolving threat of phishing and social engineering The report classifies the three major passkey credentials in the market and highlights the benefits of creating phishing-resistant users. Read more -

Active Directory Security Management: From Threat Detection to Effective Response Join us for this informative session to enhance your AD security management skills and safeguard your organization’s critical assets. Read more -

Securing Your Organization with YubiKeys at Scale – Part 2 Join us for this in-depth session as we navigate the YubiKey journey, equipping you with the knowledge and tools to elevate your organization’s rollout strategy with confidence. Read more -
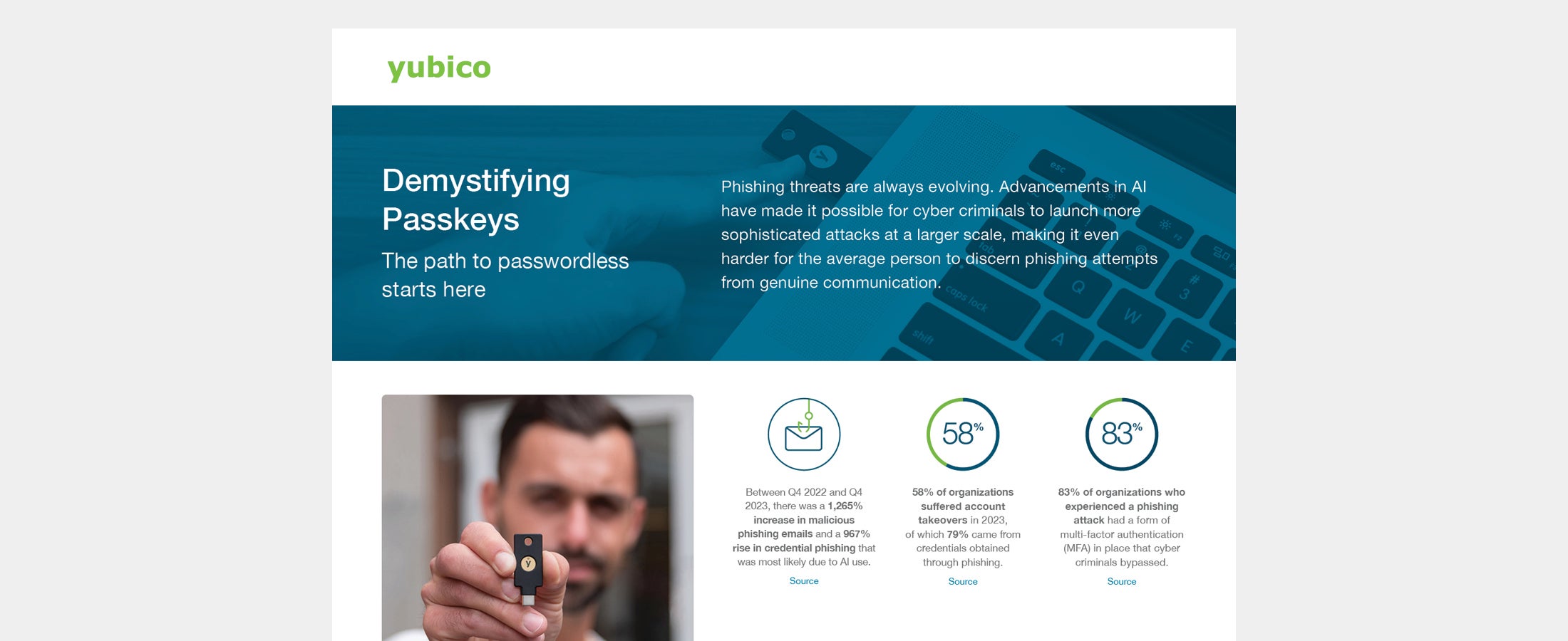
Demystifying passkeys Organizations can avail of three different types of passkey implementations but it is vital to choose the right passkey approach based on your organization’s required security and risk posture. View the Yubico visual industry brief to learn more. Read more -
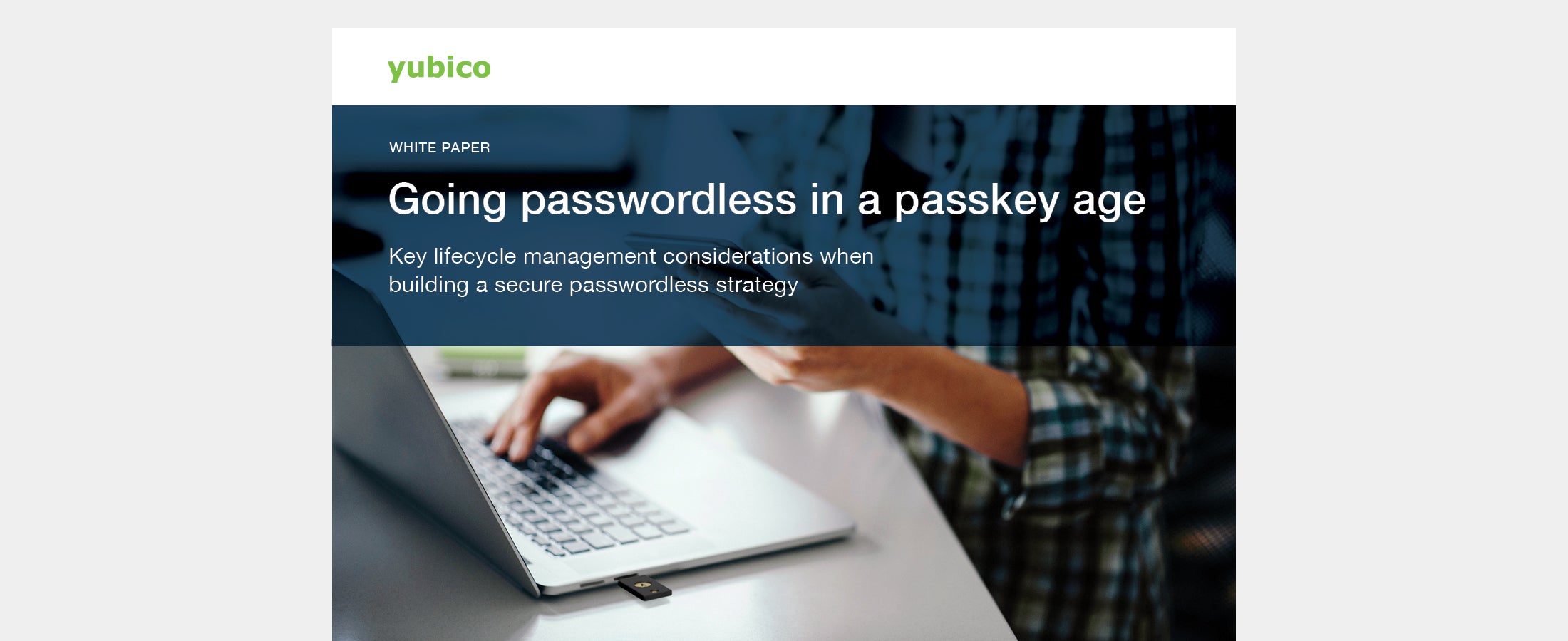
Going passwordless in a passkey age Read the Yubico white paper to get real guidance on how enterprises can evaluate passwordless authentication options in the age of passkeys. This white paper discusses how enterprises can address and mitigate current and future issues with a sound passwordless deployment. Read more -

Phishing-Resistant Insurance Enterprises Protect your insurance organization from costly phishing attacks and data breaches with YubiKey’s phishing-resistant authentication. Learn how to enhance security, save on mobile costs, and improve user experience. Read more -

Modern authentication for the Army Download the free brochure to learn how the YubiKey solves U.S. Army authentication modernization use cases. Read more -

YubiKey as a Service product brief Learn how YubiKey as a Service can help you accelerate to passwordless and create phishing-resistant users across the enterprise. Read more -

Going passwordless and meeting CJIS at City of Southgate Join us for a candid discussion with Jason Rucker, Director of IT, City of Southgate, and Robb Ervin, Sr Solutions Engineer, Yubico to learn about the goals, timelines, obstacles and wins along their passwordless deployment journey. Read more