Still undefeated.
The original passkey. The world’s largest brands are secured with YubiKey.
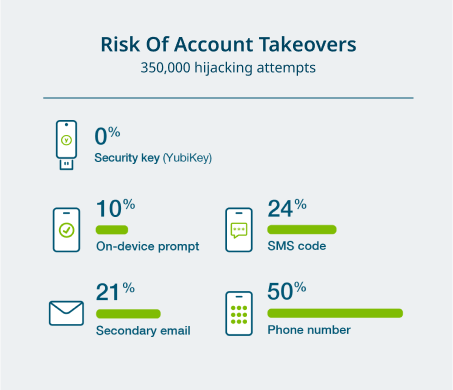
Most attackers don’t break in—they log in.
Companies pour billions into sophisticated network security and breach detection, but rely on legacy passwords, SMS and authenticator apps, that are easily bypassed by modern AI-powered hackers and create a false sense of security.
Passkeys beat passwords and outdated security—and the future is passwordless.
YubiKey—The original passkey
Yubico is the ground-breaking cybersecurity company behind the YubiKey—a modern security key that stops AI-powered cyberattacks, online identity scams, fraud, and account takeovers 100% of the time.
YubiKeys deliver hardware passkeys that eliminate passwords and remove reliance on other outdated authentication methods, and make any other passkey more secure.

The passkey standard starts here

Yubico authored modern authentication standards that led to passkeys

YubiKeys offer the most secure passkeys and make all other passkeys stronger

Each YubiKey holds 100 passkeys—work and personal accounts secured!
The original Passkey (security key) success story

Demystifying the Passkey ecosystem
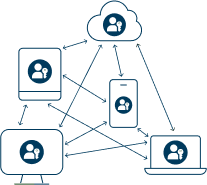
Synced / Built-in passkeys
- No extra hardware needed
- Easy for Android or iPhone ecosystems
- Medium level security backup
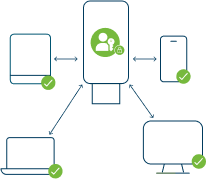
Passkeys in security keys
- Hardware delivery to a user strengthen user verification
- Works across all platforms and devices
- Affordable high security backup, enabling cyber resilience and business continuity
Passkeys are a hot topic
As the landscape evolves, leave it to us to help you understand the latest.


The Gartner Trust Scale for Authentication
FIDO2 security keys ranked “Very High”
Gartner® Report: The Must-Have IAM Requirements for Enterprise Applications 6.5.25 | Access the report
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the
U.S. and internationally and is used herein with permission. All rights reserved.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document.
Not for redistribution.

The winning passkey strategy for the enterprise
Combining both built-in and hardware passkeys

Why T-Mobile rolled out phishing-resistant device-bound passkeys to over 200k employees.
Why Okta deployed YubiKeys to their 6k employees, creating a phishing-resistant workforce.
The world’s largest and most trusted brands are already there

T-Mobile

Hyatt

Cloudflare
Get started

Have more than 500 users?
Learn how YubiKey as a Service makes delivering modern authentication easy.

Need deployment assistance?
Need help with deployment planning, user training, integrations or anything else?

Get started now
We’d love to help you make secure login easy and available for your organization.