Most organizations struggle with legacy authentication, with passwords and mobile-based solutions a source of security risk, high IT cost, and frustrated users. However, for organizations with shared workstations and shared device environments, these pain points are only intensified. Shared workstations—common across industries such as healthcare, manufacturing, retail and hospitality, financial services, energy, utilities, oil and gas, and education—are, in fact, subject to some of the most insecure practices:
How do shared workstation environments encourage a higher rate of risky user behavior? And what can you do about it?
Let’s take a look at healthcare. In a recent survey by the National Library of Medicine, 73.6% of healthcare professionals report using another staff member’s credentials to access an Electronic Health Record (EHR). For medical residents, this number jumps to 100%. In some cases, a lack of credentials or inadequate privilege are to blame (interns, visiting physicians)—but not always.
Even with strict HIPAA requirements and high rates of IT security education, IT security professionals in healthcare continue to confront these unsafe behaviors. Why? Because to the healthcare professionals, “the medical mission trumps the security mission”—and no policy or technical safeguard is likely to eliminate this kind of behavior. Any step that increases the time to access critical systems has the potential to impact patient care.
But what about in other shared workstation or shared device scenarios? While other industries may not carry the weight of patient safety concerns, there is a common theme to insecure authentication practices: urgency.
The retail industry is in the midst of a customer experience revolution. Employees feel pressure to deliver a seamless, streamlined retail experience—pressure that increases the chance of insecure practices such as staying logged into terminals or mPOS devices. In fact, a recent survey has indicated that 38% of employees (cross-industry data) say password sharing is company policy.
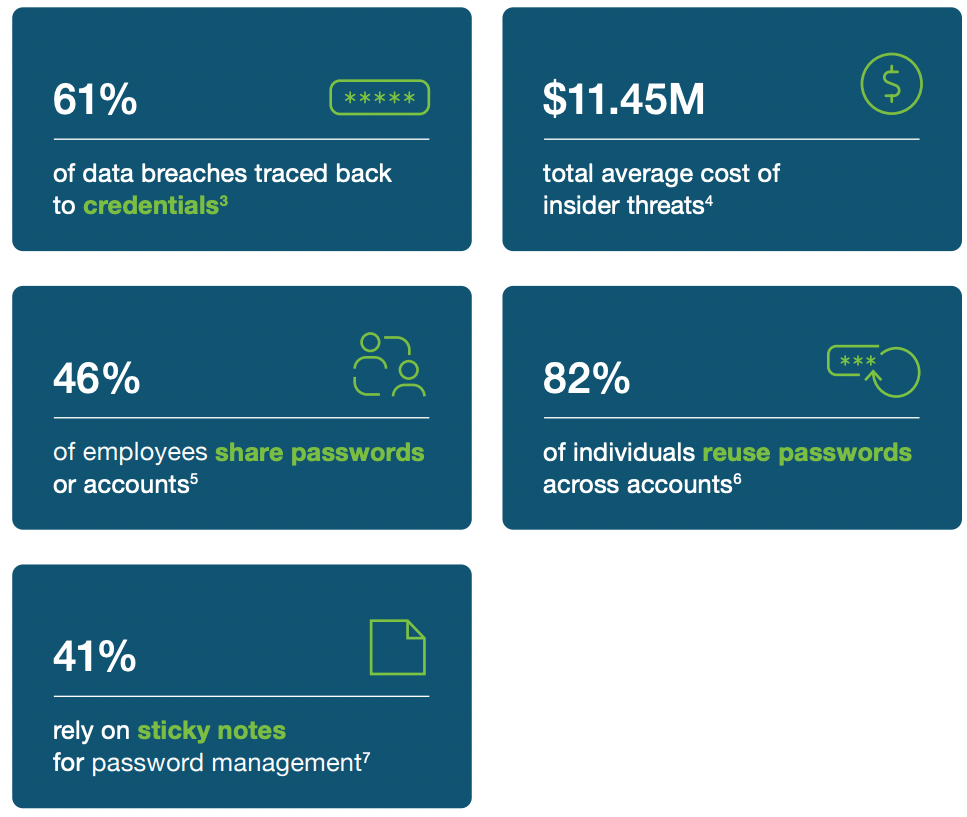
Even where knowledge of security and password best practices are high, password sharing remains a problem. A recent Yubico study found that 51% of all employees share passwords with colleagues to access business accounts – including 49% of IT security respondents.
Across pharmaceuticals, manufacturing, utilities and oil & gas, it’s often user gloves that get in the way of authenticating to production terminals and company systems. Who has time to take gloves off to enter passwords or pull out a mobile device to receive a second-factor authentication (push-app or SMS OTP)? In some mobile-restricted environments, it’s not even possible. In others, legacy systems have perpetuated the continued reliance on username and passwords over more secure multi-factor alternatives.
Similar to the above industries, user frustration and the need to get the job done create situations that encourage workarounds. Like the 41% of employees who rely on sticky notes for password management. At a shared workstation desk or shared device environment, this simply adds risk. Risk that credentials will be compromised by malicious insiders or cyberattacks. Risks that devices left unattended can be abused or absconded in high-traffic areas. Risk of compliance violation for password sharing or access to privileged or protected data. Or even the risk that a phishing attempt to gain access to shared credentials will be believed rather than mistrusted.
The fault is not with the user – it is with legacy authentication
In these types of work environments, we simply amplify the insider threat – whether malicious or negligent. But the fault does not lie with the user, corporate culture, or even with IT policy. The fault lies with legacy authentication. There is no combination of username and password, or username and password with mobile authenticator, that addresses the critical need to authenticate quickly and seamlessly to a shared office workstation environment.
Addressing authentication challenges for shared workstations requires a thorough understanding of the security, efficiency, reliability, and cost challenges of these unique environments, as well as the need for modern approaches that are simple, productive, and portable.
———
For a detailed analysis on shared workstations, continue reading our whitepaper, “Securing shared workstations against modern cyber threats.”



